-
-
Fancy Button code in CSS | HTML
HTML file CSS file Explanation : Similar explanations apply to the other a span:nth-child(n) rules, each with variations in positioning, gradient direction, and animation name. Finally, the @keyframes rules define the animations: These @keyframes rules define the animations for the spans, each animating the position (left, top, right, bottom) from off-screen to on-screen and vice…
-
Concentric loader In CSS
Concentric loader CSS file A loader, often referred to as a spinner or loading animation, is a visual indicator used to convey to users that a web page or application is processing or fetching data. It serves as a visual cue to reassure users that their request is being attended to, especially in situations where…
-
Online Earning in 2023 | Whatinfotech
Earning money through online means is becoming popular day by day. There are various ways of earning money through online means. You can either work for someone or start your own business.
-
File Structure in Angular
File structure in Angular and important files in angular .
-
Installing Angular and Creating a new project on Windows
Installing Angular on Windows System and creating our first angular project using angular CLI
-
HackTheBox retired machine writeups
Hackthebox retired machine are those machines which are not active on the Hackthebox . But the good thing about the retired machines is that the writeups for hackthebox retired machines are available . So the beginners who are starting the CTF journey can read these writeups and get the idea how the machines are solved .
-
HackTheBox Shibboleth Writeup
This machine involves scanning of ports which then leads to ipmi hashes leak. Then followed by subdomain enumeration and logging into zabbix account .Then getting reverse shell through command execution through zabbix
-
Active machines | BSD | CTF
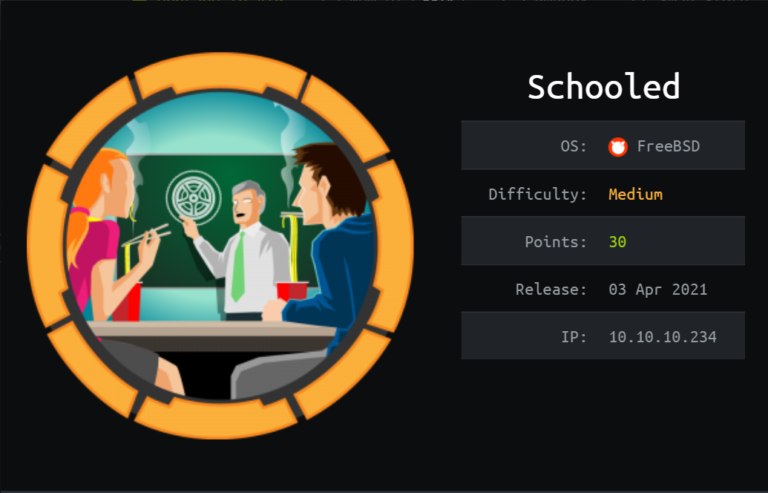
Hackthebox Schooled writeup
This box is a medium level box from the hackthebox .Which starts with the subdomain enumertion.And this using xss to get the teacher cookies …
-
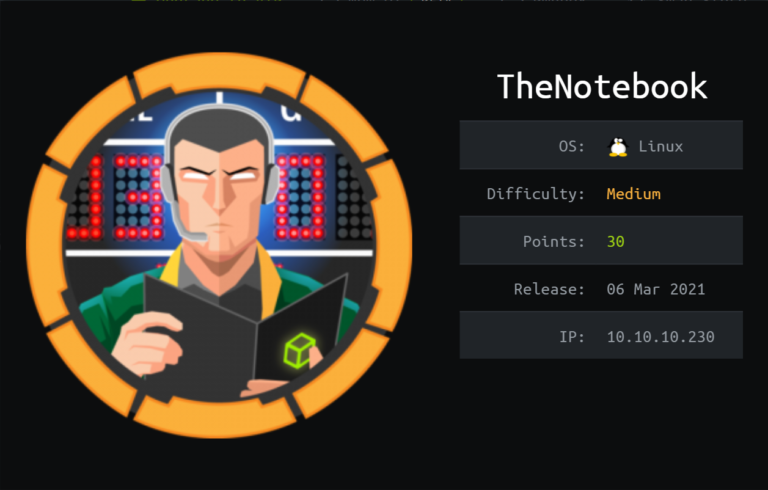
Hackthebox thenotebook writeup
It is a medium level machine from hackthebox which is great for learning new skills . It starts with the abusing of jwt token which leads to admin panel and which further leads to the www-shell . Then a little enumeration we get the ssh keys for the user. For privilege escalation sudo exploitation was enough and a little google gets the work done.